Advanced Persistent Threats (APT): Mechanisms and Defense
In the ever-evolving landscape of cybersecurity, Advanced Persistent Threats (APTs) stand as some of the most dangerous and sophisticated threats organizations face. Unlike typical malware or opportunistic attacks, APTs are highly targeted, stealthy, and long-term operations, often orchestrated by nation-state actors or well-funded criminal groups. Their objective is clear: penetrate high-value targets, remain undetected, and extract critical data or disrupt operations over extended periods. For organizations, understanding the mechanics of APTs is no longer optional; it’s essential for survival. These attacks leverage a combination of advanced techniques—spear phishing, zero-day exploits, watering hole attacks, and more—to gain initial entry.
The threat landscape is intensifying, with APTs continuously evolving to bypass even the most robust defenses. Real-world incidents—such as the infamous APT29’s infiltration of U.S. government networks or APT28’s cyber attacks on critical infrastructure—highlight the severe consequences of underestimating these threats. Organizations failing to build resilient, proactive defense mechanisms risk not only operational disruption but also reputational damage, financial losses, and potential legal consequences. This comprehensive guide dissects the core mechanics of APTs, revealing how these attackers operate, the techniques they employ, and the defense strategies organizations must adopt to counter them.
What Are Advanced Persistent Threats?
Definition and Key Features
Advanced Persistent Threats (APTs) are complex, sustained cyberattacks targeting specific organizations, industries, or sectors. Unlike mass-distributed malware or opportunistic intrusions, APTs are deliberate and calculated operations, crafted to achieve strategic objectives such as stealing intellectual property, disrupting critical infrastructure, or gathering political intelligence. These attacks are executed by sophisticated adversaries—often nation-state actors or highly skilled hacking groups—with significant resources and expertise. A hallmark of APTs is their stealthy infiltration into a network. Attackers use a variety of entry techniques, including phishing, watering hole attacks, and zero-day exploits, to gain initial access without triggering alarms.
Once inside, they employ advanced methods—such as rootkits, custom malware, and credential dumping—to maintain persistence and avoid detection. They can remain in a network for months or even years, silently exfiltrating data or preparing for large-scale disruptions. Unlike traditional malware attacks, which often exploit vulnerabilities for short-term gains, APTs focus on long-term engagement. The attackers carefully study the target’s infrastructure, behaviors, and defense mechanisms, adapting their tactics to stay ahead of detection. Their operational cycles include continuous refinement of attack tools, frequent shifts in communication channels, and tactical adjustments based on the target’s response.
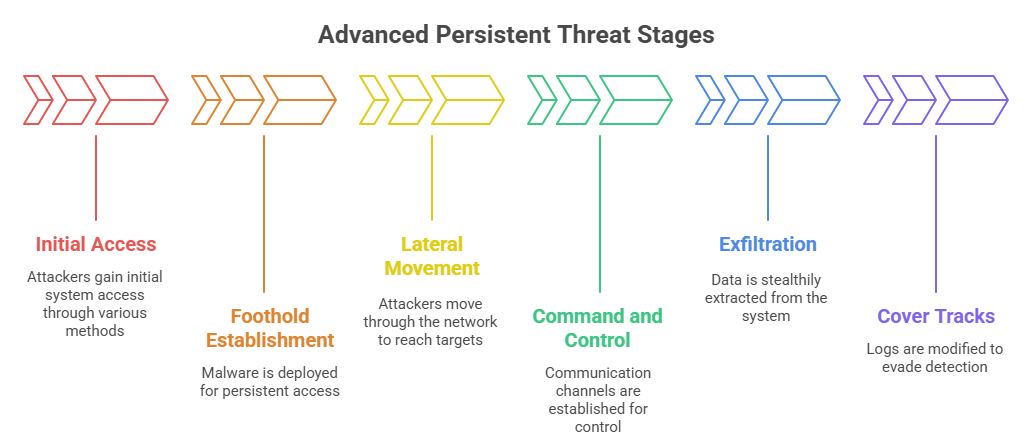
Common APT Stages
APTs typically unfold in a well-orchestrated sequence of stages, each serving a specific purpose in the attack lifecycle:
Initial Access: Attackers leverage methods like spear phishing, exploiting zero-day vulnerabilities, or watering hole attacks to compromise a system and establish a foothold.
