In today’s digital world, organizations face an ever-increasing array of cyber threats—from malware and ransomware to phishing and data breaches. With cybercriminals becoming more sophisticated, the importance of robust cybersecurity systems cannot be overstated. This is where Cyber Tech comes into play.
Cyber Tech refers to the technologies, tools, and practices used to protect digital assets and ensure the safety of an organization’s data and network. Whether you are a small startup or a large enterprise, integrating Cyber Tech solutions into your organization is crucial for safeguarding your business from cyber threats, improving operational efficiency, and ensuring regulatory compliance. In this blog, we will explore the various benefits of integrating Cyber Tech into your organization and why it should be a top priority.
1. Enhanced Protection Against Cyber Threats
In today’s digital world, cyber threats are becoming more complex and aggressive by the day. From small startups to global enterprises, no organization is immune to cyberattacks. Integrating advanced Cyber Tech solutions is no longer a luxury—it’s a necessity. One of the most important benefits of adopting Cyber Tech is the enhanced protection it offers against a broad spectrum of cyber threats. These threats range from viruses and malware to phishing scams and sophisticated attacks like advanced persistent threats (APTs).
Let’s explore how Cyber Tech solutions provide powerful protection and why every organization should prioritize cybersecurity integration.
Understanding the Range of Cyber Threats
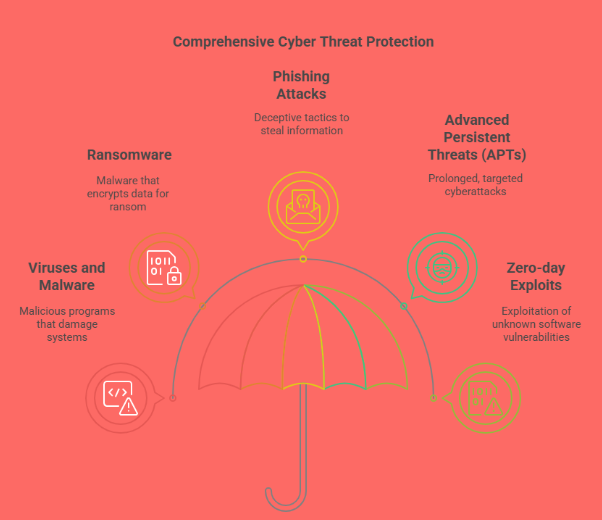
Before diving into the solutions, it's essential to understand the various types of cyber threats businesses face daily:
-
Viruses and Malware: These malicious programs are designed to damage or disrupt computer systems. They can corrupt files, steal data, or even render a system completely unusable.
-
Ransomware: A form of malware that encrypts a victim’s data and demands payment for its release. These attacks can cripple operations, especially for businesses without backups.
-
Phishing Attacks: Cybercriminals use fake emails or websites to trick users into giving away sensitive information like login credentials or credit card details.
-
Advanced Persistent Threats (APTs): These are prolonged and targeted cyberattacks where attackers infiltrate a network and remain undetected while stealing information over time.
-
Zero-day Exploits: These are vulnerabilities in software that are unknown to the vendor. Attackers exploit these loopholes before developers have a chance to patch them.
Because these threats are constantly evolving, traditional security measures alone aren’t enough. This is where Cyber Tech comes into play.
How Cyber Tech Enhances Protection
Integrating Cyber Tech solutions into your organization’s IT infrastructure provides layered security and proactive defense. Here are some of the key components and how they work together to safeguard your digital environment:
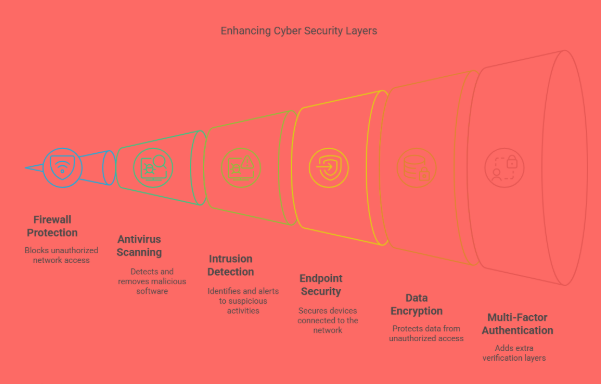
1. Firewalls
Firewalls act as the first line of defense. They monitor all incoming and outgoing network traffic and apply security rules to block unauthorized access. Whether it’s preventing an intruder from entering your network or restricting access to certain websites, firewalls provide vital control over data flow and ensure only safe connections are allowed.
2. Antivirus and Anti-malware Software
These tools are essential in identifying and removing malicious software. They continuously scan systems for known threats and suspicious behavior. With regular updates, modern antivirus programs can detect even the newest threats. This technology helps prevent infections that could compromise files, applications, or entire systems.
