GDPR & Cybersecurity: Compliance Challenges & Best Practices
The General Data Protection Regulation (GDPR) is no longer just a European framework—it’s now a baseline global benchmark for privacy and cybersecurity. In 2025, organizations across finance, healthcare, cloud SaaS, and e-commerce must adapt to GDPR’s extraterritorial reach, especially as cross-border data transfer tools like SCCs and DPF evolve rapidly. Cybersecurity teams aren’t just fending off threats anymore—they’re expected to build data protection into architecture from day one.
This guide explores what went wrong in 2024, why teams still stumble on basic GDPR principles, and what new strategies—from AI for risk mapping to smart consent audits—can future-proof cybersecurity frameworks. Whether you're a compliance lead, security engineer, or data protection officer, this is your 2025 roadmap to GDPR resilience.
The Core of GDPR and How It Affects Cybersecurity
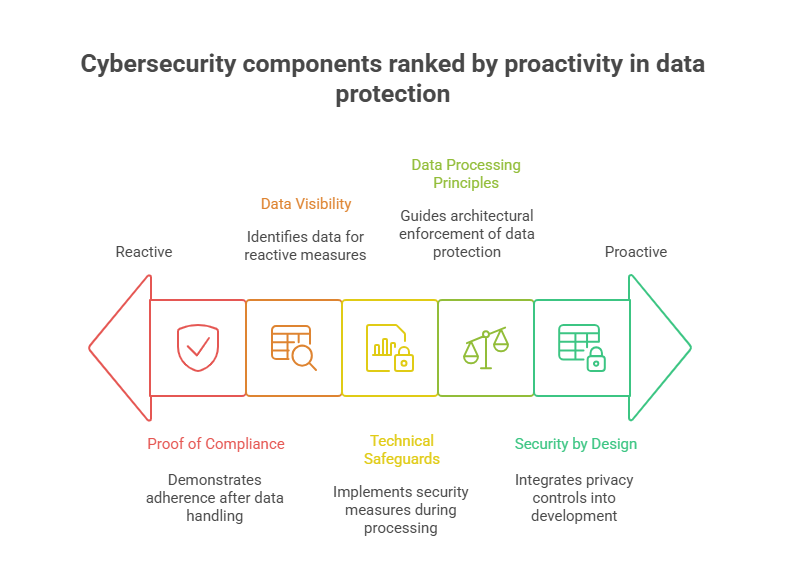
Data Processing Principles
At the foundation of GDPR lie seven core principles of data processing, all of which demand technical enforcement, not just policy acknowledgment. Organizations must ensure lawfulness, fairness, and transparency, which means systems must log every data transaction and expose it on demand. This is not just a legal requirement—it’s a cybersecurity challenge. Without real-time visibility into data flows, unauthorized access, shadow IT, or accidental exposure becomes inevitable.
The principles of purpose limitation and data minimization push back hard against data hoarding, forcing security teams to implement automated purging protocols and granular access controls. Integrity and confidentiality—a GDPR principle in itself—requires end-to-end encryption, data tokenization, and multi-factor authentication (MFA) not just at the user level, but for every backend service touching personal data.
Organizations also struggle with accountability, which requires proving compliance at every step. Logs, reports, incident histories, and user consent flows must be preserved and auditable. Security isn’t just about breach prevention—under GDPR, it’s about demonstrating you tried.
Technical Safeguards Mandated
Under Articles 32–36 of the GDPR, controllers and processors must implement “appropriate technical and organizational measures” (TOMs) to ensure data security. But what’s considered “appropriate” has evolved dramatically in 2025.
Encryption in transit and at rest is no longer optional. It must be state-of-the-art and scalable across multi-cloud environments.
Zero trust architecture is now considered baseline in industries processing large volumes of personal or sensitive data.
Organizations are expected to deploy automated intrusion detection systems (IDS), vulnerability scans, and AI-powered anomaly detection to preemptively identify data leaks.
Pseudonymization is recommended, especially for analytics environments, to reduce the identifiability of subjects during processing.