Foothold Establishment: Once inside, they deploy malware, backdoors, or rootkits to secure persistent access. The malware is often custom-tailored, making it difficult to detect with standard security tools.
Lateral Movement: Attackers pivot through the network using techniques such as pass-the-hash, credential harvesting, and privilege escalation to expand control and reach high-value targets.
Command and Control (C2): Communication channels are established between the compromised network and the attackers’ command servers, allowing continuous instructions and data exfiltration.
Exfiltration: Data is stealthily extracted using methods like DNS tunneling, encrypted data channels, or disguised outbound traffic, ensuring the theft remains undetected.
Cover Tracks: Throughout the operation, attackers modify logs, clear traces, and maintain stealth to evade detection, even as defenders deploy countermeasures.
Real-world incidents such as APT29 (Cozy Bear) and APT28 (Fancy Bear) provide compelling examples of these stages in action. These groups have demonstrated how APTs infiltrate high-profile targets, maintain persistence for extended periods, and execute data thefts or operational disruptions with alarming precision.
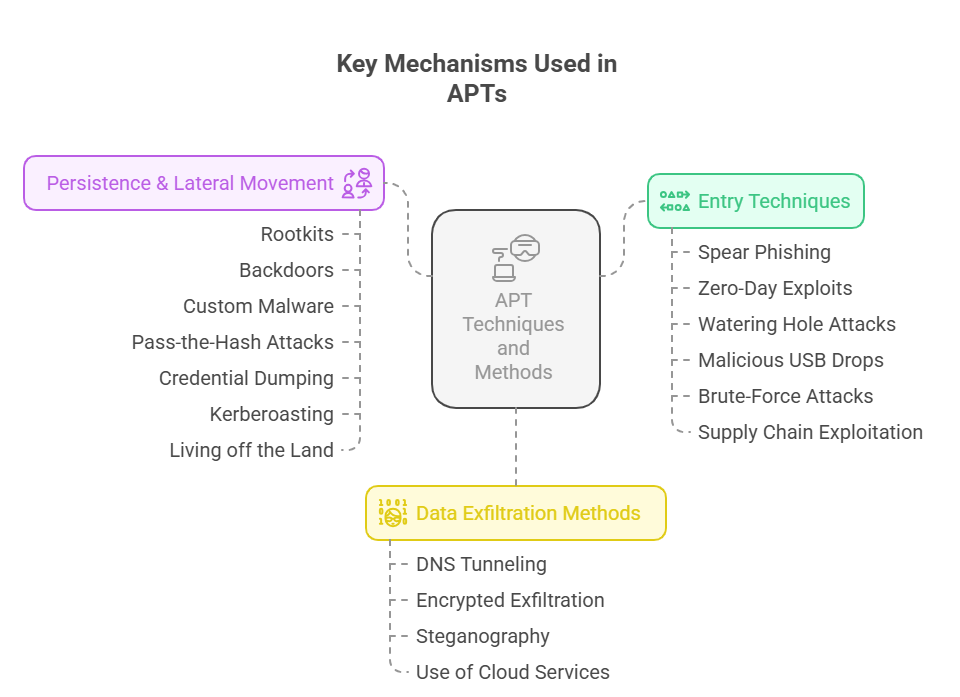
Key Mechanisms Used in APTs
Entry Techniques
APTs initiate their operations by employing sophisticated entry techniques tailored to the target environment. Spear phishing tops the list—a method where attackers craft personalized emails or messages, often mimicking legitimate communications, to deceive recipients into clicking malicious links or downloading infected attachments. This technique leverages detailed reconnaissance, ensuring high success rates by exploiting human trust. Zero-day exploits are another favored approach. These involve exploiting vulnerabilities in software or systems that have not yet been patched or publicly disclosed. By striking before the vendor can issue a fix, attackers gain a critical advantage, slipping past defenses undetected.
Watering hole attacks demonstrate strategic patience. Attackers compromise legitimate websites frequented by the target, injecting malicious scripts to silently infect visitors. This tactic is particularly effective in targeting sectors like defense or finance, where certain industry websites are visited routinely.
Other entry tactics include:
Malicious USB drops: Physical devices left in public areas, preloaded with malware.
Brute-force attacks: Systematically trying password combinations to break into poorly secured systems.
