Table of Contents
- Why is ICS OT Cybersecurity Important?
- Operational Downtime Costs:
- Physical and Human Risks:
- Economic Security:
- Compliance and Regulations:
- Who Should Pursue ICS OT Cybersecurity Certification?
- How to Earn an ICS OT Cybersecurity Certification
- Core Benefits of ICS OT Cybersecurity Certification
- Final Thoughts
- FAQ About ICS OT Cybersecurity Certification
In today’s digital world, cybersecurity has moved beyond traditional IT systems and is now a critical part of Operational Technology (OT) systems. OT systems manage and control the physical processes in industries like manufacturing, energy, transportation, and water treatment. These systems have long been isolated from the broader corporate IT network to protect them from cyber threats. However, with the increasing convergence of IT and OT systems, these once-isolated systems have become vulnerable to cyberattacks. The need to secure these systems has never been greater, as a breach can not only cause financial losses but also jeopardize public safety. This blog will dive deep into the importance of ICS OT cybersecurity, the Cybersecurity Certification Course Free, the certification path, and the different career opportunities available in this ever-growing field.
Why is ICS OT Cybersecurity Important?
The integration of IT and OT systems has brought efficiencies and improvements in operational capabilities, but it has also opened up new vulnerabilities. OT systems, which were once disconnected from the internet for safety, are now increasingly linked to broader corporate networks, exposing them to the same cyber threats that traditional IT systems face. As a result, the risks to ICS and OT systems have escalated, making cybersecurity a critical priority for industries relying on these systems. These sectors—particularly energy, utilities, transportation, and manufacturing—are essential to the functioning of national and global economies.
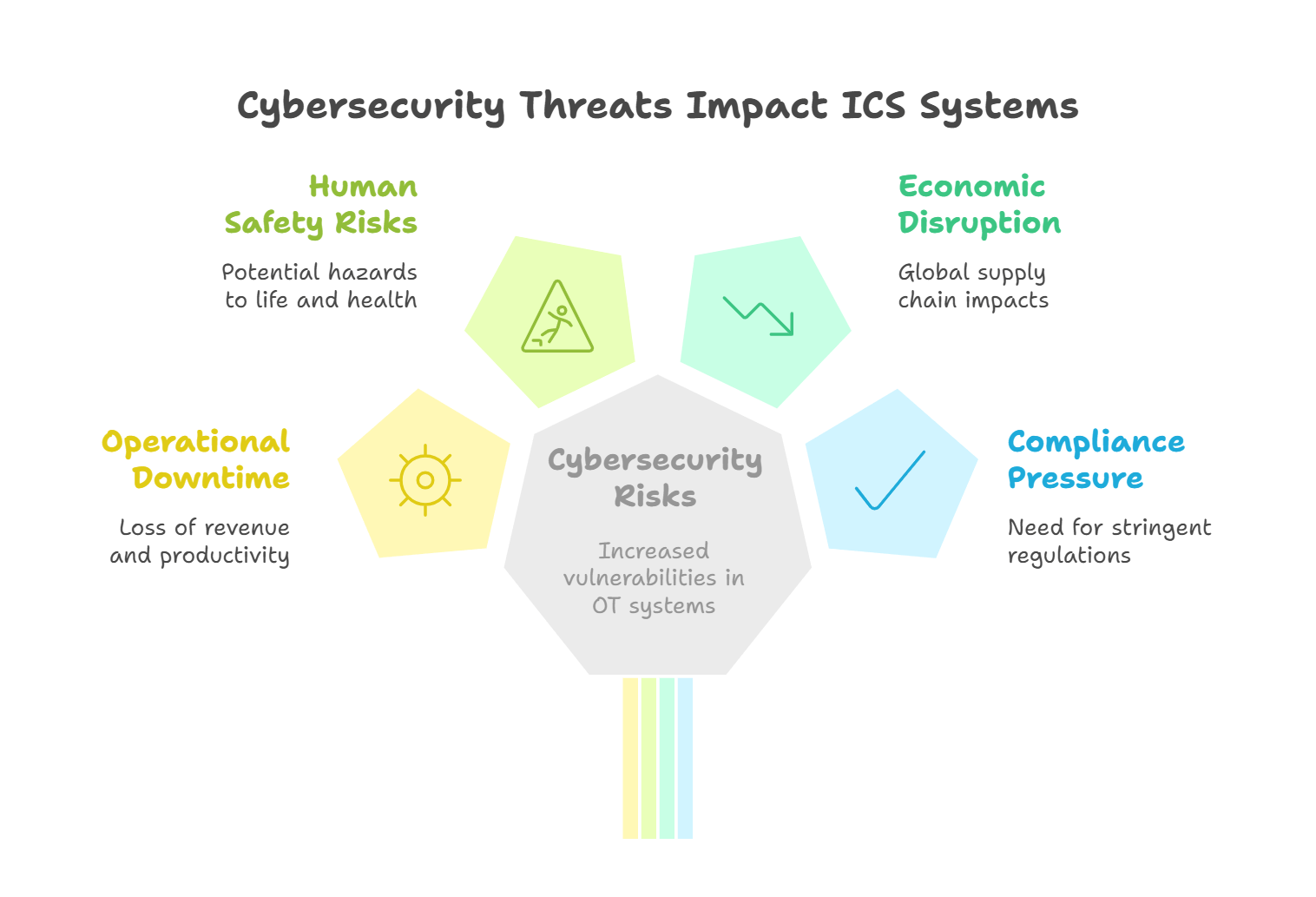
Operational Downtime Costs:
Operational downtime caused by cyberattacks on ICS or OT systems can be incredibly costly. Manufacturing plants and power grids are the backbone of many economies, and a disruption in their operations can lead to millions of dollars in revenue loss per hour. For example, a cyberattack targeting a manufacturing facility could halt production lines, disrupt the supply chain, and create a ripple effect on the broader economy.
