NIST Cybersecurity Framework Adoption & Industry Analysis
The NIST Cybersecurity Framework (CSF) has evolved from a U.S.-centric guideline into a globally adopted blueprint for cyber defense. Originally published by the National Institute of Standards and Technology (NIST) to support critical infrastructure protection, it's now being integrated into cybersecurity programs across SMEs, multinationals, and regulated industries worldwide.
This report analyzes how industries are embracing CSF 2.0, which tools are driving adoption, and how certifications like ACSMI’s cybersecurity training are closing skills gaps. Expect real case studies, current adoption rates, and the challenges companies face when aligning with NIST’s latest update.
What’s New in NIST CSF 2.0
The release of NIST CSF 2.0 in 2024 introduced the most significant update since the framework’s inception. While the original version centered on voluntary adoption and general risk management, 2.0 reflects today’s complex cybersecurity landscape—from supply chain interdependencies to regulatory convergence and board-level accountability.
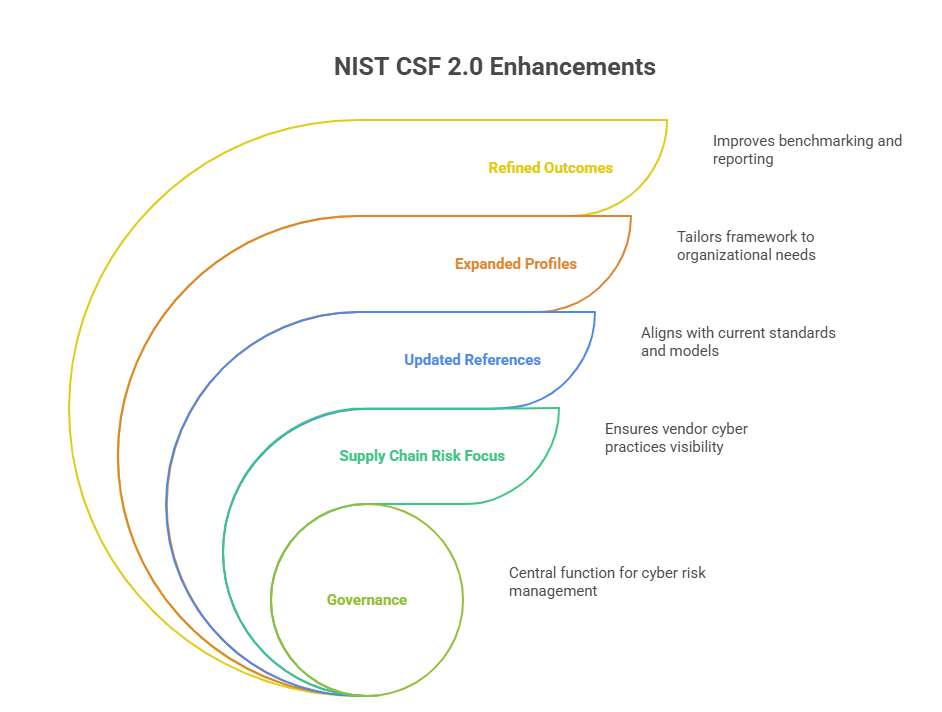
Framework 2.0 enhances the original five core functions (Identify, Protect, Detect, Respond, Recover) while introducing governance as a sixth function. This change acknowledges that cybersecurity is no longer solely an IT issue—it’s a business risk that must be governed at the highest levels. Organizations are now expected to formalize cybersecurity policies, assign accountability, and demonstrate oversight across digital risk programs.
Key Changes From 1.1
NIST CSF 2.0 makes several strategic updates:
Governance Function: The new core function (GV) elevates executive responsibility, linking cyber posture to enterprise risk tolerance.
Updated Informative References: Alignments now include ISO/IEC 27001:2022, CISA’s Zero Trust Maturity Model, and sector-specific resources.
Profile Guidance Expansion: Profile creation is now more nuanced, supporting customization by organization size, industry, and maturity level.
