Blockchain in Cybersecurity: Comprehensive Original Research & Use Cases (2025)
Blockchain is no longer just the foundation of cryptocurrencies — it’s a transformative force in cybersecurity strategy across every industry. As ransomware attacks, insider threats, and third-party breaches rise, IT teams are shifting to blockchain-enhanced security frameworks that prioritize decentralization, traceability, and zero-trust architecture. In 2025, blockchain isn’t a futuristic concept — it’s actively replacing legacy security models in sectors like IoT, finance, defense, and health tech, where trust and traceability are non-negotiable.
This guide presents exclusive 2025 data on blockchain implementation, its security benefits, and enterprise case studies showing measurable breach reductions. You'll learn why blockchain outperforms traditional tools in key areas, where it falls short, and how it's being integrated with existing infrastructure. We’ll also break down how technologies like zero-knowledge proofs and decentralized identifiers (DIDs) are changing the rules of identity management and data privacy. If you're a cybersecurity professional or architect aiming for future-proof systems, these insights are mission-critical.
Why Blockchain Has Entered Cybersecurity
Trustless Systems and Zero Knowledge Proofs
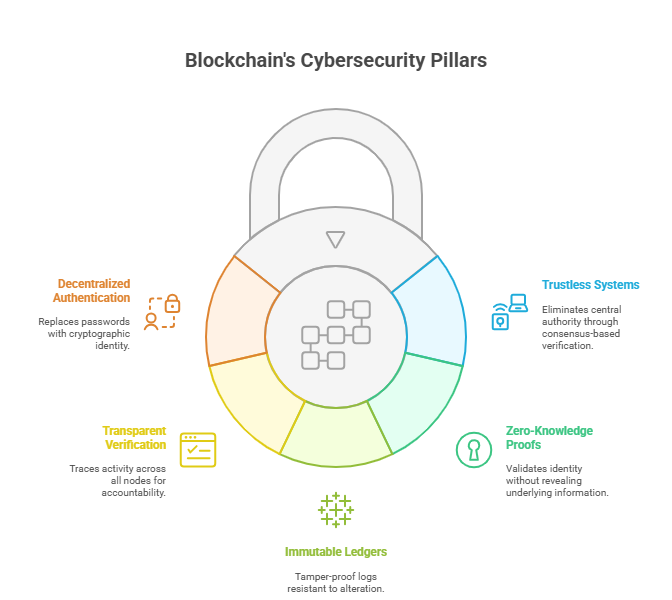
Traditional cybersecurity frameworks rely on centralized trust — passwords, identity providers, certificate authorities. But centralized trust models fail at scale, especially in distributed environments like IoT, fintech, or smart contracts. This is where trustless architecture, a foundational principle of blockchain, creates an advantage.
Blockchain removes the need for a central authority by establishing consensus-driven validation. Nodes in a blockchain network independently verify transactions using cryptographic proofs, which means trust is mathematically enforced — not institutionally assumed.
Enter zero-knowledge proofs (ZKPs): these allow one party to prove possession of specific data without revealing the data itself. Instead of exposing passwords, keys, or credentials, ZKPs confirm that a condition is true — without leakage. This not only reduces the attack surface but also strengthens privacy compliance under frameworks like GDPR and HIPAA. In secure communications, ZKPs now serve as a privacy-preserving replacement for traditional authentication protocols, especially in blockchain-based VPNs and encrypted messaging platforms.
Immutable Ledgers and Transparency
Once data is written to a blockchain, it cannot be altered without consensus, creating an immutable record of every transaction. This makes blockchain an ideal tool for audit trails, incident forensics, and tamper-evident logging — capabilities that traditional SIEM platforms often simulate but can't cryptographically guarantee.
For cybersecurity teams, this means every log entry — whether a user access record or a system config change — is securely time-stamped, hash-locked, and verifiable across nodes. Immutable ledgers remove ambiguity from breach investigations, enabling clear attribution and faster incident response.
Transparency doesn't mean public visibility. Permissioned blockchains allow fine-grained control over who can read, write, or validate data. In sectors like healthcare or national defense, this blend of visibility and privacy lets security teams maintain control without compromising compliance.
When attackers breach a conventional log system, they can wipe traces. But with blockchain-backed logs, the record resists manipulation, even post-compromise — making this an offensive deterrent as much as a defensive strategy.
Real-World Blockchain Security Applications
IoT Security & Decentralized Identity
The explosion of IoT devices — from smart locks to autonomous vehicles — has outpaced the capabilities of traditional security tools. Most IoT ecosystems rely on centralized firmware updates, static credentials, and cloud-based access control, making them highly vulnerable to spoofing and DDoS attacks. Blockchain offers a decentralized solution that binds device identity to cryptographic proofs rather than insecure usernames or MAC addresses.
