Top Penetration Testing Tools: Comprehensive Comparison (2025 Edition)
Penetration testing has evolved into a non-negotiable component of modern cybersecurity infrastructure. As cyberattacks surged by over 38% globally in 2024, organizations across sectors—from finance to healthcare to SaaS—are no longer asking if they need pen testing, but which tools will deliver the sharpest insights. These tools aren’t just utilities; they’re battle-tested frameworks used by ethical hackers to simulate real-world breaches, test response protocols, and harden digital perimeters before malicious actors strike.
In 2025, choosing the right pen testing tool can determine not just your audit score, but your breach resilience. The tools reviewed here are industry-validated, actively maintained, and optimized for practical deployment. Whether you're a cybersecurity leader, a freelance red teamer, or a student enrolled in ACSMI’s Advanced Cybersecurity & Management Certification, this guide will serve as your hands-on map to navigating today’s most effective offensive security platforms.
What Is Penetration Testing and Why It’s Critical
Penetration testing is the practice of simulating real-world cyberattacks to uncover vulnerabilities before malicious actors can exploit them. Unlike theoretical assessments or compliance checklists, pen testing mimics genuine adversarial behavior—from phishing and privilege escalation to lateral movement—giving organizations clear, actionable insights into their most exploitable weak points.
In 2025, with regulatory scrutiny rising and attack surfaces expanding due to hybrid infrastructures, penetration testing has shifted from a niche practice to a strategic necessity. Companies aren't just looking to detect flaws—they’re aiming to quantify risk, validate controls, and demonstrate cybersecurity maturity to auditors, insurers, and stakeholders. A properly scoped pen test answers three questions: What can an attacker access? How quickly? And what damage can be done?
This approach supports security teams in hardening configurations, eliminating false positives, and prioritizing remediation efforts based on exploitability rather than theory. It also trains blue teams to better respond under simulated threat pressure, increasing operational resilience.
Red Teaming vs. Pen Testing vs. Vulnerability Scanning
These three terms are often confused, but each serves a distinct role in an organization’s security lifecycle:
Vulnerability scanning is automated. It checks systems against known CVEs (Common Vulnerabilities and Exposures) and provides a list of outdated software, open ports, and misconfigurations. However, it doesn’t verify exploitability in context.
Penetration testing involves skilled ethical hackers exploiting vulnerabilities to demonstrate real-world consequences. It’s goal-oriented—break into a system, extract data, or simulate ransomware deployment.
Red teaming is broader and more strategic. It includes physical access attempts, social engineering, and persistence strategies over weeks or months. Red teams mimic nation-state attackers or advanced persistent threats (APTs), often operating without the blue team’s prior knowledge.
Each method has value—but pen testing strikes the balance between realism and scope, making it ideal for quarterly security assessments and compliance-driven risk validation.
When & Why Companies Conduct Pen Tests
Organizations don’t just test randomly—they test at critical transition points:
Post-migration to cloud: To identify new access points, misconfigured buckets, or broken authentication flows in services like AWS, Azure, and GCP.
After deploying new applications: Especially for SaaS platforms, fintech apps, and health tech tools that store sensitive PII or payment data.
To meet compliance mandates: Standards like PCI-DSS, ISO 27001, and SOC 2 require regular pen testing from independent third parties.
Before mergers or acquisitions: To reveal technical debt, legacy system risks, or embedded malware/backdoors that could compromise deal integrity.
On a recurring basis: Many companies schedule biannual or quarterly pen tests to maintain audit readiness and ensure security investments are effective.
Ultimately, pen testing isn’t a checkbox—it’s a controlled fire drill that exposes what a threat actor could do tomorrow if your defenses falter today.
Evaluation Criteria: How We Ranked These Tools
The penetration testing tools featured in this guide weren’t chosen based on popularity alone. In 2025, with hundreds of open-source and commercial options available, we applied a focused and outcome-driven evaluation model to determine which tools offer the most real-world value to cybersecurity teams.
Our assessment prioritized features that directly impact operational efficiency, exploit reliability, cross-platform integration, and community traction—criteria that align with modern enterprise use cases and high-stakes security environments. Every tool listed has a proven record in live red team engagements, capture-the-flag (CTF) competitions, or production infrastructure assessments.
Cost, OS Compatibility, Ease of Use
Cost: Tools were evaluated on whether they are fully open-source, freemium, or commercial with licensing. A free tool isn’t inherently better unless its capabilities match or exceed premium competitors. Tools like Nmap and Kali Linux scored high here due to their free licensing and depth.