Improved Outcome Clarity: Each subcategory includes refined outcomes, allowing for more precise benchmarking and gap tracking.
The transition from 1.1 to 2.0 isn't merely iterative—it’s a structural shift that repositions cybersecurity as a continuous, leadership-driven process. Organizations that previously approached the framework as a checklist will need to reorient toward dynamic program development, backed by measurable governance.
New Focus Areas: Supply Chain, Governance
Two areas receiving intense focus in CSF 2.0 are supply chain risk management and organizational governance:
Supply Chain Integration: CSF 2.0 mandates visibility into third-party and fourth-party risks. This includes assessing vendor controls, contract clauses, and incident response coordination across partners.
Governance Maturity: 2.0 includes implementation examples that emphasize tone-from-the-top leadership, board reporting, and integration with enterprise risk management (ERM) systems.
These changes are a response to modern attack surfaces, where breaches increasingly occur via compromised vendors or misaligned leadership. By embedding governance and supply chain oversight into the core structure, NIST CSF 2.0 provides a modernized architecture for scalable cyber resilience—especially for healthcare, fintech, and critical infrastructure entities facing heightened scrutiny.
Industry Adoption Data
Adoption of NIST CSF 2.0 has rapidly expanded beyond its original U.S. critical infrastructure focus. In 2025, it’s serving as the de facto standard for cybersecurity alignment in sectors ranging from healthcare and energy to financial services and manufacturing. What’s notable is not just who is adopting—but how they’re interpreting and operationalizing it based on their size, risk profile, and regulatory exposure.
Adoption Rates Across Sectors
Industry-specific adoption patterns reveal distinct trends:
Healthcare: Over 68% of U.S. hospitals now integrate some or all elements of the NIST CSF, often in combination with HIPAA and HITECH requirements. Many are leveraging CSF profiles to drive audit readiness and insurance underwriting for cybersecurity risk.
Finance: The financial sector leads in maturity. Roughly 81% of U.S.-based financial institutions reported partial or full NIST CSF adoption in 2024, using it to map to FFIEC and SEC guidelines.
Energy & Utilities: With mounting regulatory mandates (e.g., FERC, NERC CIP), 75% of power and utility companies use CSF-aligned assessments to meet both resilience and reporting benchmarks.
Manufacturing: Around 57% of mid-to-large manufacturers have implemented CSF-aligned controls, often as part of ISO 27001-based programs or DoD supplier requirements (CMMC).
This cross-sector embrace reflects not just regulatory pressure—but the rising demand for interoperable security practices that unify fragmented compliance frameworks.
Small vs Enterprise-Level Usage
The gap between SME and enterprise adoption is narrowing. In 2023, only 29% of small businesses used NIST-aligned models. As of 2025, that figure has climbed to 42%, driven by easier tooling, insurer requirements, and turnkey templates.
Key contrasts:
Small Organizations often adopt CSF in lightweight form—focusing on the Identify and Protect functions—supported by managed service providers and off-the-shelf policy kits.
Enterprises, in contrast, use CSF to build internal control catalogs, align with GRC systems, and run full-lifecycle maturity assessments across business units.
What’s enabling this shift is the rise of framework accelerators—prebuilt mapping tools, auto-generated gap assessments, and role-based training programs (explored later)—that democratize access to cybersecurity governance.
As CSF 2.0 adoption rises across sectors and org sizes, the framework is increasingly seen not just as a security tool but as a trust signal for customers, investors, and regulators.