Security by design and by default, required by GDPR Article 25, forces teams to build privacy into the development cycle. DevSecOps now mandates that security controls be embedded at every CI/CD pipeline stage, with version-controlled compliance tracking.
And perhaps the most overlooked: incident response testing. Regulators increasingly expect companies to run simulations, maintain breach impact documentation, and show they can notify authorities and users within the 72-hour breach notification window.
GDPR Breaches in 2024: What Went Wrong
Multi-Nation Breach Case Studies
2024 saw a sharp rise in cross-border GDPR enforcement, driven by violations in sectors like ad tech, AI analytics, and decentralized finance. The most impactful breaches revealed recurring blind spots:
A French AI SaaS firm was fined €38 million after failing to anonymize training datasets, exposing biometric data of EU citizens to U.S.-based third parties. Their mistake? Incomplete data mapping and no DPIA (Data Protection Impact Assessment) prior to model deployment.
A German logistics platform suffered a ransomware attack that leaked customer shipment and payment data. Investigations found their incident response plan was outdated, and they hadn’t patched known vulnerabilities for 67 days.
An Irish subsidiary of a U.S. conglomerate was penalized for non-compliant consent management—popups were deceptive, and no audit logs were maintained.
These aren’t anomalies. They're symptoms of a deeper issue: GDPR noncompliance is often baked into infrastructure choices, not just policy decisions. Teams neglect DPIAs, silo consent records, or treat DPOs as legal-only advisors, ignoring their cybersecurity role.
Enforcement Trends and Fines
The European Data Protection Board (EDPB) and national regulators are increasingly aligned in prioritizing security enforcement over mere procedural lapses. In 2024, total GDPR fines crossed €2.8 billion, with a notable pivot:
44% of major fines were tied directly to cybersecurity failings—not just misused data.
Fines are increasingly calculated based on incident impact scope, not just organizational revenue.
Regulators now expect evidence of technical controls, including encryption, access logging, and risk-based MFA. Absence of these basics now qualifies as gross negligence.
Several enforcements also called out third-party risk management failures. If a partner, vendor, or cloud provider causes a breach, the primary data controller still holds liability unless explicit technical safeguards and processor agreements are in place.
One standout case involved a fintech startup that used an offshore analytics provider without verifying their TOMs. When the provider’s S3 buckets were exposed, the startup faced a €6.5 million fine—despite having no direct hand in the breach.
In 2025, security leaders must treat GDPR as a technical and architectural obligation, not just a checkbox exercise. Because regulators already do.
| Case Study | Violation Type | Detailed Lesson Learned |
|---|---|---|
| French AI SaaS Firm | Non-anonymized training data exposed | Absence of proper data mapping and DPIAs led to exposure of biometric data. Regulators emphasized the importance of privacy-by-design in ML pipelines. |
| German Logistics Company | Outdated patching and breach protocols | Failure to patch known vulnerabilities for over 60 days resulted in ransomware exposure. Highlighted the need for continuous vulnerability management and real-time breach simulation. |
| Irish Subsidiary of U.S. Firm | Consent collection without versioned records | Regulators ruled that misleading UI consent design and lack of backend logging invalidated user agreement. Full audit trails now mandatory at the point of consent. |
| Fintech Vendor Breach | Third-party S3 bucket exposure | Primary data controller fined due to lack of oversight on offshore analytics partner. Stressed need for vendor TOM verification and shared incident protocols. |
| Regulatory Enforcement Shift | Fines tied to technical failure, not just data misuse | Over 40% of GDPR fines in 2024 were due to weak encryption, lack of access controls, and untested breach response plans—even when no intent to harm was proven. |
Biggest Pain Points for IT and Security Teams
Data Portability and Deletion
GDPR’s Right to Data Portability (Article 20) and Right to Erasure (Article 17) sound simple on paper—but in practice, they're operational nightmares for IT teams. Portability requires that personal data be exportable in a structured, machine-readable format. Yet most legacy systems store data across fragmented silos: flat files, nested databases, and proprietary APIs that don’t support seamless export.
