In today’s fast-paced and ever-evolving world, ensuring the safety and security of an organization’s assets—both physical and digital—is more critical than ever. Security management is an integral part of any organization's strategy, covering a broad spectrum of activities that safeguard its assets, people, and data. Security management is not a one-time activity; rather, it’s an ongoing process that involves planning, implementing, monitoring, and adapting security measures.
Security management encompasses a wide range of practices, from physical security measures like surveillance and access control to complex cybersecurity strategies that prevent data breaches and cyberattacks. But why is it so essential for organizations today? What exactly does it entail, and what role does it play in ensuring an organization’s long-term success?
In this blog, we will explore the fundamental aspects of security management and understand why it is indispensable for businesses and institutions of all sizes. We will also discuss the key components of a robust security management system, the risks of neglecting it, and how security management serves as the backbone for an organization’s overall risk management plan.
To learn more about risk management strategies, visit our blog on risk management in security.
What is Security Management?
Security management refers to the process of developing, implementing, and overseeing policies and procedures that ensure the safety of an organization’s physical assets, employees, and digital data. It encompasses everything from ensuring compliance with security regulations to mitigating potential threats and responding to incidents.
At its core, security management focuses on reducing risks and vulnerabilities that could harm the organization. It involves identifying security threats, assessing risks, and applying strategies to mitigate them effectively.
For further reading on managing security risks in your organization, explore our blog on risk mitigation strategies.
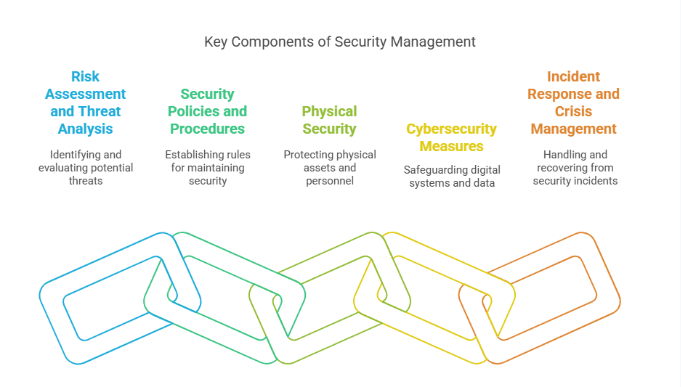
Key Components of Security Management
Effective security management is essential for any organization that aims to safeguard its assets, information, personnel, and reputation. It’s not just about hiring security personnel or installing a few cameras; rather, it's about implementing a comprehensive strategy that encompasses various critical components. These components work together to create a well-rounded and robust security framework. Below is a detailed overview of the key components of security management:
Risk Assessment and Threat Analysis
The foundation of any effective security plan begins with risk assessment and threat analysis. This is the process of identifying, evaluating, and prioritizing risks that could potentially harm the organization. These threats may come in many forms, such as cyberattacks, natural disasters, internal theft, or unauthorized access to sensitive areas.
Risk assessment helps organizations understand what assets are most valuable and vulnerable, and where their security gaps lie. Once these threats and vulnerabilities are identified, security teams can develop strategies to mitigate or eliminate them. For example, a company handling sensitive customer data may prioritize cybersecurity investments, while a manufacturing facility might focus more on physical security measures.
In addition to identifying risks, this process includes analyzing the likelihood of each threat and the potential impact it would have. This step ensures that resources are allocated effectively and helps the organization prepare for the most critical scenarios.
Security Policies and Procedures
Once risks have been assessed, it’s vital to establish clear security policies and procedures. These act as a rulebook for how employees, contractors, and visitors should behave in order to maintain a secure environment. Well-defined policies ensure consistency across the organization and provide a baseline for accountability.
Policies may cover a wide range of areas including access control, data handling, visitor protocols, incident reporting, and acceptable use of company technology. Procedures, on the other hand, offer detailed instructions on how to implement these policies. For instance, a policy may state that only authorized personnel can access the server room, while the procedure would explain how access is granted and monitored.
Effective security policies must be clearly communicated, regularly reviewed, and updated to reflect changes in technology, organizational structure, or legal requirements. Training sessions should also be conducted to ensure that everyone understands and follows the security guidelines.
Physical Security
Physical security is a crucial component of any comprehensive security strategy. It focuses on the protection of buildings, equipment, and personnel from unauthorized access, theft, vandalism, and other physical threats. This can include everything from locked doors and fences to sophisticated surveillance and access control systems.
Common physical security measures include:
-
Surveillance cameras (CCTV): To monitor and record activity in and around facilities.
