Career Path from SOC Analyst to Manager and Salary Skills
Breaking out of the SOC Analyst role into a management position isn’t just a promotion — it’s a move into strategic leadership that directly influences an organization’s cybersecurity resilience. As a SOC Analyst, you’re in the trenches, identifying threats, responding to incidents, and mastering advanced security tools. This career progression is in high demand due to the growing complexity of cyber threats and the urgent need for experienced leaders who understand both the technical and business sides of security.
The jump in responsibility comes with a significant salary leap and broader decision-making authority. SOC Managers not only command six-figure salaries in many industries but also play a key role in aligning security posture with business goals. This article will break down the exact skills you need, the certifications that fast-track promotions, and the salary benchmarks you can expect.
Understanding the SOC Analyst Role
Core Responsibilities and Day-to-Day Tasks
A SOC Analyst serves as the first line of defense against cyber threats, continuously monitoring security systems to detect anomalies before they escalate. Daily work involves analyzing SIEM alerts, investigating suspicious activity, and conducting threat hunting to identify vulnerabilities. Analysts respond to incidents by collecting evidence, containing threats, and restoring normal operations. They maintain detailed documentation for compliance and future reference, ensuring every incident’s root cause is understood and mitigated.
Beyond incident handling, analysts also engage in log analysis across endpoints, networks, and cloud environments. This involves correlating events from multiple data sources to piece together the full attack narrative. Routine vulnerability scanning and patch verification are also part of the role, along with fine-tuning detection rules in SIEM platforms to reduce false positives. A strong SOC Analyst anticipates threats before they occur, maintaining a proactive security posture that limits business impact.
Key Technical and Soft Skills Required
Technical depth is essential. Analysts must master SIEM platforms (Splunk, QRadar, Sentinel), intrusion detection/prevention systems, and malware analysis tools. Familiarity with scripting languages like Python or PowerShell helps automate repetitive tasks. Understanding attack frameworks such as MITRE ATT&CK allows for precise threat categorization and more effective defense strategies.
However, SOC success is equally dependent on soft skills. Strong communication is crucial to relay findings to both technical teams and non-technical executives. Critical thinking and rapid decision-making are vital during high-pressure incidents, while adaptability ensures analysts can pivot as threat landscapes evolve. Collaboration is another key factor — SOCs operate as team-based units, meaning each analyst must contribute to collective intelligence.
The combination of technical proficiency and interpersonal capability positions SOC Analysts for upward mobility. Mastery in this role creates the operational credibility needed to step into management, where strategic oversight and cross-team coordination become central.
Transitioning from SOC Analyst to SOC Manager
Experience Milestones and Promotions
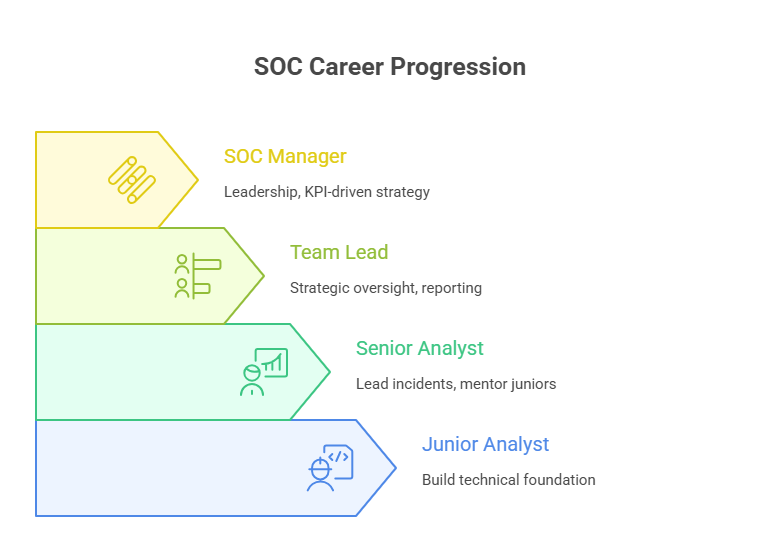
Progressing to SOC Manager typically requires 5–8 years of SOC experience, with at least 2–3 years in a senior analyst or team lead position. Early in your career, the focus is on mastering core SOC functions — incident response, threat hunting, and SIEM optimization. As you advance, you’ll need to take on mentorship responsibilities, guiding junior analysts and shaping detection strategies.
