Encryption Standards: AES, RSA, and Beyond
In 2025, data breaches cost enterprises an average of $4.7 million per incident, and the bar for digital security is only rising. Encryption isn’t just a compliance checkbox—it’s the foundation of trust in any digital system. From banking APIs to medical records, every byte of sensitive data now flows through cryptographic pipelines. Attackers aren’t just targeting weak passwords anymore—they’re targeting cryptographic assumptions. That means encryption standards are no longer optional—they’re strategic infrastructure.
Today’s encryption ecosystem is dominated by Advanced Encryption Standard (AES) and Rivest–Shamir–Adleman (RSA). But even these battle-tested protocols face limitations in the face of evolving threats—especially from quantum computing advancements. As digital ecosystems decentralize and data volumes explode, cybersecurity leaders must understand not just how these standards work—but how to evolve with them. This guide breaks down how today’s most important encryption protocols function in practice, where they’re applied, and what lies beyond AES and RSA.
Understanding Modern Encryption Protocols
What Encryption Really Means in Practice
Encryption isn't about hiding data—it’s about rendering it mathematically unreadable without authorization. Every modern encryption algorithm transforms readable data (plaintext) into scrambled ciphertext using a key. Without this key, decoding is computationally infeasible—even for supercomputers. But real-world encryption must account for far more than math. It must consider system latency, memory constraints, and interoperability across devices, browsers, and cloud platforms.
In practice, a single weak link in implementation—such as poor key storage—can make strong encryption useless. That’s why standards matter. They enforce how algorithms are used, not just which are used. AES and RSA are more than formulas—they are entire systems of vetted, documented, and stress-tested practices. In other words, encryption today is less about inventing ciphers and more about deploying them correctly at scale.
Symmetric vs Asymmetric Methods Explained
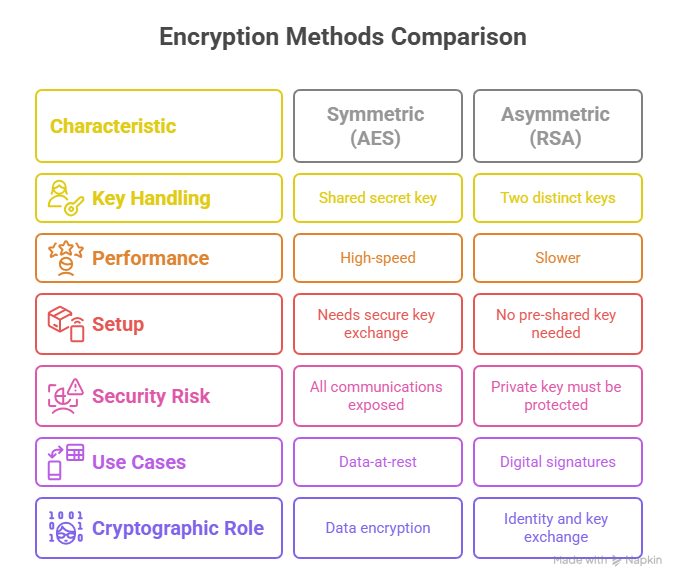
Encryption methods fall into two broad categories: symmetric and asymmetric. In symmetric encryption, the same key is used to encrypt and decrypt data. AES is the best-known example, used for its speed and efficiency. It’s ideal for encrypting large volumes of data—like in cloud backups or real-time voice communication—where performance is critical and both sender and receiver can safely share a secret key.
Asymmetric encryption, on the other hand, uses a public key to encrypt and a private key to decrypt. RSA is the gold standard here. It enables secure communication between strangers over open networks—like HTTPS or email encryption—without prior key exchange. However, asymmetric methods are computationally slower, making them better for initiating secure sessions rather than bulk data transfer.
Together, these methods are often combined in modern systems: asymmetric encryption for exchanging keys, symmetric encryption for transferring data. This hybrid approach powers virtually every secure protocol in use today.