-
Alarm systems: To alert authorities in case of unauthorized entry or fire.
-
Access control systems: Such as keycards, biometric scanners, or PIN pads to restrict entry to sensitive areas.
-
Security personnel: Trained guards who can monitor premises, control entry points, and respond to incidents.
Physical security also involves planning for emergencies such as fires or evacuations. Organizations must ensure exits are clearly marked, fire extinguishers are accessible, and emergency procedures are in place and well-practiced.
Cybersecurity Measures
In the digital age, cybersecurity is equally important—if not more so—than physical security. With most organizations relying on digital systems to manage operations, data, and communications, the risk of cyber threats is significant.
Cybersecurity involves protecting systems, networks, and data from unauthorized access, damage, or theft. Key cybersecurity practices include:
-
Firewalls and antivirus software: To block unauthorized traffic and detect malicious programs.
-
Data encryption: To protect sensitive information from being intercepted or accessed unlawfully.
-
Regular data backups: To ensure data can be restored in case of loss or corruption.
-
Intrusion detection systems (IDS): To monitor network traffic for suspicious activity.
Moreover, cybersecurity is not just a technical challenge but also a human one. Organizations must educate their employees on safe practices such as recognizing phishing emails, using strong passwords, and reporting suspicious activity.
Incident Response and Crisis Management
Even with the most robust security measures in place, incidents are bound to occur. That's why having a well-defined incident response and crisis management plan is essential. This plan outlines how the organization will detect, respond to, and recover from various types of security events.
Incident response involves:
-
Identification: Detecting and acknowledging that a security event has occurred.
-
Containment: Limiting the scope and impact of the incident.
-
Eradication: Removing the threat from the environment.
-
Recovery: Restoring systems and operations to normal.
-
Post-incident review: Learning from the incident to prevent future occurrences.
Crisis management extends beyond just the technical response. It includes communication strategies, coordination with law enforcement or emergency services, and maintaining business continuity. Having a crisis communication plan ensures that accurate information is shared with stakeholders, including employees, customers, and the media, in a timely manner.
Preparedness drills and tabletop exercises can help teams stay ready for emergencies and ensure that roles and responsibilities are clearly understood.
Looking for more insights on handling security crises? Check out our blog on incident response management.
Why is Security Management Important for Organizations?
Security management is a cornerstone of an organization’s operational integrity, resilience, and long-term success. In today’s fast-paced digital and physical environments, organizations face a wide range of potential threats—cyberattacks, data breaches, internal fraud, natural disasters, and even workplace violence. Without a strong security management framework in place, businesses risk not only financial losses but also reputational damage, legal consequences, and operational downtime.
Let’s explore in more detail why security management plays such a vital role in modern organizations.
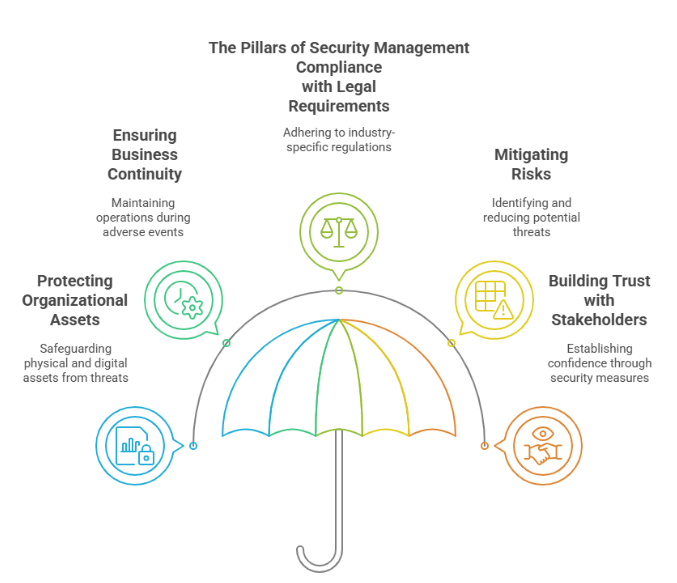
Protecting Organizational Assets
At the core of security management is the goal of protecting an organization’s assets. These assets can be broadly categorized into two types:
-
Physical Assets: These include buildings, office equipment, machinery, vehicles, and inventory. Without proper security measures—such as surveillance systems, access controls, and alarms—these assets are vulnerable to theft, vandalism, or damage.