Exploitation of supply chain vulnerabilities: Compromising third-party vendors or partners with weaker security controls.
Each of these techniques is selected based on reconnaissance, ensuring maximum impact and minimizing detection during the initial compromise.
Persistence and Lateral Movement
Once initial access is achieved, attackers deploy persistence mechanisms to maintain long-term control over the compromised environment. This may include rootkits, which modify the operating system at a deep level to hide their presence; backdoors, which provide a continuous secret entry point; and custom malware, designed to evade detection by traditional antivirus or endpoint protection tools.
APTs excel in lateral movement, where attackers spread across a network to access higher-value assets. Common tactics include:
Pass-the-hash attacks: Leveraging stolen hashed credentials to authenticate as legitimate users across systems.
Credential dumping: Extracting stored passwords from compromised machines to escalate privileges.
Kerberoasting: Targeting service accounts to crack their passwords and gain elevated access.
Living off the land (LotL): Using native tools like PowerShell or WMI to execute commands without triggering alarms.
These lateral movements enable attackers to escalate from an initial foothold to controlling critical infrastructure components. The adaptability and stealth of APTs at this stage make them particularly dangerous, as traditional security measures are often bypassed.
Data Exfiltration Methods
The final objective of most APT campaigns is data exfiltration, conducted with precision and stealth. Attackers commonly use:
DNS tunneling: Embedding stolen data within DNS queries, which often bypass monitoring tools.
Encrypted exfiltration: Wrapping data in encrypted packets to obscure its nature during transmission.
Steganography: Concealing data within seemingly innocuous files or images to evade detection.
Use of cloud services: Uploading data to compromised or attacker-controlled cloud accounts for retrieval.
These methods allow attackers to extract sensitive data over extended periods without raising immediate suspicion, often blending with normal network traffic and avoiding traditional detection tools.
Detection and Defense Strategies
Network Monitoring and Anomaly Detection
The backbone of APT defense lies in robust network monitoring and the ability to detect anomalous behaviors in real time. Organizations deploy Security Information and Event Management (SIEM) systems to aggregate logs, correlate events, and identify patterns indicative of APT activity. These systems, combined with Intrusion Detection/Prevention Systems (IDS/IPS), enable immediate recognition of suspicious access attempts or abnormal data flows.
Behavioral analytics plays a crucial role here. Instead of relying solely on known threat signatures, behavioral tools establish a baseline of normal operations. They then detect deviations—such as unusual login times, data transfer volumes, or access to sensitive files—that could indicate an APT’s lateral movement or data exfiltration.
Real-time alerts and response protocols are essential. Organizations must implement automated triggers for immediate investigation and response, preventing attackers from establishing a long-term presence.
Endpoint and Perimeter Security
Securing endpoints and network perimeters is a critical layer in APT defense. Organizations implement Next-Generation Antivirus (NGAV) solutions that leverage machine learning and behavioral analysis to detect novel malware strains. Endpoint Detection and Response (EDR) tools provide continuous visibility into endpoint activities, allowing rapid containment of suspicious processes or applications.
On the perimeter, firewalls filter incoming and outgoing traffic based on granular rules, blocking unauthorized access attempts and malicious payloads. Web Application Firewalls (WAFs) specifically shield web-facing applications from exploitation by filtering traffic and mitigating common attack vectors like SQL injection or cross-site scripting (XSS).
Endpoint and perimeter defenses must be hardened through regular patching, configuration management, and deployment of least privilege access controls to limit potential exposure points.
Incident Response and Recovery
A comprehensive incident response plan is vital to containing and eradicating APTs. Organizations must define clear procedures for identifying affected systems, isolating compromised endpoints, and initiating containment protocols to halt the attack’s progression.
Forensic analysis helps uncover the root cause, tracing how attackers gained entry and moved laterally. This information informs both remediation efforts and long-term security improvements. Lessons learned from the incident guide adjustments to detection rules, patch management, and user awareness training.
