As the digital landscape evolves, so too does the way businesses manage security. From cloud computing to artificial intelligence (AI), security management is undergoing a significant transformation. In 2025, emerging trends in security management are set to redefine how organizations protect their assets, data, and people.
Staying ahead of these trends is crucial for businesses to ensure they have the tools and strategies in place to defend against increasingly sophisticated threats. In this blog, we will explore the key security management trends emerging for 2025 and how they are shaping the future of organizational security.
For more on the foundations of security management, check out our blog on how security management affects compliance.
1. The Rise of AI and Machine Learning in Security
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the way security systems are managed and executed. These advanced technologies are no longer concepts of the future—they are actively shaping the present and are expected to play an even greater role in security management by 2025 and beyond. As cyber threats become more sophisticated, traditional security measures are no longer sufficient. AI and ML offer intelligent, data-driven solutions that empower organizations to stay one step ahead of potential threats.
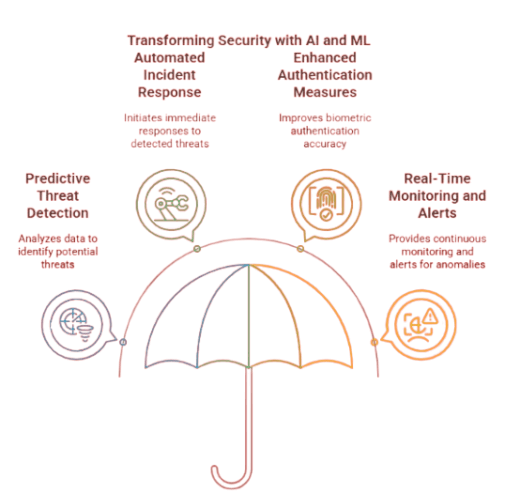
Key Ways AI and ML Are Impacting Security:
1. Predictive Threat Detection
One of the most significant contributions of AI and ML in the security landscape is their ability to perform predictive threat detection. Unlike traditional systems that react to threats after they occur, AI and ML can analyze vast amounts of historical and real-time data to identify unusual patterns or anomalies that may indicate an impending threat. By continuously learning from network activity and user behavior, these systems can flag suspicious behavior and alert security teams before any real damage is done. This proactive approach is helping organizations reduce their vulnerability and strengthen their overall cybersecurity posture.
2. Automated Incident Response
Another critical benefit of incorporating AI in security is automated incident response. When a threat is detected, AI-powered systems can initiate immediate responses such as isolating affected systems, blocking malicious IP addresses, or activating containment protocols—all without human intervention. This not only reduces response time significantly but also minimizes the impact of the breach. In many cases, the system can contain or mitigate the threat before it spreads, which is essential in fast-moving cyberattacks like ransomware or phishing.
3. Enhanced Authentication Measures
AI is also driving advancements in biometric authentication systems. Facial recognition, iris scanning, and fingerprint analysis are becoming more accurate and harder to spoof thanks to AI algorithms. These technologies are being used to replace or enhance traditional password-based systems, which are often vulnerable to attacks. With AI-driven authentication, organizations can implement multi-factor identification processes that offer both security and convenience. In high-security environments, these methods add an essential layer of protection against unauthorized access.
4. Real-Time Monitoring and Alerts
AI and ML systems can monitor security environments 24/7 with minimal human oversight. They can scan for vulnerabilities, track behavior patterns, and provide real-time alerts when something seems off. This allows security teams to take action immediately, rather than discovering breaches hours or days later. These intelligent systems learn over time, meaning their accuracy and efficiency improve the more they are used.
Looking Ahead
As we move deeper into the digital age, the adoption of AI and ML in security management will only grow. Organizations across all industries—from healthcare and finance to retail and government—are realizing the importance of investing in intelligent technologies to protect their assets. By automating routine tasks, improving detection capabilities, and enhancing response times, AI and ML are not just supporting security efforts—they’re transforming them. For businesses looking to stay secure in an increasingly complex threat landscape, embracing AI and ML is no longer optional—it’s essential.
2. Cloud Security and the Shift to Hybrid Environments
As more businesses migrate to the cloud, securing these environments has become a top priority. With the rapid adoption of cloud technologies, companies are transitioning from traditional on-premises infrastructures to hybrid environments that combine both cloud-based and on-premises resources. This shift has created a pressing need for robust cloud security solutions to safeguard data, ensure business continuity, and maintain compliance with various regulations. By 2025, cloud security will continue to be a major focus, with an increased emphasis on securing hybrid environments and enhancing protection across diverse infrastructure platforms.