Promotion-ready candidates often demonstrate consistent success in reducing incident response times, improving detection accuracy, and implementing security automation. Exposure to multiple environments — on-premises, cloud, hybrid — expands your adaptability and strategic perspective. Many analysts accelerate progression by participating in cross-department projects, such as red team/blue team exercises, governance committees, or compliance audits.
To secure the manager title, you must show measurable business impact — for example, leading an initiative that cut phishing-related incidents by 40% or implementing an automation workflow that saved 200 analyst hours per month. Hiring committees prioritize candidates who can align SOC operations with business risk tolerance and regulatory requirements, proving readiness for strategic decision-making.
Common Obstacles in Career Progression
One major barrier is the technical-to-strategic shift. Analysts accustomed to hands-on work may struggle with delegation, focusing instead on tactical firefighting. SOC Managers must pivot toward resource allocation, performance metrics, and long-term defense strategies rather than individual incident handling.
Another challenge is the perception gap. Without visibility outside the SOC, analysts may be overlooked for leadership positions. Proactively engaging with IT, risk management, and executive stakeholders ensures decision-makers understand your capabilities. Building a personal brand within the organization — through presentations, quarterly reports, or security awareness training — positions you as a leader before the formal promotion.
Lack of management-level certifications can also slow advancement. While technical credentials like CISSP or GCIA are valuable, adding leadership-oriented certifications signals readiness for broader responsibilities. Finally, some analysts face “title trap” issues, where internal promotion opportunities are limited. In such cases, moving to another organization may be the most efficient route to a manager role.
The transition isn’t purely about time served; it’s about proving you can transform SOC strategy, lead diverse teams, and bridge technical execution with business risk management. Those who deliberately cultivate these competencies shorten the path to leadership and open the door to higher-paying, more influential roles.
Salary Growth from Analyst to Manager
Entry-Level Analyst Salary Ranges
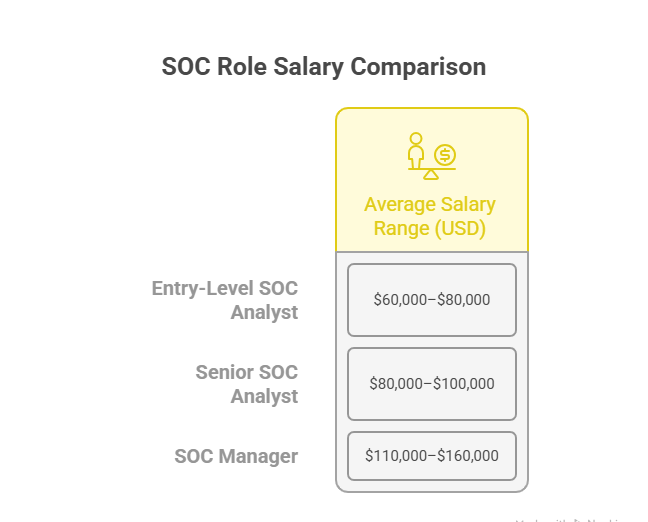
SOC Analyst salaries vary based on location, industry, and skill set, but entry-level analysts can expect to earn between $60,000 and $80,000 annually in the U.S. Roles in financial services, government, and tech often start at the higher end of this range due to heightened compliance and security requirements. Analysts with scripting abilities, cloud security experience, or knowledge of niche tools like EDR platforms may command a premium.
Shift schedules can also influence earnings, with night and weekend coverage often providing additional compensation. While bonuses are less common at the entry level, many companies offer certification reimbursement and training budgets, adding long-term value to the base salary. These early years are crucial for building the technical foundation and incident-handling record that will justify higher pay later.
