Quantum Computing & Cybersecurity: Report on Threats & Ops
Quantum computing is no longer just theoretical—it’s becoming a strategic disruptor in cybersecurity. With advances in quantum processors, entanglement protocols, and QKD (Quantum Key Distribution), governments and Big Tech are accelerating toward real-world deployment. That acceleration comes with consequences: encryption methods like RSA and ECC are on borrowed time. The very mathematical problems that power today’s cybersecurity infrastructures will be solvable by quantum machines—rendering many current safeguards ineffective almost overnight.
This report breaks down both the emerging threats and real-world opportunities quantum presents for cybersecurity professionals in 2025. From understanding the foundational concepts like qubits and superposition, to analyzing use cases already underway in defense and telecommunications, we dive deep into where the field is going and what cybersecurity leaders must act on now. Whether you’re planning your PQC (Post-Quantum Cryptography) strategy, rethinking key management, or evaluating hybrid encryption protocols, this original analysis will help you stay ahead of the curve in one of the most critical transitions security has ever faced.
What is Quantum Computing & Where It’s Heading
Qubits, Superposition, and Entanglement
Classical computers use bits—binary units that exist as either 0 or 1. In contrast, quantum computers use qubits, which can exist as 0, 1, or both simultaneously thanks to superposition. This radically expands computational possibilities. When multiple qubits become entangled, changes to one instantly affect the other, regardless of distance. This enables massive parallelism, where quantum systems explore countless permutations at once—unlike any classical architecture.
Quantum advantage lies not in speed alone, but in nonlinear problem-solving. Algorithms like Shor’s (for factoring large primes) and Grover’s (for database search) illustrate how quantum systems can disrupt encryption, logistics, and modeling. Entanglement, often dubbed “spooky action at a distance,” allows unprecedented data correlation and coherence, which forms the basis for quantum-secure communications and ultra-precise simulations.
By 2025, IBM, Google, and Chinese research labs have surpassed 100-qubit demonstrations, with claims of achieving quantum supremacy in narrow, structured tasks. The race is now about scaling coherence time, improving gate fidelity, and developing error correction that makes quantum processors practical outside lab environments. These aren’t just theoretical improvements—they’re laying the groundwork for real-world impact in cryptography, AI, and secure computing.
Projected Use by 2030
By 2030, quantum computing is expected to break out of niche experimentation and integrate into critical sectors via cloud-based access models. Companies like Amazon Braket and Microsoft Azure Quantum are already providing platform-as-a-service models, enabling developers to simulate quantum tasks without building hardware.
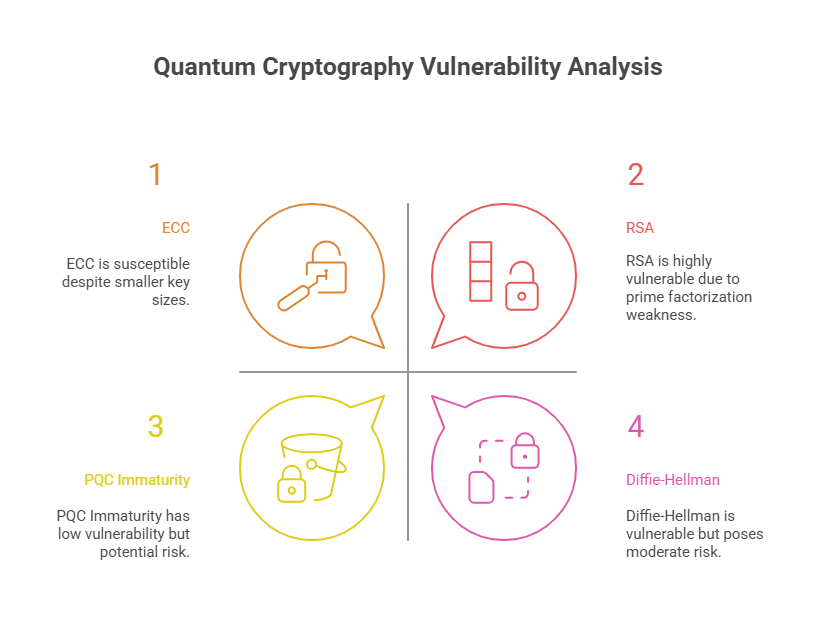
Forecasts project that financial institutions, defense agencies, and pharmaceutical firms will use quantum for molecular modeling, optimization, and threat analysis. But for cybersecurity, the most immediate impact is negative: quantum will obsolete most public-key encryption schemes. RSA, ECC, and Diffie-Hellman protocols—responsible for the security of websites, VPNs, and messaging apps—are all susceptible to quantum decryption.