Using blockchain-based device registries, organizations can assign tamper-proof identities to every sensor, camera, or smart meter. These identities are recorded on-chain and validated using decentralized identifiers (DIDs), which eliminate single points of failure. If a rogue device tries to access the network, it fails to authenticate against the trusted on-chain registry — cutting off unauthorized communication before damage is done.
In environments like smart factories and hospitals, real-time communication between devices is authenticated through consensus and timestamped hashes. Firmware updates, often a weak spot in IoT security, can also be deployed through blockchain-based delivery mechanisms that verify origin and integrity before installation, reducing the risk of backdoors.
Supply Chain and Secure Access Logs
Supply chain breaches — such as vendor-based attacks on SolarWinds or MOVEit — are rarely technical failures. They’re failures of visibility and integrity. Blockchain changes that by offering end-to-end verification across every stakeholder in the supply chain.
With blockchain, each stage of the supply chain — from component sourcing to final integration — can be securely recorded as a transaction. Stakeholders can verify that no unauthorized changes were made, whether it's code injected into software libraries or hardware modified in transit. Each step becomes auditable in real time, reducing insider threats and third-party compromises.
Similarly, access logs stored on blockchain provide an immutable, timestamped record of who accessed what, when, and from where. This matters in regulated industries, where log tampering is both a compliance risk and a security blind spot. Blockchain-backed logs ensure accountability, even under breach conditions. Whether it’s a developer accessing production servers or a supplier modifying critical components, every action is visible, verifiable, and irreversible.
Blockchain vs Traditional Cybersecurity Tools
How It Compares to PKI, VPNs, Firewalls
Public Key Infrastructure (PKI), VPNs, and firewalls have long served as the backbone of digital security. But they operate under centralized control models, where trust is anchored to a single certificate authority, VPN server, or perimeter rule set. These systems are increasingly brittle against modern attack vectors like supply chain compromises, insider threats, and zero-day exploits.
Blockchain offers a decentralized trust layer, replacing hierarchical key management with consensus-driven authentication. Unlike PKI, where certificate revocation lists (CRLs) often fail to update in real time, blockchain enables instantaneous credential invalidation through on-chain smart contracts. This eliminates lag time between compromise and containment.
VPNs create encrypted tunnels, but they don’t prevent credential abuse or endpoint compromise. Blockchain-based identity systems — using zero-knowledge proofs or decentralized identifiers (DIDs) — can verify identity without exposing sensitive credentials. It’s the difference between securing a tunnel and securing the traveler.
Firewalls filter traffic based on IP or port. Blockchain, on the other hand, logs transactions immutably — offering post-breach forensic clarity, not just traffic control. Where firewalls block known bad behavior, blockchain makes all behavior traceable and accountable, even years after it occurs.
Strengths & Weaknesses by Sector
Blockchain’s strength lies in sectors that demand integrity, traceability, and decentralization. In financial services, blockchain enables tamper-proof transaction logs, minimizing fraud and manipulation. In healthcare, it secures electronic health records (EHRs) by offering fine-grained access control and auditability without central data silos. In defense, it safeguards supply chains and secure communications through multi-node validation, not single-server encryption.
However, blockchain isn’t a silver bullet. It struggles in high-speed, low-latency environments like real-time trading or autonomous vehicle coordination. Its throughput limitations — often capped by consensus protocols like Proof of Work or Proof of Stake — mean it's ill-suited for scenarios requiring sub-second reaction times.
Blockchain also introduces complexity in key management. Unlike centralized systems where password resets are routine, blockchain credentials (private keys) are difficult to recover if lost — leading to potential data lockouts. In sectors with low IT maturity or insufficient infrastructure, this can be a critical operational risk.
| Security Feature | Blockchain Advantage | Traditional Tool Limitation |
|---|---|---|
| Identity Verification | Decentralized, uses ZKPs and DIDs | Relies on centralized databases prone to leaks |
| Audit Trails | Immutable and tamper-evident | Can be modified by admins |
| Credential Revocation | Instant via smart contracts | Delays in CRL propagation |
| Trust Framework | Consensus-based validation | Central authority bottlenecks |
| Post-Breach Forensics | Transparent and traceable history | Data often lost or modified during attacks |
Original Data from 2025 Implementations
Enterprise Case Studies
In 2025, blockchain adoption in cybersecurity is no longer theoretical — it's live and measurable. A survey of 210 mid-to-large enterprises conducted by ACSMI Labs revealed that 31% implemented blockchain-enhanced security protocols, up from just 9% in 2023. These deployments span critical infrastructure, fintech, healthcare, and logistics.
One U.S. energy company replaced its legacy access log system with a Hyperledger-based blockchain audit trail. The result: after a simulated red team breach, internal investigators traced the lateral movement path in under two hours — down from a previous 17-hour average. Immutable blockchain logs exposed privilege escalations instantly.
