Junior to Senior Penetration Tester to Career Path 2026
Most professionals enter cybersecurity with one goal in mind: mastering the skills that lead to high-impact, high-paying roles. For many, that journey starts with penetration testing — one of the most hands-on, technical, and in-demand specialties in the field. But what’s less clear is how to move from an entry-level role into a strategic leadership position like Senior Security Consultant.
This guide breaks that path down with surgical clarity. You'll discover what skills to build, which certifications to pursue, and how to gain real-world experience that actually advances your career. From the first vulnerability report to leading enterprise-level red team projects, this is your roadmap. No fluff. No filler. Just high-leverage moves that get you paid, respected, and positioned for top-tier roles in cybersecurity.
The Role of a Penetration Tester
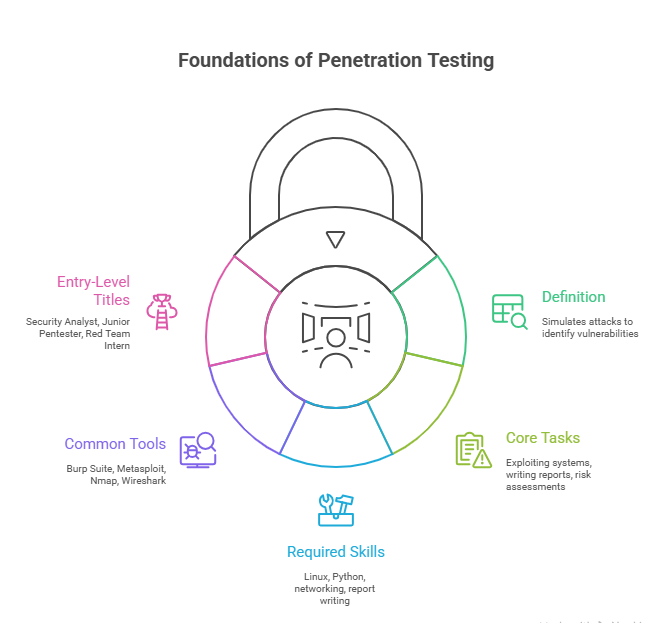
What is Penetration Testing?
Penetration testing, or ethical hacking, is the authorized simulation of cyberattacks against a system, application, or network to identify vulnerabilities before malicious actors exploit them. Unlike traditional security audits, pen testers operate from an attacker’s perspective, uncovering real-world weaknesses in defense mechanisms.
Their goal isn’t just to break in — it’s to document exactly how they did it, and how to fix it. This requires deep technical knowledge, creativity, and precision in reporting vulnerabilities that might otherwise go unnoticed. Pen testers bridge the gap between theoretical security and practical risk — which is why they're essential to any modern security program.
Key Skills Required for Penetration Testers
Penetration testers must be both technically sharp and strategically adaptive. It’s not about having a single skill — it’s about mastering a toolkit that evolves constantly.
Core skills include:
Strong command of networking protocols (TCP/IP, DNS, HTTP/S)
Familiarity with operating systems (Linux, Windows internals)
Proficiency in scripting (Python, Bash, PowerShell)
Understanding of common vulnerabilities (OWASP Top 10, CVEs)
Experience with testing tools (Burp Suite, Nmap, Metasploit, Wireshark)
Beyond technical skills, a great pen tester is also a sharp communicator. They must write clear, actionable reports and often present findings to both technical and non-technical stakeholders — a key skill that separates juniors from seasoned pros.
Career Growth in Penetration Testing
Penetration testing offers one of the most scalable career tracks in cybersecurity — but growth depends entirely on specialization and reputation.
Here’s what advancement typically looks like:
Junior Penetration Tester – Assists with scans, documentation, and script execution. Learns methodology under supervision.
Mid-Level Pen Tester – Leads individual tests, develops exploits, contributes to reporting, and begins mentoring.
Senior Penetration Tester – Designs and scopes full engagements, manages clients, and contributes to tool development.
Senior Security Consultant – Oversees multiple projects, provides strategic input, and aligns findings with business risk.
Career growth is accelerated by certifications, portfolio quality, and how well you communicate risk. You don’t just get promoted for being technical — you get promoted for being effective.
The Journey from Junior to Senior Penetration Tester
What Makes a Junior Penetration Tester?