This has already triggered massive interest in post-quantum cryptography by NIST and global regulators, aiming to establish resilient standards before quantum hits production readiness. Meanwhile, China’s deployment of quantum satellites and entangled photon networks is driving geopolitical urgency. Quantum computing is not a far-off innovation; it’s a present-tense disruptor with long-term stakes. Cybersecurity teams ignoring its trajectory risk being blindsided by algorithmic obsolescence within the decade.
Quantum’s Threat to Traditional Cybersecurity
RSA & ECC Algorithm Vulnerability
At the heart of nearly every secure internet transaction today are public-key cryptography algorithms like RSA (Rivest–Shamir–Adleman) and ECC (Elliptic Curve Cryptography). These systems rely on the mathematical difficulty of factoring large primes or solving discrete logarithm problems, tasks that classical computers can’t feasibly crack within realistic timeframes. But with quantum computing, that assumption collapses.
Shor’s Algorithm, developed in 1994, is the quantum equivalent of a wrecking ball to public-key encryption. A sufficiently powerful quantum computer—estimated to require around 4000 error-corrected qubits—could factor the keys protecting everything from financial systems to medical records in minutes. ECC, often seen as a faster alternative to RSA, is even more vulnerable under quantum attack vectors due to its smaller key sizes.
As of 2025, no quantum system has yet demonstrated this capability at scale, but research labs are aggressively racing to reach it. That urgency has prompted warnings from the NSA, NIST, and ENISA, urging organizations to transition to quantum-resilient standards now—because data encrypted today can be harvested and decrypted retroactively once quantum power matures.
Post-Quantum Cryptography Risks
The transition to post-quantum cryptography (PQC) isn’t just about replacing one algorithm with another. Most PQC candidates—such as lattice-based schemes like Kyber, Dilithium, and Falcon—come with larger key sizes, slower performance, and increased bandwidth demands. These new cryptographic primitives are still being vetted for real-world vulnerabilities.
What makes PQC risky is not just immaturity of the algorithms, but the ecosystem lag. Hardware devices, embedded systems, and firmware updates in sectors like healthcare or aviation operate on decades-long upgrade cycles. Introducing new cryptographic protocols in these environments risks breaking compatibility, opening up new attack surfaces.
Even more concerning is that some PQC schemes may be vulnerable to classical side-channel attacks—leaving open doors for adversaries who don’t even need a quantum computer. Thus, migrating to PQC is not just about deploying secure math; it’s about re-architecting entire systems to account for performance, longevity, and resilience.
For organizations handling sensitive personal data, military IP, or financial transactions, ignoring quantum’s threat surface is no longer an option. The clock isn’t just ticking—it may have already started counting backwards.
Use Cases of Quantum in Security Today
Quantum Key Distribution (QKD)
While quantum computing threatens traditional encryption, it also offers solutions—most notably through Quantum Key Distribution (QKD). Unlike classical key exchange methods, QKD leverages quantum entanglement and Heisenberg’s uncertainty principle to detect eavesdropping in real time. If a third party tries to intercept a quantum key, the act of measuring it changes the key itself—making the intrusion instantly visible.
QKD doesn't depend on computational assumptions; it’s secure by physics, not math. This is critical in an era where computational assumptions are being shattered by quantum advancement. Leading QKD protocols like BB84 and E91 are already in field tests, transmitting encryption keys over fiber-optic networks and satellite relays.
However, QKD isn’t a plug-and-play solution. It requires dedicated quantum channels, expensive single-photon emitters and detectors, and has distance limitations over terrestrial lines. Still, for high-security sectors like defense and diplomacy, QKD is becoming a viable tool in the modern cryptographic arsenal—where absolute key secrecy matters more than speed or convenience.
