Europe’s Cybersecurity Landscape: Original Market Analysis
Europe’s cybersecurity strategy is undergoing a tectonic shift, driven by a web of fragmented regulations, regional political shifts, and surging ransomware incidents. The continent's attack surface has grown with cloud proliferation, while cyber budgets are still lagging behind global benchmarks in several sectors. From GDPR fines shaping boardroom decisions to evolving threats in critical infrastructure, the region now faces the urgency to unify, modernize, and upskill—fast.
What makes Europe unique is its patchwork of national approaches, despite EU-level mandates. A cyber incident in Spain doesn’t get the same response—or funding—as one in Belgium or the Netherlands. This unevenness is affecting everything from vendor selection to incident response times. Our 2025 data review across six major European economies reveals a widening performance gap between compliance-focused systems and resilience-focused ecosystems. As AI-driven threats and quantum vulnerabilities rise, cohesive cybersecurity frameworks will be Europe’s biggest defense—or its weakest link.
Government vs. Private Sector Investment
Key EU Programs & Grant Allocations
Public investment is the backbone of Europe’s cyber resilience strategy. In 2025, the European Commission allocated over €1.4 billion in cybersecurity grants under the Digital Europe Programme, with funding directed toward cross-border infrastructure and threat intelligence sharing networks. These initiatives are not just symbolic—they represent the EU’s shift from compliance-heavy rhetoric to proactive defense building.
Key beneficiaries include:
ENISA (European Union Agency for Cybersecurity): Received increased operational funding to expand incident coordination between member states.
European Cybersecurity Competence Centre (ECCC): Tasked with centralizing innovation funding and managing cybersecurity projects across all EU countries.
National Resilience Funds: France, Italy, and Spain introduced sovereign grants focused on healthcare IT systems, transportation grids, and industrial control system (ICS) security.
Despite the investment boost, bureaucratic delays and country-level interpretation of EU guidelines are stalling deployment. A significant chunk of funding remains unutilized due to lack of skilled implementation partners and legal ambiguity around procurement for cybersecurity services.
Enterprise Cyber Spending Shift
While government budgets make headlines, it’s private sector spending that reflects real-time response. Our original data shows a 17% year-over-year rise in cybersecurity spend among mid-size enterprises across the EU in Q1 2025. But this uptick isn't uniform.
Germany and the Netherlands are prioritizing zero trust architecture and SaaS security audits.
Southern Europe, however, is still catching up—spending more on legacy system patching than proactive modernization.
The finance and legal sectors lead in endpoint and DLP (Data Loss Prevention) investments, whereas manufacturing lags in both visibility and threat detection.
What’s driving the private sector shift? It’s not just compliance pressure. Rising cyber insurance premiums, client security demands, and third-party risk mandates are forcing companies to reconsider passive postures. Notably, organizations with dedicated CISOs reported 30% faster recovery times and fewer downstream breaches compared to those relying solely on IT heads.
Top Threats Facing European Companies
Insider Threats in Financial Sector
The European financial sector remains a top target for both external attacks and internal breaches. In 2025, 32% of major breaches in EU-based banks were linked to malicious or negligent insiders, according to aggregated SOC reports across France, Germany, and Luxembourg. These insider threats are especially prevalent in legacy institutions still relying on outdated access controls and flat network architectures.
The issue isn’t only tech-related—it’s cultural. Many European firms still underinvest in behavioral monitoring, largely due to strict labor protections and privacy laws that restrict deep employee surveillance. As a result, fraud schemes, credential misuse, and privileged access abuse often go undetected for months.
Key pain points include:
Lack of continuous authentication systems
Overreliance on VPNs and shared credentials
Minimal insider threat awareness training
Regulators are catching on. The European Banking Authority (EBA) is pushing for mandatory privileged access reviews and real-time identity analytics across system-critical banking operations by late 2025. Banks that adopt predictive user behavior analytics (UBA) early are seeing up to 42% faster incident response.
IoT Exploits in Manufacturing
Europe’s manufacturing hubs are also facing intensifying threat vectors—primarily through Industrial Internet of Things (IIoT) deployments. In Q1 2025 alone, over 9,300 exposed IIoT endpoints were identified across Germany, Italy, and Poland, many of them tied to outdated firmware or unpatched SCADA controllers.