A junior penetration tester is someone at the entry point of ethical hacking, typically with foundational knowledge of networks, systems, and basic vulnerability assessments. Juniors are rarely handed complex red-team engagements — instead, they work under senior direction, supporting tasks like scanning, enumeration, and basic scripting.
Key attributes of juniors include:
Comfort with tools like Nmap, Nessus, and Burp Suite
Basic scripting ability in Python or Bash
Understanding of common vulnerabilities and how to test for them
Strong documentation skills, especially in writing initial reports
Willingness to learn and shadow experienced testers
At this stage, depth isn’t expected — discipline, curiosity, and execution are. Your job is to get good at the fundamentals while soaking in real-world tactics from senior mentors.
Gaining Experience and Building a Portfolio
To move beyond the junior level, you must show proof — not just knowledge. Experience is the currency of credibility in offensive security, and a strong portfolio sets you apart in a saturated talent pool.
Here's how to build one strategically:
Join CTF platforms – Hack The Box, TryHackMe, and PortSwigger Labs show real exploit thinking.
Document your work – Write walkthroughs, case studies, or blog posts with technical depth.
Contribute to GitHub – Share custom scripts, automation tools, or writeups.
Volunteer for pro bono audits – Local nonprofits or student groups often need help. These are real-world engagements.
Request redacted reports – With permission, include project summaries in your professional portfolio.
A great portfolio proves you’re not just learning theory — you’re applying tactics with measurable results.
Transitioning to Senior Penetration Tester
The shift from junior to senior isn’t marked by years — it’s marked by ownership, impact, and strategy.
To level up, you need to:
Start scoping projects, not just executing them
Develop custom exploits, bypasses, and novel attack chains
Mentor others, review junior work, and elevate team performance
Manage client relationships, not just deliverables
Align technical findings with business risk — senior testers speak both “exploit” and “executive”
What gets you promoted is the ability to deliver value independently and communicate findings that drive change. It's not about breaking in — it’s about breaking in, documenting precisely how, and advising what it actually means to the business.
Key Certifications and Skills for Advancing Your Career
Certifications to Consider (e.g., CEH, OSCP)
Certifications are more than credentials — they’re trust signals that validate your capabilities to employers and clients. But not all certs are created equal. The right ones show not only that you understand the theory, but that you can apply it under pressure.
Here are high-impact certifications worth pursuing:
CEH (Certified Ethical Hacker) – Good foundational cert, especially for HR filters.
OSCP (Offensive Security Certified Professional) – Widely respected hands-on cert. Requires real exploit development.
CPTS (Certified Penetration Testing Specialist) – An excellent intermediate-level option offered through CCRPS.
GPEN (GIAC Penetration Tester) – Valuable if you're targeting DoD or compliance-heavy industries.
PNPT (Practical Network Penetration Tester) – Focuses on realistic scenarios and report writing.
The Certified Penetration Testing Specialist (CPTS) is particularly ideal for those who want deep practical skills without inflated costs. It’s focused, modern, and designed to bridge junior-to-senior gaps quickly.
Essential Technical and Soft Skills
To advance in penetration testing, your stack needs to evolve. It’s not just about knowing tools — it’s about thinking critically, solving creatively, and communicating clearly.
Technical skills to master:
Manual exploitation techniques (buffer overflows, privilege escalation)
Active Directory attacks (Kerberoasting, Golden Ticket)
Web app exploitation (XSS, IDOR, SQLi)
Scripting and automation (Python, PowerShell)
Malware analysis basics (reverse engineering, sandboxing)
Soft skills that set seniors apart:
Report writing – Clear, precise, and business-relevant
Client communication – Present findings with impact
Team collaboration – Mentor juniors, coordinate with developers
Time management – Deliver under pressure with minimal oversight
Your skillset needs to scale beyond the shell — you must deliver technical results that translate into business clarity.
Gaining Hands-On Experience
Certs are great, but they don’t replace sweat equity. Real advancement comes from solving real problems in real systems. Here’s how to gain hands-on experience that matters:
Lab practice – Invest in platforms like Hack The Box Pro Labs, CyberSecLabs, or Offensive Security’s PWK labs.
Red team exercises – Join internal or freelance projects where you run full attack simulations.
Bug bounty platforms – Programs like HackerOne and Bugcrowd allow you to hunt vulnerabilities on live systems legally.