SOC Manager Salary Benchmarks Across Industries
SOC Managers typically earn $110,000 to $160,000 annually, with some roles in high-cost metro areas or critical infrastructure sectors exceeding $180,000. Industries like banking, defense, and healthcare often pay more due to the sensitivity of data handled. The jump from analyst to manager represents a 30–60% salary increase, driven by leadership responsibilities and strategic influence over security posture.
Managers may also receive performance bonuses, profit-sharing, or retention incentives. Larger organizations tend to offer more structured compensation packages, while smaller companies may trade higher salaries for broader decision-making autonomy. The role’s earnings potential is further enhanced by the visibility and cross-department influence that comes with managing the SOC.
Factors That Influence Earnings Potential
Several factors determine how far salaries can climb. Geographic location remains a major driver — cybersecurity roles in hubs like San Francisco, New York, or London often pay 20–40% more than national averages. Specialized expertise, such as cloud-native SOC management or experience with large-scale security automation, can push salaries into the top tier.
Company size and maturity also matter: established enterprises may pay more but have slower promotion tracks, while high-growth startups may offer equity or rapid advancement in exchange for broader responsibilities. Finally, holding high-value certifications — blending technical depth with management focus — signals to employers that you can lead at scale, which directly impacts earning potential.
Skills to Cultivate for Management Roles
Technical Upskilling and Tool Mastery
SOC Managers must maintain technical credibility while shifting into strategic oversight. Deep knowledge of SIEM optimization, EDR solutions, and SOAR platforms is essential to lead teams effectively. Experience with threat intelligence platforms, network forensics, and vulnerability management tools ensures you can evaluate team recommendations and approve technical strategies with confidence.
Cloud security expertise, particularly in AWS, Azure, or Google Cloud environments, is now a core requirement. Understanding security automation workflows not only streamlines operations but also frees analyst time for higher-priority work. Staying current through labs, capture-the-flag events, and emerging threat reports ensures technical decisions remain relevant and aligned with evolving attack vectors.
Leadership, Communication, and Strategic Thinking
Transitioning to management demands mastery of team leadership and decision-making under pressure. SOC Managers set priorities, assign resources, and ensure coverage for 24/7 operations without analyst burnout. Strong communication skills allow you to translate technical findings into clear risk narratives for executives and boards.
Strategic thinking involves aligning SOC goals with the organization’s business objectives. This means defining KPIs — such as mean time to detect (MTTD) and mean time to respond (MTTR) — and using them to measure and improve performance. It also means knowing when to invest in technology upgrades versus skill development to maximize ROI.
Building Cross-Department Collaboration Skills
A SOC Manager’s influence extends beyond the SOC. Collaborating with IT, compliance, legal, and executive leadership ensures security priorities are integrated across the business. Building trust with these stakeholders makes it easier to secure budget approvals, adopt new processes, and respond to incidents at scale without operational friction.
Effective collaboration also enhances incident post-mortems, allowing root causes to be addressed holistically rather than in isolation. By fostering these interdepartmental relationships, SOC Managers elevate the SOC’s role from reactive defense to a proactive driver of organizational resilience.
| Skill Area | What to Build | Evidence | Promotion Impact |
|---|---|---|---|
| SIEM / SOAR & Automation | Playbooks, alert tuning, auto-containment | Runbooks + pipelines that cut MTTR by 30–50% | Signals readiness for team leadership |
| Cloud Security (AWS / Azure / GCP) | Guardrails, logging, cloud-native detections | Sentinel/CloudTrail rules mapped to ATT&CK | Positions you for cloud-first SOCs |
| Threat Intel & Detection Engineering | ATT&CK-aligned detections, purple-team loops | Coverage >= 70% ATT&CK | Shows strategy beyond firefighting |
| Incident Command & Postmortems | IC rotations, severity models, RCA process | Taxonomy + blameless postmortems with actions | Builds crisis credibility |
| KPI / Reporting & Budgeting | MTTD, MTTR, false-positive rate, ROI | Executive dashboard + cost-savings case | Unlocks tooling and headcount |
| People Leadership & Coaching | 1:1s, career ladders, onboarding paths | Skill matrix, mentorship plan, hiring rubric | Raises team output; clear manager signal |
| Cross-Department Collaboration | RACI with IT/Legal/Compliance | Agreed workflows for patching & takedowns | Reduces friction during incidents |
| Governance & Risk Alignment | Policy mapping, control testing, risk register | Updated policies + treatment plans | Aligns SOC to business risk |
Certifications That Fast-Track Advancement
SOC-Specific Certifications
Technical mastery is validated through high-value SOC certifications. The GIAC Certified Incident Handler (GCIH) and GIAC Security Operations Certified (GSOC) confirm deep expertise in detecting, analyzing, and mitigating threats. The Certified Information Systems Security Professional (CISSP), while broader in scope, is often a prerequisite for senior SOC leadership roles.
