Guide to Becoming a Security Operations Center (SOC) Analyst
In the evolving world of cybersecurity, SOC analysts are the frontline defenders against digital threats. As cyberattacks grow in scale and sophistication, companies need skilled professionals who can detect, analyze, and respond to incidents in real-time. The Security Operations Center (SOC) is where this defense happens, and SOC analysts are the specialists who keep networks, data, and infrastructure safe 24/7.
If you're considering a career in cybersecurity, 2025 is the time to act. With rising demand, competitive salaries, and clear certification pathways, becoming a SOC analyst is one of the most accessible and high-impact roles you can pursue. This guide will walk you through everything—from skills and tools to certifications and job strategies—so you can step into the role with confidence. Whether you're a student, IT professional, or career switcher, this is your complete roadmap to getting hired as a SOC analyst in today’s threat landscape.
What is a Security Operations Center (SOC) Analyst?
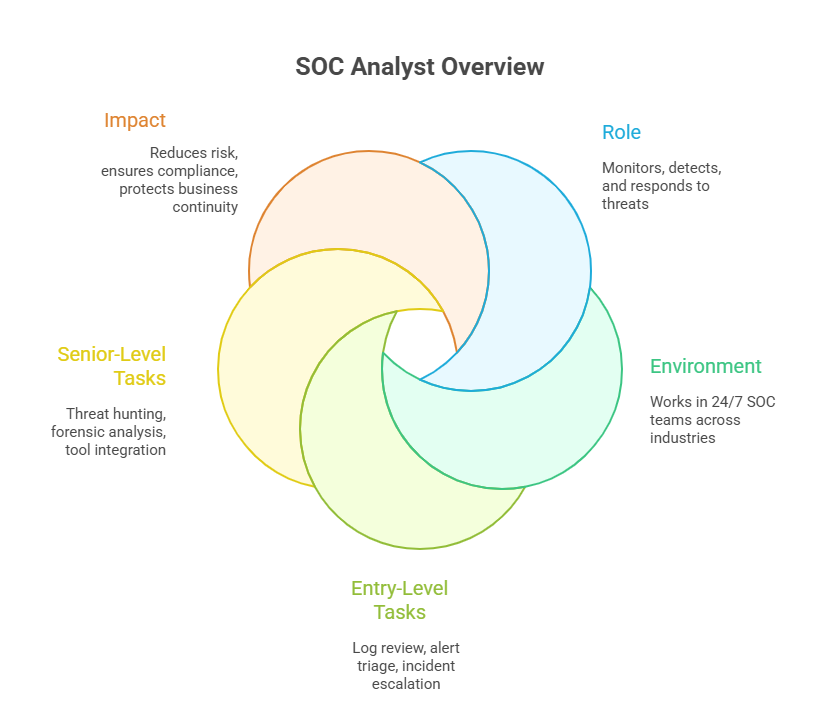
A SOC analyst is a cybersecurity professional responsible for monitoring, detecting, investigating, and responding to security events within an organization. They work inside a centralized Security Operations Center (SOC), using advanced tools to analyze suspicious activity, escalate threats, and coordinate mitigation efforts in real-time. This role is vital for protecting critical infrastructure and sensitive data from evolving cyber threats.
SOC analysts work in shifts to maintain 24/7 coverage across industries like finance, healthcare, defense, and technology. Their work reduces risk, supports compliance, and helps organizations react fast to intrusions. Entry-level analysts start with event triage, while senior analysts often lead incident response or threat hunting. The position offers fast-track opportunities into threat intelligence, red teaming, and cybersecurity engineering.
Key Responsibilities and Daily Tasks
A SOC analyst’s daily tasks center on threat detection and response. This includes reviewing alerts generated by SIEM tools, analyzing logs from firewalls and endpoints, and escalating confirmed incidents to senior staff or response teams. Analysts are also expected to investigate anomalies, correlate events, and document every action in detailed reports.
They must distinguish between false positives and real threats quickly. This demands strong pattern recognition, fast decision-making, and fluency in the organization’s security protocols. In advanced SOCs, analysts may also conduct proactive threat hunting to uncover stealthy intrusions before damage occurs.
Required Skills and Knowledge for SOC Analysts
SOC analysts need both technical skills and analytical thinking. On the technical side, they must understand networking protocols, operating systems (especially Linux and Windows logs), and basic scripting (Python or Bash). Familiarity with firewalls, IDS/IPS, and SIEM platforms like Splunk or QRadar is also essential.
