How to Become an Ethical Hacker: Comprehensive Career Roadmap
Cybercrime is growing at an unprecedented rate—and so is the demand for professionals who can stop it. Ethical hackers, also known as white-hat hackers, use their skills to find vulnerabilities before malicious actors do. They're not just testers; they're frontline defenders trusted to secure networks, applications, and infrastructure against real-world threats.
In today’s threat landscape, ethical hacking isn’t optional—it’s essential. Organizations now hire internal hackers to conduct authorized attacks, exposing weaknesses and fortifying defenses before adversaries strike. But becoming one takes more than curiosity and code. It requires a structured plan, technical expertise, hands-on experience, and strategic certifications like the Certified Ethical Hacker (CEH). This guide breaks down exactly how to move from beginner to paid professional—without wasting time on fluff or outdated advice.
What is Ethical Hacking?
Ethical hacking is the practice of intentionally probing systems, networks, and applications to find security flaws—with full authorization and legal approval. These professionals think like attackers but act in defense of organizations. Their job is to uncover vulnerabilities before malicious hackers can exploit them.
Unlike criminal hackers, ethical hackers operate within strict boundaries. Every engagement is documented, scoped, and authorized—often through legally binding contracts and nondisclosure agreements. The process may mimic real attacks, but the goal is prevention, not damage.
Ethical hackers perform:
Vulnerability scanning
Penetration testing
Social engineering simulations
Security audits and risk assessments
But this isn’t a free-for-all. Ethical hacking is bound by core principles:
Do no harm—systems must remain operational
Maintain confidentiality—no data should be leaked or altered
Gain explicit consent—no testing without written approval
The best ethical hackers blend technical expertise with strict discipline. They follow frameworks like OWASP and MITRE ATT&CK while documenting every step with forensic precision.
In today’s high-risk digital world, ethical hacking is no longer niche—it’s mission-critical. It’s how top organizations validate their defenses before attackers do, and why certified professionals are increasingly being hired directly into security teams, not just as consultants.
Key Skills Required for Ethical Hacking
To become a high-value ethical hacker, you need more than tool knowledge. You must understand how systems work, how attackers think, and how to exploit and defend at scale. The following core skill sets form the technical foundation for any ethical hacker.
Networking and System Administration
Ethical hackers must be fluent in:
TCP/IP, DNS, HTTP/HTTPS, and common protocols
Packet analysis with tools like Wireshark
Firewall configurations, routing, and segmentation
Equally important is a strong grasp of Windows and Linux administration—from user permissions to shell commands. If you can’t navigate an OS at the command line, you’ll miss critical paths of attack or defense.
Vulnerability Assessment
You’ll need to:
Run scans using tools like Nessus or OpenVAS
Analyze CVEs and CVSS scores for severity and exploitability
Prioritize vulnerabilities based on risk—not just technical presence
Ethical hacking isn’t just about finding flaws—it’s about identifying which ones are actually exploitable and business-relevant.
Penetration Testing
Pen testing is where theory meets real-world execution. Skills here include:
Manual exploitation using tools like Metasploit or Burp Suite
Writing and customizing scripts in Python, Bash, or PowerShell
Creating detailed, executive-friendly reports that explain risks clearly
Penetration testers are measured by impact, not noise. Precision matters more than tool overload.
How to Start Your Ethical Hacking Career
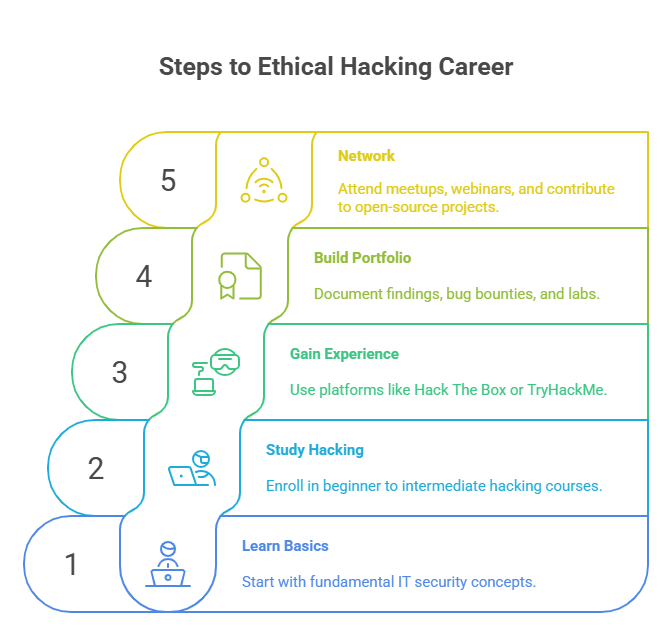
Breaking into ethical hacking doesn’t require a degree, but it does demand strategic learning, real-world practice, and credentialed proof. The journey starts with foundational knowledge and grows through hands-on experience and structured certifications.
