Endpoint Detection and Response (EDR): Tools and Implementation
Endpoint Detection and Response (EDR) is the modern cornerstone of proactive cybersecurity, essential for organizations facing increasingly sophisticated threats like fileless malware and advanced persistent threats. Unlike traditional tools that focus solely on prevention, EDR solutions specialize in post-compromise detection, leveraging continuous endpoint telemetry, automated response workflows, and behavioral analytics to identify, isolate, and mitigate threats in real time. This shift from reactive to proactive defense ensures breaches are contained before they escalate, reducing the risk of widespread impact.
The implementation of EDR is more than a technological upgrade; it’s a strategic evolution of security operations. It requires organizations to integrate granular monitoring, skilled incident response teams, and clear protocols for containment and remediation. By correlating endpoint activity across diverse devices, EDR platforms empower security teams to detect lateral movement, prevent data exfiltration, and maintain business continuity. This guide dissects EDR’s core functions, explores leading tools, and delivers actionable strategies for deploying EDR effectively—helping organizations not only react to attacks but stay several steps ahead in the evolving cybersecurity landscape.
What Is EDR?
Endpoint Detection and Response (EDR) is a sophisticated cybersecurity solution designed to detect, investigate, and respond to endpoint threats in real time. Unlike traditional antivirus software, which focuses on static threat signatures, EDR operates dynamically by collecting and analyzing vast amounts of endpoint telemetry. This includes logs, processes, registry modifications, and user activity patterns. EDR platforms leverage this data to identify subtle behavioral anomalies, flagging potential threats that evade signature-based detection.
EDR is not just about detection—it’s about rapid, effective response. Once a threat is detected, EDR solutions automatically isolate compromised devices, terminate malicious processes, and initiate forensic analysis to understand the attack vector and scope. This ensures that response efforts are immediate and precise, reducing the window for potential lateral movement across the network. By offering a combination of cyber threat detection, containment, and response, EDR platforms close the gap between breach occurrence and resolution.
Moreover, EDR solutions are scalable and adaptive, built to handle diverse environments including hybrid cloud, on-premises, and remote work setups. They integrate seamlessly with existing security infrastructures like SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response), enhancing their ability to deliver cohesive, end-to-end threat management. The versatility of EDR allows organizations to adapt their threat response strategies to evolving adversaries and infrastructure changes.
At its core, EDR represents a fundamental shift in security mindset. It transforms endpoint security from a reactive perimeter defense to a proactive, forensic-driven model. By continuously monitoring and analyzing endpoint behavior, EDR platforms provide visibility into the tactics, techniques, and procedures (TTPs) of threat actors, enabling organizations to anticipate, identify, and neutralize sophisticated attacks before they cause irreparable damage.
Core Functions
EDR platforms operate by delivering three primary functions that work in tandem to secure endpoint environments. The first is continuous monitoring and data collection. EDR solutions gather telemetry from endpoints, including processes, system calls, file modifications, and network activity. This data forms the foundation for behavioral analysis, enabling systems to detect anomalies that could indicate compromise.
The second function is advanced threat detection and analysis. EDR platforms use machine learning and heuristic algorithms to scrutinize endpoint behavior, identifying patterns associated with malware, lateral movement, or privilege escalation. Unlike static detection methods, this analysis adapts to emerging threats, recognizing both known and unknown attack vectors.
Finally, automated response and remediation capabilities empower EDR solutions to act swiftly upon detection. When an anomaly is flagged, EDR tools can isolate the affected endpoint, terminate malicious processes, and execute pre-configured scripts to contain and mitigate damage. These responses are executed at machine speed, reducing manual intervention and limiting the impact of breaches.
Together, these functions enable organizations to maintain a proactive security posture, ensuring that threats are not only detected but neutralized before they escalate.
Key Differences from Antivirus
While both antivirus software and EDR aim to protect endpoints, their approaches and capabilities differ fundamentally. Traditional antivirus relies on signature-based detection, matching known malware signatures to identify threats. This method is effective against known malware strains but fails to detect new or sophisticated attacks that don’t match existing patterns.
In contrast, EDR solutions leverage behavior-based detection. Instead of focusing on static signatures, EDR platforms monitor endpoint activities in real time to spot anomalies indicative of potential threats. This includes suspicious process behaviors, unauthorized access attempts, or lateral movement tactics that often precede large-scale breaches. This adaptability enables EDR to detect both known and unknown threats—a critical capability in today’s fast-evolving threat landscape.