Physical and Human Risks:
A successful cyberattack on critical infrastructure doesn't only lead to financial losses; it can also result in significant physical and human risks. In industries like energy and transportation, a failure in operational systems could lead to hazardous conditions such as gas leaks, explosions, or widespread electrical failures that pose threats to human life.
Economic Security:
ICS and OT systems govern many industries that play a direct role in economic security, such as energy production, oil and gas, and transportation logistics. A cyberattack that disrupts these industries can affect the supply of goods and services on a national and international level. Such attacks can have global economic ramifications, affecting stock markets, supply chains, and consumer goods availability.
Compliance and Regulations:
Governments around the world have begun to introduce more stringent cybersecurity regulations for critical infrastructure sectors. For example, in the U.S., the Department of Homeland Security has issued regulations requiring certain critical infrastructure sectors to adopt robust cybersecurity practices. With the growing pressure to meet these standards, certified professionals in ICS OT cybersecurity are crucial for organizations seeking compliance.
In summary, the importance of ICS OT cybersecurity cannot be overstated. As these systems become more interconnected, the threat landscape expands, making it essential to have skilled professionals capable of protecting critical infrastructure from emerging cyber threats.
Who Should Pursue ICS OT Cybersecurity Certification?
The demand for ICS OT cybersecurity professionals spans various sectors, including energy, manufacturing, transportation, and utilities. Several professionals can benefit from ICS OT cybersecurity certification, each for different reasons depending on their current role and future career aspirations.
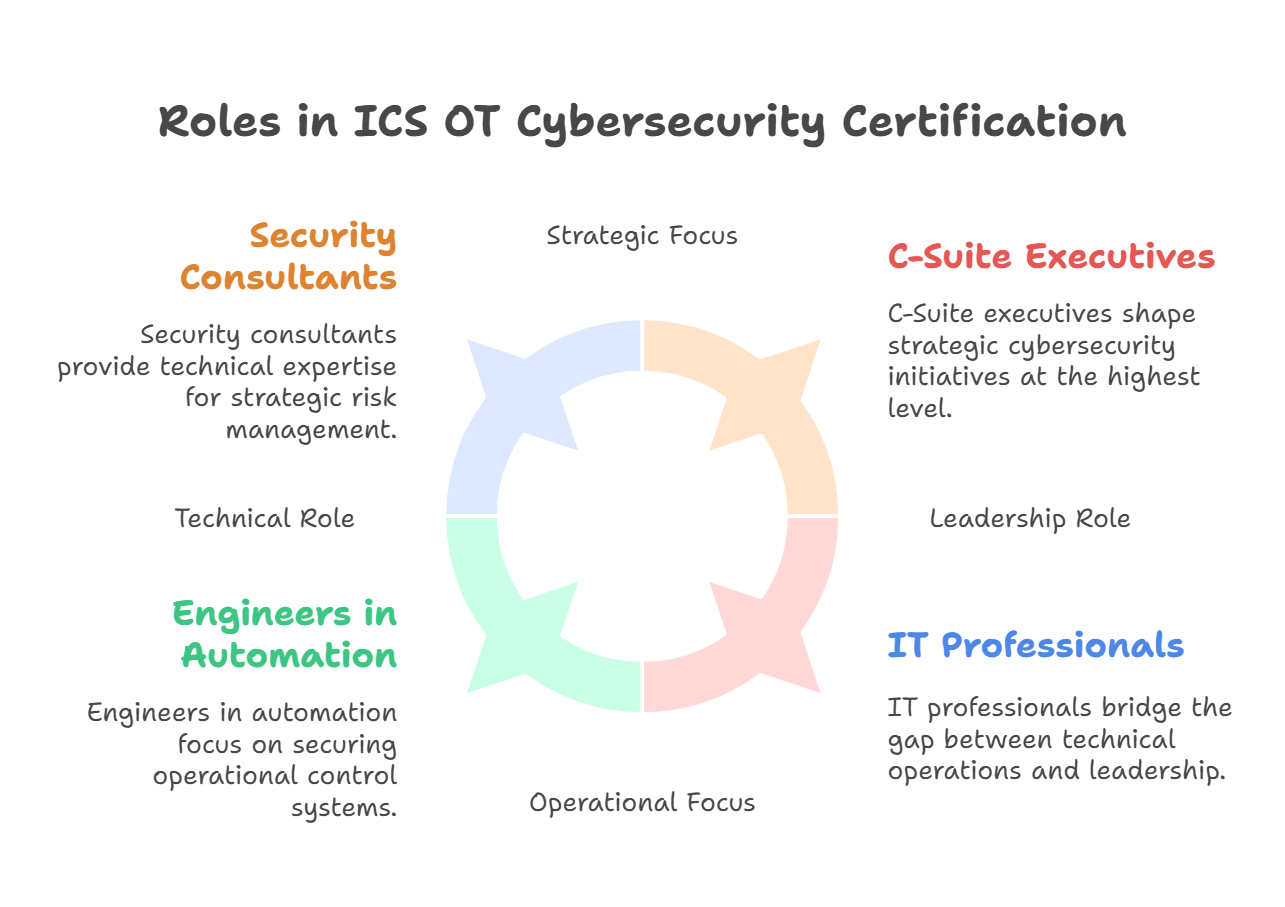
IT Professionals Expanding to OT:
IT professionals already working in cybersecurity roles will find ICS OT certification especially valuable. Transitioning into OT cybersecurity allows these professionals to expand their knowledge beyond IT systems and understand the complexities of securing industrial control systems. With their background in IT security, they can bridge the gap between IT and OT networks and ensure seamless, secure integration between the two domains.