Learning the Basics of Cybersecurity
Before you can hack ethically, you must understand how systems are built and broken. Start by studying:
Operating systems (Linux and Windows)
Networking fundamentals (OSI model, routing, firewalls)
Common attack vectors (phishing, injection, misconfigurations)
Use platforms like TryHackMe, Hack The Box, or Cybrary to apply what you learn. Your goal isn’t memorization—it’s internalizing how attackers move through networks.
Enrolling in Ethical Hacking Courses
Once the basics are clear, level up through guided programs. Look for:
CEH prep courses (available via EC-Council, Udemy, LinkedIn Learning)
Practical labs that include real-world exploit scenarios
Courses that teach both offensive and defensive perspectives
Don’t chase quantity—one solid course with hands-on labs beats five theoretical ones.
Gaining Hands-on Experience
Experience is your credibility. Start with:
Home labs using VirtualBox or VMware
Bug bounty programs on platforms like HackerOne or Bugcrowd
Open-source contribution to security tools
Document everything. Blogs, GitHub repos, or walkthroughs show employers you’re not just learning—you’re executing under real conditions.
Certifications for Ethical Hackers
Certifications separate hobbyists from professionals. They prove to employers that you not only understand theory but can execute in controlled, tested environments. The right certification can drastically increase your hiring potential and starting salary.
CEH (Certified Ethical Hacker)
The Certified Ethical Hacker (CEH) is one of the most recognized credentials in the industry. Issued by EC-Council, CEH validates your ability to:
Conduct ethical attacks using real-world tools
Understand system vulnerabilities and attack vectors
Follow legal, regulatory, and compliance standards
CEH is often requested in job descriptions because it’s mapped to DoD 8140 and accepted across both corporate and government roles. It’s ideal for entry- to mid-level professionals looking to validate their offensive security knowledge.
OSCP (Offensive Security Certified Professional)
The OSCP by Offensive Security is considered the gold standard for hands-on penetration testing. Unlike CEH, OSCP requires:
Solving live challenges in a controlled environment
Writing a full penetration test report
Demonstrating persistence, creativity, and discipline under pressure
It’s harder to earn but extremely valuable for technical credibility. If you want to be taken seriously by Red Teams or security consulting firms, OSCP can be a career-changer.
| Certification | Focus Area | Provider |
|---|---|---|
| CEH | Tool-based penetration testing | EC-Council |
| OSCP | Hands-on exploitation and report writing | Offensive Security |
| ACSMC | Strategic, technical, and management-level cybersecurity skills | ACSMI |
| CompTIA Security+ | Foundational cybersecurity knowledge | CompTIA |
| eJPT | Entry-level penetration testing | INE (eLearnSecurity) |
Career Opportunities for Ethical Hackers
Ethical hackers are no longer limited to penetration testing firms. Organizations across every sector—finance, healthcare, tech, defense—now hire full-time security professionals to think like attackers and protect proactively. The following roles are common and often overlap in responsibilities.
Penetration Tester
Pen testers simulate real attacks to find exploitable vulnerabilities. They:
Execute controlled intrusions on apps, networks, or hardware
Write detailed reports outlining technical flaws and remediation strategies
Collaborate with development and infrastructure teams to fix gaps
If you're skilled in scripting, evasion techniques, and toolkits like Metasploit or Burp Suite, penetration testing is a direct path with high demand and frequent freelance opportunities.
Security Consultant
Security consultants advise companies on how to secure systems, processes, and teams. They:
Perform audits, risk assessments, and threat modeling
Design multi-layered security architectures
Tailor defense strategies to the organization’s maturity and resources
This role blends technical depth with communication skills. It’s ideal if you can translate exploits into boardroom language.
Incident Responder
Responders contain and mitigate active threats. They:
Analyze attack timelines, malware behavior, and lateral movement
Coordinate with SOC teams, legal, and compliance during breaches
Implement lessons learned into new detection rules and response playbooks
Strong responders are in constant demand because every second lost costs money, data, and trust.
| Role | Description |
|---|---|
| Penetration Tester | Conducts authorized simulated attacks to test system defenses |
| Security Consultant | Advises companies on improving security architecture and strategy |
| Incident Responder | Detects, investigates, and responds to security breaches and alerts |
| Threat Hunter | Proactively identifies hidden or emerging cyber threats in networks |
| Security Engineer | Designs and implements secure system and network configurations |
Why the ACSMC Certification Is a Smart Investment for Aspiring Ethical Hackers
The Advanced Cybersecurity & Management Certification (ACSMC) by ACSMI isn’t just another security credential—it’s a career catalyst. While many entry-level certifications focus on tools and theory, ACSMC trains you to think like a hacker and operate like a security strategist.
What sets it apart:
Coverage of both technical exploitation and managerial oversight
Deep dives into modern vulnerabilities, Red Team workflows, and security operations
Governance, compliance, and business-aligned cybersecurity decision-making
For aspiring ethical hackers, this means you don’t just know how to exploit a flaw—you understand the risk context, escalation path, and strategic response. That’s the skillset employers want when hiring for penetration testers, incident responders, and security engineers.