3. Intrusion Detection Systems (IDS)
An IDS monitors a network or system for malicious activity or policy violations. When a threat is detected, it sends alerts to administrators, enabling them to take immediate action. IDS helps in identifying unusual behaviors that may indicate a cyberattack, such as repeated failed login attempts or unauthorized access to files.
4. Endpoint Protection
In today’s work environment, employees access company data from various devices—laptops, mobile phones, tablets, and even IoT devices. Endpoint protection secures each device connected to the network, ensuring that vulnerabilities in these endpoints don’t become entry points for hackers. This solution helps enforce security policies, manage device configurations, and detect threats at the device level.
5. Data Encryption
Encryption ensures that even if data is intercepted, it cannot be read or misused by unauthorized parties. Cyber Tech tools offer strong encryption protocols for data at rest and in transit, helping businesses protect sensitive information such as financial data, personal information, and proprietary business content.
6. Multi-Factor Authentication (MFA)
MFA adds an additional layer of security beyond just usernames and passwords. By requiring users to provide two or more verification factors—such as a fingerprint, a phone-based code, or a security token—organizations reduce the risk of unauthorized access due to stolen credentials.
7. Security Information and Event Management (SIEM)
SIEM solutions collect and analyze data from various security systems across an organization. They provide real-time insights into potential threats, streamline incident response, and help maintain compliance with regulatory standards. With automated alerts and detailed logs, SIEM tools are vital for detecting and responding to cyber incidents quickly.
Why Cyber Tech Integration Matters
Cybersecurity threats can have devastating consequences, including financial loss, legal issues, reputational damage, and loss of customer trust. By integrating modern Cyber Tech solutions, businesses can:
-
Proactively detect and respond to threats before they cause harm.
-
Reduce downtime caused by system infections or ransomware attacks.
-
Comply with industry regulations and standards such as GDPR, HIPAA, and PCI DSS.
-
Build trust with customers by ensuring that their data is protected.
-
Ensure business continuity, even in the event of a cyber incident.
Cybersecurity is not a one-time setup but an ongoing process. As hackers become more sophisticated, the tools and strategies used to defend against them must also evolve. Cyber Tech provides the flexibility and innovation needed to stay ahead of cybercriminals.
To dive deeper into how Cyber Tech defends against cyber threats, check out our blog on How Does Cyber Tech Protect You from Cyber Threats?
2. Improved Operational Efficiency
Cybersecurity today goes beyond just protecting sensitive data and digital assets—it plays a crucial role in enhancing a business’s overall operational efficiency. As organizations increasingly adopt advanced Cyber Tech solutions, they’re not only safeguarding their networks but also creating smoother, more reliable, and more productive workflows.
How Cyber Tech Contributes to Efficiency
Automated Threat Detection and Response
One of the biggest advantages of modern Cyber Tech is the ability to automate threat detection and response. With technologies like artificial intelligence (AI) and machine learning (ML), security tools can analyze vast amounts of data in real time to identify unusual activity or signs of a cyberattack. These systems can then automatically respond to threats—such as isolating infected systems, blocking malicious IP addresses, or alerting IT staff—without waiting for human intervention. This significantly shortens response times and minimizes the potential damage of cyber threats.
Reduced Downtime and Fewer Disruptions
Cyberattacks can lead to major downtime, which often results in financial losses, missed opportunities, and damage to brand reputation. By implementing robust cybersecurity measures, businesses reduce the likelihood and severity of such incidents. Cyber Tech solutions proactively prevent breaches and ensure that networks, applications, and systems remain operational even under threat. This means less time spent fixing issues and more time spent focusing on core business operations.
Simplified IT Management
Modern cybersecurity platforms often come with centralized dashboards and unified management systems. Solutions like Extended Detection and Response (XDR) and Security Information and Event Management (SIEM) integrate data from various endpoints, cloud platforms, and applications into a single interface. This allows IT teams to monitor, manage, and respond to incidents more effectively. By streamlining operations, reducing redundancy, and minimizing the complexity of managing multiple tools, businesses can maintain a stronger security posture without overwhelming their teams.
Resource Optimization
By reducing the number of security-related incidents and automating routine security tasks, Cyber Tech allows businesses to reallocate their human resources to higher-value activities. For example, instead of having security analysts spend hours sifting through alerts or running manual scans, they can focus on strategic initiatives like infrastructure upgrades or innovation projects. This not only improves employee productivity but also contributes to long-term business growth.