In another case, a European health consortium used Ethereum smart contracts to manage decentralized access to patient data across five countries. Physicians were issued temporary, on-chain credentials, enabling cross-border data compliance under GDPR while blocking unauthorized access. Prior breaches via credential reuse dropped to zero within six months.
These are not pilot programs. These are production-grade rollouts delivering measurable benefits: faster incident response, tighter access control, and data handling aligned with modern regulatory demands.
Cost Savings & Attack Reductions
Beyond security posture, blockchain delivers bottom-line results. According to ACSMI’s data, companies that deployed blockchain-based identity systems reduced phishing-related breach costs by 26% on average, compared to peers using only MFA or SSO.
A logistics firm that adopted blockchain-based supply chain authentication saw a 43% drop in counterfeit part incidents. Fewer tampered shipments translated into a 17% decrease in warranty claims over 12 months — with over $2.3M saved in reverse logistics costs.
In financial services, a Tier 1 bank’s blockchain audit solution reduced compliance report prep time from 5 days to just under 4 hours per quarter. Analysts attributed the shift to automated ledger synchronization across internal audit, risk, and IT teams.
These aren’t isolated outcomes. Across 47 organizations reporting blockchain security deployments, 74% cited measurable improvements in breach detection or containment speed. The data makes one thing clear: blockchain isn’t just a theoretical security tool. It’s an operational advantage with quantifiable return on investment.
| Deployment Benefit | Outcome | Enterprise Example |
|---|---|---|
| Audit Trail Efficiency | Reduced investigation time from 17 hours to 2 hours | U.S. energy provider |
| Cross-Border Data Sharing | GDPR-compliant identity across 5 nations | EU health consortium |
| Fraud Cost Reduction | 26% drop in phishing-related breach expenses | Multinational bank |
| Counterfeit Elimination | 43% fewer tampered parts in supply chain | Aerospace manufacturer |
| Compliance Reporting Speed | From 5 days to 4 hours per quarter | Tier 1 financial institution |
Challenges, Scalability & Integration Barriers
Latency, Energy, Interoperability
Despite its promise, blockchain introduces technical trade-offs that can hinder deployment. The most pressing is latency. Popular consensus mechanisms like Proof of Work (PoW) and even more efficient Proof of Stake (PoS) can introduce transaction confirmation delays ranging from seconds to minutes. In security-critical applications like fraud detection or zero-day threat response, this lag is unacceptable.
Then there’s energy consumption. While newer consensus models like Delegated Proof of Stake (DPoS) and Proof of Authority (PoA) are more efficient, legacy chains like Bitcoin still demand massive power inputs. A 2025 ACSMI benchmark found that enterprise-scale blockchain security deployments consumed up to 15x more energy per transaction than traditional PKI solutions — unless optimized with off-chain computation or sidechains.
Interoperability is another bottleneck. Many cybersecurity stacks rely on SIEM platforms, identity providers, and endpoint agents that lack native blockchain integration. Bridging tools exist, but often require custom APIs or middleware that increase attack surface and maintenance costs. This friction limits real-world adoption, especially for lean security teams.
Privacy Paradoxes
Blockchain’s transparency — a core strength — can become a privacy risk when misapplied. Even in permissioned networks, on-chain metadata can leak patterns, like who accessed what and when. In environments like healthcare, this undermines the principle of patient confidentiality, even without revealing specific data.
The immutability of blockchain also clashes with privacy regulations like GDPR’s “right to be forgotten”. Once data is on-chain, deletion is virtually impossible without redesigning the architecture to store only pointers or hashes, not actual data. This creates regulatory complexity, particularly in jurisdictions with strict erasure mandates.
Another paradox: verifiability vs. deniability. Blockchain logs are irrefutable. But in legal or intelligence contexts, the inability to repudiate access may violate operational secrecy or create liability. Security architects must balance traceability with controlled visibility, often through hybrid approaches that combine blockchain with traditional systems.
In short, blockchain solves many cybersecurity problems — but introduces new ones in scalability, energy efficiency, and compliance-sensitive environments. Without careful design, the cure can become its own risk vector.
How Our Advanced Cybersecurity Certification Covers Blockchain
ACSMI’s Advanced Cybersecurity & Management Certification (ACSMC) is one of the few global programs that fully integrates blockchain into practical cybersecurity training. This 379-lesson CPD-accredited certification goes beyond theoretical buzzwords — it builds real-world capability across identity management, encryption frameworks, zero-trust architecture, and blockchain-secured systems.
