Zero‑Day Vulnerability: Risk & Defense Explained
Zero-day vulnerabilities aren’t a hypothetical threat—they’re an active, evolving menace against enterprise cybersecurity and global digital infrastructure. These hidden flaws are exploited before developers can release a fix, leaving systems exposed. Forrester estimates that 80% of successful breaches involve zero-day vulnerabilities, making them a primary target for sophisticated attacks. Companies face not just financial damages but also regulatory risks and reputational fallout. Modern threat actors leverage automated tools and AI-driven reconnaissance to identify and exploit these flaws, outpacing traditional defenses. This urgent reality demands a proactive, multi-layered defense strategy that covers detection, response, and recovery.
Zero-day attacks bypass conventional antivirus and endpoint security measures, exploiting weaknesses at machine speed. Reactive patching isn’t enough; organizations must shift to real-time threat intelligence, agile patch management, and network segmentation to limit exposure. As the attack surface expands with cloud adoption and remote work, the risk multiplies. This article dives into the mechanics of zero-day vulnerabilities, outlines evolving attack methods, and details practical mitigation strategies. Understanding these threats is no longer optional; it’s essential for protecting your organization’s digital integrity and staying ahead of sophisticated adversaries.
What Is a Zero-Day Vulnerability?
A zero-day vulnerability refers to an undisclosed flaw in software or hardware that is actively exploited by attackers before a patch or fix is available. Unlike typical vulnerabilities that vendors can address through updates, zero-days are exploited in secrecy, leaving systems wide open to attack. These flaws are often discovered by hackers or sophisticated cybercriminal groups, who either deploy them for immediate gains or sell them in underground markets. The risk is magnified because no existing defense mechanisms are designed to recognize or block these attacks, allowing adversaries to gain unauthorized access or exfiltrate sensitive data.
Definition and Context
Zero-day vulnerabilities are the digital equivalent of a thief finding a key under a doormat—except in this case, the doormat isn’t even supposed to exist. These vulnerabilities arise from coding errors, misconfigurations, or overlooked system weaknesses. Their discovery doesn’t guarantee immediate exploitation, but in today’s landscape, the lag between discovery and attack is shrinking. Often associated with state-sponsored cyberattacks, zero-days also fuel targeted attacks on businesses and individuals. They’re particularly dangerous because victims are blind to the threat until damage is done, often realized only through post-incident analysis.
Key Characteristics of Zero-Day Exploits
Zero-day exploits capitalize on the element of surprise. Detection tools don’t recognize the signatures of these attacks, and their delivery often mimics legitimate system behavior, camouflaging their presence. They’re used in advanced persistent threats (APTs), where adversaries establish long-term control over systems to steal intellectual property or sabotage operations. Unlike common malware, zero-day attacks are crafted for stealth and precision. Once disclosed, the window for patching and mitigation narrows dramatically, making early detection and proactive defense essential.
Why They Pose a Unique Risk
Zero-day vulnerabilities present a unique risk because they provide a “free pass” through security controls, often bypassing antivirus, firewalls, and intrusion detection systems. Attackers can weaponize these flaws to deliver ransomware, steal credentials, or disrupt critical infrastructure. The sophistication of modern zero-day exploits means that even organizations with robust security measures can fall prey. Complicating matters, disclosure timelines for these vulnerabilities are often uncertain—by the time a patch is available, systems may already be compromised. Effective defense requires a blend of proactive monitoring, rapid patching, and incident readiness.
Quick Poll: How prepared do you feel your organization is to defend against zero-day vulnerabilities?
How Are Zero-Day Vulnerabilities Discovered?
Zero-day vulnerabilities are unearthed by two distinct groups: security researchers and malicious actors. These discoveries often spark a race between defenders and attackers, where the side that moves faster dictates the scale of impact. Security researchers employ manual code reviews, automated vulnerability scanning, and fuzz testing to identify these hidden flaws. Conversely, cybercriminals use custom tools and intelligence to seek out weak spots in software before a fix emerges. Zero-day markets thrive in the shadows, where exploits are traded for high sums, fueling underground economies. For defenders, speed and precision are critical. Delayed discovery equates to prolonged exposure, increasing the likelihood of a successful breach.