Another key difference lies in response capabilities. Antivirus software primarily prevents malware from executing but offers limited options once an attack has bypassed its defenses. EDR, however, provides real-time remediation tools. It can isolate infected endpoints, terminate malicious processes, and initiate forensic analysis to trace the attack’s origin. This immediate response dramatically reduces dwell time, minimizing the potential impact of breaches.
Ultimately, EDR transforms endpoint security from a reactive model to a proactive, adaptive defense mechanism, closing the gap between detection and response.
Top EDR Tools for 2025
The landscape of EDR tools is constantly evolving to address the latest cybersecurity challenges. In 2025, organizations seeking robust endpoint protection should focus on platforms that offer comprehensive threat detection, rapid response, and seamless integration with existing security stacks. Let’s explore the leading solutions, their comparative features, and the pros and cons of each.
Leading Solutions
Among the top contenders are CrowdStrike Falcon, Microsoft Defender for Endpoint, and SentinelOne Singularity. CrowdStrike Falcon stands out for its cloud-native architecture, which supports lightweight agents and real-time threat intelligence. It excels at rapid detection and remediation, leveraging an extensive threat database to stay ahead of adversaries.
Microsoft Defender for Endpoint integrates seamlessly with Windows environments, offering built-in endpoint protection, attack surface reduction, and automated investigation capabilities. It’s particularly appealing for organizations already invested in the Microsoft ecosystem.
SentinelOne Singularity differentiates itself with autonomous AI-driven detection and response, minimizing human intervention. It provides high-performance threat hunting, behavioral analysis, and rollback capabilities to restore affected systems to their pre-attack state.
Comparative Features
When comparing these tools, it’s essential to assess scalability, integration, and detection capabilities. CrowdStrike Falcon delivers real-time response across large, distributed networks, making it suitable for enterprises with complex infrastructures. Its API-first approach enables seamless integration with SIEM and SOAR platforms, enhancing centralized incident management.
Microsoft Defender for Endpoint leverages deep integration with Azure and Microsoft 365, offering single-pane visibility and automated actions driven by Microsoft’s threat intelligence. However, it may be less effective for heterogeneous environments that rely on diverse operating systems.
SentinelOne’s autonomous capabilities make it a top choice for organizations with limited security staff, providing automated detection, containment, and rollback with minimal manual intervention. However, its advanced features may require fine-tuning to reduce false positives in complex environments.
Pros and Cons
CrowdStrike Falcon’s cloud-native architecture and proactive threat intelligence ensure scalability and resilience, but it may incur higher costs, particularly for small businesses. Microsoft Defender for Endpoint offers cost-effectiveness and seamless integration, but its optimal performance hinges on existing Microsoft infrastructure. SentinelOne’s AI-driven automation and rollback capabilities enable rapid response and system recovery, though tuning and management may present challenges in large, heterogeneous networks.
Ultimately, selecting the right EDR tool depends on the organization’s size, infrastructure complexity, and response requirements. A tailored approach—considering detection accuracy, scalability, and integration—ensures optimal protection against evolving endpoint threats.