Compliance and Risk Management
Efficient cybersecurity tools also help organizations meet regulatory compliance requirements with greater ease. Many industries are governed by strict data protection laws, and failing to comply can result in hefty penalties. Cyber Tech solutions often come with built-in compliance features, automated reporting, and continuous monitoring, which simplify audits and ensure that companies stay on the right side of the law.
3. Enhanced Customer Trust and Satisfaction
In the digital age, customers are increasingly concerned about how businesses handle their personal information. Data breaches and leaks can severely damage a company’s reputation and erode trust. By integrating Cyber Tech, organizations can demonstrate a commitment to data protection and privacy, leading to enhanced customer trust.
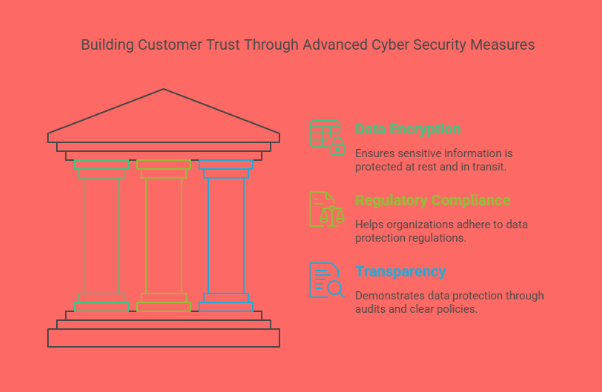
How Cyber Tech Builds Trust:
-
Data Encryption: Ensures that sensitive customer information is protected both at rest and during transmission.
-
Compliance with Regulations: Cyber Tech helps organizations comply with data protection regulations such as GDPR, HIPAA, and CCPA, ensuring that customer data is handled with care.
-
Transparency: Security measures like regular audits and clear privacy policies show customers that their data is being protected.
With robust Cyber Tech measures in place, customers can feel confident that their personal information is safe, which can lead to increased loyalty and improved customer retention.
4. Compliance with Industry Regulations
Every industry has specific regulations governing the protection of data, and non-compliance can result in hefty fines, legal action, and loss of reputation. Adopting Cyber Tech helps organizations stay compliant with these regulations, reducing the risk of legal penalties and enhancing credibility.
How Cyber Tech Ensures Compliance:
-
Automated Compliance Audits: Many Cyber Tech tools offer automated auditing capabilities that help businesses track and ensure compliance with industry standards and regulations.
-
Data Privacy: Cyber Tech solutions help businesses implement measures like data encryption, access control, and regular updates to ensure that they meet the privacy standards required by law.
-
Secure Data Storage: Ensures that data is stored securely and only accessible by authorized personnel, which is crucial for compliance with regulations like GDPR and HIPAA.
By integrating Cyber Tech, businesses can ensure they adhere to legal requirements while protecting both customer and organizational data.
5. Scalability and Future-Proofing Your Organization
As businesses grow, so do their cybersecurity needs. Cyber threats also evolve, making it essential for companies to adopt flexible, scalable cybersecurity solutions that can adapt to future challenges. Cyber Tech provides businesses with the tools they need to scale their security efforts alongside their growth.
How Cyber Tech Supports Scalability:
-
Cloud Security Solutions: Cloud-based security solutions offer scalability by allowing businesses to protect their data across multiple locations, devices, and platforms.
-
Flexible Cybersecurity Tools: Many Cyber Tech solutions, like XDR, are designed to scale as an organization grows, providing consistent protection regardless of the business's size or industry.
-
Integration with New Technologies: As new technologies (such as IoT, AI, and quantum computing) emerge, Cyber Tech tools can be integrated into these systems to ensure ongoing protection.
By investing in scalable Cyber Tech solutions, businesses can future-proof their cybersecurity measures, ensuring that they are always prepared for new challenges.
To learn more about how scalable Cyber Tech solutions work, check out our article on What Are the Latest Cyber Tech Trends in 2025?.
6. Cost-Effective Protection in the Long Run
For many businesses, the idea of investing in Cyber Tech can seem daunting at first—especially when budgets are tight and cybersecurity may not appear to be an immediate need. The initial cost of purchasing software, hardware, or even hiring cybersecurity professionals may appear high. However, this perception often changes when businesses fully understand the financial implications of a cyberattack and the long-term savings that Cyber Tech can offer.
Cyberattacks can be devastating, not just in terms of monetary loss, but also in terms of time, trust, and operations. Businesses that fall victim to data breaches, ransomware, or other cyber threats often face costly consequences such as operational downtime, data loss, reputational damage, customer attrition, and even legal fees related to compliance violations. These costs can add up quickly, far surpassing the upfront investment in cybersecurity solutions.