OS Compatibility: Versatility matters. We prioritized tools with native support across Windows, Linux, and macOS. Tools that integrate with cloud APIs (AWS CLI, Azure PowerShell) or mobile platforms were also ranked higher.
Ease of Use: We assessed interface clarity, CLI intuitiveness, documentation quality, and the learning curve for new users. Tools like Burp Suite and Metasploit scored high due to their GUI options, clear workflows, and in-tool help features that minimize onboarding time.
These criteria are critical when deploying tools in high-pressure scenarios, such as red team ops or zero-day simulations, where usability directly affects exploit success.
Community Support & Enterprise Readiness
Community Support: A tool is only as useful as its ecosystem. Active GitHub repos, frequent updates, plugin/module contributions, and Reddit or Stack Overflow engagement factored heavily. Tools with stagnant issue threads or minimal version control updates were deprioritized.
Enterprise Readiness: Features like integration with SIEMs, vulnerability management systems, automated report generation, and support for multi-user collaboration were must-haves for enterprise-grade evaluations. Tools such as Nessus and Core Impact deliver robust integrations that streamline enterprise workflows and compliance reporting.
This evaluation framework doesn’t favor trendiness—it rewards scalability, depth, and how well a tool enables ethical hackers to simulate high-fidelity attacks under real operational conditions.
Top Pen Testing Tools in 2025
Each tool below earned its spot based on real-world use cases, depth of capabilities, and adaptability across industries. Whether you're performing internal audits, red team simulations, or compliance-driven tests, these tools provide the technical edge required to identify and exploit vulnerabilities with precision.
Kali Linux
Kali Linux remains the gold standard for penetration testers. It’s a Debian-based distro preloaded with over 600 tools for scanning, exploitation, and post-exploitation tasks. Updated weekly, Kali supports ARM, VMware, and cloud installations. It’s optimized for rapid deployment in air-gapped environments, and its 2025 release includes native AI-based payload suggestions, making it ideal for seasoned testers who need everything in one place.
Metasploit Framework
Metasploit by Rapid7 is the industry’s go-to exploit development and payload testing tool. Its modular design allows ethical hackers to simulate thousands of attacks, from buffer overflows to social engineering payloads. The 2025 update improves Meterpreter’s stealth capabilities and adds better integration with containerized targets via Docker modules. It’s unmatched in exploit customization.
Burp Suite
Burp Suite is a powerful web application testing suite used by both individual researchers and enterprise red teams. It offers dynamic scanning, intercepting proxy capabilities, and a powerful plugin ecosystem. Burp's 2025 version features machine learning-based request clustering and smarter fuzzing engines for bypassing WAFs. Its Pro edition remains essential for testing OWASP Top 10 vulnerabilities.
Nessus
Developed by Tenable, Nessus leads in vulnerability assessment automation. It supports over 72,000 CVE checks and integrates seamlessly with Splunk and ServiceNow. The 2025 version expands its detection of container and IoT vulnerabilities, addressing a growing blind spot for many organizations. Nessus remains a top choice for compliance audits like PCI-DSS and HIPAA.
Nmap
Nmap is still unmatched for network discovery and port scanning. Its scripting engine (NSE) allows users to automate advanced reconnaissance tasks like SSL cipher enumeration, SMB fingerprinting, and version detection. The 2025 update added compatibility with IPv6-only environments and enhanced UDP scan reliability—key for testing hardened firewalls and segmented zones.
OWASP ZAP
Zed Attack Proxy (ZAP) from OWASP remains one of the best free dynamic application security testing (DAST) tools. It includes automated crawlers, attack mode, and custom scripting for web pentests. The latest version introduces headless scanning, making it ideal for CI/CD pipelines in agile dev environments. ZAP is lightweight, reliable, and endlessly extendable.
