Table of Contents
- What is Cybersecurity Maturity Model Certification 2.0?
- Why CMMC 2.0 Matters More Than Ever
- The Three Maturity Levels of CMMC 2.0
- Benefits of Cybersecurity Maturity Model Certification 2.0
- How to Prepare for CMMC 2.0 Certification
- FAQ
- 1. What is CMMC 2.0?
- 2. How many levels are there in cybersecurity maturity model certification 2.0?
- 3. Is self-assessment allowed under CMMC 2.0?
- 4. How does CMMC 2.0 differ from NIST 800-171?
- 5. Do small businesses need cybersecurity maturity model certification 2.0?
- 6. How long does certification take?
- 7. Can ACSMI help with CMMC 2.0 compliance?
- Top Resources for CMMC 2.0 Compliance
- Final Thoughts on Cybersecurity Maturity Model Certification 2.0
Safeguarding sensitive data has never been more crucial, especially for organizations handling government contracts. Cybersecurity Maturity Model Certification 2.0 (CMMC 2.0) is the Department of Defense’s (DoD) answer to evolving cyber threats. Initially released as an update to the original 1.0 framework, cybersecurity maturity model certification 2.0 simplifies compliance while maintaining the robust security standards required to protect classified and controlled unclassified information (CUI).
Navigating CMMC 2.0 may seem daunting—but it doesn’t have to be. This guide breaks down everything you need to know about CMMC 2.0, including updates, benefits, compliance considerations, and tools that can help organizations, like ACSMI’s comprehensive learning modules. By the end, you’ll have the knowledge to grasp what this certification entails and how to implement it efficiently.
What is Cybersecurity Maturity Model Certification 2.0?
Cybersecurity Maturity Model Certification 2.0 is a streamlined yet comprehensive framework designed to standardize cybersecurity practices across the DoD’s supply chain. This certification ensures contractors and subcontractors implement adequate security controls to safeguard Controlled Unclassified Information (CUI).
Key Characteristics of CMMC 2.0
- Tiered Model: CMMC 2.0 introduces three maturity levels instead of five, reducing compliance complexity.
- Self-Assessment: Level 1 allows organizations to self-certify annually.
- Simplified Requirements: CMMC 2.0 aligns with existing cybersecurity frameworks, like NIST SP 800-171, streamlining requirements for compliance.
- Focus on Accountability: Organizations failing to meet these standards risk losing DoD contracts, highlighting the importance of compliance.
By adopting this framework, companies can bolster their cybersecurity posture and maintain eligibility for lucrative defense contracts.
Why CMMC 2.0 Matters More Than Ever
For businesses working with government agencies, compliance with cybersecurity maturity model certification 2.0 isn’t optional—it’s a necessity. Here’s why it matters:
1. Protection of Sensitive Data
Given the surge in cyberattacks targeting government systems, ensuring proper safeguards for sensitive DoD data is critical.
2. Compliance Mandates
Non-compliance with CMMC 2.0 requirements can disqualify organizations from securing contracts with the DoD.
3. Enhanced Credibility
Achieving CMMC certification demonstrates a company’s commitment to data security, boosting its reputation and appeal to stakeholders.
4. Adaptable Framework
By aligning with established frameworks like NIST, CMMC 2.0 requirements become more adaptable for businesses already implementing foundational security standards.
5. Reduced Complexity
With fewer maturity levels and streamlined processes, smaller organizations find it easier to engage in compliance efforts.
Organizations meeting these compliance requirements position themselves as trusted leaders ready to tackle complex government contracts.
The Three Maturity Levels of CMMC 2.0
One of the most substantial updates introduced by cybersecurity maturity model certification 2.0 is the simplification of its maturity levels.
Level 1 (Foundational)
- Description: Basic safeguarding practices are implemented to protect Federal Contract Information (FCI).
- Assessment: Annual self-assessment.
- Ideal For: Small businesses or contractors without direct CUI handling responsibilities.
Level 2 (Advanced)
- Description: Adherence to NIST SP 800-171 practices, critical for CUI data safeguarding.
- Assessment: Third-party assessments every three years.
- Ideal For: Medium to large organizations handling sensitive CUI data.
Level 3 (Expert)
- Description: Advanced security practices in alignment with NIST 800-172. Focused on mitigating Advanced Persistent Threats (APTs).
- Assessment: Conducted by the DoD.
- Ideal For: Systems frequently targeted by advanced cyber threats.
Each level builds upon the previous one, ensuring scalable implementation for organizations of all sizes.
Benefits of Cybersecurity Maturity Model Certification 2.0
Achieving certification under CMMC 2.0 offers a wealth of advantages.