AES – The Backbone of Symmetric Encryption
How AES Works (128-bit, 192-bit, 256-bit modes)
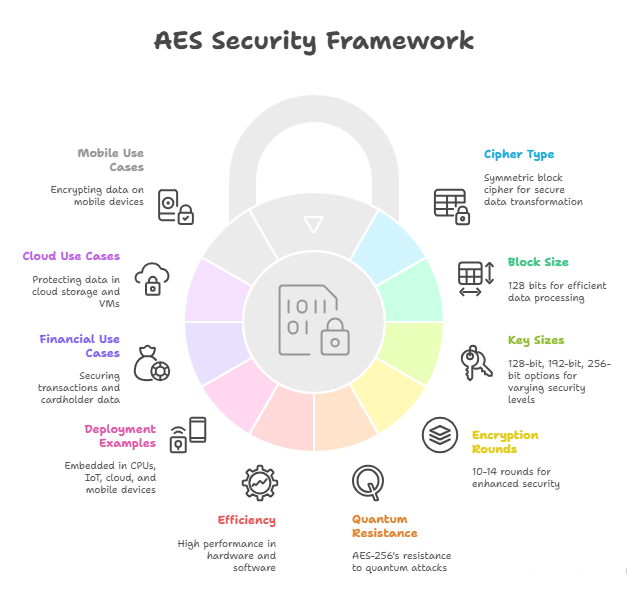
The Advanced Encryption Standard (AES) is the most widely used symmetric algorithm in the world. It’s a block cipher that operates on 128-bit blocks of data, using keys of 128, 192, or 256 bits depending on the required level of security. The encryption process involves multiple rounds (10, 12, or 14 respectively), where each round applies substitution, permutation, mixing, and key addition steps to scramble data beyond recognition.
AES was selected by NIST in 2001 after a multi-year global competition. It replaced DES due to its superior resistance against brute-force attacks and its ability to scale. AES-256 is considered quantum-resistant against brute-force attempts, not because it’s unbreakable, but because the time and computational resources required exceed practical limits—even for future quantum systems.
The simplicity of AES’s structure makes it highly efficient for both software and hardware implementations. It’s now integrated into CPUs, IoT firmware, mobile chips, and cloud APIs. AES remains the encryption gold standard not just because of its strength, but because of its proven security track record over two decades of global cryptanalysis.
Use Cases: Financial Systems, Cloud Storage, Mobile Apps
AES’s speed and low overhead make it a natural fit for environments demanding real-time, high-volume encryption. Banks and payment processors rely on AES for encrypting financial transactions, card data, and API payloads. This ensures compliance with standards like PCI-DSS while minimizing latency that could disrupt user experience.
In cloud environments, AES encrypts everything from object storage buckets to full-disk volumes. Providers like AWS, Azure, and Google Cloud use AES-256 in default storage encryption and customer-managed key systems. It’s also the engine behind secure virtual machines, container volumes, and serverless workloads.
AES is also embedded in mobile device operating systems and apps. From WhatsApp messages to biometric lock files, it protects local and in-transit data without compromising battery or performance. Modern smartphones include AES acceleration at the chip level, enabling apps to encrypt user data seamlessly—even in background tasks.
Ultimately, AES’s widespread adoption is tied to its blend of security, speed, and versatility. It’s fast enough for real-time workloads, strong enough for national security applications, and lightweight enough for embedded systems.