-
Digital and Intangible Assets: Perhaps even more valuable are the intangible assets like proprietary information, trade secrets, software, intellectual property, and customer data. In an increasingly digital world, cyber threats like hacking, ransomware, and data theft are constant concerns.
Security management strategies work to defend both types of assets through the implementation of security policies, technologies, and procedures that reduce vulnerabilities and prevent unauthorized access.
Ensuring Business Continuity
One of the main goals of security management is to ensure that the business can continue to operate without major interruptions, even in the face of adverse events. Whether it’s a cyberattack, a natural disaster, or a power outage, a well-designed security plan includes contingency strategies to minimize downtime and maintain essential services.
For example, having data backups and disaster recovery protocols ensures that critical systems can be restored quickly in case of a breach or technical failure. Similarly, physical security measures can help protect facilities and staff during emergencies. Without these preparations, companies may struggle to recover, lose customer trust, and suffer long-term consequences.
Compliance with Legal and Regulatory Requirements
Many industries operate under strict legal and regulatory requirements concerning data protection and security. These regulations are put in place to protect consumers, employees, and businesses from potential harm.
-
Healthcare organizations must follow standards like HIPAA (Health Insurance Portability and Accountability Act).
-
Financial institutions must adhere to regulations such as GLBA (Gramm-Leach-Bliley Act) and PCI-DSS (Payment Card Industry Data Security Standard).
-
Government contractors often have to comply with NIST (National Institute of Standards and Technology) guidelines.
Failing to meet these requirements can lead to hefty fines, lawsuits, loss of licenses, and reputational damage. Security management ensures that an organization remains compliant, reduces legal risk, and stays ahead of regulatory changes.
Mitigating Risks
No organization is immune to risk, but security management provides a proactive approach to identifying, assessing, and mitigating those risks before they become crises. Effective risk management involves:
-
Conducting regular risk assessments to identify potential threats.
-
Implementing controls (technical and procedural) to reduce vulnerabilities.
-
Training employees on how to recognize and respond to threats.
-
Monitoring and reviewing security systems for weaknesses.
Risks can stem from both internal and external sources. Internally, risks might include employee misconduct, human error, or poor cybersecurity practices. Externally, they might involve competitors, cybercriminals, or even geopolitical threats. Security management equips organizations with the tools and knowledge to tackle both.
Building Trust with Stakeholders
In today’s environment, trust is one of the most valuable currencies an organization can have. Clients, customers, investors, partners, and employees all expect that the companies they interact with will take security seriously. If they sense that an organization is careless with sensitive information or doesn’t have proper protections in place, they may choose to take their business elsewhere.
When an organization demonstrates a strong commitment to security—through transparent policies, employee training, regular audits, and public communication—it sends a clear message: we care about protecting your information and our shared interests. This builds lasting relationships and strengthens the organization's reputation in the market.
Security Management Systems: How They Work
In today’s fast-paced and unpredictable world, safeguarding organizational assets—whether physical, digital, or human—is more critical than ever. That’s where Security Management Systems (SMS) come into play. These systems are comprehensive frameworks designed to protect an organization from a wide range of threats by combining technology, policies, procedures, and people. When implemented effectively, they not only reduce vulnerabilities but also ensure a quick and coordinated response to incidents.
A well-structured security management system is designed to address all areas of security within an organization. It typically involves several layers of protection and follows a systematic approach to both preventing security breaches and responding to incidents. This approach allows businesses to maintain a safe and secure environment for employees, customers, and assets.
Let’s break down how these systems function and why they are essential for any modern organization.
