Security Operations Center (SOC): Roles and Responsibilities
In today’s digital threat landscape, Security Operations Centers (SOCs) stand as the nerve centers of enterprise security. Organizations, from global enterprises to healthcare systems, depend on SOC frameworks not just to protect critical assets but to proactively neutralize evolving cyber threats. A well-structured SOC is not a luxury; it’s a necessity. With the constant rise of high-profile breaches, ransomware attacks, and sophisticated phishing schemes, demand for professionals skilled in real-time monitoring, advanced forensics, and coordinated incident response has reached unprecedented levels. These aren’t just cybersecurity tools—they’re the core competencies that define modern cyber resilience.
This guide offers a deep dive into the roles and responsibilities within SOCs, the structure and components that enable their efficiency, and the technologies that underpin their operations. Whether you aim to advance into a SOC analyst role, ascend to leadership, or simply understand how real-time cyber threat detection, forensic analysis, and compliance reporting intersect, this playbook equips you with the knowledge to act decisively. Expect practical insights into what it takes to thrive in the high-pressure environment of cybersecurity operations—where every second matters and every decision can impact the integrity of an organization’s digital ecosystem.
What Is a Security Operations Center (SOC)?
A Security Operations Center (SOC) serves as the centralized hub of an organization’s cyber defense infrastructure. It operates around the clock to monitor, detect, and respond to potential threats across digital environments. Leveraging both cutting-edge technology and specialized personnel, the SOC functions as the first and last line of defense, proactively identifying and mitigating attacks before they cause significant damage.
Structure and Components
A Security Operations Center (SOC) is designed as a multi-layered, integrated system that operates 24/7. Its core comprises tiered analysts responsible for filtering alerts, identifying threats, and escalating incidents based on severity. The incident response team swiftly acts on escalated issues, isolating compromised systems and initiating containment strategies. SOC managers and team leads oversee operations, ensuring procedures are followed and communication flows effectively. Supporting technologies include a centralized SIEM platform, which aggregates data from diverse sources to enable real-time analysis, and forensic tools for post-incident investigations. Standardized playbooks ensure consistent incident handling, while regular training programs keep the team prepared for new threats. Effective SOC structures also include secure communication protocols, ensuring rapid, coordinated responses across the organization. Each layer in the SOC’s structure works in sync, forming a resilient operational framework that adapts to emerging cyber threats.
Key Technologies Used
Technological integration is the backbone of an effective SOC. SIEM platforms play a central role by aggregating and correlating logs from diverse sources, generating actionable alerts on anomalies. Endpoint Detection and Response (EDR) tools offer visibility into endpoint behaviors, detecting malware, ransomware, and suspicious lateral movements. Threat intelligence feeds provide real-time updates on global cyber threats, enriching analysis with context. Forensic analysis tools enable detailed post-breach investigations, capturing evidence and tracing attack vectors. Automation and orchestration solutions streamline repetitive tasks like alert enrichment, case assignment, and initial triage, boosting operational efficiency. Technologies such as intrusion detection systems (IDS) and network monitoring tools add further layers of visibility, ensuring nothing goes unnoticed. The integration of these technologies creates a cohesive ecosystem, enabling SOC teams to anticipate, detect, and neutralize sophisticated cyber threats.
Core Functions of SOC Teams
SOC teams perform a combination of reactive and proactive tasks that fortify an organization’s digital infrastructure. Continuous monitoring ensures real-time visibility into network activities, enabling early detection of anomalies. Once a potential threat is identified, incident detection and triage processes escalate it to the appropriate response team. Incident responders rapidly contain threats, neutralize malicious actors, and restore affected systems. Post-incident forensic investigations delve into root causes, attack methods, and system vulnerabilities, providing actionable insights to strengthen defenses. SOC teams also manage compliance reporting, ensuring adherence to regulatory standards like GDPR, HIPAA, or PCI DSS. Proactive threat hunting initiatives leverage intelligence to identify vulnerabilities and potential attack vectors before adversaries strike. These functions operate in harmony, transforming the SOC into a dynamic shield against evolving cyber threats.