Engineers in Automation:
Engineers working in automation need to develop specialized cybersecurity skills to protect OT systems like programmable logic controllers (PLCs), industrial robots, and SCADA systems. These professionals are responsible for maintaining and operating machinery and control systems that are integral to industrial processes. Learning how to secure these systems is critical for ensuring that operations are not disrupted by cyber threats.
Security Consultants:
Security consultants who work in regulated industries such as energy, oil and gas, and telecommunications can expand their expertise by pursuing ICS OT cybersecurity certifications. These industries have unique challenges in securing their OT environments, making consultants with ICS OT cybersecurity certifications highly sought after. Consultants can help organizations strengthen their security posture, ensure compliance with regulations, and implement effective risk management strategies.
Industrial Leaders:
Managers, plant operators, and compliance officers in industries reliant on ICS and OT systems also benefit from ICS OT cybersecurity certifications. These professionals need to have a high-level understanding of the risks and governance associated with securing OT environments. This knowledge enables them to oversee security operations effectively, manage risks, and ensure that their organizations are compliant with national and international cybersecurity regulations.
C-Suite Executives:
C-Suite executives, such as Chief Information Officers (CIOs) and Chief Technology Officers (CTOs), need to understand the importance of securing ICS and OT systems. They play a key role in shaping their organization’s cybersecurity strategy. ICS OT cybersecurity certification can help executives make informed decisions about risk management, secure digital transformation initiatives, and guide their companies through the challenges of integrating IT and OT systems securely.
By obtaining ICS OT cybersecurity certification, professionals in these roles can gain a comprehensive understanding of OT security, enhance their career prospects, and become essential contributors to the security of critical infrastructure.