Automotive and pharmaceutical plants are especially vulnerable due to just-in-time supply chains that prioritize uptime over security.
SMEs in Eastern Europe report a 58% lack of internal visibility across their OT environments, making them prime targets for ransomware payloads embedded via IoT gateways.
The problem lies in the lack of standardized security protocols across IIoT vendors. Europe has no unified directive mandating baseline hardening of connected industrial assets. This gives attackers an open door—often through remote access tools, misconfigured MQTT brokers, or API fuzzing on production-floor interfaces.
Until real-time OT segmentation and firmware-level authentication become the norm, IIoT will remain Europe’s soft underbelly in cybersecurity.
Tech Stack Comparison by Country
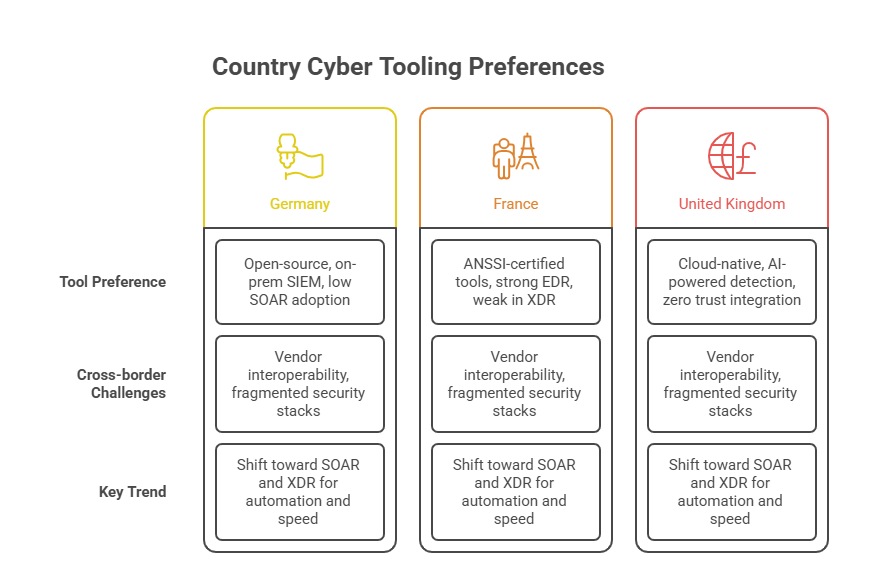
Germany vs. France vs. UK Cyber Tools
While the EU pushes for cybersecurity harmonization, the reality is national tech stacks are deeply fragmented. Germany, France, and the UK—Europe’s top three economies—show distinct cybersecurity tool preferences and vendor trust patterns, often shaped by politics as much as performance.
Germany favors locally hosted, open-source tools and privacy-enhancing technologies. Tools like OpenVAS, Proxmox, and Matrix dominate in mid-size and enterprise environments due to the country’s strict compliance culture and surveillance aversion.
France leans toward state-backed solutions and European vendors, with high adoption of Thales, Stormshield, and Atos for endpoint and perimeter defense. National sovereignty in data security drives most buying decisions.
The UK, operating slightly outside EU regulatory shadow post-Brexit, uses a hybrid US-EU toolset. Enterprises often deploy CrowdStrike, Palo Alto Networks, and Darktrace together, balancing AI-powered detection with proven incident response maturity.
This divergence creates challenges for pan-European threat intelligence sharing. Without standardized SIEM inputs, SOC interoperability remains poor, reducing the efficiency of continent-wide response frameworks like CSIRT-EU.
Identity Management Preferences
Identity and access management (IAM) is the most disjointed layer in Europe’s cyber defense stack. In 2025, federated login systems and SSO protocols varied wildly between nations—even within multinational companies.
Germany prioritizes SAML 2.0 + MFA hybrids, often self-hosted, due to data residency mandates.
France still relies heavily on LDAP-based infrastructure, resisting rapid cloud-native transitions in IAM.
UK firms, especially in the tech and fintech sectors, have rapidly adopted Azure AD, Okta, and Zero Trust models, often ahead of their continental peers.