Wireshark
Wireshark is a deep packet inspection tool that remains essential for network-layer pentests. In 2025, its real-time anomaly detection module now flags suspicious traffic patterns during live sniffing, improving response workflows. It supports over 2,000 protocols and integrates with TShark for automation in enterprise testbeds.
| Tool | Primary Use | Key 2025 Feature |
|---|---|---|
| Kali Linux | All-in-one OS for pen testing | AI-based payload suggestions & weekly updates |
| Metasploit Framework | Exploit development & payload delivery | Container target modules & enhanced stealth |
| Burp Suite | Web application security testing | ML-based request clustering & WAF bypass fuzzing |
| Nessus | Vulnerability scanning & compliance | IoT & container vulnerability support |
| Nmap | Network mapping & port scanning | Improved UDP scans & IPv6 compatibility |
| OWASP ZAP | DAST for web apps | Headless scanning for CI/CD integration |
| Wireshark | Packet inspection & network forensics | Real-time anomaly detection module |
Common Pitfalls in Pen Testing & How to Avoid Them
Penetration testing fails not because tools are inadequate—but because execution lacks clarity, precision, or legal grounding. Even skilled red teamers risk derailing projects when core pitfalls are overlooked. Avoiding these missteps isn’t just about efficiency—it’s about preserving trust, avoiding liability, and ensuring real security value.
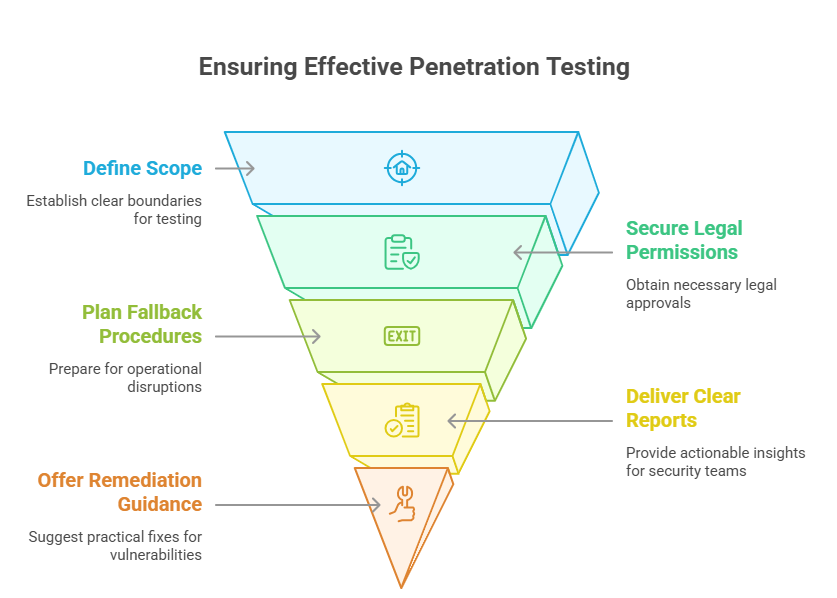
Scope Creep & Legal Boundaries
One of the most dangerous errors in penetration testing is exceeding the authorized scope. When boundaries aren’t clearly defined, testers can unintentionally disrupt production systems, trigger false alarms, or even violate data protection laws.
To avoid this:
Always get a written rules of engagement (ROE) document signed by stakeholders.
Define what is in-scope vs. out-of-scope: IP ranges, subdomains, physical devices, cloud assets.
Clarify whether social engineering, physical entry, or denial-of-service attacks are permitted.
Document fallback procedures in case a test negatively impacts operations.
Legal exposure increases when testers blur ethical lines. Even well-meaning red teams can cause compliance breaches or SLA violations if scope isn’t rigidly maintained. This isn’t a technical problem—it’s a communication one.
Lack of Post-Engagement Reporting
Many pen tests end when the last payload lands—but reporting is where real value begins. Skipping this phase renders the test almost useless to security teams, executives, and regulators.
A strong post-engagement report should include:
Executive summary for non-technical leadership: what was accessed, how, and business impact.
Detailed attack narrative: each exploit path, tool used, and target system affected.
Screenshots or logs proving access—without overloading the reader.
Risk classification using frameworks like CVSS or OWASP Risk Rating.
Prioritized remediation steps with references to patches, configurations, or best practices.
Without this documentation, the organization can’t fix the weaknesses uncovered. Worse, it can’t prove to auditors that meaningful testing occurred. And in regulated sectors, a missing report could become a non-compliance issue in itself.
Proper pen testing isn’t about break-ins—it’s about learning from them. And that learning only sticks when it’s clearly reported, presented, and acted upon.
The Future of Pentesting Tools: AI, ML, and Autonomous Red Teams
The next evolution of penetration testing isn’t just faster scanning—it’s autonomous offense. In 2025, artificial intelligence is redefining how red teams think, operate, and scale. Tools are no longer passive utilities. They’re becoming intelligent agents capable of making decisions, adapting payloads, and simulating human attackers with unprecedented realism.