Soft skills are just as important. Analysts must communicate clearly under pressure, collaborate with team members across shifts, and document findings with precision. Curiosity is key—great SOC analysts think like attackers, constantly learning new tactics and adapting fast. Entry-level analysts aren’t expected to know everything, but strong foundational knowledge and rapid learning ability are non-negotiable.
Required Education and Certifications for SOC Analysts
Becoming a SOC analyst doesn’t require a traditional four-year degree—but it does require verified technical competence. Employers often value certifications and real-world skills over formal credentials, especially in entry-level roles. That said, a relevant academic background can strengthen your resume and fast-track your growth into senior roles.
Most SOC job descriptions list a mix of education, certifications, and hands-on experience. The more closely aligned your qualifications are with industry tools and security frameworks, the faster you’ll stand out. Below is a breakdown of what’s essential in both certification and academic tracks to position yourself competitively in 2025 and beyond.
Must-Have Certifications for SOC Analysts
Certifications prove your readiness. They show hiring managers that you understand cyber fundamentals and can operate effectively within a SOC environment. The most common entry-level certification is CompTIA Security+, which covers threat types, risk mitigation, and compliance basics. For more advanced roles, Certified SOC Analyst (CSA) or Certified Cybersecurity Analyst (CySA+) offer SOC-specific training.
Tools-focused certifications like Splunk Core Certified User or IBM QRadar SIEM Certification also carry weight if you're applying to organizations that use those platforms. These certifications demonstrate operational readiness—not just theoretical knowledge—and can significantly improve your chances in technical interviews or skill tests.
Formal Education Requirements
While not always required, a degree in cybersecurity, information technology, or computer science helps build a deeper foundation. It shows employers you’ve studied core topics like networks, databases, and systems architecture. That said, it’s increasingly common for bootcamp graduates and self-taught analysts to land SOC roles—especially when paired with strong certifications.
Community colleges and online universities now offer associate degrees in cybersecurity that align closely with industry needs. For career switchers, fast-track programs or government-funded training often fill the gap. What matters most isn’t the diploma—it’s whether your education has prepared you to read logs, interpret alerts, and take action under pressure.
If you pursue formal education, pair it with certification and practical labs. Employers prioritize candidates who can hit the ground running, not just those with academic theory.
Essential Tools and Technologies for SOC Analysts
Every SOC analyst operates in a tool-driven environment. From monitoring dashboards to forensic platforms, the effectiveness of your work depends on how well you can navigate security tools. Tools don’t just assist—they define your speed, accuracy, and impact. While tool preferences vary by organization, there are core technologies that every SOC analyst must understand to operate in a live security environment.
At the heart of most SOCs is a Security Information and Event Management (SIEM) platform. Analysts also rely on incident response systems, endpoint detection tools, and forensic utilities to trace attacks and validate threats. Below, we break down the two most critical tool categories that shape your daily workflow.
SIEM Tools and Their Importance
SIEM platforms aggregate and analyze data from across the organization’s IT systems. They collect logs from firewalls, servers, endpoints, applications, and cloud services—giving SOC analysts a unified view of network activity. This is where alerts are triggered, events are correlated, and patterns of suspicious behavior are flagged.
Popular tools include Splunk, IBM QRadar, LogRhythm, and Elastic SIEM. Mastering even one of these platforms can give you an edge in hiring. You’ll need to understand how to configure alerts, write queries, and interpret log data at scale. SIEM proficiency is one of the top requirements in SOC job descriptions.
Incident Response and Forensics Tools
Beyond detection, SOC analysts must investigate and act. Incident response tools help manage the lifecycle of a security incident—from initial detection to resolution. Platforms like TheHive, Cortex XSOAR, or Microsoft Sentinel allow analysts to assign incidents, automate playbooks, and track threat containment.
For deeper analysis, forensic tools like Wireshark, Autopsy, FTK, or Volatility are used to trace the attacker’s path, recover deleted files, or analyze memory dumps. While not always used daily, knowing how to pivot to these tools during escalations makes you indispensable.