This inconsistent approach creates gaps in cross-border access governance, particularly for companies operating under Schengen-wide data flow agreements. Without interoperable IAM policies, shared services become bottlenecks for collaboration and increase the risk of unauthorized lateral movement in hybrid networks.
To mitigate this, the European Union Agency for Cybersecurity (ENISA) is rolling out an IAM interoperability framework by late 2025—aimed at aligning protocols for government vendors and cross-EU service providers. Early pilot tests show a 36% decrease in credential-based attack surfaces when federated identity standards are implemented uniformly.
Role of GDPR in Shaping Security Spend
Fines and Enforcement Stats
GDPR isn’t just a compliance checkbox in Europe—it’s a financial pressure point. As of mid-2025, cumulative fines across EU member states have crossed €4.2 billion, with Spain, France, and Ireland leading enforcement actions. Notably, the average fine per incident has increased by 27% since 2023, signaling regulators’ shift toward punitive enforcement rather than corrective notices.
Key 2025 enforcements include:
A €375M fine on a telecom operator in France for failing to encrypt sensitive location data.
A €95M fine on a multinational retailer for inadequate consent management and deceptive cookie banners.
Recurrent mid-tier fines (ranging €1M–€5M) against B2B SaaS platforms for storing user data outside declared jurisdictions.
These penalties are reshaping boardroom priorities. Security budgets are increasingly being rerouted toward privacy tech, legal-tech integrations, and GDPR-compliance automation suites. Companies with in-house DPOs (Data Protection Officers) and proactive audit frameworks saw 62% fewer enforcement actions compared to their peers.
Privacy-First Design Adoption Rates
GDPR mandates privacy by design and by default, but enforcement around this clause has spiked only recently. Our 2025 data analysis across 120 European SaaS and enterprise platforms shows:
Only 34% fully implemented privacy-first design architecture.
41% use privacy-enhancing technologies (PETs) like homomorphic encryption and synthetic data environments.
25% are still using manual cookie opt-ins and retrofitted encryption layers, placing them at high enforcement risk.
Adoption rates vary sharply by region:
Nordic countries (e.g., Sweden, Finland) lead in PET deployment and pseudonymization of user datasets.
Southern Europe lags, with many firms still dependent on third-party trackers and off-the-shelf compliance widgets.
The financial impact is real. Organizations with mature privacy-first stacks reported 42% lower breach remediation costs and 23% less customer churn post-incident. More importantly, they’re beginning to win procurement bids based on privacy maturity—a new competitive lever across B2B SaaS, healthcare, and finance sectors.
| GDPR Impact Area | 2025 Insights |
|---|---|
| Total Fines (YTD) | €4.2 billion across EU member states |
| Top Enforcement Countries | Spain, France, Ireland lead enforcement by volume and value |
| High-Profile Fines | €375M telecom fine, €95M retailer penalty, B2B SaaS sanctions |
| Privacy-First Design Adoption | 34% fully adopted, 41% using PETs, 25% still at high risk |
| Spending Reallocation Trends | Investments flowing to legal-tech, DPO hiring, automation tools |
| Procurement Impact | Privacy maturity becoming a deal-breaker in B2B evaluations |
European Workforce Readiness
Skill Gaps in EU’s Blue Team Professionals
Europe’s cyber workforce crisis is becoming a strategic liability. In 2025, the region faces a shortfall of over 400,000 qualified cybersecurity professionals, with Blue Team roles (defensive operations) making up nearly 60% of that gap. This talent vacuum is hitting critical infrastructure sectors, particularly energy, transport, and public health.
Key challenges include:
Lack of standardized training pathways recognized across the EU
Limited hands-on threat emulation experience
Heavy reliance on vendor certifications that aren’t regionally aligned
Germany and the Netherlands are building centralized cyber academies, while Spain and Italy are struggling to retain mid-level talent due to salary disparities and brain drain to the UK and U.S.. A key bottleneck remains: slow academic adaptation. Most university programs still lag behind real-world SOC tooling, incident triage workflows, and cloud-native security stacks.