Hands-on certifications like Offensive Security Certified Professional (OSCP) or GIAC Certified Forensic Analyst (GCFA) demonstrate advanced incident handling, forensics, and threat hunting capabilities. These credentials not only increase credibility but can also lead to immediate salary boosts, especially in regulated sectors where certified personnel are a compliance requirement.
Employers also value certifications tied to specific tools, such as Splunk Certified Power User or Microsoft Security Operations Analyst Associate, as they prove operational readiness in the platforms your SOC uses daily.
Management and Leadership Certifications
To move from technical execution to strategic leadership, SOC professionals must validate their management skills. The Certified Information Security Manager (CISM) focuses on governance, risk management, and program development — core functions of SOC leadership. The Project Management Professional (PMP) certification signals your ability to deliver complex security initiatives on time and within budget.
Executive-focused programs like the Certified in Risk and Information Systems Control (CRISC) emphasize risk governance, while cybersecurity MBA programs bridge the gap between technical expertise and business strategy.
Combining technical SOC credentials with leadership-oriented certifications positions you as a complete candidate — one who can lead threat detection teams while aligning security priorities with corporate goals. This dual-certification strategy is often the fastest way to bypass mid-level plateaus and secure a SOC Manager role.
| Certification Type | Example Certifications | Benefit |
|---|---|---|
| SOC-Specific | GCIH, GSOC, OSCP, GCFA | Validates incident handling and threat analysis skills |
| Leadership & Management | CISM, PMP, CRISC | Proves ability to lead teams and align security with business goals |
| Tool-Specific | Splunk Certified Power User, Microsoft Security Operations Analyst | Confirms operational readiness in key SOC platforms |
Leveraging the Advanced Cybersecurity & Management Certification (ACSMC) for SOC Career Advancement
The Advanced Cybersecurity & Management Certification (ACSMC) is designed for professionals aiming to bridge the gap between deep technical expertise and executive-level leadership. For SOC Analysts aspiring to management, ACSMC provides structured, high-impact training that blends advanced threat detection methodologies with leadership, governance, and risk management principles.
Unlike certifications focused purely on tools or frameworks, ACSMC develops the strategic mindset required to oversee 24/7 SOC operations, manage multi-disciplinary teams, and align detection capabilities with business objectives. The curriculum covers real-world case studies on incident response leadership, security automation implementation, and cross-department collaboration — all critical to thriving as a SOC Manager.
One of the ACSMC’s key advantages is its emphasis on cybersecurity program governance. This skillset ensures that SOC Managers can not only respond to incidents but also design detection and prevention strategies that support enterprise resilience and compliance mandates. Graduates are well-equipped to influence budget decisions, justify technology investments, and build KPIs that track SOC performance at scale.
Frequently Asked Questions
-
Most professionals advance from SOC Analyst to SOC Manager in 5–8 years, depending on experience, skills, and organizational opportunities. The fastest paths involve securing senior analyst or team lead roles within 3–4 years, then demonstrating measurable leadership impact — such as improving incident response metrics or reducing false positives through automation. Earning both technical certifications (e.g., CISSP, GCIH) and leadership credentials (e.g., CISM, PMP) accelerates career growth. Participation in cross-department initiatives and exposure to budget or compliance decisions also strengthens your readiness for management positions. The timeline shortens when you combine high-demand skills with visible strategic contributions to the SOC.