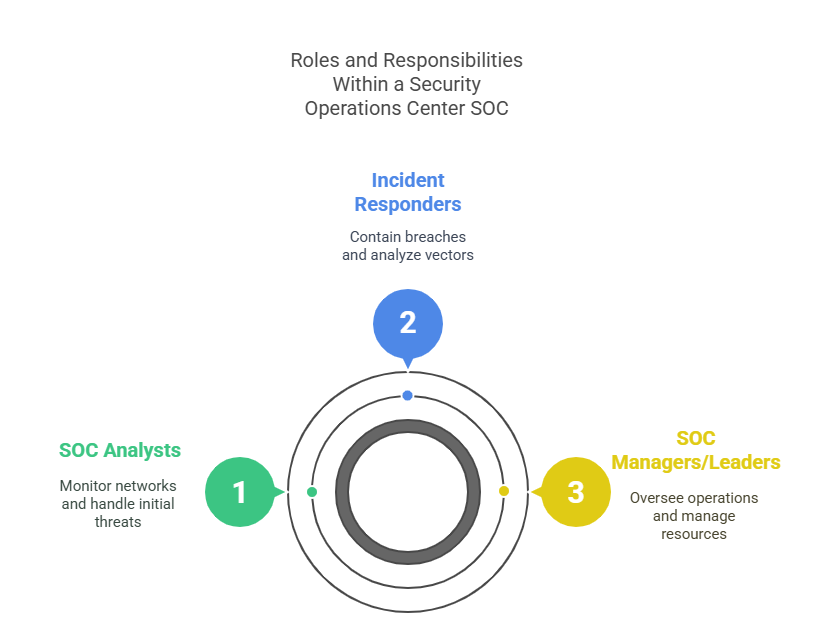
Roles and Responsibilities Within a SOC
The Roles and Responsibilities within a Security Operations Center (SOC) are meticulously structured to ensure continuous protection of an organization’s digital assets. Every team member, from frontline analysts to incident responders and leadership, plays a critical part in detecting, containing, and resolving cyber threats. Understanding these distinct roles provides clarity into how SOCs operate effectively, ensuring that every alert, investigation, and response is coordinated.
SOC Analysts
SOC analysts are the backbone of the Security Operations Center, tasked with the continuous monitoring of networks and systems to identify threats. They use SIEM tools and threat intelligence platforms to sift through vast amounts of log data, filtering false positives and escalating genuine threats. Analysts are typically divided into tiers: Tier 1 handles initial alerts, applying predefined playbooks to determine urgency. Tier 2 delves deeper into analysis, correlating data across multiple sources to identify patterns of malicious activity. Tier 3, the most advanced, engages in complex investigations, reverse-engineering malware, and providing in-depth threat assessments. Beyond detection, SOC analysts craft detailed incident reports and maintain documentation for compliance and auditing purposes. They also collaborate closely with incident responders, ensuring seamless handoffs during escalations. A skilled SOC analyst combines technical acumen with critical thinking, enabling rapid identification and contextual understanding of threats, often within seconds.
Incident Responders
Incident responders step in when an alert escalates into a potential security breach. Their primary role is containment, ensuring the attacker is isolated and damage is minimized. They swiftly analyze compromised systems, identifying attack vectors and applying countermeasures to halt further spread. Forensic expertise is essential, as responders collect and preserve digital evidence, maintaining chain of custody for legal and compliance purposes. They often operate under intense pressure, balancing swift response with meticulous documentation. Collaboration is crucial; they liaise with analysts for incident context and with leadership to ensure decision-makers understand the scope and impact. Incident responders also spearhead post-incident recovery, working with IT and system owners to restore services while eliminating residual threats. They don’t just react; they prepare. Tabletop exercises, red team-blue team drills, and continuous training sharpen their skills, ensuring they’re ready for the next inevitable breach.
SOC Managers and Leadership
SOC managers and leadership oversee the entire security operation, ensuring all functions—from real-time monitoring to post-incident analysis—are executed effectively. They develop and enforce operational procedures, establish escalation protocols, and ensure adherence to regulatory requirements. Managers assess and allocate resources, balancing workload across SOC analysts and responders, while maintaining staff readiness through training and certifications. Leadership responsibilities also include evaluating the effectiveness of SOC technologies, ensuring tools are optimized and up to date. SOC managers coordinate with executives, translating technical incidents into business-impact narratives that inform strategic decisions. They champion a culture of continuous improvement, encouraging threat hunting, knowledge sharing, and collaboration with external cybersecurity communities. Metrics and reporting are essential, with managers tracking incident trends, response times, and compliance outcomes. The role demands a blend of technical expertise, strategic vision, and exceptional communication skills to align the SOC’s mission with the broader goals of the organization.
SOC Tools and Workflows
SOC Tools and Workflows form the operational backbone of an effective security operations center. These technologies and processes enable seamless monitoring, incident response, and compliance reporting in real time. By integrating automation, advanced analytics, and structured escalation protocols, SOCs ensure that every threat is addressed promptly and thoroughly. Understanding the essential tools and the workflows that guide their use provides insight into how modern SOCs maintain resilience and efficiency against a constantly evolving threat landscape.