Secure Communications Trials in 2024–25
The last two years have seen explosive growth in quantum-secure communication pilots across Asia, Europe, and North America. China’s Beijing–Shanghai quantum backbone spans over 2,000 km and supports secure messaging, financial transactions, and classified communications using QKD. The EU’s EuroQCI initiative is building a similar infrastructure, integrating quantum encryption into cross-border digital sovereignty frameworks.
In the U.S., defense contractors and academic labs have partnered under DARPA’s Quantum Aperture program, testing hybrid QKD and PQC networks on military-grade fiber lines. Meanwhile, telecom giants like BT, SK Telecom, and Toshiba have conducted live demos of quantum-encrypted video conferencing and secure VoIP across city-scale networks.
These pilots are not just PR exercises—they signal a paradigm shift in how critical communications will be secured post-2030. The combination of classical resilience (PQC) and quantum-native defenses (QKD) is shaping a hybrid model of encryption where both technologies coexist. While not yet ready for consumer-grade rollout, quantum-secured channels are no longer speculative—they’re operational prototypes already influencing global cyber doctrine.
| Use Case | Real-World Example |
|---|---|
| QKD (Quantum Key Distribution) | Used in BB84 protocol; detects eavesdropping via quantum interference |
| Satellite-Based QKD | China’s Micius satellite enabling intercontinental secure communication |
| City-Scale Trials | Toshiba and SK Telecom tested quantum-encrypted VoIP over fiber |
| EuroQCI Infrastructure | EU’s initiative to integrate QKD into border-spanning secure channels |
| Hybrid PQC + QKD | DARPA-funded pilots in defense networks combining classical and quantum |
Barriers to Mass Adoption
Hardware, Power, and Cost
Despite major strides in quantum development, widespread adoption faces steep hardware, energy, and cost constraints. Quantum systems are not miniaturized chips—they're delicate, cryogenic setups requiring temperatures colder than outer space to maintain qubit coherence. Maintaining superconducting states, isolating from environmental noise, and executing high-fidelity gates all demand specialized infrastructure most organizations can’t afford.
Building even a 50–100 qubit quantum system with sufficient coherence time can cost tens of millions of dollars, with operational expenses including liquid helium, vacuum chambers, and electromagnetic shielding. This places real, usable quantum computers firmly in the domain of national labs, hyperscalers, and defense agencies—not commercial IT departments.
Moreover, qubit error rates remain a central obstacle. Every additional qubit increases complexity exponentially, making error correction and noise management major bottlenecks. Without breakthroughs in topological qubits or photonic architectures, cost-effective scalability remains years away—limiting access to quantum-secure applications at enterprise scale.
Skill Gaps and Compatibility Issues
Quantum computing demands a radically different programming paradigm. Existing software engineers, cybersecurity architects, and cryptographers are often unequipped to work with quantum algorithms, which require understanding of quantum gates, measurement theory, and linear algebra over Hilbert spaces. The workforce shortage in quantum-skilled professionals is among the most cited adoption barriers in 2025 surveys.
Additionally, even if quantum systems were ready at scale, the classical stack isn’t. Most enterprise security infrastructures are tightly coupled with legacy protocols, middleware, and outdated firmware—creating compatibility deadlocks. Replacing core encryption modules, identity frameworks, and certificate systems for PQC or QKD involves breaking and rebuilding secure pathways from the ground up.
Training materials are scarce, middleware integration tools are immature, and certification pathways for quantum-readiness are still evolving. This leaves CISOs and IT managers in a difficult position: they know change is coming, but the playbook remains incomplete. Bridging this divide will require not just better hardware, but better tooling, standards, and education ecosystems tailored for the quantum transition.
What Cybersecurity Pros Should Prepare For
Hybrid Encryption
The path to quantum resilience won’t be a binary switch. Instead, we’re entering a hybrid cryptographic era, where traditional algorithms are paired with post-quantum counterparts. Hybrid encryption combines classical methods like RSA or ECC with lattice-based algorithms (e.g., Kyber or SABER), ensuring that if one method fails under quantum attack, the other still offers a safeguard.
Organizations need to adopt crypto-agility—the ability to switch, layer, and update cryptographic schemes without breaking services. This means moving beyond hardcoded cryptographic dependencies and implementing modular, upgradable encryption stacks. Hybrid protocols are already in use in test environments, including TLS 1.3 with post-quantum extensions, offering a bridge to more future-proof deployments.