| Industry | CSF 2.0 Adoption Insight |
|---|---|
| Healthcare | Adoption exceeds 68% in 2025. Hospitals use CSF 2.0 to align with HIPAA and HITECH, boost cyber insurance eligibility, and build board-level cyber risk visibility through governance functions. |
| Finance | 81% of financial institutions report CSF-aligned architectures. Mapped to FFIEC, SOC2, and SEC cyber guidelines. Used to demonstrate executive oversight and meet banking partner security expectations. |
| Energy & Utilities | 75% adoption driven by FERC and NERC CIP mandates. CSF is used to baseline OT and IT asset risks, drive supply chain visibility, and meet national resilience benchmarks. |
| Manufacturing | 57% of mid-to-large manufacturers leverage CSF 2.0 to align with ISO 27001 and DoD’s CMMC. CSF’s outcome-based mapping helps suppliers retain federal contracts. |
| SMEs vs Enterprises | SMEs have reached 42% adoption due to low-code templates and MSP offerings. Enterprises exceed 90%, integrating CSF into GRC platforms and risk dashboards across global operations. |
Real Business Case Studies
While adoption statistics offer a macro lens, business case studies expose how the NIST Cybersecurity Framework 2.0 plays out in practice—especially in sectors where data sensitivity, operational uptime, and compliance obligations collide. The following examples spotlight CSF implementation across healthcare and fintech, where stakes are highest and margins for error smallest.
Healthcare Implementation
A mid-sized U.S. hospital group operating across four states adopted NIST CSF 2.0 after a ransomware event led to a week-long EHR outage. Post-incident reviews revealed fragmented policies and poor alignment with risk tolerance. The organization initiated a gap analysis using CSF core functions and discovered:
Incomplete asset inventories under the Identify function
Lack of segmented access controls under Protect
Absence of threat detection telemetry under Detect
To remediate, leadership created a CSF-aligned roadmap. They used outcome-based subcategories to prioritize tooling, training, and vendor oversight. Governance was formally embedded with a cyber risk committee reporting to the board. Within 14 months, the hospital moved from ad hoc controls to measurable cybersecurity maturity—evidenced by insurer discounts and reduced incident response times.
Fintech Implementation
A fast-scaling fintech firm managing API-based payment gateways used CSF 2.0 to establish regulatory resilience before undergoing PCI DSS and SOC 2 audits. Rather than adopting multiple frameworks independently, leadership mapped both standards into the CSF core—creating a unified control architecture across:
Governance (GV): Board risk oversight and SLA-tiered vendor requirements
Detect: Cloud-native SIEM deployment with automated anomaly scoring
Respond & Recover: Runbook creation tied to ransomware playbooks and breach disclosure laws
The firm’s use of the Governance function allowed them to demonstrate tone-from-the-top accountability, a key factor in winning early-stage banking partnerships. Within two quarters, the company reported a 36% faster audit cycle and secured a strategic investment from a major financial institution citing mature security governance.
These cases show that NIST CSF 2.0 is more than a framework—it's a practical blueprint for resilience, stakeholder assurance, and growth enablement, especially in high-risk, high-regulation verticals.
| Sector | Implementation Overview | Results Achieved |
|---|---|---|
| Healthcare | Mid-sized hospital group adopted CSF 2.0 post-ransomware attack. Used gap analysis across core functions and formalized board governance. Policies were mapped to outcome categories. | Achieved faster incident response, insurer premium discounts, and measurable control maturity across all five technical CSF functions plus governance. |
| Fintech | Startup scaled CSF 2.0 with PCI and SOC2 alignment. Used governance function for board oversight and Detect/Respond categories to implement SIEM and incident runbooks. | Completed audit cycles 36% faster. Secured enterprise funding after demonstrating governance maturity and risk transparency via CSF metrics. |
| Cross-Sector Takeaways | CSF 2.0 enables unified cyber planning across compliance regimes. Custom profiles, role alignment, and toolkit use were central to success. | Built trust with regulators and clients; improved incident recovery times; drove strategic visibility into cybersecurity ROI at the board level. |
Challenges in Aligning With NIST
Despite its modular, scalable design, adopting the NIST Cybersecurity Framework 2.0 poses serious challenges—especially for organizations without deep cybersecurity maturity. Many businesses underestimate the capability, time, and leadership alignment needed to operationalize the framework’s principles beyond paper.
Internal Capability Gaps
One of the largest barriers is the technical and strategic skill gap within internal teams. While the framework offers guidance, execution demands cross-functional competence across:
Asset identification: Many organizations still lack a real-time inventory of IT, OT, and SaaS assets, which is foundational to the Identify function.
