Firewall Technologies: Types and Configurations
Firewalls are the first line of defense in cybersecurity, serving as critical barriers between trusted internal networks and external threats. They act as gatekeepers, inspecting incoming and outgoing traffic to enforce predefined security rules. In today’s threat landscape, where cyberattacks exploit even minor vulnerabilities, firewalls are not optional—they are essential. Organizations deploy diverse firewall technologies tailored to specific environments, whether on-premises, cloud, or hybrid. However, the complexity of configuring these solutions often introduces vulnerabilities. Misconfigurations, inadequate updates, and poor rule management can expose networks to sophisticated cyber attacks.
This guide dissects the types of firewalls, key configurations, real-world case studies, and best practices. It also explores how ACSMI’s Advanced Cybersecurity & Management Certification equips professionals with hands-on expertise in designing, deploying, and managing robust firewall architectures. Despite advancements, configuring firewalls for maximum protection is challenging. IT teams must balance tight security controls with operational efficiency, ensuring legitimate traffic flows unhindered while malicious activities are blocked. Missteps in firewall deployment have led to high-profile breaches, demonstrating the need for proper configurations and continuous monitoring.
Overview of Firewall Types
Packet-Filtering Firewalls
Packet-filtering firewalls inspect network traffic at the packet level, checking headers for criteria like IP addresses, protocols, and ports. They operate at OSI Layer 3 and 4, comparing packets against a set of predefined rules to determine whether to allow or block them. This type of firewall is straightforward and resource-efficient, making it suitable for simple network environments. However, it lacks state awareness, meaning it evaluates each packet in isolation without understanding connection context. This limitation allows attackers to exploit weaknesses through spoofing, fragmentation, or sequence number prediction. Packet-filtering firewalls are also ineffective against application-layer attacks, as they cannot inspect payload contents. Consequently, they offer only a basic layer of protection and are best used in combination with more advanced technologies.
Stateful Inspection Firewalls
Stateful inspection firewalls introduce contextual awareness, tracking the state of active connections to determine the legitimacy of incoming packets. These firewalls build a state table, recording session details such as source, destination, and port numbers, along with packet sequence numbers. By understanding the flow of an entire session, stateful firewalls can detect and block packets that deviate from expected behavior, effectively thwarting many spoofing and hijacking techniques. Operating at both the network and transport layers, they balance strong security with acceptable performance for most business environments. However, stateful firewalls are still limited in their ability to inspect payload content and may struggle to identify threats concealed in allowed traffic. They remain an integral component of layered security but require complementary tools for deep analysis.
Next-Generation Firewalls (NGFW)
Next-generation firewalls (NGFWs) build on traditional approaches by integrating deep packet inspection (DPI), intrusion prevention systems (IPS), and application-level control. NGFWs analyze complete packet content to identify sophisticated threats, such as malware, ransomware, and advanced persistent threats (APTs), that bypass conventional filters. These firewalls can enforce granular policies based on user identity, device characteristics, and application behavior, ensuring precise control over network access. Integration with threat intelligence feeds and automated response mechanisms enables proactive mitigation of emerging threats. NGFWs are designed for dynamic enterprise environments where a mix of devices and services interact across cloud and on-premises networks. Their ability to correlate data across layers makes them indispensable for modern security architectures, particularly in organizations handling sensitive data or subject to stringent compliance requirements.
| Firewall Type | Key Features | Limitations | Best Use Cases |
|---|---|---|---|
| Packet-Filtering Firewalls |
Inspects packet headers at OSI Layer 3/4 Compares to static rules Resource-efficient |
No state awareness Vulnerable to spoofing and fragmentation Cannot inspect payloads |
Simple, low-risk environments In combination with advanced technologies |
| Stateful Inspection Firewalls |
Tracks active session states Builds state tables Blocks spoofed/hijacked sessions Operates at network and transport layers |
Limited payload inspection May miss concealed threats |
Core network segmentation Layered security architectures |
| Next-Generation Firewalls (NGFW) |
Deep packet inspection (DPI) Intrusion prevention (IPS) Application-level control Granular, user/device-based policies Integrated threat intelligence and response |
Complexity and resource demands Requires skilled management |
Dynamic enterprise environments Handling sensitive data and compliance-heavy sectors |
Key Firewall Configurations and Use Cases
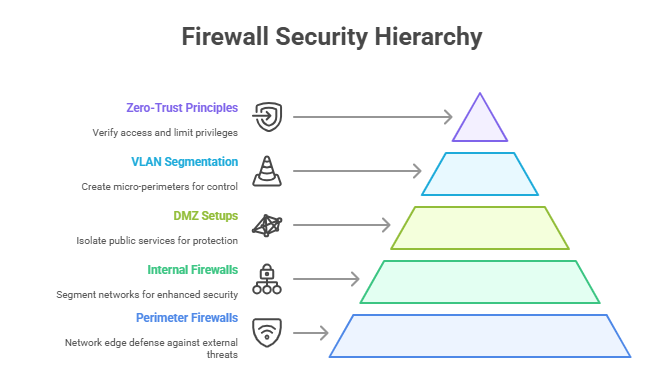
Perimeter vs. Internal Configurations
A firewall’s effectiveness hinges on where and how it is deployed. Perimeter firewalls are positioned at the network edge, acting as the first barrier against untrusted traffic. They are essential for filtering malicious traffic, preventing external threats from reaching internal systems. However, relying solely on perimeter firewalls leaves internal segments vulnerable if attackers breach the outer defenses.