Real-Time Monitoring and Alerting
Real-time monitoring and alerting form the SOC’s first line of defense. Utilizing SIEM platforms, SOC teams ingest and analyze log data from endpoints, networks, and cloud environments to detect anomalies as they occur. Automated alerting mechanisms identify deviations from established baselines, triggering notifications that prompt immediate action. Analysts use correlation rules and machine learning algorithms to differentiate false positives from genuine threats, ensuring resources are focused where they matter most. Dashboards provide a consolidated view of alerts, enabling rapid assessment and prioritization. Integration with threat intelligence feeds enriches alerts with context, revealing the nature and severity of potential threats. This proactive, automated workflow enables SOC teams to maintain 24/7 situational awareness, accelerating detection and response times. Effective real-time monitoring not only mitigates immediate risks but also informs long-term security strategies, allowing organizations to anticipate and adapt to evolving threat landscapes.
Forensics and Post-Incident Analysis
Forensic and post-incident analysis provides deep insight into the anatomy of a cyberattack. Once containment is achieved, SOC teams shift focus to identifying root causes, attack vectors, and exploited vulnerabilities. Using forensic tools like memory dump analyzers, file integrity checkers, and malware sandboxes, they reconstruct attacker actions. This analysis reveals not just how an attack happened, but why it succeeded, providing vital lessons to harden defenses. Comprehensive post-incident reviews produce detailed reports documenting timelines, impact assessments, and remediation steps. This documentation supports regulatory compliance and strengthens legal positions in potential litigation. Knowledge sharing sessions with internal and external stakeholders enhance preparedness for future incidents. By transforming breach experiences into actionable intelligence, forensics work creates a feedback loop that refines security controls and response protocols, reducing an organization’s exposure to repeat attacks and improving overall cyber resilience.
Compliance and Reporting
Compliance and reporting ensure that SOC operations align with legal and regulatory mandates such as GDPR, HIPAA, or PCI DSS. Automated compliance modules within SIEM platforms track and document key metrics, including incident types, response times, and recovery actions. SOC teams compile comprehensive reports detailing security events, control effectiveness, and deviations from compliance baselines. These reports are essential for audits, executive reviews, and regulatory submissions. Metrics-driven insights help leadership assess SOC performance and justify resource allocation. Reporting workflows often integrate with governance, risk, and compliance (GRC) tools to centralize documentation and streamline approvals. Beyond formal reporting, compliance involves continuous monitoring of controls, ensuring that security measures adapt to evolving regulations and industry best practices. A robust compliance and reporting framework not only reduces legal exposure but also reinforces stakeholder trust, demonstrating an organization’s commitment to cybersecurity excellence.
| SOC Tools and Workflows | Key Function |
|---|---|
| Real-Time Monitoring | Use SIEM and threat intelligence tools to detect anomalies, trigger alerts, and maintain 24/7 situational awareness. |
| Forensics & Post-Incident | Reconstruct attacks, identify vulnerabilities, and generate reports to support legal and compliance efforts. |
| Compliance & Reporting | Track metrics, generate audit-ready reports, ensure compliance with regulations, and build organizational trust. |
How Advanced Cybersecurity Certification by ACSMI Prepares You for SOC Roles
The Advanced Cybersecurity Certification by ACSMI equips professionals with the critical competencies, tools, and strategic mindset to excel in SOC roles. Its comprehensive curriculum spans the entire spectrum of responsibilities, from real-time threat monitoring and alert management to deep forensic investigation and compliance reporting. Aligned with the latest industry standards and regulatory frameworks, the course ensures learners gain immediately applicable skills that meet today’s evolving cybersecurity demands.
A hallmark of this program is its practical, hands-on approach. Participants work with real-world tools such as SIEM platforms, endpoint detection solutions, and forensic analysis applications, mirroring the exact technologies used in modern SOC environments. Simulated incident scenarios replicate high-pressure, high-stakes situations, training learners to react swiftly and effectively. These exercises develop not only technical skills but also critical thinking and problem-solving capabilities essential for roles like SOC analysts, incident responders, and SOC managers.
Moreover, the course emphasizes collaboration and communication—essential skills for managing complex incident responses and ensuring seamless cross-team coordination. Learners gain a solid understanding of reporting workflows, escalation protocols, and compliance with standards such as GDPR, HIPAA, and PCI DSS. By course completion, participants can produce comprehensive, actionable reports that meet both operational needs and regulatory requirements.
The Advanced Cybersecurity Certification by ACSMI doesn’t just teach technologies and tactics—it cultivates a proactive, strategic mindset. Graduates emerge with the ability to integrate threat intelligence, orchestrate effective response workflows, and adapt swiftly to evolving cyber threats. This holistic readiness empowers them to excel in dynamic, high-pressure SOC environments and positions them as invaluable assets to any cybersecurity team.