The Impact of Cloud Security Trends:
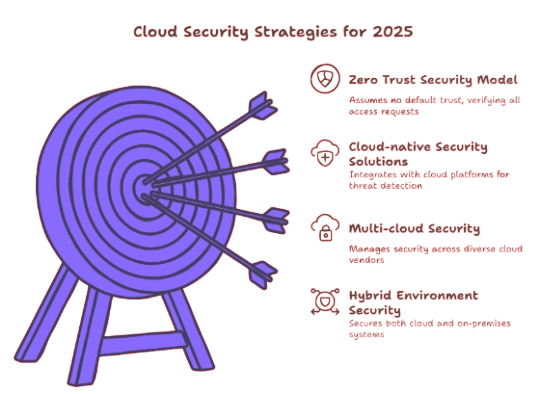
Zero Trust Security Model
The Zero Trust security model is becoming a cornerstone of cloud security strategies. Unlike traditional security models, which implicitly trust users and devices within the organization’s network, Zero Trust assumes that no user or device, inside or outside the organization, should be trusted by default. Every request for access is verified and validated before being granted, reducing the risk of unauthorized access and insider threats. By 2025, the implementation of Zero Trust principles will be widespread across cloud infrastructures, offering more robust protection against sophisticated cyberattacks, particularly as organizations adopt hybrid and multi-cloud environments. The model focuses on continuous authentication and micro-segmentation, which are essential for preventing lateral movement within networks and ensuring that sensitive data remains secure.
Cloud-native Security Solutions
With the increasing use of cloud environments, organizations are expected to adopt cloud-native security solutions designed specifically for cloud environments. These tools are built to integrate seamlessly with cloud platforms, enabling real-time threat detection, automated responses, and continuous monitoring of cloud resources. Unlike traditional security solutions that were designed for on-premises systems, cloud-native tools are optimized for the dynamic, scalable nature of cloud infrastructures. These tools provide advanced threat protection, leveraging artificial intelligence (AI) and machine learning (ML) to detect anomalies and vulnerabilities that could pose a risk to the organization's data and applications. By 2025, the demand for cloud-native security solutions will significantly rise as more organizations move their critical workloads to the cloud, necessitating tools that can protect and scale with their evolving needs.
Multi-cloud Security
As businesses increasingly adopt multiple cloud service providers to meet specific needs, managing security across different platforms will become more complex. Multi-cloud environments, where organizations use services from multiple cloud vendors such as AWS, Azure, and Google Cloud, present unique security challenges. With each cloud provider offering its own set of tools, features, and security protocols, businesses will need new tools and strategies to manage security across these diverse platforms. The ability to maintain control, ensure visibility, and enforce consistent security policies across all environments will be critical. In response to this growing challenge, specialized multi-cloud security solutions are being developed that offer unified visibility, integrated threat intelligence, and automated policy enforcement, ensuring businesses can protect their data and applications across all cloud environments effectively.
The Future of Cloud Security
The future of cloud security lies in a combination of more advanced tools, innovative strategies, and a proactive security mindset. By 2025, as cloud environments become more ubiquitous and hybrid models dominate, businesses will face a critical need to secure sensitive data and maintain compliance with regulatory requirements. The ability to effectively manage security in hybrid environments, where on-premises and cloud-based infrastructure intersect, will be a key determinant of success. By adopting the latest cloud security trends, such as the Zero Trust model, cloud-native security solutions, and multi-cloud security strategies, organizations can better safeguard their digital assets, minimize vulnerabilities, and ensure that their business operations remain secure in an increasingly complex cloud landscape.
Cloud security solutions are becoming more robust, and by 2025, the ability to effectively manage hybrid environments will be critical to protecting sensitive data and maintaining compliance.
To learn more about cloud security, visit our blog on how to choose the right security management tools.
3. Privacy-First Security Practices
As concerns around data privacy continue to escalate, privacy-first security practices have become a central focus for organizations worldwide. With growing public awareness and the introduction of more stringent regulations, businesses in 2025 will be expected to integrate privacy into every aspect of their security management systems. This shift reflects a broader recognition that protecting personal data is not only a regulatory requirement but also an essential component of building trust with customers and stakeholders.