Recovery strategies emphasize system restoration from clean backups, validation of system integrity, and gradual reintroduction of affected systems into production. Communication plans ensure stakeholders are informed, while compliance requirements are met with detailed documentation of the incident and response.
| Defense Layer | Key Tools and Techniques | Benefits |
|---|---|---|
| Network Monitoring & Anomaly Detection | SIEM, IDS/IPS, Behavioral Analytics | Detects suspicious activity, enables real-time threat response |
| Endpoint & Perimeter Security | Next-Gen Antivirus, EDR, Firewalls, WAFs | Protects endpoints and perimeters, blocks malware and unauthorized access |
| Incident Response & Recovery | Forensic Analysis, Containment Protocols, Clean Restores | Contains threats, recovers systems, strengthens future defenses |
Real-World APT Case Studies
Case Study 1: APT29 (Cozy Bear)
APT29, also known as Cozy Bear, represents one of the most sophisticated and persistent APT groups, linked to Russian intelligence services. This group has targeted government agencies, energy sectors, and think tanks across the globe. Their operations are characterized by stealth, long-term engagement, and the use of custom malware and advanced evasion techniques. APT29's tactics often begin with spear phishing, delivering malicious payloads via emails mimicking trusted contacts. Once inside, they deploy custom malware strains like HAMMERTOSS and MINIDIONIS, designed to evade detection by leveraging encrypted channels and legitimate services like social media platforms for command and control communications.
Their lateral movement includes using stolen credentials and exploiting Active Directory vulnerabilities, enabling them to blend seamlessly into the network's daily operations. Exfiltration methods involve DNS tunneling and encrypted payloads, ensuring data theft remains undetected for extended periods. One notable incident involved the compromise of U.S. government agencies, where Cozy Bear maintained access for months, extracting sensitive diplomatic and political information. The response involved rapid containment, advanced forensics, and long-term monitoring to fully eradicate their presence. The case highlighted the importance of multi-layered defenses, continuous monitoring, and proactive threat hunting to counter persistent adversaries.
Case Study 2: APT28 (Fancy Bear)
APT28, also known as Fancy Bear, is another prominent Russian-linked APT group, notorious for its aggressive campaigns targeting critical infrastructure, political organizations, and military sectors. Their operations often blend cyber espionage with psychological operations, aiming to disrupt, discredit, or destabilize targets. APT28's entry techniques typically involve spear phishing emails, malicious documents exploiting zero-day vulnerabilities, and watering hole attacks compromising frequently visited websites. Their malware arsenal includes tools like X-Agent, Sednit, and CHOPSTICK, engineered for persistence, credential harvesting, and lateral movement.
In a high-profile attack on critical infrastructure, Fancy Bear used malware-loaded emails to penetrate an energy provider’s network. They then escalated privileges, moved laterally, and exfiltrated sensitive operational data, posing both national security risks and potential operational failures. Detection efforts were hindered by their use of encrypted communications and fileless malware, which left minimal forensic traces. Key lessons from this case include the necessity of layered defense strategies, user awareness training, and the deployment of advanced endpoint monitoring. Organizations also recognized the value of incident response simulations, preparing teams to respond decisively under pressure.
How Our Cybersecurity Certification Prepares You for APT Defense
Comprehensive Skills Training
Our cybersecurity certification program equips professionals with a deep understanding of Advanced Persistent Threats (APTs), focusing on both theoretical knowledge and hands-on expertise. The curriculum covers essential topics such as APT identification, mitigation strategies, and response planning, ensuring participants are ready to tackle complex cyber threats.
Through immersive modules, learners gain mastery in threat intelligence analysis, forensic investigation, and incident response protocols. They practice recognizing APT attack patterns, assessing vulnerabilities, and deploying effective containment strategies. Participants also learn to leverage advanced tools like SIEM systems, endpoint detection platforms, and behavioral analytics for early detection and response.
Graduates of the program emerge with the skills and confidence to protect organizations from persistent and evolving APT threats.
Access to Real-World Scenarios
The program’s strength lies in its inclusion of real-world APT simulations, providing participants with hands-on experience in red-team/blue-team exercises. These simulations mirror the complexities of actual APT incidents, testing learners’ abilities to detect, contain, and recover from sophisticated attacks.
Participants work with customized malware samples, network forensics challenges, and live incident response scenarios, bridging the gap between classroom theory and real-world applications. This practical approach ensures that learners not only understand the mechanics of APTs but also know how to apply this knowledge effectively in high-pressure environments.
