In today’s digital age, businesses are increasingly dependent on technology to operate efficiently, connect with customers, and protect sensitive data. However, as the use of digital technologies grows, so do the risks associated with cyber threats. This is where Cyber Tech comes into play.
Cyber Tech refers to the set of technologies, tools, and solutions designed to protect organizations from cyberattacks, data breaches, and other security risks. It encompasses a wide range of services, from network protection and data encryption to artificial intelligence-driven threat detection and cybersecurity infrastructure. Whether you run a small startup or a large corporation, Cyber Tech is essential to safeguard your business against the evolving landscape of cyber threats.
In this blog, we will explore what Cyber Tech is, its importance for businesses, and how implementing Cyber Tech solutions can significantly enhance the security, efficiency, and profitability of your organization.
What is Cyber Tech?
Cyber Tech, short for Cybersecurity Technology, is a broad and essential field that focuses on protecting digital systems, networks, and data from unauthorized access, attacks, and damage. As our reliance on technology increases, so does the need for robust cyber defenses. Cyber Tech plays a critical role in both personal and organizational security, helping individuals, companies, and governments protect their digital infrastructure from a wide range of cyber threats.
At its core, Cyber Tech involves a combination of tools, techniques, and strategies that are designed to secure information systems. These technologies work together to maintain the confidentiality, integrity, and availability of data—three of the most important principles in cybersecurity. Whether it’s preventing data breaches, securing network connections, or detecting suspicious activity, Cyber Tech provides the necessary framework to build a safer digital environment.
Here are some of the key components and functions of Cyber Tech:
1. Network Security
Network security involves protecting internal computer networks from unauthorized access, misuse, or theft. This includes implementing firewalls, virtual private networks (VPNs), and intrusion detection systems that monitor and control incoming and outgoing traffic. By securing networks, organizations can reduce the risk of hackers or malware infiltrating their systems.
2. Data Encryption
Encryption is a method used to protect sensitive data by converting it into a code that is unreadable to anyone without the proper decryption key. This ensures that even if the data is intercepted, it remains secure and inaccessible to unauthorized users. Encryption is commonly used in email communication, online banking, and data storage solutions.
3. Threat Detection and Prevention
Cyber Tech relies heavily on artificial intelligence (AI) and machine learning (ML) to monitor systems in real-time and identify potential threats. These technologies can detect unusual patterns of behavior, flag malicious activities, and take preventive measures automatically. Early detection of threats significantly reduces the risk of serious damage to digital assets.
4. Cyber Defense Systems
These systems consist of a wide array of security measures, such as antivirus software, firewalls, endpoint protection, and security protocols. Together, they form a multilayered defense strategy that protects against viruses, phishing attacks, ransomware, and other types of cyberattacks. Businesses of all sizes benefit from deploying comprehensive cyber defense mechanisms to keep their data and operations secure.
5. Access Control and Authentication
Controlling who has access to information and systems is another crucial aspect of Cyber Tech. Tools like multi-factor authentication (MFA), biometrics, and secure password management help ensure that only authorized individuals can access certain areas of a system.
By implementing Cyber Tech solutions, businesses can strengthen their security posture, build trust with customers, and comply with industry regulations. In an age where cyber threats are constantly evolving, investing in Cyber Tech is not just a smart decision—it’s a necessary one.
Why is Cyber Tech Important for Businesses?
With the increasing number of cyberattacks targeting businesses, the importance of Cyber Tech cannot be overstated. According to recent studies, cybercrime is expected to cause global damages of over $10.5 trillion annually by 2025. This staggering number highlights the urgent need for businesses to adopt Cyber Tech solutions that can defend against both internal and external threats.
Here are several reasons why Cyber Tech is crucial for businesses:
1. Protection Against Cyberattacks
Every business, whether it’s a small startup or a multinational corporation, is vulnerable to cyberattacks. Cyber Tech helps defend against a wide variety of cyber threats such as phishing attacks, malware, ransomware, and denial-of-service attacks. With the right tools, businesses can detect and respond to these threats in real-time, preventing them from causing significant damage.