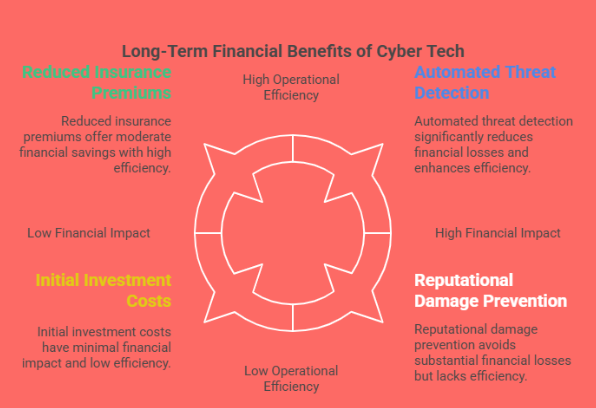
How Cyber Tech Saves Money:
1. Reduced Risk of Cyberattacks:
Cyber Tech plays a crucial role in preventing security breaches by detecting and blocking threats before they infiltrate systems. With real-time monitoring, advanced encryption, and multi-layered defenses, businesses can significantly reduce their vulnerability. Avoiding even a single cyber incident can save an organization thousands—or even millions—of dollars. The cost of recovering from a serious breach is often multiple times greater than the cost of prevention.
2. Increased Operational Efficiency:
Modern Cyber Tech solutions often include automated features that streamline threat detection and response. This automation minimizes the need for large, specialized IT security teams and allows businesses to operate more efficiently. With fewer manual processes, staff can focus on higher-value tasks while the system handles much of the day-to-day monitoring and incident response. This reduction in labor and improved workflow translates to tangible cost savings over time.
3. Lower Insurance Premiums:
Cyber insurance is becoming a standard part of many businesses’ risk management strategies. Insurers assess how well a company is protected before setting premium rates. Organizations that have invested in advanced Cyber Tech—like firewalls, intrusion prevention systems, and employee training—are often seen as lower risks. As a result, they may qualify for lower premiums or additional coverage benefits, contributing further to long-term savings.
4. Protection of Business Reputation:
Although harder to quantify, reputational damage from a cyberattack can result in lost customers, decreased trust, and reduced revenue. Cyber Tech helps maintain a company's reputation by demonstrating a proactive approach to security. Customers and partners are more likely to trust businesses that prioritize data protection, which can lead to sustained business growth and stability.
Conclusion
Integrating Cyber Tech into your organization offers a multitude of benefits, from enhanced protection against cyber threats and improved operational efficiency to increased customer trust and compliance with industry regulations. By adopting advanced Cyber Tech solutions, businesses can not only safeguard their digital assets but also position themselves for long-term growth and success.
At ACSMI, we understand the critical role that technology plays in today’s business environment. That’s why we remain committed to providing our clients with the tools and certifications they need to thrive in an increasingly digital and cybersecurity-driven world.
FAQs
1. What are the main benefits of integrating Cyber Tech into a business?
Integrating Cyber Tech into a business offers several key benefits, including enhanced protection against cyber threats, improved operational efficiency, and greater compliance with industry regulations. It also boosts customer trust, reduces downtime, and provides scalable security solutions that grow with the business. Ultimately, Cyber Tech helps businesses reduce risks and improve overall productivity.
2. How does Cyber Tech improve operational efficiency in organizations?
Cyber Tech improves operational efficiency by automating threat detection and response, reducing the time spent on manual security tasks. With tools like XDR (Extended Detection and Response) and AI-powered systems, organizations can monitor security events in real-time and respond quickly to incidents. This reduces downtime, minimizes disruptions, and allows businesses to focus on growth and innovation.
3. How can Cyber Tech help businesses build customer trust?
Cyber Tech helps businesses build customer trust by ensuring that sensitive data is protected through encryption, secure access controls, and continuous monitoring. By complying with privacy regulations such as GDPR and HIPAA, businesses can demonstrate to customers that their personal information is safe. This transparency and security can lead to stronger customer relationships and greater loyalty.
4. How does Cyber Tech help organizations stay compliant with regulations?
Cyber Tech solutions help organizations stay compliant with industry regulations by providing automated tools for monitoring, reporting, and managing data protection. Many Cyber Tech tools are designed to align with compliance standards like GDPR, HIPAA, and CCPA, ensuring that businesses meet the necessary requirements. This reduces the risk of legal penalties and ensures that sensitive data is handled securely.
5. Can Cyber Tech solutions scale as an organization grows?
Yes, Cyber Tech solutions are designed to be scalable. As businesses grow, their cybersecurity needs become more complex. Cloud-based security tools, XDR, and multi-cloud security platforms allow organizations to expand their security infrastructure without major disruptions. These tools can adapt to new technologies and larger data volumes, ensuring continuous protection as the business evolves.

Leave a Reply