Security teams are often left scrambling to build export functions manually, which increases the risk of data misclassification or over-disclosure. Worse, many organizations don’t know where personal data resides. Without a unified data inventory or live data mapping, erasure requests become guesswork—often missing redundant or backup systems entirely.
For deletion, merely “removing access” doesn’t count. You must prove data is completely destroyed, which includes cache layers, dev/test environments, CDNs, and offline backups. IT must balance this with legal holds and compliance with other data retention laws—a tightrope few teams walk well.
Modern approaches require:
Privacy-by-design architectures, where deletion triggers cascade through all connected systems
Auto-tagging of personal data, so teams don’t miss dependencies
Immutable audit trails of both portability and deletion actions
Failing to execute these rights correctly isn’t just a UX issue—it’s now a top reason for GDPR penalties.
Consent Logging and Audits
The Right to Consent under GDPR isn’t just about opt-ins—it’s about provability. Security and IT teams must implement backend systems that log each consent event, including what version of the policy was displayed, the timestamp, and the user’s IP or device signature.
But here’s the challenge: many platforms log consent at the UI layer, not at the database or server level. That means no centralized record exists when audits hit. Even worse, third-party plugins (like outdated CMPs) often store logs externally, without giving DPOs or engineers full access to audit trails.
Teams need to harden systems to:
Store consent logs locally, with tamper-proof hashing and indexing
Tie consent logs to specific policy versions, ensuring backward traceability
Use blockchain or distributed ledgers, where high-integrity logging is mandatory (finance, health tech)
In 2025, regulators aren’t just asking whether consent was given. They want to see when, where, under what conditions, and how that proof is stored. If your system can’t surface this instantly, you’re non-compliant.
Tools That Simplify GDPR Alignment
DLP, IAM, and Privacy Automation
GDPR alignment in 2025 isn’t possible without technical augmentation. Manual processes—spreadsheets, emailed checklists, and retroactive audits—don’t scale. Smart tooling is now essential to close compliance gaps before enforcement does.
Data Loss Prevention (DLP) systems are the first layer of defense. Modern DLP tools now integrate with email, cloud storage, messaging apps, and endpoints to:
Flag and quarantine PII exfiltration attempts
Monitor encrypted files and file renaming patterns
Auto-classify unstructured data using NLP and prebuilt GDPR classifiers
Then comes Identity and Access Management (IAM). With GDPR’s principle of least privilege, IAM tools enforce role-based access while logging every credential elevation and authentication handshake. The best platforms now offer adaptive access policies, factoring in risk scores based on geography, device, and login anomalies.
To eliminate manual log review, privacy automation platforms have emerged. These tools:
Run real-time compliance scoring
Manage data subject request (DSR) workflows
Auto-generate DPIAs with integrated risk scoring
Orchestrate deletion workflows across SaaS, cloud, and on-prem systems
Security leaders must ensure all these tools integrate with SIEMs and ticketing systems. Siloed privacy tools offer minimal protection if they don’t feed alerts into the broader cybersecurity ecosystem.
AI for Risk Mapping
The shift to AI-assisted compliance is no longer a future trend—it’s the current norm. AI-based risk mapping tools now ingest logs, consent data, access patterns, and even Slack messages to detect latent GDPR violations in real time.
These platforms:
Use machine learning models to spot over-retention of personal data
Auto-flag abnormal access to sensitive fields (e.g., HR files opened by non-HR users)
Build visual maps of cross-system data transfers, enabling faster DPIAs and impact predictions
Some also tie into NLP-based contract analysis tools, identifying third-party vendor risks by scanning DPA clauses, TOMs, and breach terms. This gives compliance teams a live vendor risk score, updated with breach feeds, audit logs, and processing volume shifts.