-
Eligibility for DoD Contracts
Compliance is mandatory for organizations bidding on contracts requiring controlled unclassified information (CUI) protection. -
Streamlined Processes
The alignment with NIST frameworks reduces the complexity of compliance, saving costs and time. -
Improved Cyber Hygiene
Through mandatory practices, companies enhance their overall cybersecurity operations, reducing vulnerabilities across the board. -
Futureproofing Investments
CMMC 2.0’s forward-thinking approach ensures organizations remain resilient against cyber threats while prepared for regulatory evolution. -
Strengthened Trust
Achieving certification showcases robust security, solidifying trust among partners and customers.
How to Prepare for CMMC 2.0 Certification
1. Conduct a Gap Analysis
Evaluate your organization’s existing cybersecurity measures against the requirements of cybersecurity maturity model certification 2.0.
2. Invest in Training
Programs like ACSMI’s modular certification scheme help bridge knowledge gaps and ensure your team is prepared for audits and compliance.
3. Create a System Security Plan (SSP)
Document your cybersecurity protocols, risks, and remediation plans. A comprehensive SSP is mandatory for higher maturity levels.
4. Engage Third-Party Assessors
Organizations seeking Level 2 or Level 3 certification must engage independent assessors. Proper preparation ensures smoother reviews.
5. Leverage Tools and Resources
Using frameworks like NIST as a guide simplifies the process. Additionally, resources like ACSMI’s online modules make certification attainable.
Explore ACSMI’s learning modules here to optimize your readiness.
FAQ
1. What is CMMC 2.0?
CMMC 2.0 is the updated version of the DoD’s cybersecurity framework, streamlining compliance requirements for protecting controlled unclassified information (CUI).
2. How many levels are there in cybersecurity maturity model certification 2.0?
There are three levels in CMMC 2.0—Foundational, Advanced, and Expert—each building upon the preceding level’s requirements.
3. Is self-assessment allowed under CMMC 2.0?
Yes, organizations pursuing Level 1 certification can self-assess annually. Higher levels require third-party or DoD-led assessments.
4. How does CMMC 2.0 differ from NIST 800-171?
While CMMC 2.0 incorporates NIST 800-171 requirements as a foundation, it includes additional accountability measures, like third-party assessments, to validate compliance.
5. Do small businesses need cybersecurity maturity model certification 2.0?
Yes, small businesses working with the DoD must achieve at least Level 1 certification, ensuring basic safeguarding measures are in place.
6. How long does certification take?
The process varies but typically takes several months, depending on the organization’s readiness and the level of certification pursued.
7. Can ACSMI help with CMMC 2.0 compliance?
Absolutely. ACSMI offers over 400 online modules tailored to meet the requirements of cybersecurity frameworks like CMMC 2.0.
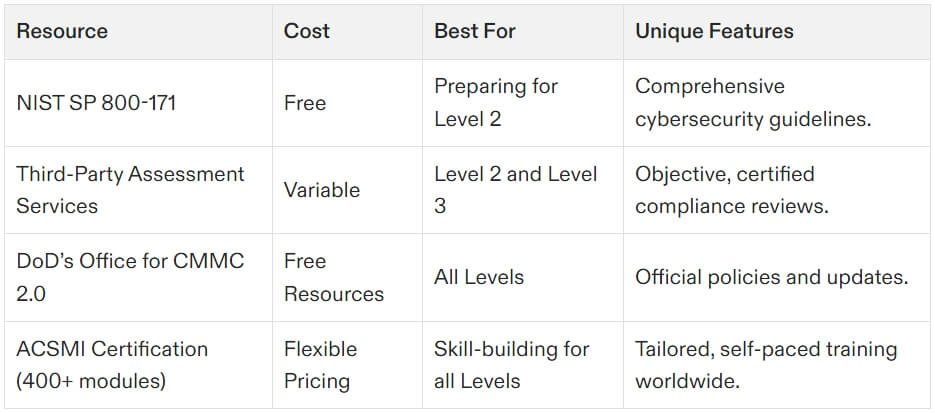
Top Resources for CMMC 2.0 Compliance
Explore how ACSMI empowers seamless CMMC 2.0 compliance here.
Final Thoughts on Cybersecurity Maturity Model Certification 2.0
Navigating the intricacies of cybersecurity maturity model certification 2.0 may seem challenging, but with the correct resources and preparation, compliance is within reach. This framework offers not just regulatory adherence but also a tool to enhance enterprise cybersecurity postures and safeguard sensitive data.
ACSMI’s modular program is one of the most efficient ways to prepare for CMMC 2.0. With 400+ modules designed to cater to different organizational needs and maturity levels, ACSMI ensures you’re fully equipped for compliance and long-term success.
Stay ahead in cybersecurity by exploring ACSMI’s expertly designed modules today here. Protect your business, secure your data, and unlock new government contracts in 2025!

Leave a Reply