Quick Poll: What SOC Role Interests You Most?
Conclusion
A Security Operations Center (SOC) is more than a reactive shield—it’s a proactive engine of digital resilience. By combining real-time threat monitoring, advanced forensic analysis, and rapid incident response, SOC teams safeguard organizations from an ever-growing array of cyber threats. This dynamic ecosystem demands professionals who not only understand the technologies but can integrate them seamlessly into operational workflows. The continuous adaptation to emerging attack vectors and the pressures of regulatory compliance make SOC roles both challenging and indispensable. Those who master these complexities drive organizational resilience and ensure that data integrity and business continuity remain intact.
The Advanced Cybersecurity Certification by ACSMI prepares aspiring SOC professionals with the hands-on experience, strategic insight, and technical fluency required for success. Learners gain command over SIEM, endpoint detection tools, and forensic analysis, while developing the critical thinking and adaptability essential for high-stakes incident response. Practical scenarios, compliance training, and collaborative exercises build confidence and competence. Graduates of this program don’t just fill positions—they become key contributors to the evolving cybersecurity landscape. In a world where digital breaches can halt business operations overnight, professionals trained through ACSMI’s certification stand as pillars of proactive, effective cybersecurity defense.
Frequently Asked Questions
-
To excel in a SOC role, candidates typically need a blend of education, certifications, and hands-on experience. A bachelor’s degree in cybersecurity, computer science, or information technology is common, but many employers value industry certifications like CompTIA Security+, Certified Information Systems Security Professional (CISSP), or the Advanced Cybersecurity Certification by ACSMI. Practical experience with tools such as SIEM platforms, intrusion detection systems, and forensic analysis software is highly valued. Strong analytical skills, attention to detail, and familiarity with compliance standards like GDPR and HIPAA are crucial. Continuous professional development through workshops, labs, and specialized training keeps SOC professionals current and competitive in the evolving threat landscape.
-
When a large-scale cyberattack hits, SOC teams follow a structured, multi-tiered response plan. Tier 1 analysts identify and validate alerts, escalating genuine threats to Tier 2. Incident responders contain the attack, isolating affected systems to limit spread. Simultaneously, forensic teams begin collecting and analyzing digital evidence. SOC managers coordinate efforts, ensuring seamless communication between technical teams and executive stakeholders. Comprehensive documentation of actions taken is maintained for legal, regulatory, and post-incident reviews. Continuous monitoring ensures residual threats are neutralized. Post-attack, teams conduct detailed forensics to uncover root causes, updating playbooks and improving defenses to prevent recurrence. Collaboration, speed, and clarity are key to mitigating impact.
-
SOC teams face challenges including alert fatigue, where overwhelming volumes of false positives obscure genuine threats. Managing and updating diverse security tools—such as SIEM platforms, endpoint detection systems, and threat intelligence feeds—requires constant vigilance and optimization. Staff retention is another critical issue, as the demanding nature of SOC work leads to burnout. Skill gaps, especially in advanced forensics or cloud security, can limit effectiveness. Regulatory changes demand continuous adjustment of compliance protocols. Additionally, integrating threat intelligence into actionable workflows remains a complex task. Effective SOCs address these challenges through automation, continuous training, proactive threat hunting, and strong internal communication.
-
The Advanced Cybersecurity Certification by ACSMI provides hands-on experience with industry-standard tools like SIEM, EDR, and forensic applications. It includes simulated real-world incidents that replicate high-pressure SOC scenarios, developing rapid analysis and response skills. Learners gain expertise in alert management, forensic analysis, and compliance reporting. The program emphasizes critical thinking, collaboration, and regulatory knowledge, covering GDPR, HIPAA, and PCI DSS standards. By the end, participants can produce actionable reports, manage escalations, and integrate threat intelligence into workflows. This certification doesn’t just provide knowledge—it builds practical competence, strategic foresight, and confidence to operate effectively within high-stakes SOC environments.
-
SOC analysts focus on monitoring and initial alert triage, distinguishing false positives from genuine threats using SIEM and threat intelligence tools. They escalate critical issues for response. Incident responders handle escalated threats, containing breaches, preserving digital evidence, and restoring services. They require deep technical and forensic skills, operating under intense pressure. SOC managers oversee the entire operation, developing procedures, managing resources, and ensuring compliance with standards like GDPR. They bridge technical and business perspectives, ensuring clear communication between the SOC team and leadership. Each role is essential, interdependent, and contributes uniquely to the SOC’s overall effectiveness and resilience.