Freelance gigs – Platforms like Upwork or direct client outreach can help you secure your first engagements.
Contribute to OS projects – Help security teams test their open-source tools.
Hands-on means more than breaking in — it means delivering insights, documenting risks, and improving defenses. That’s how you grow.
| Certification | Purpose | Provider |
|---|---|---|
| CEH | Ethical hacking fundamentals | EC-Council |
| OSCP | Hands-on offensive security techniques | Offensive Security |
| GPEN | Pen testing methodologies and best practices | GIAC |
| Soft Skills | Communication, leadership, project delivery | General/Workshops |
| Hands-on Skills | Network pentesting, web app security | Labs, Real-World Practice |
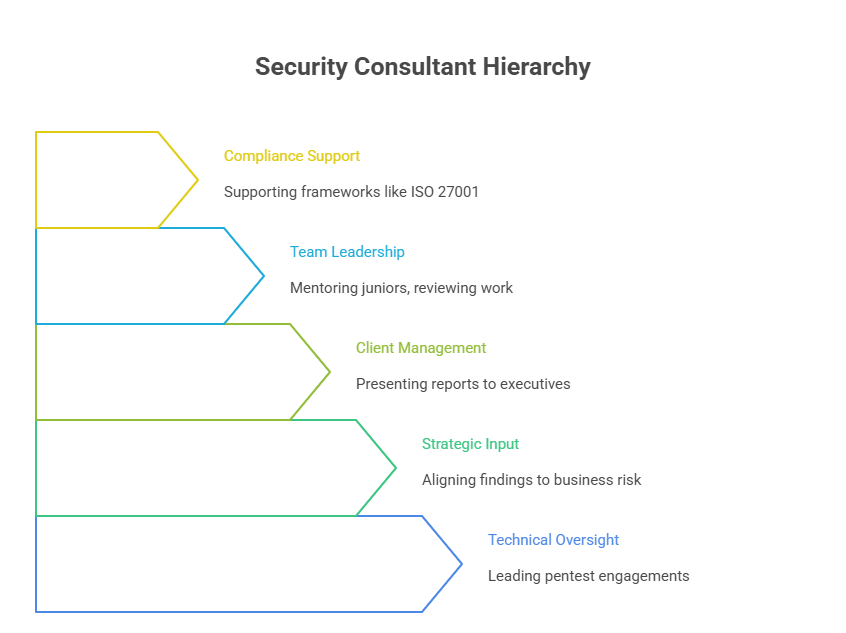
Responsibilities of a Senior Security Consultant
Overview of the Senior Security Consultant Role
A Senior Security Consultant is not just a highly skilled hacker — they are a strategic advisor, project leader, and client-facing authority. Unlike penetration testers focused purely on execution, consultants interpret findings through the lens of risk, impact, and business priorities.
Core expectations include:
Leading full-scope assessments (web, network, cloud, and physical)
Communicating findings to technical teams and executive stakeholders
Mapping vulnerabilities to compliance frameworks (NIST, ISO 27001, PCI-DSS)
Scoping, pricing, and architecting engagements end-to-end
Mentoring junior testers and overseeing quality assurance
Consultants don’t just test — they translate complex security issues into actionable business decisions.
Leading Penetration Testing Projects
Running a pentest project as a senior means taking full ownership — from client kickoff to final debrief. You’re expected to balance depth with delivery, ensuring engagements are thorough, ethical, and on time.
What this typically includes:
Scoping the engagement – Define objectives, limitations, and rules of engagement.
Planning logistics – Schedule team members, tools, and timeframes.
Executing attacks – Deploy targeted recon, exploitation, and post-exploitation techniques.
Reporting and validation – Draft reports that map findings to impact, then validate fixes.
Debriefing clients – Deliver findings with clarity, urgency, and remediation guidance.
Success is measured not just by how many systems you break into, but by how clearly you show clients what matters and what to do next.
Client Management and Strategic Guidance
Senior consultants sit at the intersection of technical execution and strategic influence. Clients rely on you to translate vulnerabilities into prioritized action plans that align with business goals.
To do this well:
Tailor communication by audience – CISOs care about impact and compliance; developers want reproducibility and fix paths.
Understand the client's industry – Know the regulatory landscape and attack surface specifics.
Push for remediation, not just reporting – The job isn't done until risks are addressed.
