As cyber threats continue to grow in sophistication and frequency, businesses must invest in Cyber Tech solutions to protect their digital assets and ensure the security of their networks, systems, and data. However, with so many different security tools available, choosing the right Cyber Tech solutions can be overwhelming.
The right solution will depend on several factors, including the size of your organization, the type of data you handle, your budget, and your overall cybersecurity strategy. In this blog, we will guide you through the process of choosing the best Cyber Tech solutions for your needs. From evaluating different tools to considering the specific requirements of your business, this guide will help you make an informed decision.
1. Understand Your Cybersecurity Needs
Choosing the best Cyber Tech solutions starts with a deep understanding of your organization’s unique cybersecurity needs. Cybersecurity is not a one-size-fits-all approach. Different businesses, based on their size, industry, and the type of data they handle, face varying levels and types of cyber threats. Identifying these factors early in the decision-making process will help you select the most effective security solutions for your organization.
Size of Your Organization
The size of your organization plays a significant role in determining your cybersecurity requirements.
-
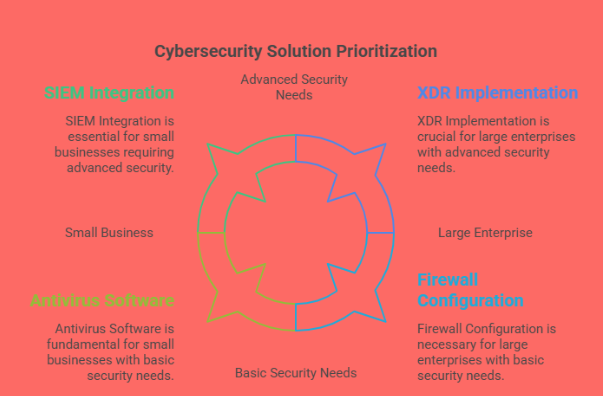
Small businesses often operate with limited budgets and smaller IT teams. They typically benefit from fundamental security tools like antivirus software, secure Wi-Fi routers, firewalls, and regular system updates. Many cyber attackers target small businesses precisely because they’re less likely to have robust protections in place.
-
Medium to large enterprises, on the other hand, require more advanced security systems. These organizations often manage large volumes of sensitive data and have a more complex IT infrastructure. In such cases, solutions like XDR (Extended Detection and Response), SIEM (Security Information and Event Management), endpoint detection, and threat intelligence platforms become essential. These tools offer real-time monitoring, data correlation, and faster incident response capabilities.
Industry-Specific Risks
Each industry has its own set of cybersecurity challenges and regulatory requirements.
-
Healthcare providers need to adhere to strict privacy standards such as HIPAA, which requires safeguarding electronic health records (EHRs) and other patient information.
-
Financial institutions must protect financial transactions, account data, and comply with regulations like PCI-DSS or SOX.
-
Retailers handling online transactions face threats like credit card fraud, phishing scams, and malware attacks.
Understanding these specific risks will guide you in selecting a solution that not only protects your assets but also ensures compliance with industry regulations.
Type of Data Handled
The kind of data your business collects, processes, or stores should also guide your cybersecurity planning.
-
If your company deals with personal identification information (PII), such as customer names, addresses, or Social Security numbers, then data encryption, secure storage solutions, and access control are critical.
-
Organizations that work with intellectual property or confidential business information should prioritize advanced threat protection and endpoint security to prevent corporate espionage or data leaks.
-
For businesses offering e-commerce services, protecting customer payment data and preventing transaction fraud are top concerns.
Tailoring Solutions to Your Needs
By thoroughly assessing your organization’s specific cybersecurity landscape, you can avoid over-investing in unnecessary tools or under-protecting your critical assets. A tailored solution ensures efficient allocation of your cybersecurity budget and resources while maximizing protection and compliance. Whether you’re just starting with basic antivirus software or need a full suite of enterprise-level cybersecurity tools, understanding your needs is the crucial first step toward a safer digital environment.
2. Evaluate Different Cyber Tech Tools
Once you have a clear understanding of your cybersecurity needs, it's time to evaluate the different Cyber Tech tools available in the market. Some of the most common Cyber Tech solutions include:
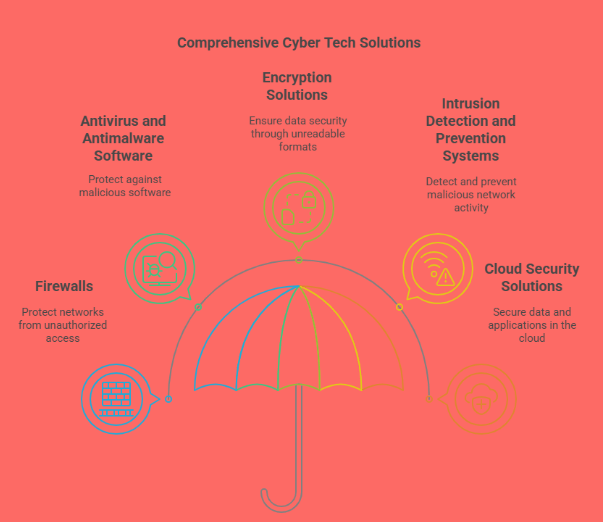
1. Firewalls
Firewalls are essential for protecting your network from unauthorized access. They monitor incoming and outgoing traffic based on predetermined security rules. When selecting a firewall, consider whether you need a next-generation firewall (NGFW), which offers advanced features such as deep packet inspection, intrusion prevention, and application control.
2. Antivirus and Antimalware Software
Antivirus and antimalware software help protect your organization from viruses, worms, ransomware, and other malicious software. These tools scan files, emails, and websites for malware and can quarantine or remove threats. Be sure to choose a solution that offers real-time scanning, automatic updates, and a low false-positive rate.