The increasing need to safeguard sensitive information has brought about significant changes in how businesses approach data protection. In the years ahead, organizations will need to prioritize privacy alongside traditional security measures, ensuring that they address both external threats and the internal handling of sensitive data. Let’s explore the key privacy trends businesses should be aware of as they navigate the future of security management.
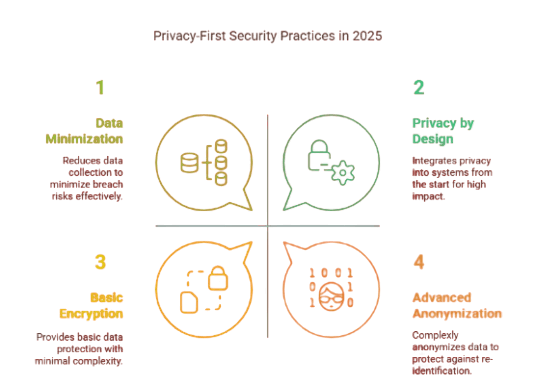
Privacy Trends to Watch:
Data Minimization: Reducing Risk Through Less Data Collection
One of the key principles driving privacy-first security practices is data minimization. This principle dictates that businesses should only collect the minimum amount of personal information necessary for a given purpose. By reducing the amount of sensitive data stored, businesses can limit the scope of potential breaches and reduce their exposure to data theft or misuse.
In 2025, this approach will become a standard in security management strategies. With the rapid rise of data breaches and cyberattacks, organizations will be under increasing pressure to reevaluate their data collection practices. The less data they store, the less there is to steal, which inherently reduces the risk of sensitive information being compromised. This approach is also crucial for ensuring compliance with global data protection regulations such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA), which emphasize the need for organizations to protect personal information by collecting only what is necessary.
Data Anonymization and Encryption: Safeguarding Personal Data
As businesses handle more personal information, the use of data anonymization and encryption will become essential to meet regulatory requirements and ensure the privacy of customers. Data anonymization involves altering data in such a way that it can no longer be linked to an individual, even if it falls into the wrong hands. This process helps businesses minimize the impact of a data breach by ensuring that stolen information cannot be traced back to a specific person.
On the other hand, encryption ensures that personal data is transformed into an unreadable format, protecting it from unauthorized access. Whether in transit or at rest, encrypted data remains protected, even if intercepted or accessed by malicious actors. Both of these techniques will be increasingly adopted by businesses as core components of their security management systems, ensuring that personal data is not only kept private but also secured against potential threats.
These practices are becoming essential to comply with evolving data protection laws and consumer expectations. GDPR, CCPA, and similar regulations demand that businesses take appropriate steps to protect personal data. Failure to do so can result in significant fines and damage to an organization’s reputation.
Privacy by Design: Integrating Privacy into Systems from the Start
In 2025, privacy by design will become a foundational approach for all security solutions. This concept involves integrating privacy features into systems and processes from the ground up, rather than bolting them on as an afterthought. By adopting a privacy-by-design approach, businesses can ensure that privacy protections are not just an add-on but an inherent part of their operations and technological infrastructure.
This proactive approach is critical in a landscape where privacy laws are becoming stricter, and consumers are demanding more control over their personal data. Privacy by design ensures that privacy is embedded in the development of products, services, and processes, making it easier for organizations to comply with legal obligations and create products that customers trust.
The Path Ahead: Meeting the Privacy Demands of 2025
As privacy laws continue to tighten, businesses will face increasing pressure to adopt comprehensive privacy-first security practices. These measures will help organizations safeguard customer data and comply with evolving regulations. Moreover, the growing demand for transparency and control over personal data will make privacy-first practices not just a legal necessity but a competitive advantage. Consumers are more informed than ever, and their expectations around privacy will shape the future of business security.
By embracing principles like data minimization, anonymization, encryption, and privacy by design, businesses will be better equipped to manage the challenges of 2025 and beyond. Those that prioritize privacy-first security practices will build stronger relationships with customers and stakeholders, ensuring long-term success in an increasingly privacy-conscious world.
As privacy laws become stricter and consumers demand greater control over their personal data, businesses will need to enhance their security management systems to meet these new challenges.
4. The Expansion of IoT Security
The Internet of Things (IoT) continues to expand, with more devices being connected to the internet every day. This creates new opportunities but also introduces significant security risks. In 2025, securing IoT devices and networks will be a major priority in security management.