RSA – Powering Public-Key Cryptography
Core Mechanics of RSA (Key Generation, Encryption, Decryption)
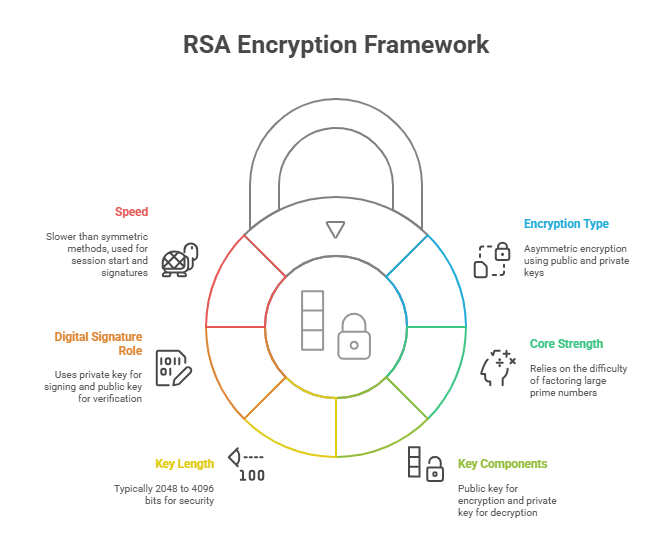
RSA (Rivest–Shamir–Adleman) is the foundational algorithm for public-key cryptography. Unlike symmetric encryption, RSA generates a key pair: one public, one private. The public key encrypts data, while only the matching private key can decrypt it. This enables secure data exchange without needing to share secrets in advance.
The strength of RSA lies in its reliance on the mathematical difficulty of factoring large prime numbers. Generating an RSA key involves choosing two large primes, multiplying them to create a modulus, and deriving public/private exponents. Key sizes typically range from 2048 to 4096 bits, with 2048-bit being the minimum standard in most industries today.
Encryption with RSA is relatively straightforward: the sender uses the recipient’s public key to transform plaintext into ciphertext. Only the recipient’s private key can reverse this process. Digital signatures reverse the process—a sender signs with their private key, and receivers verify using the sender’s public key. This dual-use capability makes RSA critical for both confidentiality and authentication in modern systems.
Despite being slower than symmetric methods, RSA remains vital for secure session initiation and digital verification, where data volume is low but trust is paramount.
Practical Applications in SSL/TLS, Email, Secure Messaging
RSA is embedded in the fabric of internet trust. When you connect to a website via HTTPS, RSA often helps establish the initial TLS handshake, ensuring that you’re talking to the real server—not an impostor. This process includes certificate verification and secure key exchange, which then transitions to a faster symmetric cipher like AES for the session itself.
Email encryption protocols like PGP (Pretty Good Privacy) and S/MIME use RSA to protect email contents and authenticate sender identity. Users share public keys, enabling recipients to decrypt and verify that a message hasn’t been altered or forged. In enterprise settings, RSA keys are managed via internal directories and certificate authorities for large-scale automation.
In secure messaging apps, RSA is typically used in tandem with ephemeral key exchange protocols like Diffie-Hellman or Elliptic Curve Diffie-Hellman. These hybrids provide forward secrecy while retaining RSA’s trust infrastructure. Messaging platforms may retire RSA for newer alternatives in the future, but as of now, it continues to power billions of encrypted communications daily across email servers, login portals, and virtual private networks.
Beyond AES and RSA – Next-Gen and Post-Quantum Encryption
Elliptic Curve Cryptography (ECC) vs RSA
Elliptic Curve Cryptography (ECC) is gaining dominance as a more efficient alternative to RSA in many security systems. While RSA relies on factoring large primes, ECC is based on the mathematical difficulty of the elliptic curve discrete logarithm problem. This allows ECC to offer equivalent security at much smaller key sizes. For example:
ECC with a 256-bit key provides similar security to RSA with a 3072-bit key.
ECC computations are faster, require less bandwidth, and use less power.
These benefits make ECC a natural fit for resource-constrained environments like mobile apps, smart cards, IoT devices, and secure boot firmware. Major tech firms—including Apple, Google, and Microsoft—have incorporated ECC into their TLS and code-signing stacks.
However, ECC is not quantum-resistant. Like RSA, it can be broken by Shor’s algorithm in a post-quantum world. While it's ideal for modern lightweight security, ECC isn’t the future-proof answer for systems that need to last decades—like critical infrastructure or embedded medical tech.