Threat detection engineering: Customizing detection logic to match subcategories often requires dedicated security analysts and SIEM expertise.
Control mapping: Aligning existing tools with CSF subcategories demands fluency in both NIST terminology and tool-specific configurations.
In mid-market firms, these gaps often mean over-reliance on vendors who may not prioritize outcome-based reporting or framework fidelity. Without in-house oversight, organizations risk building control surfaces that appear compliant but fail under real-world attack simulation.
Budget & Leadership Buy-In
The second roadblock is the disconnect between cybersecurity teams and executive leadership. Governance, newly formalized in CSF 2.0, requires:
Cybersecurity KPIs tied to business outcomes
Board-level reporting on digital risk exposure and remediation timelines
Strategic investment in both people and platform consolidation
However, cybersecurity is still too often viewed as an operational cost. In a 2024 survey of 500 mid-sized enterprises, 67% cited lack of budget and leadership buy-in as the top reason for failed CSF implementation. In many cases, organizations begin implementation but stall at the Protect or Detect stage—never achieving full-cycle maturity across the framework.
The most successful adopters tie CSF metrics to risk quantification models—such as reduction in ransomware exposure, downtime savings, or insurance underwriting results—converting security into a business value driver. Without this narrative, cyber initiatives remain siloed, making CSF adoption fragmented and ineffective.
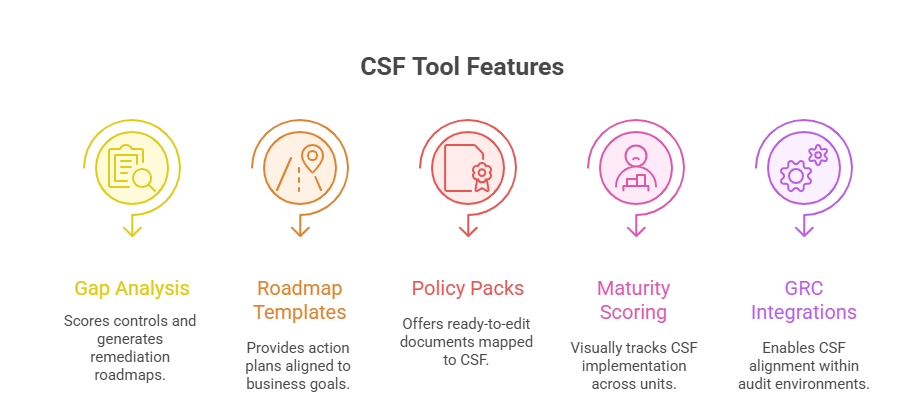
Tools and Templates That Accelerate Adoption
Adopting NIST CSF 2.0 requires more than intent—it demands structured execution. Organizations that succeed typically lean on automated tools and curated templates that translate abstract categories into practical, measurable tasks. These accelerators reduce onboarding friction, eliminate ambiguity, and compress time-to-value by 40–60% compared to manual adoption approaches.
Gap Analysis and Roadmap Builders
A robust starting point is an interactive gap analysis tool that maps current controls against the CSF’s core functions and subcategories. These tools often include:
Automated questionnaires that profile current maturity levels
Dynamic scoring engines that identify red zones across Identify, Protect, Detect, Respond, and Recover
Roadmap generators that produce phased action plans based on risk priority and available resources
More mature platforms integrate with configuration management databases (CMDBs), ticketing systems, and SIEMs to auto-populate evidence of control effectiveness. This tightens the feedback loop between technical operations and governance visibility.
Many organizations also embed these roadmaps into their GRC platforms to track progress with quarterly board-level KPIs, enabling audit-ready documentation that aligns with ISO 27001, SOC 2, or HIPAA if required.