The ACSMC credential is ideal if you’re serious about turning ethical hacking into a sustainable, long-term career—not just a technical side path.
Frequently Asked Questions
-
Ethical hacking involves legally probing systems for vulnerabilities, with permission from the system owner. Unlike malicious hackers who exploit weaknesses for gain or disruption, ethical hackers use their skills to prevent breaches. They perform penetration tests, simulate attacks, and recommend fixes. The difference isn’t just intent—it’s process. Ethical hackers follow strict guidelines: written approval, defined scope, and zero tolerance for data tampering or system damage. Most work with enterprises, governments, or consulting firms. Certifications like the Advanced Cybersecurity & Management Certification (ACSMC) teach not only the technical skills but also the legal and ethical boundaries required to operate responsibly and professionally in this space.
-
No, a degree is not required to become an ethical hacker. What you need is hands-on technical skill, structured training, and a strong ethical foundation. While some employers may prefer a degree in computer science, many prioritize experience, portfolios, and certifications. Online labs, Capture The Flag (CTF) challenges, and practical assessments often matter more than a transcript. Certifications like ACSMC validate that you understand modern vulnerabilities, threat modeling, and strategic mitigation—not just textbook theory. If you can prove you understand networks, exploit vectors, and can responsibly test systems, you’re already competitive—degree or not.
-
Ethical hackers benefit from learning languages that help them automate tasks, manipulate data, and analyze systems. The top priorities are:
Python – Widely used for scripting, exploit development, and automation.
Bash – Essential for Linux environments and command-line operations.
JavaScript – Crucial for web application testing, especially for XSS.
PowerShell – Valuable in Windows environments for post-exploitation and enumeration.
The goal isn’t to become a full-stack developer, but to understand enough code to read exploits, write payloads, and debug attack paths. Many ACSMC-aligned training programs include Python scripting labs, helping you go from reading to deploying scripts that matter in real-world penetration tests.
-
Vulnerability scanning uses automated tools to identify known weaknesses—like outdated software or open ports. It’s broad but shallow. Penetration testing goes further by manually exploiting those weaknesses to assess impact. It simulates what a real attacker would do after discovering a flaw. Pen testers verify whether a vulnerability is exploitable, chain attacks together, and test defenses in context. They also document everything, from technical steps to business risk exposure. Tools like Nessus help with scanning; Metasploit, Burp Suite, and custom scripts are used in pen testing. Certifications like ACSMC teach you to perform both—and explain when each is appropriate.
-
You don’t need a job to get real experience—you need a lab and a strategy. Start with:
TryHackMe and Hack The Box – Gamified platforms for attack simulation.
Home labs using VirtualBox or VMware – Build networks, simulate attacks, test defenses.
Bug bounty platforms – HackerOne, Synack, and Bugcrowd let you test real systems with legal permission.
Document your findings on a blog or GitHub repo. Employers love to see proof you’ve solved real problems. Many ACSMC candidates build portfolios of write-ups, scripts, or walk-throughs that show they’re already operating like ethical hackers—regardless of formal job titles.
-
Entry-level ethical hackers typically earn $65,000–$85,000 per year, depending on region and certifications. With 2–3 years of experience and a credential like ACSMC, salaries can climb to $95,000–$120,000, especially in tech hubs or government sectors. Freelance bug bounty hunters can earn more if they’re skilled and consistent. Salaries grow quickly because the role is specialized, high-impact, and in demand. Once you prove you can find exploitable flaws, write clear reports, and work within ethical boundaries, your value multiplies. Add soft skills and cross-team collaboration, and you’re looking at six-figure opportunities within 3–5 years.
-
The Advanced Cybersecurity & Management Certification (ACSMC) helps you stand out by combining hands-on hacking skills with strategic and operational security management. While most certifications focus on tools, ACSMC teaches how to lead penetration tests, manage incidents, and align findings with business risk. It’s ideal if you want to be more than a technician—if you want to own entire engagements or lead Red Teams. Employers value ACSMC because it signals maturity: you understand both attack execution and post-breach recovery, along with compliance, documentation, and stakeholder reporting. It’s a full-spectrum credential for ethical hackers aiming to lead.
Conclusion
Becoming an ethical hacker isn’t just about mastering tools—it’s about developing a mindset, a method, and a mission to protect digital systems. From learning the fundamentals of cybersecurity to building hands-on experience through labs and certifications, each step you take solidifies your path in this fast-growing field.
To truly stand out, align your skills with industry-recognized credentials like the Advanced Cybersecurity & Management Certification (ACSMC) by ACSMI. It doesn’t just validate your technical capabilities—it positions you as a future leader in the cybersecurity ecosystem.
If you’re ready to transition from enthusiast to expert, now is the time to take the leap. The demand is real. The risks are evolving. And organizations need professionals who can ethically outsmart attackers before damage is done. Be that professional.