Lattice-Based & Quantum-Resistant Algorithms (NIST finalists)
As quantum computing accelerates, both RSA and ECC face extinction-level vulnerabilities. To prepare, NIST launched a multi-year competition to identify post-quantum encryption algorithms that resist known quantum attacks. In 2022, four finalists were selected for standardization, including:
CRYSTALS-Kyber (key encapsulation): Lattice-based, efficient, and drop-in ready for TLS-like protocols.
CRYSTALS-Dilithium (digital signatures): Lightweight and robust for authentication use cases.
FALCON: A digital signature scheme optimized for fast verification.
SPHINCS+: A stateless hash-based scheme offering long-term quantum safety.
These algorithms are designed to withstand Shor’s and Grover’s algorithms, which threaten all current asymmetric cryptosystems. Lattice-based cryptography, in particular, is favored due to its high-speed implementation and worst-case hardness assumptions.
Adoption is already underway:
Google and Cloudflare have tested Kyber in experimental Chrome builds.
Microsoft has integrated post-quantum readiness into their PQCrypto project.
The NSA recommends transitioning to quantum-safe algorithms for national security systems by 2030.
In short, quantum-resistant encryption is not science fiction—it’s deployment-ready, and organizations securing long-lifecycle assets are moving fast to future-proof their systems.
| Feature / Attribute | Elliptic Curve Cryptography (ECC) | NIST Post-Quantum Algorithms (Kyber, Dilithium, etc.) |
|---|---|---|
| Security Basis | Elliptic curve discrete logarithm problem | Lattice-based and hash-based cryptography |
| Key Size Efficiency | High – 256-bit ECC = strong classical security | Moderate – larger keys, but designed for quantum resilience |
| Performance | Fast, low power, bandwidth-efficient | Varies by algorithm; Kyber and Dilithium optimized for performance |
| Quantum Resistance | ❌ Not resistant (breakable by Shor’s algorithm) | ✅ Resistant to quantum attacks (e.g., Shor’s, Grover’s) |
| Use Cases | Mobile apps, IoT, secure firmware, TLS, digital signatures | Long-term encryption, post-quantum secure VPNs, government systems |
| Standardization Status | Standardized (e.g., NIST SP 800-186, adopted in TLS stacks) | Finalists in NIST’s post-quantum standardization (under active rollout) |
| Industry Adoption | Used by Apple, Google, Microsoft in security infrastructure | Piloted by Google Chrome, Cloudflare, Microsoft PQCrypto |
Encryption in Action: Key Management, Protocols & Performance
Key Distribution & Lifecycle Challenges
Encryption is only as secure as the keys that protect it. In practice, key management—not algorithms—is the hardest part of enterprise cryptography. Key distribution must ensure that authorized parties receive keys securely, without interception or duplication. If a symmetric key is leaked or a private RSA key is exposed, the entire encryption scheme collapses instantly.
Key lifecycle management includes:
Generation: Creating keys with true randomness and secure entropy sources.
Storage: Using hardware security modules (HSMs), TPMs, or encrypted vaults like HashiCorp Vault.
Rotation: Replacing keys regularly to limit damage from potential compromise.
Revocation: Immediately invalidating compromised keys while maintaining system continuity.
Cloud-native environments complicate this process, especially with autoscaling services and ephemeral containers. Systems must support zero-trust key access, automated audit logging, and role-based access control. Improper key reuse, weak entropy, or lack of rotation policies are among the most common causes of data exposure—even with strong algorithms in place.
As encryption standards evolve, organizations are investing in centralized key orchestration and policy-based automation, integrating services like AWS KMS, Azure Key Vault, and Google Cloud KMS for scalable governance.
Protocols Using Encryption: TLS, IPSec, S/MIME
Modern encryption isn’t abstract—it operates through protocols built for specific layers of communication. Some of the most critical include:
TLS (Transport Layer Security): Powers HTTPS, email servers, APIs, and VPNs. Uses asymmetric encryption for handshake (RSA/ECDSA) and symmetric (AES/ChaCha20) for session data.
IPSec: Secures IP-level data for VPN tunnels and internal network traffic. Often deployed in site-to-site or host-to-site configurations.