| Tool | Key Features | Pros | Cons |
|---|---|---|---|
| CrowdStrike Falcon |
- Cloud-native - Lightweight agents - Real-time threat intelligence - API-first integration |
- Scalable - Proactive threat detection - Integrates with SIEM & SOAR |
- Higher cost - May be complex for small businesses |
| Microsoft Defender for Endpoint |
- Deep integration with Windows, Azure, and Microsoft 365 - Built-in protection - Automated investigation |
- Cost-effective - Seamless in Microsoft environments |
- Limited effectiveness in diverse operating systems |
| SentinelOne Singularity |
- Autonomous AI-driven detection - Containment - Rollback - Minimal manual intervention |
- Automated - Efficient threat hunting - System recovery |
- May require fine-tuning - Possible false positives in complex setups |
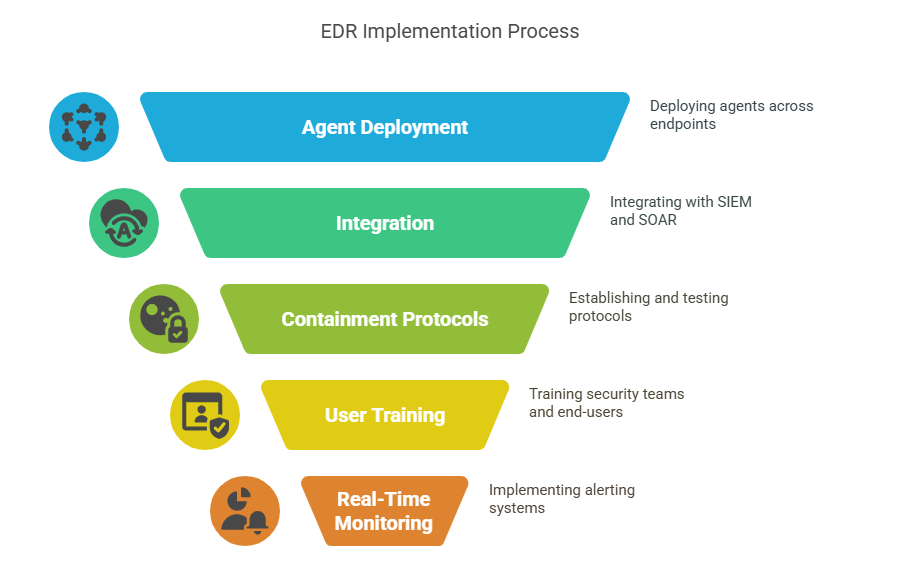
Effective EDR Implementation
Successful EDR implementation hinges on a balanced combination of technology, processes, and human expertise. Organizations must approach deployment strategically, ensuring seamless integration and continuous monitoring to derive maximum value from their chosen EDR solution.
Deployment Best Practices
Begin with a comprehensive readiness assessment to identify existing vulnerabilities and define clear objectives. This step ensures alignment between business goals and security needs. Next, deploy EDR agents across all endpoint types—laptops, desktops, servers, and mobile devices—ensuring consistent visibility and telemetry collection.
Integrate the EDR platform with existing security infrastructure, including SIEM and SOAR solutions, for centralized incident management and automated workflows. Establish clear containment and remediation protocols tailored to the organization’s risk tolerance and operating environment. Regularly test these protocols through simulated breaches and tabletop exercises to refine detection and response capabilities.
User training is crucial; ensure security teams understand the EDR platform’s functionality, including threat hunting, forensic analysis, and automated playbooks. Equally important is ensuring end-user awareness to reduce the risk of social engineering attacks or user errors that could compromise endpoints.
Post-Deployment Monitoring
Once deployed, continuous monitoring is essential. Implement real-time alerting systems with actionable thresholds to detect suspicious behavior immediately. Set up automated containment actions for high-severity incidents to reduce reliance on manual intervention.
Regularly review endpoint telemetry to identify emerging threats or previously undetected anomalies. Leverage the EDR platform’s forensic and root cause analysis tools to investigate incidents thoroughly, minimizing recurrence. Maintain detailed logs of all activities for compliance and audit purposes.
Finally, establish a continuous improvement cycle. Analyze performance metrics, false-positive rates, and incident response timelines to fine-tune detection rules and response workflows. By iterating and optimizing processes, organizations can ensure that their EDR deployment remains adaptive and resilient, ready to counter emerging endpoint threats effectively.
Mastering EDR Tools and Strategy with ACSMI’s Advanced Cybersecurity Training
Endpoint Detection and Response (EDR) is not just a standalone technology—it’s an integral component of advanced cybersecurity frameworks, exemplified by programs like ACSMI’s Advanced Cybersecurity & Management Certification. This certification program, designed for security professionals, emphasizes the need for a comprehensive understanding of EDR to meet today’s complex threat landscape.
EDR equips cybersecurity specialists with the ability to proactively detect, contain, and respond to endpoint attacks. The ACSMC curriculum aligns with this by covering essential topics such as real-time endpoint monitoring, behavioral analysis, forensic investigations, and automated response protocols. These skills are critical for security leaders tasked with safeguarding sensitive infrastructures and maintaining regulatory compliance.
The integration of EDR with broader security architectures, including SIEM, SOAR, and threat intelligence platforms, is a focal point of ACSMC’s practical modules. This ensures participants gain hands-on experience configuring and managing EDR solutions as part of an end-to-end defense strategy. Such comprehensive training prepares professionals not just to deploy EDR tools effectively but also to optimize and evolve their deployment strategies in response to emerging adversarial tactics.