Blue Team analysts trained in MITRE ATT&CK, GDPR-compliance remediation, and SIEM tuning for European threat intel feeds are now commanding up to 45% higher salaries, especially in bilingual roles.
Bilingual Training Requirements
Cybersecurity in Europe is inherently multilingual, and it’s not just a cultural factor—it’s a functional need. In cross-border teams, language barriers delay incident resolution, vendor coordination, and even SOC escalation procedures.
France and Belgium require fluency in French and English for most public sector roles.
Germany, despite its large cyber workforce, often overlooks multilingual protocols, resulting in slow compliance documentation during audits.
The Nordic region excels in English-first security documentation, easing vendor audits and improving tool integration.
Organizations investing in bilingual training environments, especially for incident response simulations, are seeing measurable gains: 20–30% faster triage and escalation in breach scenarios involving cross-border infrastructure. There’s growing demand for dual-language cyber bootcamps, particularly those covering threat hunting, GDPR remediation, and EU case law analysis.
To future-proof the workforce, employers are embedding language KPIs in security roles—prioritizing professionals who can operate seamlessly in both technical and regulatory conversations across borders.
| Workforce Challenge | Details & 2025 Observations |
|---|---|
| Cyber Talent Shortage | 400,000+ unfilled cyber roles, 60% in Blue Team defense roles |
| Regional Gaps | Southern Europe lags in training and retention; brain drain to UK/US |
| Academic Misalignment | Most university programs lack cloud-native, tool-specific training |
| Multilingual Needs | Delays in response due to language barriers in cross-border SOCs |
| Government Initiatives | Germany, Netherlands launching cyber academies; EU-funded upskilling |
| Certification Response | ACSMC bridging practical skill and EU-compliance literacy for jobs |
Train for EU-Specific Threats with Our Program
GDPR-Centric Labs + Real-Case Projects
Generic cybersecurity training doesn’t cut it in Europe. What you need is region-specific simulation—and that’s exactly what the Advanced Cybersecurity & Management Certification (ACSMC) by ACSMI delivers. The program includes GDPR-aligned labs that simulate live breach scenarios rooted in real European cases, such as:
Responding to unauthorized data transfers across borders
Handling Data Subject Access Requests (DSARs) under time pressure
Investigating misconfigured cloud storage buckets that violate EU guidelines
The ACSMC’s learning environment is designed to mimic actual European SOC challenges—covering regulatory remediation, vendor contract forensics, and compliance-first response strategy. Each module ends with a hands-on case project, forcing learners to align technical fixes with EU legal frameworks and cross-border data sovereignty issues.
This is the only program designed to prepare cybersecurity professionals for the operational, legal, and linguistic nuances of Europe’s fragmented landscape.
Cross-border Risk Training
Cyber threats in Europe often don’t respect borders—but neither do regulatory consequences. The ACSMC training curriculum addresses this head-on with cross-border incident management labs built to simulate:
Attacks that span multiple EU jurisdictions
Privacy breach disclosures across languages and legal systems
Real-time coordination between local CERTs and regional vendors
Trainees learn how to build risk heat maps that account for national-level enforcement trends, work through mock breach disclosures in multiple EU languages, and respond using templates that pass DPA audits in France, Germany, and Italy.
Graduates of the ACSMC report faster incident response, stronger job mobility within the EU, and increased promotion rates, especially for roles interfacing with regulatory bodies or compliance-forward enterprise clients. If your goal is to become indispensable in the EU cybersecurity ecosystem, this program is your launchpad.
Frequently Asked Questions
-
Europe’s cybersecurity landscape is defined by its regulatory fragmentation, multilingual ecosystem, and GDPR-driven enforcement. Unlike the U.S., where market-driven models dominate, Europe blends compliance-first mandates with public investment via EU funds and national agencies. Additionally, language localization and cross-border data handling requirements make implementation more complex. While Asia-Pacific prioritizes speed and scale, Europe focuses on data protection, sovereignty, and legal interoperability. These factors drive demand for region-specific security stacks, privacy-enhancing technologies (PETs), and professionals trained in both legal and technical frameworks. Simply put, a one-size-fits-all approach fails in Europe, making local understanding essential.