By the end of the course, participants are equipped to lead incident response teams, implement proactive security measures, and contribute meaningfully to organizational defense strategies. This comprehensive preparation positions them as highly sought-after professionals in the cybersecurity landscape.
Final Thoughts
Advanced Persistent Threats (APTs) represent a formidable challenge to organizations worldwide. Their stealth, persistence, and adaptability enable them to bypass traditional defenses, target high-value assets, and cause lasting damage. As attackers refine their methods, the need for vigilant, highly trained cybersecurity professionals becomes more urgent than ever. Organizations that underestimate APT risks expose themselves to data breaches, operational disruptions, and reputational damage. Proactive measures, including layered defense strategies, continuous monitoring, and rigorous incident response planning, are essential to fortify systems against these evolving threats.
Our cybersecurity certification program provides a comprehensive path for professionals to master APT detection, response, and mitigation. Through immersive training and real-world simulations, learners develop the skills to identify threats early, contain incidents effectively, and implement robust defensive strategies. With APT attacks on the rise, investing in high-level cybersecurity training isn’t optional—it’s a critical step in safeguarding digital infrastructures and advancing career opportunities. Explore our certification course today and join the front lines in the battle against sophisticated cyber adversaries.
Frequently Asked Questions
-
An Advanced Persistent Threat (APT) is a targeted, long-term cyberattack that infiltrates a network to steal data or disrupt operations. Unlike typical cyberattacks that focus on quick gains or opportunistic breaches, APTs are highly strategic and stealthy. They often involve multiple stages—initial access, lateral movement, persistence, and exfiltration—and are orchestrated by sophisticated adversaries like nation-states or elite hacking groups. APTs use advanced tactics such as zero-day exploits, custom malware, and social engineering, allowing them to remain undetected for months or years. Their goal is sustained access to high-value environments, unlike regular attacks which are often short-lived or financially motivated.
-
Description text APT attacks follow a structured lifecycle designed to infiltrate, control, and exploit a target over time. The stages include:
Initial Access: Gaining entry via spear phishing, zero-day exploits, or watering hole attacks.
Establishing Foothold: Deploying malware or rootkits for persistence.
Lateral Movement: Spreading through the network using techniques like pass-the-hash or credential dumping.
Command and Control (C2): Maintaining remote communication for command instructions.
Data Exfiltration: Stealthily extracting sensitive data using methods like DNS tunneling or encrypted channels.
Covering Tracks: Modifying logs and deleting evidence to avoid detection.
Each stage is meticulously planned to achieve long-term objectives while remaining hidden.goes here
-
APTs target organizations with valuable data or critical functions, particularly those in government, defense, energy, financial services, healthcare, and technology sectors. High-profile targets include national security agencies, critical infrastructure providers, intellectual property holders, and political organizations. These entities are appealing because they possess sensitive information, operational control over vital systems, or influence over policy and decision-making. APT groups often focus on supply chain compromises, where they exploit weaker links to access larger, more secure networks. Even organizations with robust defenses can be targeted, making industry-specific risk assessments and proactive defense strategies crucial for long-term protection against these adversaries.
-
Defending against APTs requires a layered and adaptive approach. Key strategies include:
Network Monitoring: Using SIEM, IDS/IPS, and behavioral analytics to detect anomalies.
Endpoint Security: Deploying next-gen antivirus, EDR, and hardening systems with patches.
User Training: Educating staff on phishing risks and social engineering tactics.
Incident Response Plans: Establishing procedures for rapid containment, forensics, and recovery.
Threat Intelligence Integration: Leveraging external intelligence feeds to detect emerging threats.
Zero Trust Architecture: Limiting access based on verification, not trust, to contain lateral movement.
These combined efforts create a resilient defense posture against persistent and evolving threats.
-
Item descripThreat intelligence provides organizations with insight into evolving attacker techniques, infrastructure, and behavior patterns, enabling them to anticipate and block attacks before damage occurs. Integrating real-time threat feeds with SIEM systems and behavioral analytics tools allows for proactive detection of anomalies that align with APT activity. Continuous monitoring of endpoints and network traffic uncovers subtle indicators of compromise (IOCs), such as unusual file access patterns or data transfers. This combination of proactive intelligence and vigilant monitoring enables organizations to identify and neutralize threats early, minimizing the risk of prolonged APT presence and reducing the potential impact on operations and data security.tion