In short: AI doesn’t just assist GDPR compliance—it redefines it. It shifts compliance from reactive incident handling to proactive data governance, with precision at a scale that manual audits will never achieve.
| Tool Type | Core Functionality | Role in GDPR Compliance |
|---|---|---|
| Data Loss Prevention (DLP) | Scans and blocks unauthorized PII transfers across endpoints, email, SaaS | Protects data integrity and confidentiality, aligned with Article 32 on security of processing |
| Identity and Access Management (IAM) | Role-based access, MFA, conditional logic, and credential lifecycle tracking | Supports data minimization and ensures only authorized users access sensitive data |
| Privacy Automation Platforms | Manage data subject requests, DPIAs, retention rules, and compliance scoring | Enables continuous compliance and audit-readiness across complex data ecosystems |
| AI Risk Mapping Tools | Detect access anomalies, build real-time data flow maps, flag over-retention | Automates detection of GDPR violations and supports Article 35 DPIA execution |
| Contract Analysis Tools (NLP-powered) | Scans vendor contracts, DPAs, and TOM clauses for risk gaps | Ensures processor compliance and identifies third-party risks before onboarding |
Team Structures That Ensure GDPR Success
DPO Roles and Internal Collaboration
In 2025, Data Protection Officers (DPOs) cannot function as siloed legal advisors. They must be embedded in cross-functional teams and possess enough technical fluency to evaluate encryption models, understand incident forensics, and supervise vendor architecture decisions.
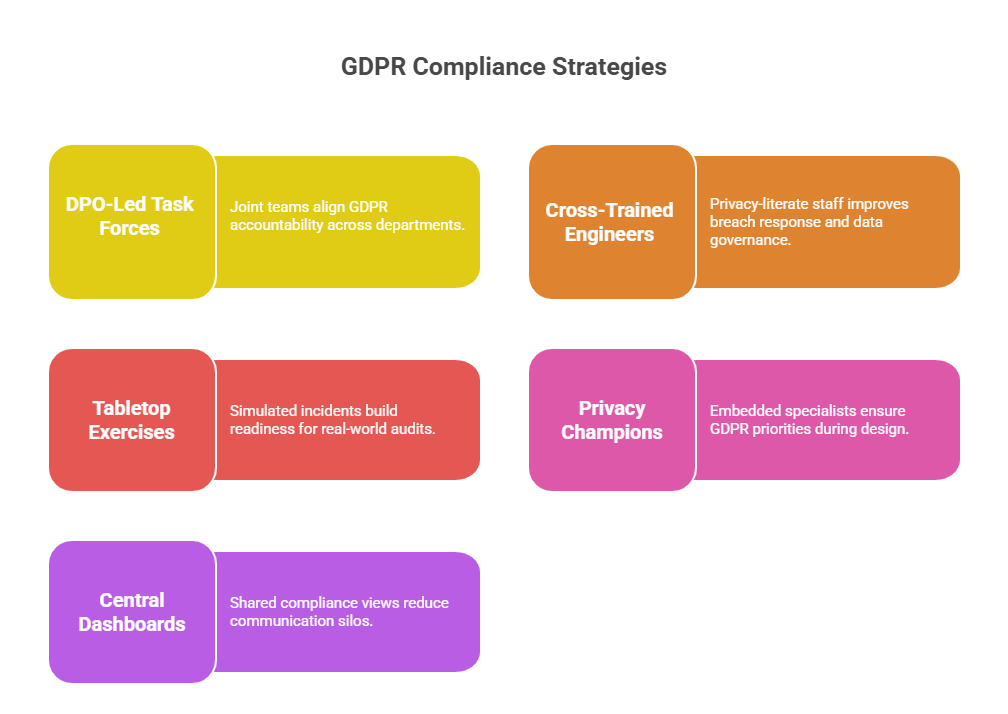
The most effective organizations elevate their DPOs to C-level status or direct board access, ensuring that GDPR isn’t treated as a compliance afterthought. But elevation alone isn’t enough. DPOs must be paired with security architects, legal analysts, and data engineers, forming unified GDPR task forces that operate with agility across departments.
For collaboration to work, organizations need:
Centralized compliance dashboards, visible to all stakeholders
Shared incident documentation templates and auto-routing for review
Joint sprint planning between DevOps and DPOs, ensuring privacy gets baked in before code goes live
Misalignment often stems from poor data ownership clarity. Who owns personal data in an internal CRM? Who owns deletion authority for archived employee files? These questions must be settled before a regulator asks—not after.