The most successful SOC analysts build muscle memory with these platforms. They not only respond faster but understand threat behavior at a deeper level, helping their teams stay ahead of evolving attack vectors.
| Tool Category | Purpose |
|---|---|
| SIEM Platforms (Splunk, QRadar) | Aggregate and analyze logs from systems, endpoints, and firewalls to detect threats. |
| SOAR Platforms (Cortex XSOAR, TheHive) | Automate repetitive response tasks and streamline incident handling workflows. |
| EDR Tools (CrowdStrike, SentinelOne) | Monitor endpoint behavior and detect malicious activity in real time. |
| Forensics Tools (Wireshark, FTK, Volatility) | Analyze network traffic, memory dumps, and artifacts for deep threat investigation. |
| Open-Source Lab Tools (Security Onion, Zeek) | Provide training environments for practicing detection, logging, and packet capture. |
How to Build Experience as a SOC Analyst
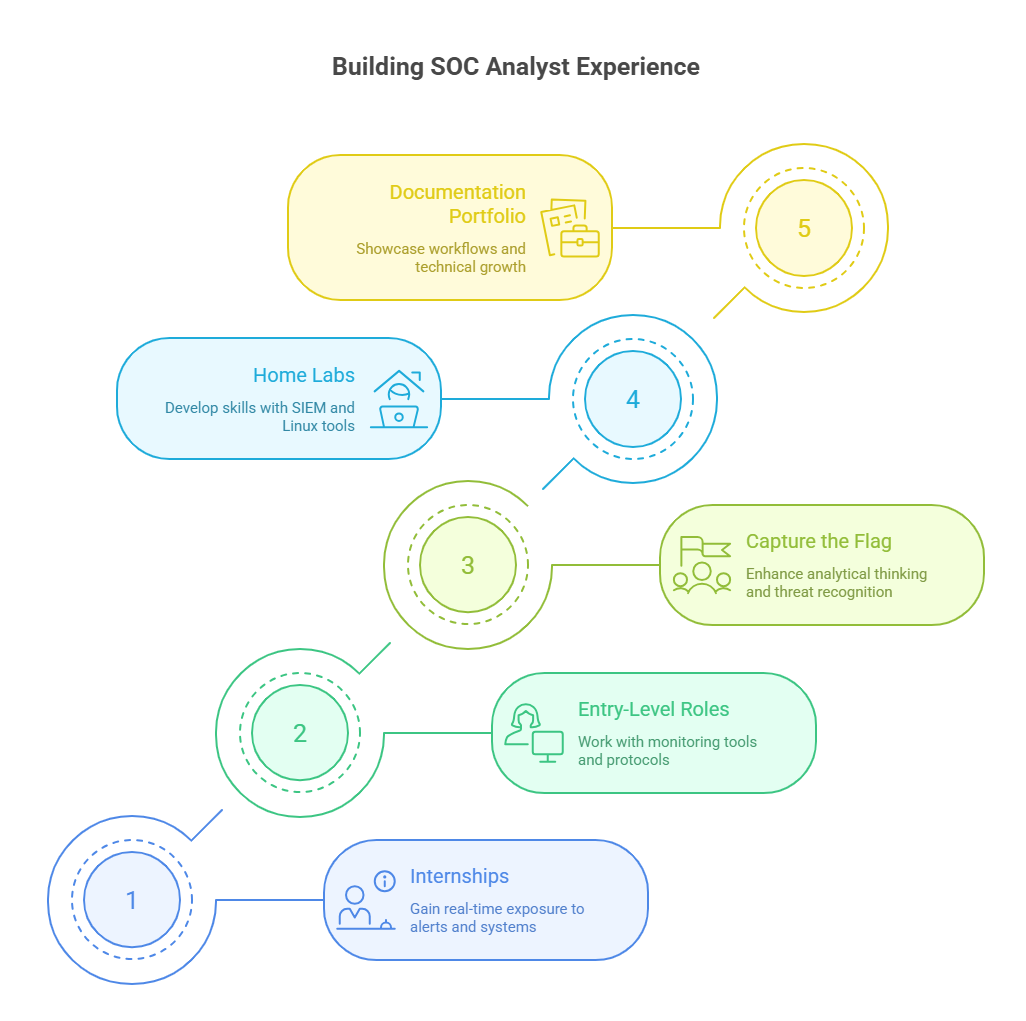
Certifications and education help you qualify—but experience gets you hired. SOC teams want analysts who can jump into live environments and handle the pressure. But how do you gain experience before landing your first full-time role? The key is to build a portfolio of real-world exposure—through labs, entry-level roles, and targeted technical practice.
Experience doesn’t just mean years on the job. It means working with security tools, interpreting logs, writing reports, and improving your ability to recognize patterns. Below are two proven paths to start building experience—whether you’re a student, bootcamp grad, or career switcher.