Key functions of a security management system include:
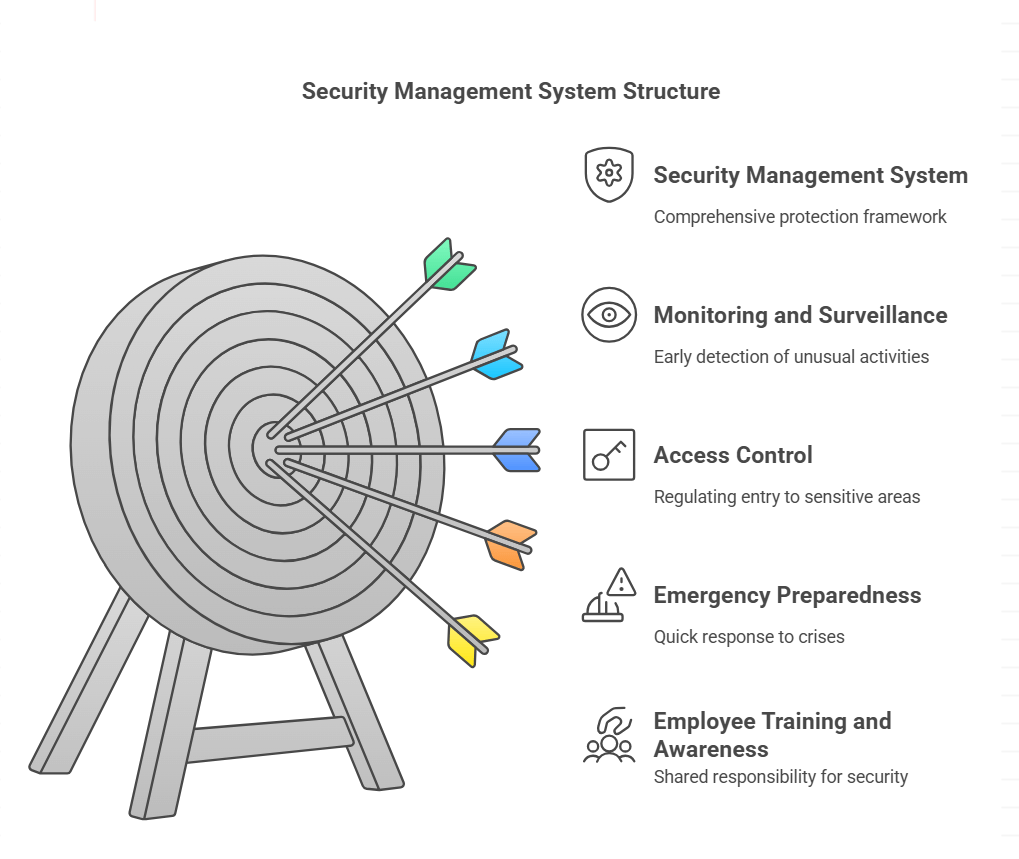
Monitoring and Surveillance
One of the foundational elements of a security management system is continuous monitoring. This typically involves the use of:
-
CCTV cameras strategically placed throughout the premises.
-
Motion sensors and other detection technologies.
-
Security personnel who patrol and monitor activity in real time.
-
Remote monitoring systems, allowing security teams to track activities off-site.
These surveillance tools help in early detection of unusual activities, which is essential in preventing incidents before they escalate. Surveillance also provides valuable evidence when investigating incidents after they occur.
Access Control
Controlling who enters and exits certain areas is crucial. Access control systems use a variety of methods to restrict entry based on role or clearance level. These systems include:
-
Keycard or biometric systems (fingerprint or facial recognition).
-
PIN code entry pads.
-
Turnstiles and smart locks.
-
Visitor management systems that track and regulate non-employees on the premises.
Effective access control reduces the risk of unauthorized access to sensitive areas or information, ensuring that only approved personnel can access critical spaces or systems.
Emergency Preparedness
Security isn't just about preventing crime or breaches—it’s also about responding quickly and effectively when emergencies occur. A robust SMS includes comprehensive emergency response protocols such as:
-
Evacuation plans and drills for fires, natural disasters, or active threats.
-
Lockdown procedures in the case of intrusions or violent incidents.
-
Communication systems (like mass notification alerts) to keep staff informed in real time.
-
Coordination with local law enforcement and emergency services.
Being prepared can significantly reduce harm and chaos during a crisis and helps organizations return to normal operations faster.
Employee Training and Awareness
Even the most sophisticated security system can fall short if staff aren’t properly trained. Human error is one of the most common security vulnerabilities. That’s why ongoing education and awareness programs are vital. Training programs typically include:
-
Security protocol education (e.g., what to do in case of a breach).
-
Recognizing suspicious behavior or phishing attempts.
-
First aid and emergency response training.
-
Updates on new threats and system changes.
By making security a shared responsibility, organizations strengthen their overall safety net.
Challenges in Security Management
Security management plays a vital role in protecting an organization’s assets, information, and personnel. Whether it's a corporate office, government agency, or small business, a strong security framework helps ensure business continuity, protects confidential data, and reduces the risk of internal and external threats. However, despite its importance, effective security management comes with several challenges that can hinder its success.