How to Earn an ICS OT Cybersecurity Certification
Achieving an ICS OT cybersecurity certification requires a mix of foundational knowledge, specialized courses, and hands-on experience. The path to certification varies depending on the individual’s current skillset and the type of certification they wish to pursue. For a structured approach, referring to a Cybersecurity Certification Guide can help candidates navigate the process effectively. Below are the general steps to obtain ICS OT cybersecurity certification:
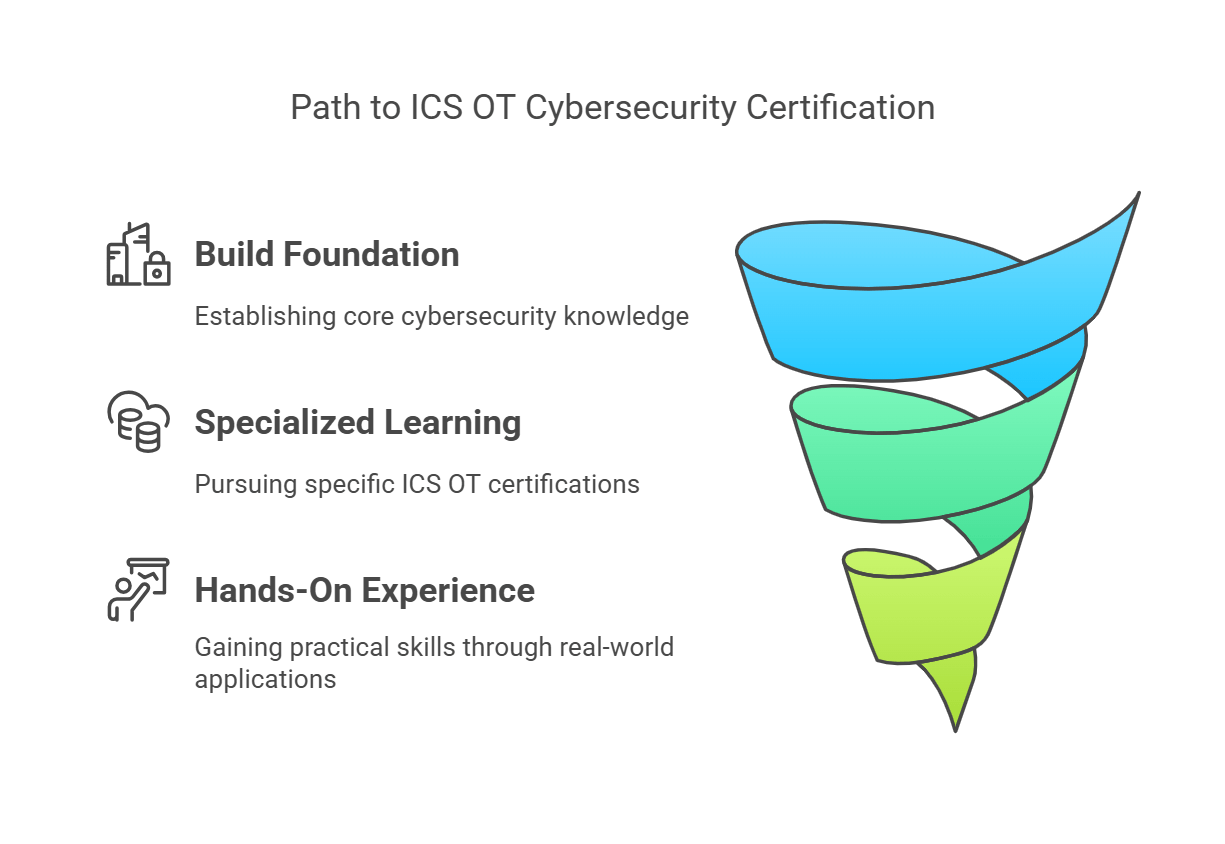
Build Your Foundation
Before diving into OT-specific security topics, professionals should first build a solid foundation in general cybersecurity principles and IT network protocols. Certifications like CompTIA Security+ are great starting points for those new to cybersecurity. This certification covers essential topics such as network security, encryption, and vulnerability management. With this foundational knowledge, individuals will be well-prepared to transition into more specialized ICS and OT cybersecurity training.
Specialized Certifications in ICS OT Security
Once foundational knowledge is in place, professionals can pursue specialized ICS OT security certifications. These certifications are designed to provide expertise in securing critical infrastructure and industrial control systems. Some of the key certifications include:
-
GIAC Global Industrial Cybersecurity Professional (GICSP): This certification offers a blend of IT principles and engineering concepts, addressing both the IT side of industrial networks and the operational technology used to control processes in industries like energy and manufacturing.
-
Certified SCADA Security Architect (CSSA): Aimed at professionals working with SCADA systems, the CSSA certification focuses on securing process control systems that are widely used in critical infrastructure.