To counter this, internal firewalls segment the network into zones with specific security controls. For example, a firewall between user devices and sensitive systems like finance servers limits lateral movement if an endpoint is compromised. DMZ (demilitarized zone) configurations isolate publicly accessible services (such as web and mail servers) from critical backend resources, reducing exposure.
VLAN segmentation enhances security by dividing a physical network into logical subnetworks, with firewalls enforcing strict communication rules. This segmentation is critical for zero-trust architectures, where no device or user is trusted by default, and each access request must be verified. Adopting a least privilege model limits permissions to only what is necessary for each role, dramatically shrinking the attack surface.
These layered configurations—combining perimeter and internal controls, DMZ setups, VLAN segmentation, and zero-trust enforcement—create robust security frameworks capable of containing sophisticated attacks.
Best Practices for Secure Firewall Setup
Even the most advanced firewalls can be rendered ineffective by misconfigurations or poor maintenance. Avoid overly permissive rules that inadvertently allow unwanted traffic. Conduct regular updates to patch vulnerabilities and keep firewall firmware current. Enforce strict access control policies to limit who can modify firewall settings, and use multi-factor authentication for administrative access.
Firewalls should be integrated with SIEM platforms to provide real-time logging and correlation of security events, enabling rapid response to suspicious activity. Regular penetration testing and configuration audits are crucial to identify and rectify weaknesses.
Operational efficiency is key. Overly restrictive configurations can impede business processes, so balancing security with usability is essential. Consider automated rule tuning and cloud-native firewall management tools like AWS WAF and Azure Firewall to maintain consistency across hybrid infrastructures.
Firewalls must be constantly monitored and tuned to adapt to evolving threats. Proper placement, segmentation, and strict policy enforcement form the backbone of a resilient network security architecture.
Advanced Security Integrations
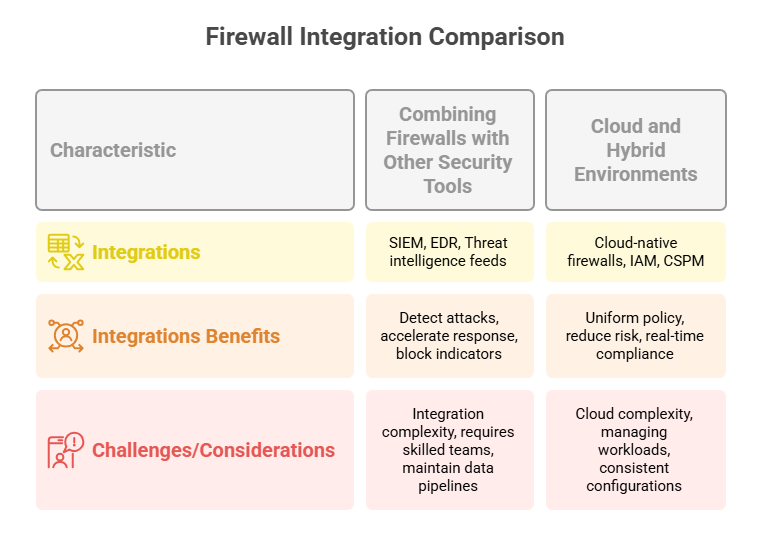
Combining Firewalls with Other Security Tools
Firewalls alone cannot secure a network. Integrating them with other advanced security solutions forms a defense-in-depth strategy. SIEM (Security Information and Event Management) platforms aggregate logs from firewalls and correlate them with data from intrusion detection systems (IDS), endpoint detection and response (EDR) tools, and network monitoring solutions. This comprehensive view allows security teams to identify complex attack patterns that isolated tools might miss.