Internal linking: If you're looking to explore how to protect your business from cyberattacks, check out our guide on How Does Cyber Tech Protect You From Cyber Threats?.
2. Safeguarding Customer Data
In today’s data-driven world, customer data is one of the most valuable assets for businesses. A data breach can result in the loss of sensitive customer information, leading to legal consequences and loss of trust. Cyber Tech solutions such as encryption, secure data storage, and compliance with privacy regulations like GDPR ensure that customer data is protected at all times.
3. Ensuring Business Continuity
A successful cyberattack can disrupt business operations, resulting in downtime, loss of productivity, and revenue. By adopting Cyber Tech, businesses can ensure that they have robust backup systems, disaster recovery plans, and real-time monitoring in place to minimize the impact of cyber incidents on business continuity.
4. Enhancing Compliance with Regulations
In today’s regulatory environment, businesses are required to comply with various data protection laws and industry standards. Cyber Tech tools help organizations meet regulatory requirements such as GDPR, HIPAA, and PCI-DSS, avoiding costly fines and penalties. By implementing security measures like secure data storage and encrypted communications, businesses can stay compliant and avoid legal troubles.
The Core Components of Cyber Tech for Businesses
As the digital landscape continues to evolve, businesses are increasingly reliant on Cyber Tech to safeguard their digital assets and maintain operational continuity. Cybersecurity technologies play a crucial role in protecting against data breaches, cyberattacks, and other digital threats. Below are the core components every business should consider when building a robust cybersecurity framework.
1. Firewall Protection
A firewall is often the first line of defense in a business's cybersecurity strategy. Acting as a shield between the internal network and untrusted external networks (like the internet), firewalls monitor and regulate incoming and outgoing traffic based on predetermined security rules. This ensures that only authorized users and safe data packets are allowed to pass through, effectively reducing the risk of cyber intrusions.
Firewalls can be hardware-based, software-based, or a combination of both. Modern firewalls also offer advanced features like deep packet inspection, virtual private network (VPN) support, and application-layer filtering. Businesses of all sizes, whether startups or large enterprises, benefit significantly from implementing robust firewall protection.
2. Antivirus and Antimalware Software
Antivirus and antimalware solutions are critical for defending against a wide range of malicious software, including viruses, worms, trojans, ransomware, and spyware. These tools work by scanning files, programs, and system memory for known threats and suspicious behavior. Once detected, they quarantine or remove the harmful files before they can cause damage.
With cyber threats evolving constantly, modern antivirus software uses machine learning and heuristic analysis to identify previously unknown threats. Regular updates and scans are essential to ensure comprehensive protection. For businesses, using enterprise-grade antivirus solutions across all endpoints—desktops, laptops, servers, and mobile devices—is crucial for maintaining network integrity and minimizing downtime.
3. Encryption Solutions
Encryption is the process of converting data into a secure format that is unreadable without the proper decryption key. It's an essential component of Cyber Tech that protects sensitive data both at rest and in transit. From customer records and financial transactions to intellectual property and confidential communications, encryption ensures that even if data is intercepted or stolen, it remains useless to unauthorized parties.
Cybersecurity encryption solutions include technologies like Secure Sockets Layer (SSL) for websites, email encryption tools, and full-disk encryption for devices. Implementing encryption across your digital infrastructure not only enhances data privacy but also helps in regulatory compliance with laws such as GDPR, HIPAA, and PCI-DSS.
If you want to learn more about how encryption works, check out our article on The Benefits of Data Encryption in Cyber Tech.
4. Intrusion Detection and Prevention Systems (IDPS)
An Intrusion Detection and Prevention System (IDPS) is a cybersecurity tool designed to monitor network traffic for suspicious behavior or known attack patterns. While intrusion detection systems (IDS) alert administrators to potential threats, intrusion prevention systems (IPS) take it a step further by actively blocking or mitigating the threat.