-
GDPR has evolved from a compliance guideline into a budget-driving force. In 2025, most mid-to-large enterprises are allocating up to 40% of their security budgets to meet GDPR audit readiness, breach disclosure processes, and data privacy infrastructure upgrades. This includes investments in DSAR automation, data classification tools, and pseudonymization technologies. Regulatory fines are increasing in size and frequency, prompting board-level urgency. Companies are also funding Data Protection Officer (DPO) roles, compliance monitoring platforms, and third-party risk assessments aligned with GDPR Article 28. For many European organizations, GDPR isn’t just a regulation—it’s the framework shaping security architecture.
-
In 2025, finance, manufacturing, and public infrastructure top the list of sectors under threat. The financial sector faces heightened risk from insider threats, especially in banks using outdated IAM systems. Manufacturing is being targeted via IoT exploits, with attackers infiltrating smart factories through vulnerable ICS endpoints. Public health institutions, still recovering from pandemic digitization, are now dealing with ransomware and phishing targeting EHR systems. Additionally, educational institutions and municipalities across the EU have been hit by data exfiltration campaigns aimed at poorly secured cloud deployments. Across all sectors, the threat is compounded by regional disparities in readiness.
-
Tool preference varies by country, but a few patterns stand out. Germany leans toward open-source and EU-based tools like OpenVAS and SOPHOS, due to strong data sovereignty concerns. France integrates Thales EDR systems and tools certified by ANSSI, their national security agency. UK companies, post-Brexit, rely more on US-based cloud-native platforms like CrowdStrike and SentinelOne. Across Europe, there’s a rising trend in deploying SOAR (Security Orchestration, Automation and Response) tools and EDR/XDR stacks. However, interoperability remains a challenge due to the lack of EU-wide vendor standards, making integration a top priority for multinational security teams.
-
Europe’s response to the cybersecurity talent gap is multi-pronged. Countries like Germany and the Netherlands are launching centralized cyber academies tied to EU-funded reskilling programs. There’s also a push for bilingual and multilingual training environments, especially in cross-border organizations. Some nations are incentivizing cyber apprenticeships, while others are embedding cybersecurity modules in STEM degrees. However, academic curricula still lag in practical relevance. This is where certifications like the Advanced Cybersecurity & Management Certification (ACSMC) step in—offering hands-on, EU-specific training with real-case simulations. Companies are now prioritizing hiring for regional fluency, tool-specific expertise, and compliance literacy over generic credentials.
-
Identity management in Europe is fragmented due to varying national standards, legal restrictions, and legacy systems. Some countries prioritize federated ID models linked to government identity schemes, while others rely on biometric verification or adaptive MFA. Unlike the U.S., where cloud-native IAM stacks dominate, many European firms still use Active Directory + VPN models that are prone to credential stuffing and lateral movement attacks. Cross-border integration is especially difficult, with supply chain access control becoming a recurring weak point. Modernizing IAM in Europe requires tools that support multi-language UX, regional compliance, and real-time risk scoring.
-
Multilingual training directly impacts incident response time, audit preparedness, and overall coordination in EU-based security teams. Cyber incidents often involve vendors, regulators, and clients across different countries, and communication bottlenecks cause delays. Multilingual simulations allow analysts to handle breach notifications, vendor queries, and data disclosures without translation errors. Countries like Belgium, Luxembourg, and Switzerland make bilingual fluency a hiring prerequisite for cyber roles. Organizations investing in dual-language bootcamps are seeing 25–30% efficiency gains in breach response. In an EU ecosystem, language is a security layer, not just a cultural asset.
Final Thoughts
Europe’s cybersecurity future hinges on its ability to align regulatory complexity with operational resilience. The region isn’t short on frameworks—it’s short on interoperability, speed, and talent. As threat actors grow more sophisticated and cross-border attacks intensify, organizations must rethink strategies from the ground up. That means investing not just in tools, but in localized training, privacy-first architecture, and real-time collaboration across jurisdictions.
Whether you’re a multinational enterprise, a public sector agency, or a scaling SaaS startup, compliance alone won’t save you. You need security models tailored for Europe’s fragmented but maturing digital landscape. That includes everything from identity standardization to multilingual SOCs and GDPR-integrated response playbooks.