By mastering EDR’s nuances within the ACSMC framework, cybersecurity professionals gain a distinct competitive edge, positioning them as essential players in defending modern digital ecosystems against evolving endpoint threats.
Our Verdict
Endpoint Detection and Response (EDR) represents a fundamental shift in endpoint security, moving from static, signature-based protection to a dynamic, behavior-driven defense model. EDR solutions offer the real-time detection, rapid response, and comprehensive forensic insights necessary to secure modern organizations against increasingly sophisticated threats. Their integration with existing security infrastructures—like SIEM and SOAR—further enhances threat visibility and response capabilities, providing a cohesive security posture.
However, the effectiveness of EDR depends heavily on strategic implementation, ongoing monitoring, and continuous improvement. Organizations must align EDR deployment with broader cybersecurity goals, ensuring seamless integration and user adoption. By investing in the right tools, robust protocols, and continuous skill development, security teams can transform EDR from a reactive tool into a proactive, adaptive defense strategy. Ultimately, EDR is not just a security upgrade—it’s an operational imperative in today’s evolving threat landscape.
Frequently Asked Questions
-
EDR and traditional antivirus solutions differ fundamentally in approach and capability. While antivirus tools focus on signature-based detection, identifying threats that match known malware patterns, EDR systems leverage behavior-based analysis. EDR platforms continuously monitor endpoint activity, flagging anomalies like lateral movement, suspicious process behavior, and unauthorized access attempts. This enables detection of both known and unknown threats, providing a far more comprehensive layer of protection than static antivirus solutions can offer.
-
EDR solutions dramatically reduce incident response times by automating detection and containment processes. Once a potential threat is detected, EDR can automatically isolate the affected endpoint, terminate malicious processes, and initiate forensic analysis. This swift action minimizes the window for attackers to cause damage or exfiltrate data. Real-time alerting and automated playbooks ensure that incidents are addressed promptly, often before human intervention is required, enhancing overall security effectiveness.
-
Yes, most modern EDR solutions are designed for seamless integration with SIEM, SOAR, and threat intelligence platforms. This integration enables centralized incident management, automated workflows, and cohesive visibility across the entire security ecosystem. By correlating EDR telemetry with broader threat intelligence, security teams can identify patterns and respond more effectively, ensuring a holistic defense strategy that adapts to evolving threats.
-
EDR implementation can face several challenges, including ensuring endpoint coverage, minimizing false positives, and managing operational complexity. Organizations must deploy agents consistently across all endpoints and fine-tune detection rules to balance sensitivity and accuracy. Skilled personnel are essential for effective configuration, threat hunting, and response management. Additionally, aligning EDR with existing security protocols and ensuring user adoption can be time-consuming but is critical for long-term success.
-
EDR platforms provide detailed logs, forensic insights, and real-time monitoring, enabling organizations to meet compliance requirements for data protection and breach reporting. Automated containment and response actions reduce the likelihood of data exfiltration, while comprehensive reporting capabilities ensure transparency and accountability during audits. EDR’s ability to maintain detailed activity records supports regulatory compliance with frameworks like GDPR, HIPAA, and PCI DSS.
-
Absolutely. EDR platforms are particularly adept at detecting fileless malware—malicious code that operates entirely in-memory and doesn’t leave traditional file signatures. By focusing on behavior patterns and system interactions, EDR can identify the anomalous activities that signal fileless attacks, such as unusual PowerShell execution, WMI abuse, or suspicious registry modifications. This ensures that even stealthy, signature-less threats are effectively contained and neutralized.
-
Modern EDR solutions are designed to scale efficiently across large, distributed environments, including hybrid cloud, on-premises, and remote work infrastructures. Cloud-native architectures support lightweight agents and centralized management, ensuring consistent visibility and response capabilities across all endpoints. Scalability features like automated updates, policy inheritance, and centralized dashboards make it feasible to manage vast numbers of endpoints with minimal manual intervention, even in dynamic, globally distributed organizations.
-
EDR platforms empower security teams to engage in proactive threat hunting by providing detailed telemetry, customizable detection rules, and forensic investigation tools. Analysts can query endpoint data, correlate events, and identify subtle indicators of compromise (IOCs) that might otherwise evade detection. By actively seeking out anomalies and vulnerabilities, organizations can neutralize emerging threats before they materialize into full-scale attacks, transforming EDR into a proactive defense mechanism rather than a reactive tool.