These systems can identify anomalies in user behavior, detect brute-force attacks, flag unusual network activity, and even prevent unauthorized access attempts. IDPS solutions are especially valuable in real-time threat response, allowing businesses to react quickly to cyber incidents before they escalate.
The Growing Role of Artificial Intelligence in Cyber Tech
Artificial Intelligence (AI) is quickly becoming a cornerstone of modern cybersecurity efforts, transforming how organizations defend themselves against an ever-evolving digital threat landscape. With cyberattacks growing in frequency, complexity, and sophistication, traditional cybersecurity methods are no longer sufficient on their own. AI introduces a new level of intelligence, speed, and adaptability that empowers cyber professionals to stay ahead of potential threats.
AI is not just a buzzword in the tech industry—it is a practical and powerful tool reshaping the future of cyber tech. AI-powered cybersecurity solutions can process vast amounts of data at lightning speed, identify patterns that might otherwise go unnoticed, and learn from past incidents to better predict and prevent future threats. As cyber criminals use more advanced technologies, AI offers a critical advantage in defending digital assets.
Let’s explore some of the key ways AI is shaping cybersecurity and enhancing the overall strength and reliability of digital defenses.
Threat Intelligence: Predicting and Identifying Emerging Threats
One of the most valuable contributions of AI in cyber tech is its ability to support threat intelligence. By continuously analyzing data from millions of sources across the globe—such as logs, network activity, user behavior, and threat databases—AI systems can detect patterns and signals that may indicate a cyber threat.
Machine learning algorithms, a subset of AI, can evaluate vast datasets to recognize subtle anomalies and unusual patterns that humans might miss. This allows cybersecurity teams to detect and prepare for new types of malware, phishing attacks, ransomware variants, and zero-day exploits even before they cause harm. The proactive nature of AI-based threat intelligence significantly reduces response times and improves an organization’s security posture.
AI also supports predictive analytics, which uses historical and real-time data to forecast future attacks. These predictions help organizations prioritize their defenses, patch vulnerabilities promptly, and strengthen weak points in their networks before they are exploited.
Automation: Freeing Up Human Resources for Strategic Tasks
Another significant benefit of AI in cybersecurity is automation. Many cybersecurity tasks are repetitive and time-consuming, such as scanning for vulnerabilities, monitoring logs, or running compliance checks. While these tasks are important, they can be tedious and reduce the time available for cyber professionals to focus on more complex and strategic issues.
AI enables automation of these routine tasks, making cybersecurity operations more efficient. For example, AI-driven vulnerability scanners can continuously monitor systems and flag potential issues without requiring constant human oversight. This automation allows security teams to shift their focus toward analyzing threat intelligence, responding to incidents, and designing long-term defense strategies.
In addition, AI tools can automate incident response processes. When a security event occurs, AI systems can follow pre-programmed protocols to contain the threat—such as isolating affected systems, blocking malicious traffic, or alerting administrators—within seconds. This rapid response reduces damage and improves an organization’s ability to recover from cyber incidents.
Real-Time Detection and Response: Staying Ahead of Cyber Criminals
In today’s digital world, cyberattacks can unfold in a matter of seconds. Organizations need tools that can detect and respond to threats just as quickly. AI excels in real-time monitoring and response, enabling security systems to identify suspicious behavior as it occurs and take immediate action.
For example, AI-powered intrusion detection systems (IDS) can analyze network traffic in real time to detect unusual patterns or activities. If a user is trying to access sensitive data without proper credentials or if a system starts behaving abnormally, the AI can flag it instantly and take predefined steps to contain the risk.
Similarly, AI tools can identify malware hidden within encrypted files or disguised as legitimate software. With advanced behavioral analysis, these tools can recognize even the most subtle indicators of compromise and initiate mitigation steps before significant damage is done.
This capability is particularly crucial in defending against ransomware, where every second counts. Real-time AI detection can stop the spread of ransomware by isolating infected machines and preventing further encryption of files.