Internships and Entry-Level Positions
Internships in IT security or SOC environments are one of the best launchpads. Even if you’re doing basic log triage or alert monitoring, you’re gaining exposure to real-world threats and live team workflows. Look for programs at MSPs, universities, hospitals, or government IT departments.
If internships aren’t available, consider entry-level roles like Security Analyst I, SOC Trainee, or NOC (Network Operations Center) support. These roles often act as stepping stones and allow you to prove your technical skills in operational settings. Many analysts start in IT help desk or networking roles, then transition to SOC once they’ve built system familiarity.
Developing Advanced Technical Skills
If you can’t get hired yet—train like you’re already on the team. Use platforms like TryHackMe, CyberDefenders, and Blue Team Labs Online to practice SIEM queries, packet analysis, and log forensics. Build a home lab using open-source tools like Security Onion, Wazuh, or Zeek, and document your workflows in a portfolio or GitHub repo.
Focus on building pattern recognition by reviewing incident case studies, participating in CTFs (Capture The Flag), or following current breach investigations. Employers don’t just hire based on what you’ve done—they look for how you think under pressure. When your resume shows hands-on analysis and thoughtful reporting, it puts you ahead of applicants with generic coursework.
The Future of SOC Analysts and Cybersecurity Careers
SOC analysts will be more critical than ever in 2025 and beyond. As cyberattacks grow in complexity and speed, organizations are shifting from reactive models to proactive, intelligence-driven security operations. SOC teams are at the heart of this shift—integrating threat hunting, AI-driven analysis, and automation to keep up with modern threat actors.
The analyst’s role is evolving from monitoring to decision-making. Tools like SOAR (Security Orchestration, Automation, and Response) are reducing manual work, allowing analysts to focus on high-level analysis and rapid threat response. Analysts who adapt to automation workflows and threat intelligence integration will be in the highest demand.
Emerging roles—like cyber threat hunter, cloud SOC analyst, and adversary emulation specialist—are redefining what’s possible within a SOC. Companies are prioritizing cross-skilled analysts who understand incident response, scripting, and cloud infrastructure. This means SOC careers aren’t limited—they’re scalable, flexible, and increasingly high-paying.
For career security, adaptability is everything. Analysts who consistently upskill in tools, scripting, and real-world threat modeling will be the ones promoted fastest. As more SOCs move toward remote and hybrid operations, analysts who can demonstrate discipline, documentation skills, and independent problem-solving will rise above the competition.
| Trend | Career Implication |
|---|---|
| AI & Automation in SOCs | Reduces manual triage and increases the demand for analysts with scripting and SOAR skills. |
| Remote & Hybrid SOC Models | Expands job opportunities for analysts who can work independently and document thoroughly. |
| Rise of Threat Intelligence | Increases need for analysts skilled in attacker profiling and IOC correlation. |
| Cloud Security Integration | Creates demand for SOC analysts who understand Azure, AWS, and hybrid cloud environments. |
| Cross-Training & Career Mobility | Encourages career paths into threat hunting, security engineering, and red teaming. |
How SOC Analyst Certifications Accelerate Career Growth in 2025
In cybersecurity, certifications aren’t just checkboxes—they’re career accelerators. For SOC analysts in 2025, the right certifications unlock job access, boost promotion potential, and provide critical knowledge for staying relevant in an evolving threat landscape. In many cases, certifications are what separate candidates with similar experience levels.
Entry-level professionals benefit from foundational credentials like CompTIA Security+ or EC-Council’s Certified SOC Analyst (CSA). These validate core skills in log analysis, threat detection, and incident handling—areas employers screen for immediately. As analysts progress, advanced certifications like CySA+, GIAC Security Essentials (GSEC), or CISSP can fast-track promotions into Tier 2 or Tier 3 roles.
Certifications also prove your ability to work with real-world tools. Employers often look for tool-specific certs like Splunk Core Certified Power User or Microsoft SC-200, especially in environments where those platforms are critical. These credentials don’t just check a box—they show you can operate inside the ecosystem from day one.
Finally, certifications build confidence—not just for employers, but for analysts themselves. They offer structured learning, industry-aligned training, and practical labs that simulate real SOC workflows. In a competitive hiring environment, this preparation often determines who gets hired and who gets passed over.
Investing in certification is more than a resume boost—it’s a strategic move that expands your job options, raises your earning ceiling, and prepares you for the next evolution of SOC work.