Machine learning is already enhancing vulnerability prioritization by learning from past exploit outcomes. Instead of flagging every low-priority issue, ML models analyze contextual data—application stack, system criticality, network topology—and suggest the most impactful paths. This doesn’t just save time. It radically improves signal-to-noise ratio in enterprise assessments.
Autonomous red teams are also on the rise. Tools like SnapAttack, MITRE Caldera, and XM Cyber are pioneering platforms that emulate APT-level behavior using automated kill chains. These systems:
Chain vulnerabilities together dynamically based on network structure.
Modify TTPs (tactics, techniques, procedures) in response to blue team defenses.
Inject real-world adversary logic via MITRE ATT&CK and custom threat libraries.
This shift means pen tests no longer require constant human input to remain effective. Instead, ethical hackers become orchestrators—defining objectives, reviewing attack paths, and validating AI-generated exploit chains.
AI also enables smarter defense training. Red team simulations can now adapt in real-time to simulate multi-stage intrusions, including lateral movement, credential harvesting, and privilege escalation across hybrid cloud infrastructures. These simulations are harder to detect, mimic actual threat actors more accurately, and prepare defenders under pressure.
Yet, AI in pen testing isn’t without limits. Ethical oversight, false positives, and black-box decision-making remain concerns. But as models grow more transparent and customizable, they’ll increasingly become core components in any advanced pentesting toolkit—not to replace the human, but to supercharge them.
| Technology/Tool | Primary Function | AI/ML-Powered Capabilities |
|---|---|---|
| SnapAttack | Adversary emulation & threat hunting | Creates automated kill chains & adaptive testing paths |
| MITRE Caldera | Automated red teaming framework | Uses ML for TTP adaptation and AI for planning attacks |
| XM Cyber | Hybrid cloud breach simulation | Chains vulnerabilities using AI-based logic maps |
| Custom ML Models | Vulnerability prioritization | Ranks threats based on context: stack, topology, exposure |
| Red Team Simulations | Adaptive training exercises | Emulates multi-stage APTs across hybrid environments |
Mastering These Tools Through a Hands-On Certification Program
Penetration testing tools are not just for professionals already in the field—they're core components of structured cybersecurity education. In ACSMI’s Advanced Cybersecurity & Management Certification, hands-on use of tools like Metasploit, Burp Suite, and Kali Linux is embedded directly into the curriculum, ensuring students don’t just learn concepts—they deploy them in realistic attack scenarios.
This certification program emphasizes practical immersion over passive theory. Learners are placed into controlled lab environments that simulate enterprise networks, cloud stacks, and hybrid infrastructures. Within these labs, candidates use:
Nmap for reconnaissance, mapping live hosts and fingerprinting services.
Burp Suite for dynamic web testing, including session hijacking, XSS, and SQL injection attacks.
Metasploit for exploit chaining, privilege escalation, and reverse shell sessions.
Wireshark for network traffic analysis, decrypting packets and isolating indicators of compromise.
Students also complete offensive security challenges structured like real red team engagements—each requiring them to replicate APT techniques using the actual tools discussed in this guide.
Moreover, ACSMI’s certification maps directly to industry expectations: understanding tool integration into larger SIEM workflows, knowing how to document exploitation paths in formal reports, and presenting remediation guidance during tabletop simulations. Each tool becomes part of a broader skill set—not just for exams, but for field-ready consulting and security architecture roles.
By the end of the program, learners can build modular toolchains, write automation scripts for repetitive test cases, and distinguish between manual testing, semi-automated reconnaissance, and AI-augmented exploit modeling. No theoretical fluff—just real skills built around real tools, for real career outcomes.
Frequently Asked Questions
-
While the terms are often used interchangeably, penetration testing is a structured assessment with defined scope, goals, and reporting, whereas ethical hacking is a broader concept that encompasses all white-hat hacking practices. Pen testing is typically done in a professional or contractual context and is part of security compliance routines. Ethical hacking might also include bug bounties, red teaming, or research outside formal client engagements. Both require permission and legal clearance, but penetration testing is standardized, repeatable, and often tied to audit frameworks, whereas ethical hacking can be exploratory or research-driven without fixed engagement rules.