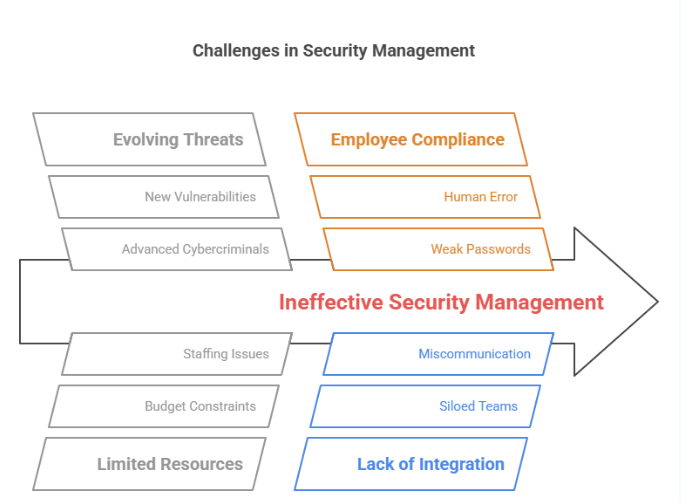
Evolving Threats
One of the most pressing challenges in security management is keeping up with the constantly evolving threat landscape. As technology advances, so do the methods and sophistication of cybercriminals, hackers, and other malicious actors. Threats that were relevant a year ago may no longer pose the same risk, while new vulnerabilities are discovered regularly. From ransomware attacks and phishing scams to advanced persistent threats (APTs) and insider threats, security managers must remain vigilant and proactive. Continuous monitoring, real-time threat intelligence, and timely updates to security protocols are necessary to stay one step ahead of potential attackers.
Limited Resources
Another significant hurdle is the lack of adequate resources. Many organizations—especially small to mid-sized enterprises—struggle with limited budgets and staffing issues. Building and maintaining a robust security system requires investment in tools, technologies, and qualified personnel. However, when resources are stretched thin, critical areas may be overlooked, resulting in weak points that can be exploited. Limited funding can also restrict access to modern security solutions such as intrusion detection systems, automated monitoring tools, and advanced cybersecurity software. Without sufficient investment, the ability to detect and respond to threats is greatly compromised.
Employee Compliance
Even the most advanced security measures can be rendered ineffective if employees do not follow proper protocols. Human error remains one of the leading causes of security breaches. Whether it's clicking on malicious links, using weak passwords, or neglecting to update software, unintentional mistakes can have serious consequences. Ensuring that employees understand their role in maintaining security is essential. This includes regular training programs, awareness campaigns, and clear communication about security policies. Additionally, creating a culture of accountability can encourage employees to take security seriously and report suspicious activity.
Lack of Integration and Coordination
In some organizations, security is managed in silos, with physical security, cybersecurity, and data privacy teams operating independently. This lack of integration can lead to gaps in coverage, miscommunication, and inefficient response to incidents. A unified approach to security—where all aspects work together seamlessly—is essential for comprehensive protection. Coordinating efforts across departments, sharing information, and using integrated security platforms can improve response times and overall effectiveness.
Keeping Up With Compliance Requirements
Regulatory compliance is another area that adds complexity to security management. Organizations must adhere to industry-specific standards and government regulations such as GDPR, HIPAA, or ISO/IEC 27001. Meeting these requirements often involves regular audits, extensive documentation, and ongoing risk assessments. Failure to comply can result in hefty fines and reputational damage, making it a critical aspect of security planning.
Looking for solutions to common security management challenges? Check out our blog on overcoming security management challenges.
Conclusion
In conclusion, security management is not just about securing physical spaces or digital information; it’s about creating a proactive and systematic approach to risk mitigation. A well-executed security management strategy protects organizational assets, ensures business continuity, and builds trust with clients and stakeholders.
By implementing robust security management practices, businesses can protect themselves from a wide array of threats and avoid costly mistakes.
At ACSMI, we understand the importance of maintaining a secure environment. We provide medical coding and billing certifications, ensuring that professionals have the skills and knowledge necessary to safeguard sensitive data and comply with industry standards. We also offer a wide range of snacks online to fuel your workday, keeping you energized and focused.
FAQs
What are the key components of a security management system?
A security management system includes risk assessments, security policies, physical and cyber protection, and incident response.
How can security management prevent business interruptions?
By identifying risks and implementing preventive measures, security management ensures that business operations continue smoothly without interruptions from security breaches.
What is the role of cybersecurity in security management?
Cybersecurity protects an organization’s data and digital assets from cyberattacks, including malware, phishing, and ransomware.
Why is employee training crucial in security management?
Employee training ensures that everyone in the organization understands security protocols and is equipped to handle security threats effectively.
How do security management systems adapt to emerging threats?
Security management systems evolve by incorporating new technologies and strategies, ensuring they can respond to the latest security challenges.

Leave a Reply