Continuous Learning and Adaptability
One of AI’s most powerful features is its ability to learn and evolve. Unlike traditional rule-based systems, which require manual updates, AI models continuously improve over time as they are exposed to new data and attack patterns. This means they become more accurate and effective the more they are used.
This learning capability is essential in the fast-moving world of cyber threats. As hackers constantly develop new techniques and tools, AI-driven systems can adapt quickly and update their defenses without waiting for human intervention. The result is a more resilient and proactive cybersecurity framework.
A Collaborative Approach to Cybersecurity
It’s important to understand that AI is not a replacement for human cybersecurity experts. Instead, it acts as a force multiplier—augmenting human capabilities, speeding up decision-making, and providing deep insights that would be impossible to gather manually.
Cybersecurity is most effective when AI and human intelligence work together. While AI excels at handling data, spotting patterns, and automating tasks, human experts provide context, intuition, and strategic thinking. Together, they form a powerful team that can better protect organizations from a growing range of cyber threats.
Challenges of Implementing Cyber Tech
While Cyber Tech offers numerous benefits—such as improved data security, faster threat detection, and enhanced business continuity—implementing these solutions is not always a smooth or simple process. Businesses of all sizes may encounter several roadblocks along the way. Below are some of the most common challenges companies face when integrating Cyber Tech into their operations:
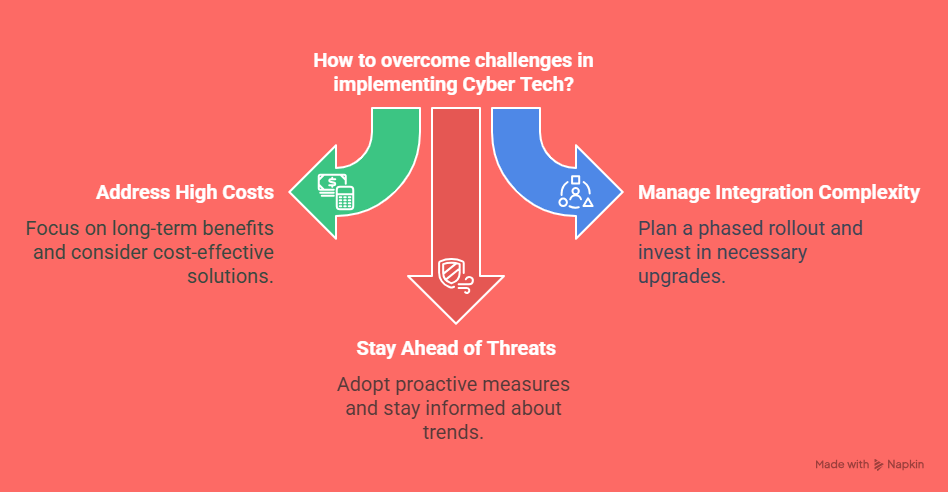
1. High Initial Costs
One of the most significant hurdles in adopting Cyber Tech solutions is the high upfront cost. For small and medium-sized enterprises (SMEs), this can be particularly daunting. The implementation process typically involves purchasing advanced cybersecurity software, specialized hardware, and other tools essential for a comprehensive security system.
Moreover, businesses often need to hire or consult with cybersecurity experts who can tailor solutions to their specific needs. These experts don’t come cheap, and retaining them long-term for maintenance, updates, and monitoring adds to the overall cost. Despite these expenses, it’s important to remember that the long-term benefits—such as preventing costly data breaches or compliance penalties—often outweigh the initial investment. In many cases, the cost of recovering from a cyberattack far exceeds the cost of implementing a robust cybersecurity framework.
2. Complexity of Integration
Integrating new Cyber Tech solutions with existing IT systems can be another major challenge. Many businesses operate on legacy systems or outdated infrastructure that may not be compatible with modern cybersecurity technologies. Attempting to mesh old and new systems can lead to operational disruptions or leave vulnerabilities exposed if not done properly.