Build long-term trust – Most senior roles are relationship-based, not transactional.
A good senior consultant doesn’t just find vulnerabilities. They help build security programs that evolve and scale.
Networking and Professional Development in Cybersecurity
Joining Cybersecurity Communities
If you’re not plugged into the right communities, you’re falling behind. Cybersecurity moves fast, and communities are where the real-time learning happens. They’re also where referrals, collaborations, and job leads flow freely — often before they hit job boards.
Start with:
Slack groups and Discord servers like The Many Hats Club, Cyber Mentoring Monday, and Red Team Village
Reddit subs like r/netsec, r/cybersecurity, and r/AskNetsec
Twitter/X circles where researchers share zero-days, tools, and frameworks
LinkedIn groups focused on offensive security or bug bounty hunting
Local meetups and DEFCON groups (DCGs) for in-person connection
The key isn’t just joining — it’s showing up. Ask questions, share findings, and contribute. This builds your reputation, and people refer the names they remember.
Attending Industry Conferences and Seminars
Conferences aren't just for learning — they’re prime ground for networking, visibility, and professional growth. Whether you're attending virtually or in person, every event is an opportunity to meet hiring managers, tool creators, or future collaborators.
Target these events:
DEF CON – The hacker Olympics. Red teamers, researchers, and toolmakers in one place.
Black Hat – Enterprise-level insight meets bleeding-edge research.
BSides – Community-driven, accessible, and packed with rising stars.
ShmooCon, Wild West Hackin’ Fest, and Hack In The Box – Niche but high-value conferences.
To get the most out of any event:
Don’t just attend — submit talks or workshops
Network with purpose — know who you want to meet
Share takeaways on LinkedIn or in blogs — it positions you as a thought leader
Your next opportunity often doesn’t come from a job posting — it comes from someone remembering your name at a conference.
| Method | Benefit |
|---|---|
| Conferences | Learn latest threats, tools, and network with peers |
| Online Forums (e.g., Reddit) | Community learning and reputation building |
| Certifications | Formal proof of knowledge and expertise |
| Social Media | Build personal brand, share insights and content |
| Mentorship | Accelerate growth through expert guidance |
How the Cybersecurity Certification by ACSMI Accelerates Your Career Path
Why Certification Validates Your Career Growth
Without certification, your resume is just a claim. With one, it’s a statement. The Cybersecurity Certification by ACSMI gives aspiring and experienced professionals the structured knowledge, credibility, and industry-backed validation that employers look for when hiring or promoting for penetration testing and security consultant roles.
This certification signals that you’ve mastered:
Core offensive security principles and practical testing methodology
Real-world application of tools and tactics across systems and networks
Ethical guidelines, client communication, and compliance-awareness
In a saturated market, ACSMI certification is the edge that moves your resume from the stack to the shortlist.
Where Certification Fits Along the Junior–Senior Journey
Whether you're just starting out or pivoting from mid-level, the ACSMI Cybersecurity Certification is designed to plug into your career trajectory.
As a junior penetration tester, it helps you:
Build foundational skills in recon, exploitation, and reporting
Learn how to operate in professional pentest environments
Understand frameworks like OWASP and MITRE ATT&CK
Gain hands-on experience through labs and assessments
As you move toward a senior security consultant role, it strengthens your ability to:
Lead assessments with strategic focus
Communicate findings in a business-aligned way
Coach others and contribute to secure architecture discussions
Bridge gaps between red team findings and executive decisions
It’s not just about what you know — it’s about showing you can apply it in live-fire situations with confidence.
Standing Out in a Crowded Cybersecurity Market
Certifications like CEH and OSCP are valuable — but the Cybersecurity Certification by ACSMI stands out for its balance of technical depth and real-world consulting focus. It’s not just built for test takers — it’s built for future leaders.
With ACSMI certification:
You’re recognized as ready to work in actual consulting environments
You gain access to a network of experts, mentors, and hiring partners
You demonstrate both technical skills and business literacy, which most hiring managers find rare
You differentiate yourself from the thousands of “certified but inexperienced” candidates flooding the market
In short: If you want to go from executing payloads to advising on risk at the board level, ACSMI’s certification is your launchpad.