-
ACSMI Certification (ICS Modules): The ACSMI certification offers a hands-on approach with over 400 modules focused on securing SCADA-driven industrial networks, testing ICS for vulnerabilities, and protecting industrial protocols.
Take Hands-On Approaches
Practical experience is key to mastering ICS OT cybersecurity. While theoretical knowledge is essential, hands-on training sets experts apart from generalists. Certifications like the ACSMI Certification emphasize real-world applications of security principles, providing professionals with the opportunity to work with industrial control systems, IoT devices in smart factories, and even mitigate zero-day vulnerabilities. By applying their knowledge in simulated environments, individuals gain the confidence to manage real-world cybersecurity challenges in ICS and OT systems.
Core Benefits of ICS OT Cybersecurity Certification
Earning an ICS OT cybersecurity certification provides professionals with numerous benefits that can help advance their careers and increase their value in the job market. Some of the core benefits include:
-
High Demand, High Salaries: Certified ICS OT specialists are in high demand as industries worldwide seek experts who can protect their critical infrastructure from cyber threats. These professionals often earn salaries 20-30% higher than their peers without specialized credentials. This demand for skilled workers is expected to grow as the convergence of IT and OT continues to increase cyber vulnerabilities.
-
Validated Expertise: ICS OT cybersecurity certifications are a testament to a professional’s ability to handle complex security challenges in industrial environments. Certification demonstrates the ability to implement real-time threat detection, manage vulnerabilities in ICS/OT networks, and safely interconnect IT and OT systems without compromising security.
-
Versatile Career Options: The skills gained through ICS OT cybersecurity certification are applicable across many industries, including healthcare (for securing Internet of Medical Things or IoMT devices), energy grids, smart pipelines in oil and gas, and critical transportation infrastructure. This versatility opens up career opportunities across a broad spectrum of sectors.
-
Preparation for Digital Transformation: The ongoing adoption of Industrial Internet of Things (IIoT) devices in industries like manufacturing and energy is driving a digital transformation in OT systems. These connected devices bring new security challenges that ICS OT professionals are trained to address. By earning ICS OT cybersecurity certification, professionals are well-equipped to manage this transition securely.
Strengthening Your Portfolio with ACSMI Certification
The ACSMI certification enhances the skills learned through ICS OT cybersecurity certification by providing a hands-on, immersive learning experience. With over 400 topics covering critical areas such as PLC programming, vulnerability testing for industrial protocols, and malware analysis, the ACSMI certification prepares professionals to lead in the ICS OT space. By combining theoretical knowledge with practical experience, ACSMI certification ensures that professionals can troubleshoot, secure, and maintain industrial networks in any setting.
The ACSMI certification covers a variety of relevant topics, including the protection of IoT devices in smart factories, securing SCADA-driven industrial networks, and managing risks associated with legacy ICS systems. This blend of theory and practice gives professionals the confidence to handle the cybersecurity challenges of modern industrial environments.
Final Thoughts
As cyber threats targeting critical infrastructure continue to evolve, the need for skilled ICS OT cybersecurity professionals becomes even more pressing. By pursuing ICS OT cybersecurity certification and complementing it with the ACSMI certification, professionals can gain both the theoretical knowledge and the practical skills needed to safeguard the world's most vital systems. This combination will future-proof your career and enable you to play an essential role in securing the backbone of our global economy.
FAQ About ICS OT Cybersecurity Certification
What industries benefit most from ICS OT cybersecurity certification?
Industries such as energy, manufacturing, utilities, and transportation benefit the most due to their reliance on ICS and OT systems for their daily operations. These industries often face the highest risks from cyberattacks and thus require highly skilled cybersecurity professionals.
Which ICS OT cybersecurity certification is right for me?
For those transitioning into OT cybersecurity, certifications like GICSP or CSSA are great starting points. However, combining these with the ACSMI certification will provide a comprehensive, hands-on approach to securing ICS/OT systems.
Does ICS cybersecurity align with IT security objectives?
While there is some overlap in cybersecurity principles, ICS focuses more on securing physical systems and ensuring the operational uptime of critical infrastructure rather than just protecting information or data.
Why should I pair ICS OT certification with ACSMI?
The ACSMI certification provides practical skills and hands-on experience, which is essential for those working in ICS OT security. Pairing it with your ICS certification ensures you have both the theoretical knowledge and the real-world experience needed to succeed in this field.
How do ICS certifications keep up with evolving threats?
Certification bodies like GIAC and ACSMI regularly update their content to reflect current industry challenges, including new threats such as ransomware, malware, and the vulnerabilities associated with industrial IoT devices.

Leave a Reply