Vendors are responding. Leading cloud providers and cybersecurity platforms have started incorporating PQC-hardened APIs and hybrid VPNs, giving enterprises early access to migration tools. But the onus is still on CISOs and security architects to initiate pilot programs and develop deployment roadmaps that fit organizational needs. Waiting until standards are finalized is not a safe option.
Transition Strategy for Enterprises
The first step in quantum resilience is a crypto asset inventory—identifying where and how cryptography is used across the organization. Most enterprises use encryption in hundreds of interdependent systems: data at rest, in transit, TLS handshakes, internal APIs, cloud storage, user authentication, and more. Without visibility, there’s no path to protection.
Next, build a PQC migration framework, aligning with guidance from NIST’s Post-Quantum Cryptography Standardization Project and leveraging their chosen algorithms (such as Kyber and Dilithium) for early integration testing. Implement a risk-prioritized rollout—start with systems that handle regulated data, public-facing services, or long-lifecycle encryption (e.g., software updates, legal documents).
Importantly, communicate the transition upstream and downstream. Vendors must be held accountable for their PQC-readiness, and clients need assurance that data encrypted today won’t be vulnerable tomorrow. Cross-functional collaboration between IT, legal, compliance, and cybersecurity is essential to ensure that policy aligns with technical execution.
For security leaders, this is no longer a theoretical issue—it’s a strategic imperative for continuity. Quantum risk may not be fully realized by 2025, but the window for proactive preparation is closing fast.
| Action Step | Why It Matters |
|---|---|
| Crypto Asset Inventory | Understand all places where cryptography is currently applied |
| Hybrid Encryption Adoption | Adds redundancy by pairing classical and post-quantum algorithms |
| Pilot PQC in Sandboxes | Reduces production risk and reveals performance tradeoffs |
| Vendor PQC Alignment | Forces supply chain to modernize securely |
| Staff Training & Certification | Prepares internal teams to handle quantum migration proactively |
Post-Quantum Training in Our Cybersecurity Course
The Advanced Cybersecurity & Management Certification by ACSMI equips professionals with the real-world skills needed to navigate the quantum threat landscape, well beyond traditional security frameworks. As quantum breakthroughs shift from research labs into enterprise relevance, this course prepares you to lead the transition with post-quantum cryptography (PQC), hybrid encryption, and quantum-safe architectures.
The course includes in-depth modules on lattice-based encryption schemes, analyzing how Kyber, Dilithium, and Falcon perform under current benchmarks. You’ll learn to evaluate algorithmic strength against quantum attack models, model attack surfaces in mixed classical-quantum environments, and deploy crypto-agile frameworks that can handle both legacy and PQC stacks. Emphasis is placed on building quantum-resilient VPNs, secure communication protocols, and key lifecycle management.
You’ll also explore the practical integration of Zero-Knowledge Proofs (ZKPs) in post-quantum settings—vital for secure authentication and data minimization in sensitive sectors like finance and healthcare. Through real-world case studies, labs, and access to NIST-aligned migration blueprints, the course ensures you're prepared not just in theory but in applied security practice.
Unlike outdated cybersecurity bootcamps, this program is engineered for 2025 and beyond, continuously updated with the latest from NIST, ENISA, and global PQC consortiums. Graduates leave with skills that aren’t just reactive—they’re anticipatory. In a world where quantum disruption is guaranteed, proactive training is your most critical defense.
Frequently Asked Questions
-
The most pressing threat is the breakdown of public-key cryptography, which secures everything from HTTPS websites to VPNs, emails, and banking systems. Quantum computers can run Shor’s algorithm to efficiently factor large integers and solve discrete logarithms—rendering RSA, ECC, and DH encryption obsolete. This puts all current internet communications, even those stored now for future decryption (“harvest now, decrypt later”), at severe risk. While quantum computers aren’t fully capable yet, the anticipatory threat means organizations must begin migrating to post-quantum cryptography (PQC) and hybrid encryption models immediately to prevent future data breaches from today’s encrypted assets.