Cross-Training Cybersecurity Teams
GDPR success depends on whether security teams speak the language of compliance—and vice versa. In most breaches reviewed in 2024, the root cause wasn’t lack of tools—it was lack of shared understanding across functions.
Cross-training initiatives now include:
Mandatory GDPR modules for all cybersecurity engineers, including hands-on labs with mock DSRs and breach simulations
Legal training for SOC teams, helping them recognize what logs qualify as proof of consent, erasure, or data flow documentation
Monthly tabletop exercises, where cross-department groups handle simulated regulatory investigations or multi-jurisdiction breach notifications
Some organizations have gone further, embedding privacy champions into red and blue teams. These specialists act as GDPR enforcers during pen tests and post-incident reviews, flagging policy blind spots and legal misalignments.
The new rule is clear: GDPR cannot be enforced by one department alone. It must become a team sport, with every player understanding their role, from breach detection to regulator reporting.
How ACSMI’s Program Trains Teams for GDPR Readiness
GDPR-Focused Assessments
The Advanced Cybersecurity & Management Certification (ACSMC) is uniquely engineered to address GDPR’s toughest real-world demands. Rather than focusing on abstract policy theory, the program dives straight into functional privacy enforcement, with a curriculum built around the GDPR articles most scrutinized by regulators.
Key modules simulate real enterprise scenarios:
Live consent management exercises, where candidates configure logging systems to align with Article 7 requirements
Data minimization workflows, where students reduce PII exposure across CRM, HR, and analytics stacks
Breach notification simulations, practicing under 72-hour windows with forensic and legal documentation templates
Assessments don’t rely on multiple choice. Instead, ACSMC candidates undergo GDPR compliance scoring labs, where each step—whether configuring role-based access or auditing vendor DPAs—is scored against live enterprise benchmarks.
This makes graduates uniquely capable of bridging the compliance-engineering divide, a skill most teams lacked in 2024 breaches.
Labs on Real-World Breach Recovery
One of ACSMI’s most praised features is its interactive breach recovery training. Candidates walk through mock breach events with real artifacts: IDS logs, flawed TOMs, compromised credentials, and press release drafts. They must:
Run root cause analysis and trace breach vectors across on-prem and cloud
Draft regulatory notifications and internal incident summaries
Rebuild systems using GDPR-compliant architectures (zero trust, immutable logs, encryption-first recovery)
Each lab reinforces a specific GDPR clause—from Article 32 (security of processing) to Article 35 (DPIAs)—ensuring theoretical knowledge turns into deployable skill.
The certification also includes vendor audit simulations, where candidates assess hypothetical processors based on TOMs, DPA language, and breach history. This builds the capability to evaluate partners—before regulators or attackers do.
For CISOs, DPOs, and privacy engineers, ACSMI’s ACSMC program is one of the only certifications that trains for both strategic compliance and hands-on remediation, helping teams proactively defend against tomorrow’s GDPR violations.
Frequently Asked Questions
-
The most significant challenge is maintaining real-time visibility across hybrid infrastructures. In 2025, companies operate on multi-cloud, on-prem, and edge networks—creating fragmented data trails. GDPR requires instant access, correction, or deletion of personal data. Without automated data mapping, organizations struggle to locate data across microservices, containers, and legacy systems. Compliance isn’t just about encryption or firewalls anymore—it’s about knowing exactly where personal data lives and flows. Security teams must integrate data discovery tools, live DPIAs, and real-time access logs to meet regulatory expectations. Anything less is considered willful negligence in audits.
-
While the GDPR’s legal obligations apply universally, resource constraints make compliance harder for startups. Large enterprises can hire DPOs, privacy engineers, and legal counsel; small teams often delegate GDPR to a single IT or legal person. This leads to gaps in consent management, third-party processor oversight, and data minimization enforcement. However, enforcement authorities have increasingly fined startups—especially those in ad tech, SaaS, and mobile apps—for non-compliant tracking or weak breach notification protocols. Startups must adopt lightweight but powerful tools like privacy automation platforms, default encryption SDKs, and prebuilt audit templates to remain compliant without scaling their teams prematurely.