Discovery by Security Researchers
Security researchers—both independent experts and those within cybersecurity firms—deploy a range of proactive techniques to unearth zero-day vulnerabilities. These include reverse engineering, sandbox analysis, and behavior-based detection, allowing them to observe how software handles unexpected inputs. In ethical hacking environments, researchers mimic real-world adversaries, using advanced simulation tools to stress-test systems. Bug bounty programs further incentivize this work, offering monetary rewards for discovering flaws before they’re exploited. The collective goal is clear: close the gap between discovery and patching, limiting adversaries’ opportunities to exploit these weaknesses.
Discovery by Cybercriminals
On the other side, cybercriminals operate with stealth and resourcefulness. They employ customized malware, targeted phishing campaigns, and vulnerability scanners to identify zero-day flaws in software ranging from operating systems to niche business applications. Unlike ethical researchers, their intent isn’t disclosure—it’s weaponization. Once a zero-day is discovered, it may be sold on black markets for millions or used directly in high-value attacks. State-sponsored groups often lead these efforts, employing elite hacking teams to identify vulnerabilities that can be used in espionage or sabotage. The commercial value of these exploits drives a relentless, competitive pursuit.
Examples of Recent High-Profile Zero-Days
Recent zero-day incidents underscore the urgency of proactive defense. The SolarWinds Orion breach, linked to a sophisticated supply chain attack, exploited multiple zero-days to infiltrate U.S. government agencies and major corporations. The Log4Shell vulnerability in Apache’s Log4j library exposed millions of servers worldwide to remote code execution, demonstrating how widespread and damaging such flaws can be. More recently, Google’s Chrome zero-day exploits have highlighted how even widely used browsers remain vulnerable. These examples reinforce that zero-day vulnerabilities are not rare anomalies—they’re ongoing, escalating threats demanding immediate, strategic action.
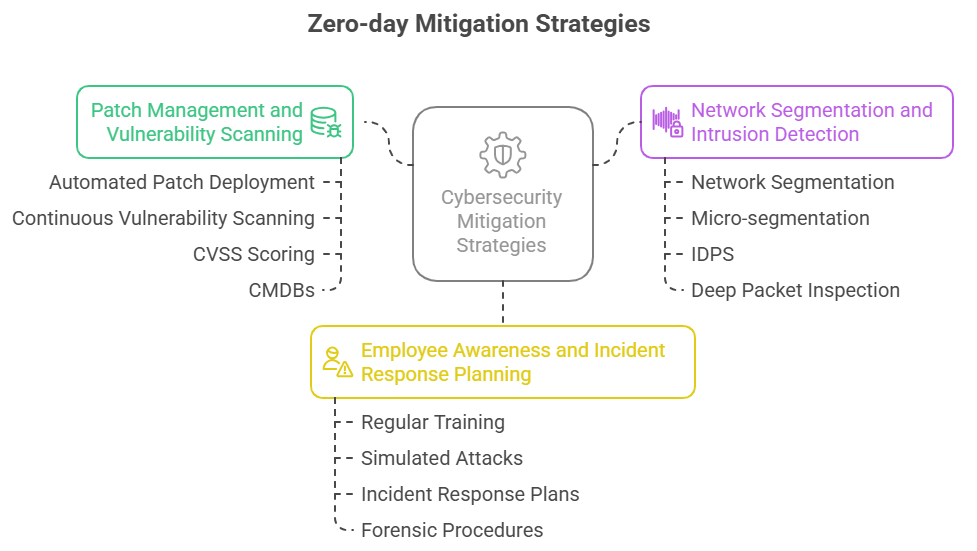
Mitigation Strategies and Best Practices
Mitigating zero-day vulnerabilities demands a proactive, multi-layered defense strategy that integrates cutting-edge tools and organizational policies. Traditional, reactive security postures are insufficient against these fast-evolving threats. Instead, organizations must shift to continuous monitoring, aggressive patch management, and comprehensive user awareness programs. Building resilience against zero-days starts with recognizing the inevitability of initial exposure and preparing systems to limit damage and recover swiftly.