Prebuilt Policy Packs
CSF adoption often falters due to policy paralysis—a situation where teams spend months drafting controls without clear starting points. Prebuilt policy packs offer an immediate lift by providing:
Template libraries mapped directly to each CSF subcategory
Editable documents including access control policies, vendor risk templates, and incident response workflows
Role-based distribution formats—ensuring stakeholders from IT to legal receive only what’s relevant
These packs not only reduce drafting time but standardize language and formatting, helping organizations avoid audit failures due to inconsistent documentation. Some providers even offer crosswalks to other frameworks, allowing for simultaneous alignment with CMMC, ISO, or GDPR from a single policy source.
When combined, these tools enable organizations—especially resource-constrained ones—to implement CSF 2.0 faster, with fewer missteps, and with verifiable governance outcomes that withstand scrutiny from regulators, partners, and insurers alike.
How ACSMI’s Certification Program Builds NIST Expertise
For organizations and professionals aiming to implement NIST CSF 2.0 effectively, theory isn’t enough. Success demands practical fluency in role-specific tasks, evidence management, and framework translation across real-world architectures. The ACSMI Advanced Cybersecurity & Management Certification fills this gap with precision—equipping learners not only with conceptual understanding but operational skillsets tailored for CSF execution.
Role-Based NIST Modules
Unlike generic cybersecurity courses, ACSMI’s certification is structured around NIST CSF-aligned functions, broken down by professional role and operational tier. This ensures:
Security engineers master detection engineering, not just framework theory
GRC analysts build audit-traceable documentation aligned with subcategory outcomes
Managers learn to translate CSF into budget requests and executive KPIs
Each lesson incorporates real artifacts—network diagrams, access control logs, incident reports—mapped directly to CSF categories like PR.AC-1 (identities and credentials) or DE.CM-7 (monitoring for unauthorized personnel). This makes abstract categories tactically implementable in real environments.
The program also includes profile creation labs, helping learners design custom CSF profiles for industries like healthcare, fintech, and education. By the end of the certification, candidates can construct end-to-end governance programs aligned with CSF 2.0 and crosswalked to frameworks like ISO 27001 or NIS2.
Audit Simulation & Toolkit Access
Where most training ends at theory, ACSMI delivers audit simulation environments modeled after real-world compliance audits. Learners are tasked with:
Performing gap assessments
Generating control evidence
Justifying risk remediation priorities under executive review scenarios
These simulations are supported by exclusive toolkit access, including:
Editable policy packs pre-mapped to CSF 2.0
Maturity scoring templates compatible with leading GRC platforms
Board reporting decks with sample KPIs, risk dashboards, and governance flows
This not only sharpens implementation skill but builds board-facing communication fluency—one of the most underestimated aspects of CSF execution.
Ultimately, the ACSMI certification is built for high-impact transformation: whether you’re leading a cybersecurity initiative, managing compliance portfolios, or serving as a consultant, it turns NIST CSF from a guideline into an operational advantage.
Frequently Asked Questions
-
The NIST Cybersecurity Framework (CSF) is a globally recognized guideline developed by the U.S. National Institute of Standards and Technology to help organizations manage cybersecurity risk. In 2025, its adoption has surged because CSF 2.0 incorporates critical updates like supply chain risk, governance accountability, and enhanced outcome metrics. It’s widely used across healthcare, finance, manufacturing, and SMEs because of its flexible, outcome-driven structure that supports various maturity levels. Unlike static checklists, NIST CSF enables organizations to adapt security practices to real-world threats and business contexts, making it ideal for both compliance and resilience. Its framework is scalable, risk-based, and highly mappable to global standards.
-
NIST CSF 2.0 is structured around six core functions: Identify, Protect, Detect, Respond, Recover, and the newly added Govern. Each function represents a key pillar of a comprehensive cybersecurity strategy. “Identify” focuses on asset awareness, “Protect” implements safeguards, “Detect” enables threat identification, “Respond” handles incidents, and “Recover” ensures operational restoration. The new “Govern” function elevates cyber risk to a board-level responsibility, enforcing oversight and accountability. This modular layout allows organizations to assess gaps and maturity in each domain. Collectively, these functions guide organizations from reactive security models to proactive, measurable risk management, aligned with modern threat landscapes.