S/MIME (Secure/Multipurpose Internet Mail Extensions): Provides end-to-end email encryption and sender authentication, often using RSA or ECC keys. Widely used in enterprises for compliance-heavy communication.
These protocols aren’t just technical preferences—they’re tied to compliance mandates like HIPAA, PCI-DSS, and GDPR, which specify encryption at rest, in transit, and in use. A misconfigured cipher suite or outdated protocol version (e.g., TLS 1.0) can open attack vectors like downgrade attacks or padding oracles.
As encryption matures, performance and compatibility remain core concerns. Organizations must benchmark algorithm strength against CPU load, latency, memory impact, and cross-platform support. Efficient encryption now means using the right protocol stack in the right place—with encryption that’s not only secure, but practical under load.
| Phase | What It Involves | Why It Matters |
|---|---|---|
| Key Generation | Use of high-entropy, cryptographically secure random number generators | Prevents predictability and brute-force vulnerabilities |
| Key Storage | Storing keys in secure hardware/software: HSMs, TPMs, or HashiCorp Vault | Protects keys from unauthorized access—even from internal threats |
| Key Rotation | Regularly replacing keys using automated, policy-based rotation | Limits exposure if a key is compromised or reused |
| Key Revocation | Disabling keys immediately when compromised or expired | Maintains system trust while isolating breaches |
| Cloud Integration | Managing keys across multi-region, autoscaling, and ephemeral environments | Requires orchestration tools like AWS KMS, Azure Key Vault, or Google Cloud KMS |
Why Encryption Standards Matter for Cybersecurity Careers
How ACSMI’s Advanced Cybersecurity & Management Certification (ACSMC) Covers Encryption
Encryption isn’t just a technical layer—it’s a core skill for cybersecurity professionals, from entry-level analysts to CISOs. The Advanced Cybersecurity & Management Certification (ACSMC) by ACSMI trains learners on how to deploy, manage, and audit encryption systems across real-world networks and enterprise stacks. It goes far beyond textbook theory and deep dives into:
AES deployment in cloud-native and hybrid environments
RSA key lifecycle policies in enterprise email and VPN setups
Integration of TLS, S/MIME, IPSec, and hybrid encryption stacks
Hands-on labs with tools like OpenSSL, GnuPG, and encrypted containers
The ACSMC curriculum includes over 170 CPD hours across 379 in-depth lessons, giving learners exposure to cryptographic standards in action—alongside the operational policies needed to manage them at scale. The certification also covers post-quantum preparedness, ensuring students don’t just rely on outdated systems.
Professionals graduating from the ACSMC program gain practical experience across symmetric, asymmetric, and hybrid encryption—positioning them as strong candidates for encryption-centric roles in both public and private sectors.
In-Demand Roles Requiring AES/RSA Knowledge (Security Analyst, Network Engineer, CISO paths)
Modern cybersecurity roles demand more than basic awareness of encryption—they demand deployment fluency. Below are some high-demand roles where AES, RSA, and protocol mastery are not optional:
Security Analyst: Analysts must monitor traffic for encrypted threats, ensure TLS configurations are up to date, and identify improper key usage. Tools like Wireshark, Zeek, and Suricata rely on encryption visibility.
Network Security Engineer: Engineers implement IPSec VPNs, configure SSL inspection systems, and handle certificate infrastructure across large environments. Encryption is a daily function, not an edge case.
CISO / Security Architect: These leadership roles design encryption policies, enforce regulatory compliance, and evaluate quantum-risk exposure. They must make buy/build decisions on cryptographic systems while managing vendor risk.
Mastery of RSA and AES is no longer a specialization—it’s a hiring filter. Organizations assume candidates can audit, configure, and troubleshoot encryption stacks. Certifications like ACSMC signal to employers that a candidate has current, operational-grade cryptography training—not just academic exposure.