3. Encryption Solutions
Data encryption ensures that sensitive information is stored in an unreadable format, protecting it from unauthorized access. Encryption is especially important for businesses that handle personal or financial data. Look for encryption solutions that comply with industry standards, such as AES encryption, and ensure that the encryption is applied both at rest and in transit.
4. Intrusion Detection and Prevention Systems (IDPS)
An IDPS helps detect and respond to malicious activity in your network. It can identify unusual network traffic patterns or signs of a cyberattack and provide real-time alerts. Some IDPS solutions also have automatic blocking features to prevent an attack from spreading.
5. Cloud Security Solutions
As more businesses migrate to the cloud, the need for cloud security has grown. Cloud security solutions protect data and applications hosted in the cloud. When evaluating cloud security tools, look for features like data encryption, identity management, and multi-factor authentication (MFA).
For a deeper dive into cloud security, check out our blog on How Cyber Tech Protects Your Cloud-Based Data.
3. Consider Scalability and Flexibility
Your business needs will evolve over time, so it’s important to choose Cyber Tech solutions that can scale with your growth. Whether you're expanding to new locations, adopting new technologies, or dealing with increasing amounts of data, your cybersecurity solutions must be flexible enough to accommodate these changes.
Questions to Ask About Scalability:
-
Can the solution handle growing amounts of data or traffic without sacrificing performance?
-
Does the solution integrate well with new technologies or tools that you plan to adopt in the future?
-
Can the solution be easily upgraded or customized to meet your evolving security needs?
Scalability is especially important for organizations that anticipate significant growth or rapid changes in their IT infrastructure.
4. Evaluate Vendor Reputation and Support
The reputation of the Cyber Tech vendor is a critical factor in selecting the right solution. Before purchasing any cybersecurity product, research the vendor’s reputation for providing reliable solutions, excellent customer support, and ongoing product updates.
What to Look for in a Vendor:
-
Customer Reviews and Case Studies: Look for reviews from other businesses in your industry to see if the vendor’s solution is effective at addressing similar challenges.
-
Support Options: Choose a vendor that offers robust support options, including 24/7 customer service, online resources, and dedicated support teams.
-
Regular Updates: Cyber threats evolve constantly, so it’s essential to choose a vendor that provides regular updates to protect against new threats and vulnerabilities.
By selecting a vendor with a strong reputation and excellent support, you can ensure that your business is protected for the long term.
5. Consider Cost and Return on Investment (ROI)
Cybersecurity is an investment, and while it’s important to find the right solution, it’s equally important to ensure that you are getting value for your money. Consider both the upfront cost of purchasing the solution and the ongoing maintenance costs.
Questions to Ask About Cost:
-
What is the total cost of ownership (TCO) of the solution, including licensing, installation, and ongoing updates?
-
Does the solution provide a clear return on investment (ROI) by reducing the risk of data breaches, downtime, and lost revenue?
-
Are there any hidden costs, such as additional hardware or specialized personnel needed to maintain the system?
While it’s tempting to choose the cheapest option, investing in high-quality Cyber Tech solutions will ultimately save your business money in the long run by reducing the risk of costly cyber incidents.
Conclusion: Making the Right Choice for Your Business
Choosing the best Cyber Tech solutions for your organization is crucial to maintaining a strong cybersecurity posture. By understanding your specific needs, evaluating different tools, considering scalability and vendor support, and weighing the cost against potential ROI, you can make an informed decision that protects your business from the growing threat of cybercrime.
At ACSMI, we understand the importance of cybersecurity in the digital age. Our team is committed to providing you with the knowledge and tools needed to stay ahead of the latest Cyber Tech trends and ensure the safety of your organization’s digital assets.
FAQs
1. What are the most important factors to consider when choosing Cyber Tech solutions?
When choosing Cyber Tech solutions, it’s essential to consider your organization’s specific cybersecurity needs, scalability, the reputation of the vendor, cost, and the flexibility of the solution. Evaluate whether the solution can grow with your business, whether it addresses your specific security concerns, and if the vendor offers strong customer support and regular updates.
2. How can I determine the best Cyber Tech solution for my business size?
The best Cyber Tech solution for your business size depends on your organization's needs and resources. Small businesses may need basic solutions like antivirus software, firewalls, and endpoint protection. Larger businesses often require more comprehensive solutions like XDR, SIEM, or cloud security platforms that can scale as the organization grows and handle complex IT environments.
3. What is the role of scalability when selecting Cyber Tech solutions?
Scalability is crucial when selecting Cyber Tech solutions because as your business grows, your cybersecurity needs will evolve. Scalable solutions ensure that your security infrastructure can handle increasing amounts of data, traffic, and devices without compromising performance or protection. Look for solutions that can adapt to new technologies and expand as your business develops.
4. How do I evaluate the reputation of a Cyber Tech vendor?
To evaluate the reputation of a Cyber Tech vendor, research customer reviews, case studies, and industry certifications. Look for vendors with a proven track record of delivering reliable and effective cybersecurity solutions. Check if the vendor provides 24/7 support, regular software updates, and has a strong security culture. Reputable vendors also offer transparent pricing and clear service level agreements (SLAs).
5. What should I consider about cost when choosing Cyber Tech solutions?
When considering cost, think beyond the initial purchase price. Factor in the total cost of ownership (TCO), which includes licensing, maintenance, updates, and potential hidden costs such as the need for specialized staff. It’s essential to balance cost with the solution's ability to reduce risks and provide long-term value. High-quality Cyber Tech solutions may have a higher upfront cost but can save money in the long run by preventing costly cyberattacks and minimizing downtime.

Leave a Reply