Patch Management and Vulnerability Scanning
Effective patch management is the frontline defense. Organizations should implement automated patch deployment systems to reduce the lag between vulnerability disclosure and patch implementation. Vulnerability scanning tools, running on a continuous basis, identify known weaknesses and misconfigurations that could compound the impact of a zero-day. Prioritization frameworks, such as CVSS scoring and threat intelligence integration, enable teams to address the most critical issues first. Complementing this with configuration management databases (CMDBs) ensures that all assets are tracked and protected. These practices compress the window of vulnerability and reduce the attack surface.
Network Segmentation and Intrusion Detection
Zero-day mitigation requires limiting the blast radius. Network segmentation isolates critical systems, preventing lateral movement of attackers if a breach occurs. Micro-segmentation techniques, leveraging software-defined networking (SDN), dynamically enforce security policies at the workload level. Coupled with intrusion detection and prevention systems (IDPS), organizations can identify anomalous behavior indicative of a zero-day exploit in progress. Deep packet inspection and behavioral analytics flag suspicious activity, allowing security teams to respond in near real-time. Effective segmentation also supports containment strategies when patching isn’t immediately possible, buying crucial response time.
Employee Awareness and Incident Response Planning
Human factors play a pivotal role. Regular, targeted training programs equip employees with the knowledge to recognize phishing attempts, suspicious links, and social engineering tactics that often precede zero-day exploits. Simulated attacks and red team exercises further reinforce this vigilance. Beyond awareness, robust incident response plans ensure that breaches are contained and remediated swiftly. These plans should include clearly defined roles, communication protocols, forensic procedures, and legal considerations. Regular testing of incident response readiness, through tabletop exercises and live simulations, ensures teams can execute under pressure. This holistic approach transforms employees from potential vulnerabilities into active defenders.
How Zero-Day Exploits Evolve Over Time
Zero-day exploits aren’t static; they represent a continuously shifting frontier of cyber risk. Attackers refine their tactics at a rapid pace, leveraging automated scanning, AI-driven reconnaissance, and adaptive malware to sidestep evolving defenses. As organizations reinforce their infrastructures, adversaries respond with more sophisticated, persistent attack strategies that exploit even minor system weaknesses. These exploits aren’t limited to individual systems; they increasingly target entire supply chains, cloud-native platforms, and IoT ecosystems, amplifying potential impact.
Continuous Evolution of Exploit Tactics
Zero-day exploits aren’t static code anomalies—they’re dynamic tools in an attacker’s arsenal. As organizations implement stronger defenses, cyber adversaries leverage automated reconnaissance, AI-powered scanning, and adaptive attack frameworks to locate undiscovered flaws. Modern exploits shift from isolated strikes to coordinated campaigns targeting entire industries or supply chains. This constant evolution transforms zero-days from technical curiosities into long-term strategic threats that demand relentless vigilance.
Escalation of Attack Complexity
Zero-day exploits now involve multi-stage, modular payloads designed for stealth and persistence. Techniques such as fileless malware, privilege escalation, and lateral movement via LotL (living-off-the-land) complicate detection and remediation. Zero-day-as-a-service offerings on underground markets have further democratized these sophisticated attack methods, making them accessible to cybercriminals beyond nation-state actors. This escalation expands the threat landscape and challenges even the most mature cybersecurity teams.