Frequently Asked Questions
-
AES is a symmetric encryption algorithm, meaning the same key is used to encrypt and decrypt data. It’s fast, efficient, and widely used in real-time systems like mobile apps and cloud storage. RSA is an asymmetric encryption method, using a public key for encryption and a private key for decryption. It’s slower but more secure for key exchange and digital signatures. In most systems, RSA initiates secure communication, while AES handles the actual data transmission. Together, they form the backbone of modern hybrid encryption protocols like TLS.
-
Yes—AES remains one of the most secure encryption standards available today, especially in its 256-bit variant. It’s resistant to brute-force attacks and has withstood decades of global cryptanalysis. AES-256 is even considered secure against near-term quantum attacks, although future systems may require post-quantum alternatives. Its performance, scalability, and proven security make it the default choice in banking, government, and cloud infrastructure globally. However, correct implementation, key management, and secure environments are critical to maintaining its strength.
-
RSA provides critical functionality in secure communications, such as key exchange and digital signatures. Despite being slower than AES or ECC, RSA’s reliability and widespread adoption make it indispensable in protocols like HTTPS, VPN authentication, and email encryption. Its asymmetric nature enables encryption without prior key exchange, which is crucial in open-network environments. While newer algorithms are gaining ground, RSA continues to secure billions of daily internet transactions, especially in enterprise and compliance-heavy sectors.
-
Post-quantum encryption refers to cryptographic algorithms that are secure against quantum computer attacks. Quantum systems running Shor’s algorithm could break RSA and ECC in seconds. To future-proof sensitive data—especially long-term medical, financial, and military records—quantum-resistant algorithms like CRYSTALS-Kyber and Dilithium are being standardized. These use lattice-based and hash-based techniques that remain hard even for quantum processors. As the quantum era approaches, organizations must adopt hybrid or post-quantum-ready protocols to prevent retroactive data compromise.
-
TLS (Transport Layer Security) is a hybrid encryption protocol. During the handshake, RSA or ECC is used for asymmetric key exchange and digital certificate validation. Once a secure session is established, a symmetric key is generated and used with AES for fast, encrypted communication. This hybrid model balances performance with security—RSA handles the trust, AES handles the speed. Modern TLS versions often support multiple ciphers, but AES remains the dominant symmetric cipher due to its speed and robustness.
-
Not entirely. While both ECC and RSA provide asymmetric encryption capabilities, they differ in efficiency, key size, and computational cost. ECC offers equal security at smaller key sizes, which improves performance in mobile and embedded devices. RSA is more established and broadly supported, especially in legacy systems and browsers. Some protocols, like TLS 1.3, support both, allowing negotiation based on device capability. However, ECC is rapidly replacing RSA in new systems, especially where bandwidth and power efficiency matter.
-
The most common encryption mistakes include:
Weak or hardcoded keys stored in source code or exposed environments.
Lack of key rotation policies, allowing outdated keys to remain active.
Using deprecated protocols like TLS 1.0 or weak ciphers like RC4.
Misconfigured certificate chains or ignoring certificate expiration.
No centralized key management, leading to visibility and audit failures.
Encryption alone doesn't guarantee security—implementation hygiene and governance are essential. Even strong algorithms like AES or RSA can be bypassed if attackers exploit key exposure or configuration gaps.
Final Thoughts
Encryption standards are no longer a backend detail—they’re a front-line defense in today’s cybersecurity strategy. As threats evolve, so must your understanding of what encryption protects, how it's implemented, and why even the strongest algorithm fails without disciplined key management. AES and RSA remain core to global data security, but the shift toward ECC and post-quantum algorithms is already underway. Professionals who can adapt with these changes are not just more employable—they're indispensable.
If you're pursuing a career in cybersecurity, cryptography fluency is non-negotiable. It’s the difference between configuring a secure VPN and unknowingly exposing a critical vulnerability. Whether you're hands-on with systems or overseeing enterprise policies, your ability to work with encryption—from TLS handshakes to lattice-based signatures—is a strategic asset. Stay ahead by mastering both the fundamentals and the future of encryption.