-
Estimates suggest that within the next 5–10 years, quantum computers with thousands of logical, error-corrected qubits could break RSA-2048 and ECC-based cryptographic systems. While current quantum machines are still noisy and underpowered, progress is accelerating, with companies like IBM, Google, and others projecting major hardware milestones by 2029–2030. Because of this, governments like the U.S. and China are investing heavily in post-quantum research and advising early migration to quantum-safe algorithms. The risk isn’t just theoretical—it’s already triggering policy shifts, NIST standards, and cyber procurement changes. The window to prepare is short—and irreversible once closed.
-
Post-quantum cryptography (PQC) refers to encryption algorithms that are designed to resist quantum attacks, particularly those that exploit quantum speedups like Shor’s or Grover’s algorithms. Unlike traditional RSA or ECC, PQC relies on mathematical problems believed to be hard even for quantum machines, such as lattice-based problems, multivariate equations, hash-based signatures, and code-based systems. The most widely accepted candidates (e.g., Kyber, Dilithium, Falcon) are undergoing NIST standardization. These algorithms are implemented on classical computers, making them immediately deployable—unlike quantum cryptography, which requires specialized hardware. PQC allows organizations to maintain encrypted security while preparing for future quantum risk.
-
Not yet. Quantum Key Distribution (QKD) offers the strongest form of secure communication—backed by physics, not math—but it's currently impractical for mass deployment. QKD requires dedicated optical fiber or satellite channels, single-photon emitters, and ultra-sensitive detectors. It also suffers from distance limitations, transmission instability, and high setup costs. As of 2025, QKD is mainly used in defense, national labs, and financial institutions conducting experimental pilots or securing high-value assets. For most organizations, post-quantum cryptography is the more feasible first step. Over time, QKD may become viable as infrastructure improves, but it's not a short-term solution for most networks.
-
Start with a cryptographic asset inventory to identify where encryption is used across data-in-transit, at-rest, APIs, cloud systems, and identity layers. Then evaluate those systems based on lifespan, risk level, and migration difficulty. Next, build a PQC-readiness roadmap, leveraging tools from NIST and adopting hybrid encryption frameworks where appropriate. Train your technical teams on crypto-agility, ensuring they can swap out algorithms without breaking architecture. Engage vendors about their post-quantum support timelines, and begin testing PQC algorithms in sandboxed environments. Proactive migration isn’t just about compliance—it’s about maintaining trust, confidentiality, and business continuity in a rapidly evolving threat landscape.
-
As of 2025, the Advanced Cybersecurity & Management Certification by ACSMI is among the few training programs that directly address post-quantum cryptography, hybrid encryption models, and quantum threat preparedness. It covers key topics such as lattice-based algorithms, zero-knowledge proofs in PQC contexts, and the integration of NIST-aligned migration plans. Other certifications from traditional bodies like CompTIA and ISC² are beginning to touch on quantum, but few provide the depth, practical labs, or toolkits needed to deploy secure systems today. For professionals aiming to future-proof their skills, ACSMI’s program is currently a top-tier option with real-world relevance.
-
No. Quantum computers are not general-purpose replacements for classical systems. They excel at solving specific mathematical problems that are computationally intractable for classical machines, such as prime factorization or quantum simulations. In cybersecurity, their primary role is in breaking certain cryptosystems and enabling ultra-secure communication methods (like QKD). However, classical computers will remain essential for system control, logic, interfaces, and general processing. The future is hybrid, where quantum hardware handles targeted tasks and classical infrastructure provides orchestration, data management, and user-facing operations. Quantum will augment—but not replace—the cybersecurity stack.
Final Thoughts
Quantum computing is no longer a distant disruptor—it’s an imminent force reshaping cybersecurity strategy. While current systems still operate on classical assumptions, quantum breakthroughs are accelerating faster than enterprise preparedness. Every organization—whether in finance, healthcare, defense, or tech—must now rethink encryption, update cryptographic infrastructure, and train teams for a hybrid future.
Waiting for full-scale quantum maturity before acting is a critical risk. Adopting post-quantum cryptography, piloting hybrid encryption, and upskilling through programs like ACSMI’s Cybersecurity Certification are no longer optional—they’re foundational to safeguarding digital assets beyond 2030. The quantum shift doesn’t demand panic, but it does demand precision, urgency, and a long-view mindset.
Poll: Do you think your organization is ready for quantum-era cybersecurity challenges?