EDR solutions complement firewalls by monitoring endpoint behavior, detecting anomalies, and enabling rapid containment of compromised systems. When combined with firewall logs, EDR tools provide critical context to validate alerts and prioritize incident response. Threat intelligence platforms further enhance this integration by supplying up-to-date indicators of compromise (IOCs), helping firewalls block known malicious IP addresses, domains, or signatures in real time.
Automated workflows between firewalls and these tools can reduce response times and mitigate damage during an attack. This integration is not optional for organizations facing sophisticated, multi-vector threats—it’s essential for maintaining resilience.
Cloud and Hybrid Environments
Traditional firewall configurations often fail to address the complexities of cloud and hybrid environments. Organizations leveraging AWS, Azure, or Google Cloud need scalable firewall solutions that integrate seamlessly with cloud-native controls. Cloud firewalls, such as AWS WAF or Azure Firewall, offer deep packet inspection, application-layer filtering, and integration with cloud-native IAM (Identity and Access Management) systems.
Hybrid environments, where workloads span on-premises data centers and cloud platforms, demand consistent security policies. Centralized firewall management platforms enable uniform rule enforcement and visibility across disparate systems. Microsegmentation techniques further enhance security by isolating workloads and controlling lateral movement within the cloud.
Dynamic environments require firewalls that can adapt to elastic workloads, automated scaling, and continuous delivery pipelines. Integrating firewalls with cloud security posture management (CSPM) tools helps maintain compliance and identify misconfigurations in real time. This approach ensures security scales with infrastructure and adapts to evolving business needs.
Real-World Case Studies
Enterprise Firewall Failures and Lessons Learned
Misconfigurations in firewall setups have led to some of the most devastating breaches in cybersecurity history. In one case, a financial services firm left an unused firewall port open, allowing attackers to exfiltrate sensitive data undetected for months. The breach resulted in millions of dollars in fines and irrevocable damage to customer trust. Another notable incident involved an e-commerce platform whose poorly segmented network enabled malware to spread laterally, bypassing perimeter firewalls and compromising critical systems.
Inadequate logging and monitoring contributed to these breaches, as alerts were either ignored or not configured to trigger for unusual patterns. These failures highlight the importance of comprehensive configuration reviews, robust change management processes, and active monitoring tools integrated with firewall solutions. Regular testing and validation of firewall rules and segmentation strategies are non-negotiable.
Success Stories from Industry Leaders
Leading organizations have demonstrated how proactive firewall strategies can prevent cyber breaches and enhance resilience. A global manufacturing company implemented a multi-layered firewall architecture combining perimeter, internal, and cloud-native firewalls to protect critical intellectual property. This setup, combined with zero-trust principles and continuous monitoring, successfully detected and contained multiple attempted intrusions without operational disruption.
A healthcare provider leveraged an integrated firewall and EDR solution, enabling rapid containment of a targeted ransomware attack. Real-time correlation of firewall logs with endpoint telemetry allowed for swift isolation of affected systems, minimizing data loss and maintaining regulatory compliance. These successes underscore the value of well-configured, adaptive firewall defenses that align with operational requirements and evolving threats.
| Which firewall type do you think offers the best balance between security and usability? | |
|---|---|
| Packet-Filtering Firewall | |
| Stateful Inspection Firewall | |
| Next-Generation Firewall (NGFW) | |
What ACSMI’s Cybersecurity Training Teaches About Modern Firewall Architecture
Why Firewall Mastery Matters
Understanding firewall configurations is essential for maintaining a robust cybersecurity posture. Firewalls form the foundation of a layered defense strategy, but their effectiveness depends on proper deployment, meticulous configuration, and continuous monitoring. Without these, even the most sophisticated systems can be rendered useless, leaving networks vulnerable to data breaches, malware infiltration, and compliance failures.
In today’s dynamic threat landscape, organizations must leverage advanced firewall capabilities to defend against multi-vector attacks, including zero-day exploits and ransomware. A solid grasp of firewall principles—ranging from packet-filtering basics to next-generation technologies—equips cybersecurity professionals to design and manage resilient defenses. Mastery in this area is not optional for those aiming to lead in the field of cybersecurity.
How ACSMI’s Program Equips You
ACSMI’s Advanced Cybersecurity & Management Certification is meticulously designed to provide hands-on training in firewall deployment and management. The curriculum covers real-world scenarios, from configuring perimeter and internal firewalls to integrating firewalls with cloud-native environments and other security platforms. Participants gain practical skills in firewall rule creation, segmentation strategies, and continuous monitoring, all aligned with zero-trust and compliance frameworks.