Frequently Asked Questions
-
On average, it takes 3–5 years to transition from a junior role to senior security consultant — but it depends entirely on how quickly you build relevant skills, certifications, and field experience. Juniors who actively pursue hands-on labs, contribute to projects, and invest in certifications like the Cybersecurity Certification by ACSMI often accelerate this timeline. The key is proving not just technical proficiency but leadership, communication, and strategic thinking. Progression isn’t automatic; it’s earned by showing you can scope projects, lead clients, and communicate risk clearly. Those who treat every project like a case study for growth tend to move up faster than those who stay task-focused.
-
No — while degrees can help open doors, they’re not required. In fact, many senior consultants come from non-traditional backgrounds and are self-taught or transitioned from IT, engineering, or even liberal arts. What matters more than academic background is proof of competence. Certifications like the Cybersecurity Certification by ACSMI give you validated credibility without needing a university pathway. When paired with real-world experience, a portfolio of work, and strong communication skills, certification is more than enough to get hired, promoted, or contracted by enterprise clients. The industry prioritizes skills over diplomas, especially for offensive security roles.
-
Both certifications serve different purposes. OSCP is well-known in the offensive security community for its hands-on, exploit-focused approach. It’s excellent for building core hacking skills. However, the Cybersecurity Certification by ACSMI takes a broader view — combining penetration testing expertise with strategic consulting, client communication, and report delivery. If your goal is to become a well-rounded consultant who can both hack and advise, ACSMI’s certification is the better choice. It’s especially valuable for those looking to progress into roles like senior consultant, red team lead, or vCISO, where business alignment is as important as technical skill.
-
Juniors should start with foundational tools that cover the full testing lifecycle. These include:
Nmap for reconnaissance
Burp Suite for web application testing
Nikto and Dirbuster for enumeration
Metasploit for exploit testing
Wireshark for packet analysis
Gobuster, Hydra, and John the Ripper for brute-force and cracking tasks
As skills progress, juniors can move into more advanced tools like Cobalt Strike or custom scripting with Python. The Cybersecurity Certification by ACSMI offers structured exposure to these tools in lab environments, helping testers go beyond tool usage into attack strategy and reporting, which is essential for career advancement.
-
Report writing is critical. It’s not enough to find vulnerabilities — you must articulate the risk clearly to both technical and business stakeholders. Poor reporting undermines good technical work. Senior consultants are expected to write reports that:
Explain vulnerabilities in plain language
Include exploit paths and remediation steps
Prioritize based on business impact
Align findings with compliance standards like NIST or PCI-DSS
The Cybersecurity Certification by ACSMI trains you in real-world reporting, including formatting, language, and executive summary writing. Mastering this skill makes you more promotable and trusted in client-facing roles — especially when advising C-level executives.
-
Yes. The ACSMI certification is designed with consultants in mind, not just job-seekers. Its focus on communication, risk assessment, and client engagement makes it ideal for professionals aiming to build their own brand or work independently. Having the certification on your website, LinkedIn, or proposals signals to clients that you have formal training and strategic understanding, not just technical skills. It also prepares you to scope, price, and deliver your own engagements. Many freelancers use their ACSMI-backed credential to justify higher rates, gain client trust faster, and stand out in platforms like Upwork, Toptal, and LinkedIn.
-
While technical expertise gets you in the door, soft skills move you up the ladder. As a senior security consultant, you must:
Communicate complex findings clearly to non-technical clients
Manage time effectively across multiple projects
Lead teams of juniors or collaborate across departments
Negotiate and influence during remediation or planning meetings
Write persuasive, executive-ready reports
The Cybersecurity Certification by ACSMI integrates these skills into its framework — with modules on client presentations, stakeholder communication, and translating vulnerabilities into business-aligned priorities. These abilities often determine your career ceiling more than tool mastery ever will.
Conclusion – Final Thoughts
Advancing from junior penetration tester to senior security consultant isn’t about waiting your turn — it’s about earning your seat. Every project, every report, every exploit is a step in that journey. But technical skills alone won’t get you there.
The leap happens when you combine hands-on expertise with strategic thinking, clear communication, and business alignment. That’s what separates hackers from consultants — and it’s where the Cybersecurity Certification by ACSMI becomes a pivotal asset. It validates your skills, proves your value, and prepares you to lead.
Whether you're just getting started or already halfway there, use your current role as a training ground. Build your reputation, sharpen your skills, and position yourself as the consultant who delivers clarity, not just code.