Frequently Asked Questions (FAQs)
-
A SOC analyst monitors an organization’s IT infrastructure for signs of cyber threats or suspicious behavior. Using SIEM tools, they review logs, investigate alerts, and escalate potential incidents to senior staff or incident response teams. They also document findings, maintain security dashboards, and respond to phishing, malware, or unauthorized access attempts. Tier 1 analysts typically focus on alert triage and log analysis, while Tier 2 and Tier 3 analysts dig deeper into threat hunting, forensics, and advanced incident response. Communication and precision are key—every action must be logged accurately. The role is hands-on, fast-paced, and essential to modern cybersecurity operations.
-
For beginners, CompTIA Security+ is the most widely accepted entry point. It covers core security concepts, risk management, threat types, and basic incident response—all critical knowledge for SOC teams. If you want a role-specific credential, the Certified SOC Analyst (CSA) from EC-Council is purpose-built for Tier 1 roles and gives you practical exposure to SIEM tools and ticket workflows. Once you have some experience, CySA+ or SC-200 (Microsoft Security Operations Analyst) can take you to the next level. Employers often look for a combination of these certs, especially when hiring for SOCs that use platform-specific technologies.
-
Yes. In 2025, many SOC analysts are getting hired without a formal degree—especially those with the right certifications and hands-on skills. While a degree in cybersecurity or computer science helps, it’s not a requirement. Employers care more about your ability to read logs, understand alerts, and operate within their security tools. If you can demonstrate this with a home lab, certification, or internship experience, you’ll be competitive. Start with foundational certs, join CTF competitions, and build a portfolio. A resume that shows technical readiness and proactive learning often beats a degree with no real-world exposure.
-
The timeline varies based on your starting point. If you’re new to tech, expect to spend 6–12 months preparing with certifications like Security+, building a lab, and completing entry-level training. Career switchers from IT or help desk roles can often move into a SOC analyst role in 3–6 months with focused study and skill development. For those pursuing degrees, it may take 1–2 years, depending on coursework and internships. The fastest path combines self-paced certifications, hands-on practice, and strategic networking. It’s less about time and more about proving you’re operationally ready on day one.
-
Start with SIEM platforms like Splunk, IBM QRadar, or Elastic. Learn how to search logs, analyze alerts, and create dashboards. Understanding endpoint detection and response (EDR) tools like CrowdStrike or SentinelOne is also valuable. You should also get familiar with packet analysis tools like Wireshark, and if possible, SOAR platforms such as Palo Alto Cortex XSOAR. Open-source tools like Security Onion, Zeek, and Wazuh can help you simulate a SOC lab at home. Employers are looking for candidates who don’t just know theory—they want people who can navigate these tools efficiently during investigations.
-
Yes—remote SOC analyst roles are becoming increasingly common. Many organizations now operate hybrid or fully remote SOCs to reduce costs and access global talent. Entry-level roles may still require on-site work or hybrid training periods, but mid- and senior-level analysts can often work fully remotely. That said, remote roles require strong communication skills, self-discipline, and the ability to document incidents clearly across time zones. Tools like Slack, Jira, and remote access to SIEM platforms make this setup efficient. If you're targeting remote work, emphasize your ability to handle incidents independently and showcase home lab or freelancing experience.
-
SOC analysis is just the beginning. Many analysts move into specialized roles like threat hunter, malware analyst, digital forensics expert, or red teamer. Others shift into leadership, becoming SOC managers or incident response leads. If you’re strong with scripting and systems, security engineering or DevSecOps may be a fit. The key is to keep learning—especially in threat intelligence, cloud security, and automation. Certifications like GCFA, GCIH, or CISSP can help with these transitions. SOC experience teaches you how real attacks unfold, making it one of the best launchpads for any advanced cybersecurity career.
Conclusion: Becoming a SOC Analyst in 2025
The path to becoming a SOC analyst in 2025 is clear, but it’s not passive. It takes focused training, hands-on practice, and smart certification choices to break into one of the most in-demand cybersecurity roles today. Whether you’re a student, career switcher, or IT professional, the role is accessible—but only if you bring technical readiness and the mindset to handle real-world threats.
SOC analysts are no longer just log reviewers—they’re strategic operators. As the field evolves, analysts who master tools like SIEM, EDR, and SOAR and combine them with threat intelligence and automation will lead the future. Pair that with communication skills and curiosity, and you're not just hireable—you’re promotable.
Start now. Build your lab. Earn your certification. Learn the platforms employers use. With the right steps, you can be on the frontline of cybersecurity, defending systems, protecting data, and driving impact in a career that truly matters.