-
Kali Linux is the ideal entry point for beginners due to its preinstalled suite of tools and rich documentation. It allows users to explore scanning (Nmap), exploitation (Metasploit), web testing (Burp Suite), and wireless analysis (Aircrack-ng) all from one environment. The community support is massive, tutorials are widely available, and the learning curve is forgiving compared to fragmented tools. Beginners can also start with OWASP ZAP for web app security testing, as it has a GUI, tutorials, and step-by-step automation support. These tools offer safe, guided ways to explore penetration testing fundamentals without requiring advanced scripting skills.
-
Organizations should conduct penetration tests at least annually, though high-risk industries—such as fintech, healthcare, or cloud-native SaaS—may require quarterly or event-triggered assessments. Events like a major system upgrade, acquisition, or infrastructure shift (e.g., migrating to AWS) often justify immediate testing. Regulatory standards such as PCI-DSS mandate annual pen tests and additional tests after significant changes. Modern security posture demands continuous vulnerability assessment supplemented by deep-dive pen testing at strategic points. Frequency should reflect the organization’s threat model, regulatory obligations, and internal risk tolerance, with some firms integrating pen testing into DevSecOps pipelines for continuous validation.
-
Penetration testing tools are legal to possess and use, but legality hinges on context. Unauthorized scanning, exploitation, or data exfiltration is illegal and may violate cybersecurity laws like the Computer Fraud and Abuse Act (CFAA) in the U.S. or the Computer Misuse Act in the UK. Tools like Metasploit or Nmap are dual-use: they serve both legitimate and malicious purposes. To remain compliant, you must obtain explicit, written permission (scope document or rules of engagement) before conducting any test. In educational or lab environments, these tools are fully legal and critical for cybersecurity skill development.
-
Certifications that offer real-world labs and tool integration are best. The ACSMI Advanced Cybersecurity & Management Certification includes Metasploit, Burp Suite, Nmap, and Kali Linux in its syllabus. Other strong options include Offensive Security’s OSCP, which is hands-on and tool-heavy, and CompTIA PenTest+, which blends technical knowledge with risk reporting. Certifications should provide sandboxed environments where students perform actual exploit development, privilege escalation, and vulnerability chaining. Avoid programs with too much theory and no lab exposure. Choose credentials that align with red teaming practices and emphasize tool-based learning under controlled, legal conditions.
-
Yes—but not entirely. AI is transforming parts of the penetration testing workflow, such as vulnerability triage, exploit suggestion, and payload obfuscation. Tools like MITRE Caldera or XM Cyber use autonomous agents to simulate adversarial behavior. AI can chain exploits, mimic APT tactics, and analyze system configurations faster than humans. However, complete automation lacks the intuition, ethics, and creativity that human red teamers provide. For now, AI is best used as a force multiplier—augmenting human testers by reducing noise, suggesting attack paths, and creating adaptive simulations. Full automation remains a supplement, not a replacement.
-
Using outdated tools can result in missed vulnerabilities, false positives, or system crashes. Threat landscapes evolve quickly—zero-day exploits emerge, protocols get deprecated, and new evasion techniques are adopted. Old tools may fail to detect modern attack vectors or lack the modules required to assess new technologies (e.g., containers, serverless functions). They also pose operational risks: using legacy codebases with known bugs can crash production systems during testing. To maintain effectiveness, tools must be regularly updated, patched, and validated against the latest CVEs. Relying on obsolete tools undermines test credibility and exposes organizations to undetected risk.
Final Thoughts
Choosing the right penetration testing tools isn’t just about features—it’s about fitness for purpose. Whether you're simulating internal breaches, testing web application firewalls, or preparing for regulatory audits, the tools in this guide are proven, scalable, and adaptable to 2025’s evolving threat landscape.
But tools alone don’t create security maturity. Mastery comes from structured training, practical labs, and real-world application—precisely what the ACSMI Advanced Cybersecurity & Management Certification delivers. By combining tool fluency with scenario-based learning, this program bridges the gap between academic knowledge and operational expertise.
The most effective cybersecurity professionals aren’t just certified—they’re armed with the right tools, trained in how and when to use them, and capable of turning exploits into insights. Whether you’re upskilling for a red team role, advancing in a compliance-heavy industry, or building technical leadership credibility, penetration testing tools are now foundational—not optional.
Choose tools that align with your scope. Choose a certification that makes them second nature.
| Which Penetration Testing Tool Do You Think Is Most Essential in 2025? | |
|---|---|