Emerging Vulnerabilities in Expanding Attack Surfaces
With cloud-native architectures, IoT ecosystems, and supply chain platforms proliferating, attackers are pivoting to less-defended and complex environments. APIs, containerized applications, and microservices architectures often lack comprehensive patching protocols, leaving them susceptible to zero-day exploitation. The fusion of IT and OT systems introduces new attack vectors, including industrial control systems and critical infrastructure. This shift underscores the need for future-ready cybersecurity strategies that preemptively identify and mitigate evolving vulnerabilities.
Tools and Frameworks for Zero-Day Defense
Defending against zero-day vulnerabilities requires a robust mix of cutting-edge tools and compliance-driven frameworks. This ecosystem must be dynamic, adaptive, and deeply integrated with both IT and security operations. While no single tool can guarantee immunity, combining multiple solutions creates a layered defense that complicates an attacker’s path.
EDR, XDR, and Threat Intelligence Tools
Modern zero-day defense hinges on advanced detection technologies. Endpoint Detection and Response (EDR) platforms, fortified with machine learning, spot behavioral anomalies indicative of exploit attempts. Extended Detection and Response (XDR) consolidates signals from endpoints, networks, and cloud workloads to provide a unified incident response mechanism. Threat intelligence platforms (TIPs) ingest global data feeds to recognize and correlate emerging zero-day attack patterns, empowering proactive defense. These tools ensure that even novel attack vectors don’t go unnoticed.
Deception Technologies and Early Warning Systems
To detect zero-day attacks early, organizations deploy deception technologies like honeypots and honey tokens. These tools mimic legitimate assets, diverting attackers and revealing exploit attempts before they reach critical infrastructure. Behavioral analytics embedded in these systems allow for precise detection without generating excessive false positives. By providing a controlled environment for adversaries to expose their tactics, these technologies enable defenders to adapt in real time, minimizing impact.
Compliance-Driven Frameworks and Best Practices
Security frameworks provide a blueprint for resilience. MITRE ATT&CK, NIST CSF, and ISO/IEC 27001 outline tactical defenses, risk management protocols, and operational hardening practices. Compliance standards such as PCI DSS for payment processing and HIPAA for healthcare enforce strict controls to limit vulnerability exposure. Integrating these frameworks ensures that organizations not only meet legal and regulatory mandates but also stay ahead of evolving zero-day exploit methodologies.
| Category | Details |
|---|---|
| EDR, XDR, and Threat Intelligence Tools |
|
| Deception Technologies and Early Warning Systems |
|
| Compliance-Driven Frameworks and Best Practices |
|
How Advanced Cybersecurity & Management Certification Can Help You Master Zero-Day Defense
The Advanced Cybersecurity & Management Certification isn’t just another cybersecurity course—it’s an immersive, elite-level program crafted to arm professionals with real-world tactics against zero-day threats. The curriculum integrates live attack simulations, case studies of major breaches, and hands-on labs, mirroring the rapidly evolving threat landscape. Learners don’t just absorb theory—they master real-world TTPs (tactics, techniques, procedures) used by today’s adversaries.This certification dives deep into vulnerability discovery, zero-day exploit prevention, and incident response planning, ensuring participants can seamlessly integrate tools like EDR, XDR, and deception technologies into their operational workflows.
The program aligns with MITRE ATT&CK and NIST CSF, equipping learners with frameworks that are directly applicable to enterprise environments. Graduates exit the program fully prepared to anticipate, mitigate, and neutralize advanced zero-day exploits. With expert-led instruction, exclusive access to a global threat intelligence network, and a globally recognized certification, the Advanced Cybersecurity & Management Certification delivers both credibility and actionable skills. Organizations investing in this program build a workforce capable of transforming potential vulnerabilities into proactive resilience. In an era where zero-day attacks are the norm, this certification provides the expertise to turn defense into competitive advantage.
Conclusion
Zero-day vulnerabilities are more than technical flaws—they are strategic threats that can devastate organizations if left unaddressed. The stakes have never been higher, with state-sponsored actors, sophisticated cybercriminals, and opportunistic hackers exploiting these hidden gaps at unprecedented speed. Proactive defense isn’t just a best practice; it’s a survival imperative.