Key IoT Security Considerations:
-
Device Authentication and Authorization: Ensuring that IoT devices are properly authenticated and authorized before being granted network access will be critical in preventing unauthorized access.
-
Network Segmentation: IoT devices will need to be segmented from critical network infrastructure to prevent a compromised device from spreading malware or other attacks across the network.
-
End-to-End Encryption: Ensuring that data transmitted between IoT devices is encrypted will protect it from interception and unauthorized access.
With the rapid adoption of IoT devices, organizations must stay ahead of emerging threats by implementing robust security measures for their IoT ecosystems.
5. The Emergence of Privacy-Enhancing Technologies (PETs)
As businesses strive to comply with evolving privacy regulations, Privacy-Enhancing Technologies (PETs) will become a key trend in security management by 2025. PETs are designed to protect personal data while still allowing businesses to perform necessary data analysis and processing.
Examples of Privacy-Enhancing Technologies:
-
Homomorphic Encryption: This allows data to be encrypted and processed without needing to decrypt it, ensuring data privacy while enabling analysis.
-
Secure Multi-Party Computation (SMPC): This technology allows multiple parties to compute data without sharing sensitive information with each other.
-
Federated Learning: A machine learning technique that allows data to be trained locally on a device, reducing the need for centralized data storage and enhancing privacy.
By integrating PETs into their security frameworks, organizations can ensure they are in compliance with privacy regulations while still utilizing data for business purposes.
6. Enhanced Security for Remote Workforces
As remote work continues to be the norm for many businesses, securing remote workforces has become a major aspect of security management. In 2025, we can expect an increase in security solutions designed specifically for remote and hybrid work environments.
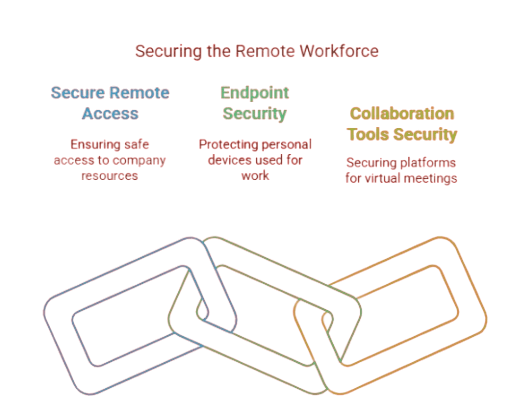
Key Security Trends for Remote Work:
-
Secure Remote Access: Tools like Virtual Private Networks (VPNs) and Zero Trust architecture will become standard to ensure secure remote access to company resources.
-
Endpoint Security: Securing personal devices, including laptops and smartphones, that employees use to access business systems will be essential to preventing breaches.
-
Collaboration Tools Security: As remote work increases reliance on collaboration tools, these platforms will need to be secured to protect sensitive data shared during virtual meetings and discussions.
Organizations will need to implement a comprehensive approach to securing remote work environments, ensuring employees have secure access to the tools and data they need without compromising security.
Conclusion
As we move into 2025, the landscape of security management continues to evolve. From AI and machine learning enhancing threat detection to new privacy practices and cloud security strategies, organizations must stay ahead of emerging trends to effectively protect their assets, data, and workforce. Implementing the latest security innovations is not just about staying compliant; it’s about building a resilient security posture that can withstand the challenges of an increasingly connected and data-driven world.
At ACSMI, we understand the importance of staying secure in an ever-changing environment. We offer medical coding and billing certifications to ensure that professionals have the expertise to safeguard sensitive data in compliance with legal standards. We also provide a variety of snacks online to keep your team energized and productive as they work to implement the latest security measures.
FAQs
How does AI help in security management?
AI and machine learning improve threat detection, automate responses to incidents, and enhance authentication through predictive analytics.
What are the key privacy-enhancing technologies?
Technologies such as homomorphic encryption, secure multi-party computation, and federated learning are emerging to ensure data privacy while enabling business operations.
How do IoT devices impact security management?
IoT devices create new vulnerabilities, making it essential to implement measures like device authentication, encryption, and network segmentation.
What is the Zero Trust security model?
The Zero Trust model assumes that no one—inside or outside the organization—should be trusted by default. It requires continuous verification and authentication of every user and device.
What trends should organizations focus on for securing remote work?
Focus on secure remote access, endpoint security, and collaboration tools security to ensure that remote workforces can securely access company resources.

Leave a Reply