-
GDPR Article 32 mandates “appropriate technical and organizational measures” (TOMs), but the term evolves annually. In 2025, appropriate means minimum expected safeguards in your industry, not just good faith efforts. These include end-to-end encryption, role-based access control (RBAC), multi-factor authentication (MFA), data classification, automated DSR workflows, and SIEM-integrated breach monitoring. The term also implies continuous testing and updating—static security policies are non-compliant. Regulators consider TOMs context-specific, meaning a fintech app must adopt stronger safeguards than a basic newsletter site. The lack of periodic risk assessments, breach simulation drills, or secure-by-design infrastructure can disqualify TOMs as insufficient.
-
Organizations must report qualifying personal data breaches to their supervisory authority within 72 hours of becoming aware of the breach. This doesn’t mean 72 hours from the breach itself—it starts when the controller or processor discovers it. If the breach poses a high risk to data subjects, affected individuals must also be notified “without undue delay.” To meet this requirement, companies must establish incident detection pipelines, real-time alerts, and pre-written communication templates. Teams should also define what constitutes “awareness,” and log every step—because regulators will check timestamps. Delayed, vague, or incomplete reporting is now a leading cause of fines in breach cases.
-
Point-in-time audits aren’t enough. Regulators now expect a compliance lifecycle, which includes version-controlled privacy policies, audit-ready DSR logs, breach simulation results, and cross-system consent records. Organizations should implement compliance dashboards, with automatic scoring linked to risk assessments, retention periods, and policy enforcement logs. Periodic reviews, continuous DPIAs, and updated TOMs prove you're not treating GDPR as a one-time setup. Embedding privacy-by-design into DevOps cycles and maintaining immutable logs for all policy changes, access revocations, and processor onboarding further reinforce ongoing alignment. If you can’t show what changed—and when—you can’t prove you’re truly compliant.
-
No. AI systems often process large datasets with latent personal information, and most aren’t GDPR-compliant by default. If an AI model processes EU resident data, even indirectly, you must conduct a Data Protection Impact Assessment (DPIA). You also need to address the lawfulness of processing, especially if profiling is involved. Transparency requirements mean users must understand how their data is used in the AI’s logic. Data minimization, purpose limitation, and access control must be enforced at every layer—training, inference, and output. Organizations must also evaluate model explainability and audit trails, especially if AI-driven decisions affect individual rights.
-
In 2025, the Data Protection Officer (DPO) is no longer just a legal advisor—they’re a strategic function embedded in cybersecurity planning. DPOs must understand technical architectures, participate in vendor risk assessments, and co-lead breach response drills. They should coordinate with CISOs to evaluate TOMs and flag non-compliant processors. Their KPIs now include compliance automation rates, incident recovery timelines, and DSR fulfillment speeds. The most effective DPOs use centralized dashboards, integrate with DevSecOps teams, and champion privacy-by-design at the architectural level. Without a technically literate DPO, GDPR programs tend to devolve into reactive checklists—an approach regulators no longer accept.
Our Verdict
GDPR in 2025 is no longer just a legal framework—it’s a cybersecurity blueprint. With threat surfaces expanding through AI, remote work, and decentralized data flows, GDPR now acts as a minimum bar for security readiness. Teams that still treat it as paperwork or an annual review will continue to fall into the same traps that led to 2024’s most severe breaches.
What separates resilient organizations today is cross-functional execution. DPOs, CISOs, engineers, and legal teams must operate as one unit, armed with privacy-by-design tools, AI-driven compliance mapping, and breach simulation routines. The ACSMC program by ACSMI provides the exact training modern teams need to meet these challenges head-on—with real-world breach labs and actionable compliance scoring.
| Poll Question | |
|---|---|
| Question | What is your biggest GDPR compliance challenge in 2025? |
| Option A | Managing data subject requests (DSRs) efficiently |
| Option B | Ensuring vendor/third-party compliance |
| Option C | Real-time data visibility across systems |