This guide has equipped you with a deep understanding of zero-day vulnerabilities—their discovery, evolving attack patterns, and best-in-class mitigation strategies. It’s now clear that resilience requires a layered approach, combining advanced tools, user training, and adherence to industry frameworks. For professionals and organizations ready to turn this knowledge into actionable defense, the Advanced Cybersecurity & Management Certification offers the roadmap. In a digital ecosystem where threats evolve faster than defenses, preparedness is everything. The time to act is not tomorrow—it’s now.
Frequently Asked Questions
-
A zero-day vulnerability is a software or hardware flaw unknown to the vendor and unpatched, leaving it open to immediate exploitation. These vulnerabilities arise from coding errors, overlooked system weaknesses, or misconfigurations. Unlike known vulnerabilities, which vendors can address through security patches, zero-days offer no early warnings. Attackers leverage them to infiltrate networks, steal data, or disrupt operations before defenses are in place. The window of risk persists until a patch is developed and deployed. Recognizing these threats is crucial for organizations aiming to safeguard their digital assets against high-impact cyberattacks.
-
Known security flaws are publicly disclosed, with patches and updates available from vendors, while zero-day vulnerabilities remain undisclosed and actively exploited. Zero-days present an asymmetric threat because defenders lack prior knowledge of the flaw, leaving systems defenseless. Attackers exploit this secrecy to bypass traditional defenses, causing significant breaches. In contrast, known flaws often have documented signatures, enabling antivirus tools and intrusion detection systems to mitigate risks. Rapid identification, patching, and incident response planning are vital to minimize exposure from known flaws, but zero-days require proactive, advanced detection strategies.
-
Zero-day vulnerabilities evade conventional detection because their signatures are unknown and their exploitation mimics legitimate behavior. Attackers use advanced techniques, such as living-off-the-land (LotL) methods, to blend into normal system processes. Traditional antivirus and intrusion detection systems often miss these subtle anomalies. Furthermore, zero-days may be embedded in critical systems or supply chains, making identification challenging. Effective mitigation requires behavior-based analytics, advanced endpoint detection tools (EDR), and threat intelligence platforms that monitor for unusual patterns. Without proactive defense mechanisms, organizations remain vulnerable to these stealthy, high-impact attacks.
-
Upon discovering a zero-day exploit, organizations must act swiftly. First, isolate affected systems to prevent lateral movement and limit damage. Next, engage incident response teams to analyze the exploit’s nature, scope, and potential impact. Deploy compensating controls, such as network segmentation and enhanced monitoring, to contain the threat. Collaboration with vendors and trusted cybersecurity partners accelerates patch development or alternative mitigations. Additionally, communication plans should be activated to inform stakeholders and regulatory bodies if necessary. Proactive containment, combined with rapid response, minimizes business disruption and preserves operational integrity.
-
The Advanced Cybersecurity & Management Certification equips learners with actionable skills to detect, mitigate, and neutralize zero-day threats. The program includes hands-on labs, real-world attack simulations, and expert-led sessions covering advanced detection tools like EDR, XDR, and deception technologies. Participants master frameworks such as MITRE ATT&CK and NIST CSF, enabling precise, compliance-aligned responses to evolving threats. This certification also connects professionals to a global threat intelligence network, keeping them updated on emerging zero-day tactics. Graduates exit with the expertise to anticipate, contain, and recover from zero-day breaches effectively.
-
Effective zero-day defense relies on an ecosystem of specialized tools. Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) platforms monitor system behaviors for anomalies that signal zero-day exploits. Threat Intelligence Platforms (TIPs) aggregate real-time data from global sources, helping detect emerging threats. Deception technologies, like honeypots, divert attackers and provide early warning. Vulnerability management and patch automation tools accelerate response times once a flaw is identified. Collectively, these technologies create a proactive, layered defense that reduces the window of exposure and improves incident readiness.