-
While CSF 1.1 was centered on voluntary adoption and generalized cybersecurity hygiene, CSF 2.0 introduces structural shifts to reflect the evolving risk climate. The biggest difference is the introduction of the Govern function, which mandates top-level ownership of cybersecurity programs. CSF 2.0 also updates its references to include ISO/IEC 27001:2022, Zero Trust models, and regulatory mappings. Furthermore, it enhances guidance for supply chain visibility, third-party oversight, and custom profile creation. These changes prioritize governance maturity, making the framework not just operational but strategically aligned with enterprise risk. CSF 2.0 is less about compliance snapshots and more about continuous cybersecurity evolution.
-
The NIST CSF is not legally mandatory, but it is increasingly treated as a de facto baseline by regulators, insurers, and industry stakeholders. In the U.S., sectors like healthcare, finance, and energy are encouraged to adopt it for compliance alignment with HIPAA, PCI DSS, FFIEC, and FERC. Internationally, NIST CSF is often adopted voluntarily and crosswalked with ISO 27001, GDPR, or local cyber laws like the NIS2 Directive in Europe. While no law mandates it directly, many cybersecurity insurance providers and clients expect CSF adoption as proof of governance and operational readiness. It is now a key market differentiator for trust and risk assurance.
-
For a mid-sized organization (200–1000 employees), implementing NIST CSF 2.0 usually spans 6 to 12 months, depending on current maturity and tooling. A phased approach begins with gap assessment, followed by prioritized remediation, policy drafting, and board reporting alignment. Organizations with legacy GRC tooling or strong ISO 27001 foundations may complete adoption faster. However, companies starting from scratch often require dedicated project management, cross-functional training, and possibly third-party support. Use of framework accelerators like roadmap generators, policy packs, and role-based toolkits (as offered in the ACSMI certification) can significantly reduce timeline and enable quicker governance outcomes.
-
The most frequent pitfalls include:
Treating CSF as a checklist rather than a risk management lifecycle
Failing to engage executive leadership or board governance
Over-engineering implementation without clear outcome metrics
Ignoring “Detect” and “Respond” in favor of front-loaded controls
Not aligning CSF adoption with business priorities or compliance drivers
Additionally, many organizations purchase tools before defining their framework outcomes—leading to misconfigured tech stacks and audit gaps. Success requires beginning with a capability and maturity assessment, then aligning action to business risk. Without this, the framework becomes surface-level and fails to deliver resilience or reporting value.
-
The ACSMI certification is purpose-built to help professionals implement NIST CSF 2.0 in real-world environments. It offers role-specific modules that teach how to execute subcategory controls, build custom CSF profiles, and align policies with regulatory requirements. Learners receive access to audit simulation labs, editable CSF-aligned policy templates, and maturity scoring tools. This bridges the gap between framework theory and operational skill. Whether you’re in security operations, governance, or executive leadership, the certification sharpens your ability to translate CSF outcomes into measurable actions. It’s ideal for GRC professionals, CISOs, and consultants who need to lead or assess CSF-driven initiatives.
Final Thoughts
In 2025, the NIST Cybersecurity Framework 2.0 is no longer a forward-looking ideal—it’s the operational core of modern cybersecurity programs. Its inclusion of governance, supply chain, and tailored outcomes marks a decisive shift from theory to execution. Organizations that succeed with CSF 2.0 aren’t just checking boxes—they’re embedding security into strategy, culture, and accountability structures.
From real-world adoption trends and sector-specific benchmarks to gap-closing tools and role-based training like the ACSMI certification, the path to CSF maturity is clearer than ever. But clarity doesn’t equal ease. Effective adoption still demands executive alignment, skilled execution, and the right frameworks to operationalize insight.
As cyber threats escalate and compliance demands intensify, CSF 2.0 offers a flexible, outcome-driven foundation to build trust—internally, across supply chains, and with regulators. Those who move decisively now will be positioned not only for compliance, but for competitive security leadership in a risk-defined digital era.
| Poll Question: How familiar are you with the NIST Cybersecurity Framework 2.0? | |
|---|---|