-
SOC Analysts typically earn $60,000 to $90,000 annually, with entry-level roles on the lower end and experienced analysts reaching the top of the range. SOC Managers often command $110,000 to $160,000, with salaries exceeding $180,000 in high-demand sectors like finance, defense, and healthcare. This represents a 30–60% pay increase upon promotion. Factors influencing the gap include industry, geographic location, and organizational size. Additional perks for SOC Managers may include bonuses, stock options, and retention incentives. Certifications, proven leadership, and specialized expertise — such as managing cloud-native SOCs — can further widen the salary advantage in your favor.
-
A successful SOC Manager blends technical mastery with leadership and strategic skills. On the technical side, expertise in SIEM optimization, EDR, threat intelligence platforms, and security automation is crucial. On the leadership side, skills in team management, communication, and KPI-driven decision-making are essential. Strategic thinking — aligning SOC objectives with business goals — is a differentiator. The ability to collaborate across departments, influence executives, and secure budget approvals is also vital. A SOC Manager must shift from incident-level problem solving to designing systems and processes that enhance the SOC’s long-term efficiency, scalability, and resilience.
-
SOC Analysts aiming for management should first secure technical SOC credentials like GCIH, GSOC, OSCP, or GCFA to build credibility. The CISSP is highly regarded for leadership readiness. Then, layer on management-focused certifications such as CISM, PMP, or CRISC to prove strategic capability. Tool-specific certifications — like Splunk Certified Power User or Microsoft Security Operations Analyst Associate — provide an edge in organizations using those platforms. A balanced portfolio of technical and leadership certifications signals to employers that you can manage teams, oversee detection strategy, and align SOC operations with corporate risk management frameworks.
-
Both approaches have merit, but many SOC professionals achieve faster advancement by switching organizations when internal promotion pipelines stall. Internal moves are advantageous if your company offers clear career ladders, ongoing leadership opportunities, and support for certifications. However, external moves often come with immediate title upgrades, higher salaries, and exposure to different security environments. If staying internally, focus on visibility — present metrics to leadership, join governance committees, and take on interdepartmental projects. If moving externally, target companies with mature SOC structures where your existing skills and leadership potential can make an immediate impact.
-
Cloud security expertise is now non-negotiable for SOC Managers, as most organizations operate in hybrid or fully cloud-native environments. Understanding AWS, Azure, and Google Cloud security services allows you to oversee detection strategies that protect assets regardless of hosting model. Experience with cloud-native SIEM and SOAR tools — such as Microsoft Sentinel or AWS Security Hub — is increasingly valuable. SOC Managers must also address unique cloud threats like misconfigurations, API exploitation, and identity compromise. This knowledge not only improves incident handling but also ensures the SOC remains aligned with business adoption of modern infrastructure
-
Key SOC KPIs include Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), both critical for minimizing breach impact. False positive rate is another important metric, as it affects analyst workload and detection accuracy. Tracking incident recurrence rates helps assess the effectiveness of remediation strategies. Volume of incidents handled per analyst, automation coverage percentage, and cost per incident provide additional operational insights. Strategic KPIs — such as the percentage of incidents mapped to MITRE ATT&CK tactics — give leadership confidence in the SOC’s ability to address real-world threats systematically and proactively.
Conclusion
Moving from SOC Analyst to SOC Manager is not just about tenure — it’s about targeted skill-building, strategic visibility, and leadership readiness. Analysts who excel in threat detection, SIEM optimization, and incident response lay the technical foundation for advancement. Pairing this with certifications like CISSP, CISM, and ACSMC builds the strategic credibility employers demand in management candidates.
The salary jump from analyst to manager reflects the shift from operational execution to shaping detection strategies, managing cross-functional teams, and aligning SOC priorities with business objectives. Success in this transition comes from demonstrating measurable impact — reducing response times, increasing automation, or improving security KPIs — and consistently communicating that value to decision-makers.
Whether you aim to climb internally or pursue opportunities elsewhere, the key is to combine technical excellence with leadership acumen. By mastering both, you position yourself not only for the SOC Manager role but also for future executive-level cybersecurity positions. The path is competitive, but for those who invest in both capability and influence, it offers one of the most rewarding trajectories in the cybersecurity field.