The program also provides access to live labs and expert mentoring, ensuring participants not only understand firewall theory but also develop the ability to implement configurations that mitigate real-world risks. Graduates of the program emerge with the confidence and competence to lead firewall deployments, manage adaptive security architectures, and contribute effectively to their organization’s resilience against cyber threats.
Final Thoughts
Firewalls are not just perimeter barriers—they are the cornerstone of comprehensive cybersecurity strategies. In a world where advanced persistent threats, ransomware, and zero-day exploits constantly evolve, understanding the nuances of firewall types and configurations is no longer optional. Professionals who master these skills can design robust defenses that protect critical assets and maintain operational continuity under pressure.
ACSMI’s Advanced Cybersecurity & Management Certification offers more than theory. It provides hands-on, practical training in configuring, managing, and optimizing firewall architectures, empowering participants to anticipate and mitigate real-world threats. By integrating firewalls with other security solutions, applying zero-trust principles, and mastering cloud-native environments, graduates of the program emerge as indispensable assets to any cybersecurity team.
Frequently Asked Questions
-
Packet-filtering firewalls inspect each packet’s header for IP addresses, ports, and protocols without context, making them efficient but prone to spoofing. Stateful firewalls, in contrast, track the entire session’s state and flow, building a table of legitimate connections. This enables stateful firewalls to detect anomalies like sequence mismatches or unexpected packet flows, blocking suspicious traffic effectively. Stateful inspection provides greater security for dynamic environments, reducing risks of session hijacking or spoofing. Packet-filtering firewalls, though lightweight, are best suited for simple, low-risk environments, while stateful inspection firewalls are essential for modern, layered security architectures.
-
NGFWs combine deep packet inspection (DPI), intrusion prevention systems (IPS), and application-level controls to provide granular security. Unlike traditional firewalls, NGFWs analyze entire packet content, identify malicious payloads, and apply adaptive policies. Integration with threat intelligence feeds and automated responses enables real-time mitigation of emerging threats like zero-day exploits and ransomware. NGFWs also enforce identity-based access, considering user and device context. This layered approach ensures that NGFWs can block sophisticated, multi-vector attacks that traditional methods might miss. NGFWs are indispensable for modern organizations handling sensitive data and critical infrastructures.
-
VLAN segmentation divides a network into logical subnets, isolating sensitive systems and limiting lateral movement. Firewalls enforce rules between these segments, creating micro-perimeters that reduce the attack surface. If a breach occurs, segmentation helps contain the threat to a specific VLAN, minimizing potential damage. VLANs are essential for zero-trust environments, ensuring that no internal system can be accessed without explicit authorization. Properly segmented networks also simplify compliance by aligning with data protection requirements. When combined with firewalls, VLAN segmentation provides granular control over traffic flow, bolstering overall security.
-
Firewalls generate detailed logs of network activity, but analyzing these logs in isolation limits visibility. Integrating with SIEM platforms allows logs to be aggregated, correlated, and analyzed alongside data from other sources like intrusion detection systems and endpoints. EDR solutions add context by monitoring endpoint behaviors and detecting anomalies. When SIEM and EDR tools work with firewalls, they create a comprehensive threat detection system. Automated workflows can isolate affected systems and adjust firewall rules in real time. This integration shortens response times, improves detection rates, and strengthens overall security posture.
-
Cloud and hybrid environments introduce dynamic network architectures with elastic scaling and distributed workloads. Traditional firewalls are often insufficient in these setups. Cloud-native firewalls like AWS WAF and Azure Firewall integrate with platform-specific controls and Identity and Access Management (IAM) systems. They enforce consistent policies across hybrid infrastructures and provide application-layer filtering. Additionally, microsegmentation techniques isolate workloads, minimizing lateral movement. Maintaining real-time visibility and adjusting firewall rules in response to changing workloads ensures security scales with business needs. Effective firewall configuration in these environments is critical for safeguarding data and ensuring compliance.
-
Common misconfigurations include overly permissive rules, outdated firmware, and inadequate logging. These errors create exploitable gaps in defenses, allowing unauthorized access or undetected malware infiltration. To avoid them, organizations should enforce strict change management, apply regular updates, and use multi-factor authentication for firewall administration. Firewall configurations should be reviewed regularly, ideally with penetration testing and automated configuration audits to identify vulnerabilities. Integration with SIEM systems ensures real-time alerting for unauthorized changes. Meticulous configuration, coupled with continuous monitoring, is essential for maintaining an effective firewall.