This challenge often requires businesses to undertake a broader digital transformation. They may need to upgrade existing hardware, update software, and redesign internal processes to support the integration. Additionally, team members must be trained on how to use the new tools and systems effectively, which adds to the time and cost involved. A well-planned implementation strategy that includes thorough assessments and phased rollouts can help ease this transition.
3. Keeping Up with Evolving Threats
The cybersecurity landscape is constantly changing. Hackers are continuously developing new techniques, malware, and strategies to exploit system weaknesses. This means that no Cyber Tech solution is a one-time fix. Instead, organizations must adopt a proactive approach to stay ahead of potential threats.
Staying protected requires regular software updates, real-time threat monitoring, and the adoption of cutting-edge technologies such as AI-driven threat detection or behavioral analytics. It also means staying informed about the latest cybersecurity trends and regulatory changes. Businesses must be ready to pivot and adapt quickly when new vulnerabilities are discovered or when new compliance requirements are introduced.
Conclusion
In conclusion, Cyber Tech is no longer a luxury for businesses—it's a necessity. As cyber threats continue to evolve, businesses must adopt robust Cyber Tech solutions to protect their digital assets, ensure business continuity, and comply with regulatory standards. From preventing cyberattacks to safeguarding customer data, Cyber Tech plays a pivotal role in the success of modern organizations.
For businesses looking to improve their security infrastructure and stay ahead of cybercriminals, implementing cutting-edge Cyber Tech solutions is the key. At ACSMI, we specialize in providing high-quality medical scribe certifications that equip professionals with the skills needed to excel in today’s cybersecurity-focused medical industry. As technology continues to evolve, having the right knowledge and certifications in Cyber Tech will be critical for career advancement in the healthcare sector.
FAQs
1. What is Cyber Tech in simple terms?
Cyber Tech refers to a range of technologies and solutions designed to protect digital systems and data from cyber threats. It includes tools like firewalls, antivirus software, encryption, and intrusion detection systems that help secure networks and prevent unauthorized access to sensitive information. In essence, Cyber Tech ensures that businesses can operate securely in the digital age.
2. Why do businesses need Cyber Tech solutions?
Businesses need Cyber Tech solutions to protect themselves from the growing number of cyberattacks, such as hacking, phishing, and malware. These attacks can lead to significant financial losses, data breaches, and damage to a company's reputation. By implementing Cyber Tech, businesses can safeguard their sensitive data, ensure business continuity, and comply with industry regulations to avoid costly penalties.
3. What are the most common types of Cyber Tech solutions for businesses?
The most common types of Cyber Tech solutions for businesses include:
-
Firewall Protection: Prevents unauthorized access to a network.
-
Antivirus and Antimalware Software: Protects against viruses and other malicious software.
-
Encryption: Secures sensitive data by making it unreadable to unauthorized users.
-
Intrusion Detection Systems (IDS): Detects and alerts businesses to potential threats in real-time. These solutions work together to create a robust cybersecurity framework for businesses.
4. How does Artificial Intelligence enhance Cyber Tech?
Artificial Intelligence (AI) plays a vital role in enhancing Cyber Tech by providing advanced threat detection, real-time monitoring, and automated responses. AI can analyze vast amounts of data, identify patterns indicative of potential cyber threats, and take immediate action to prevent them. Additionally, AI systems can continuously learn from new data, improving their ability to detect evolving threats and vulnerabilities.
5. What are the challenges businesses face when implementing Cyber Tech solutions?
Some of the key challenges businesses face when implementing Cyber Tech solutions include:
-
High Initial Costs: The upfront investment in cybersecurity tools and systems can be expensive, particularly for small businesses.
-
Integration Complexity: Integrating new cybersecurity tools with existing IT infrastructure can be complex and require expertise.
Constantly Evolving Threats: Cyber threats are continuously evolving, requiring businesses to update their Cyber Tech solutions regularly to stay protected. Overcoming these challenges is essential for businesses to effectively safeguard their operations and data.

Leave a Reply