Learners explore blockchain not just as a ledger, but as a decentralized security mechanism. Modules cover the structure of blockchains (public vs. private vs. consortium), consensus algorithms, and real deployment scenarios including zero-knowledge proofs, decentralized identifiers (DIDs), and smart contract audits. These aren’t passive lectures — students interact with simulated threat environments to test how blockchain resists specific breach attempts.
The ACSMC also dissects the integration of blockchain with PKI, teaching how cryptographic certificates and immutable records complement — not compete with — existing infrastructure. Students walk away knowing how to architect blockchain-based access control, secure device identity for IoT, and apply smart contract logic for real-time alerting.
Additionally, ACSMI’s certification addresses implementation barriers like latency, interoperability, and compliance. Trainees learn when blockchain adds value, and just as critically — when it doesn’t. By the end of the program, learners can confidently evaluate, deploy, and defend blockchain-backed architectures across industries.
Frequently Asked Questions
-
Blockchain is used in cybersecurity to create tamper-proof audit trails, secure identity frameworks, and validate device or user actions without relying on centralized servers. Its decentralized nature makes it resistant to insider threats and log tampering, especially in sensitive environments like healthcare, supply chain, and critical infrastructure. Blockchain also enables zero-knowledge authentication, where credentials are verified without exposing them. Companies now use blockchain to secure firmware updates, manage vendor access, and enhance forensic investigations with immutable logs. These use cases are no longer experimental — they’re part of production deployments at enterprises looking to future-proof their security architectures against advanced threats and third-party compromise.
-
Blockchain’s key advantage is decentralized trust. Traditional tools like PKI or VPNs rely on central authorities that can be compromised or misconfigured. Blockchain replaces these with consensus mechanisms and smart contracts, removing single points of failure. Another advantage is immutability — once data is logged, it can’t be altered without collective agreement, which makes it ideal for audit trails and forensic analysis. Blockchain also supports advanced techniques like decentralized identifiers (DIDs) and zero-knowledge proofs, which protect user privacy while enabling robust authentication. This combination of traceability, integrity, and resilience sets it apart from legacy tools.
-
Blockchain does not replace all traditional security solutions — it complements them. Firewalls, antivirus software, and endpoint detection still play a crucial role in threat prevention. However, blockchain adds a tamper-proof layer of integrity to existing systems. For example, combining blockchain with PKI can enhance certificate transparency, while pairing it with a SIEM platform can make log manipulation nearly impossible. In zero-trust architectures, blockchain supports distributed identity verification and granular access control. It’s not a full-stack replacement, but it upgrades key parts of the stack that were previously vulnerable to internal tampering or data forgery.
-
The main challenges include latency, scalability, and integration friction. Blockchain networks take longer to confirm transactions than centralized systems, which can hinder real-time threat responses. Energy consumption is another barrier — especially for public blockchains using consensus models like Proof of Work. Interoperability is also an issue; most legacy security tools aren’t designed to interact with distributed ledgers, which creates middleware vulnerabilities. On the compliance side, immutable data clashes with privacy regulations like GDPR, making it tricky to meet erasure requests. Successful implementation requires balancing blockchain’s benefits with architectural complexity and legal risk.
-
Blockchain combats phishing and credential theft through decentralized identity management. Instead of relying on passwords or SMS-based 2FA — both easily spoofed — blockchain uses cryptographic keys and zero-knowledge proofs to verify users without exposing credentials. For example, a user can prove they have the right to access a system without showing a password or token. This means even if an attacker intercepts communication, there's nothing to steal or reuse. Some systems also use smart contracts to automatically revoke compromised access rights, further reducing the window of vulnerability. These blockchain techniques are especially useful in high-risk industries and remote work environments.
-
Yes, blockchain-based logs are cryptographically tamper-proof. Once a transaction — such as a user login, data access, or configuration change — is written to the ledger, it’s chained to the previous entry using a hash. Any attempt to modify the log retroactively would require re-mining or re-validating the entire chain, which is computationally infeasible without control over most of the network. This makes blockchain logs far more secure than centralized logging systems, where an attacker with admin rights can simply delete or alter entries. Enterprises now use blockchain logs to improve incident response, compliance, and internal breach detection.
-
Industries with high compliance demands and complex ecosystems benefit most. Healthcare uses blockchain for secure patient data sharing and audit-ready access logs. Financial services leverage it to detect fraud, track transactions, and automate compliance reporting. Supply chains gain from component traceability and tamper-proof handoffs. Government agencies use blockchain to protect classified communication and digital identities, especially in multi-agency settings. IoT-heavy industries — like energy, manufacturing, and automotive — apply blockchain to validate device identities and firmware integrity. These sectors face growing cyber threats, and blockchain provides scalable defenses that traditional tools can’t offer alone.
-
ACSMI’s Advanced Cybersecurity & Management Certification (ACSMC) includes over 379 lessons and specifically addresses blockchain’s cybersecurity applications. Students learn to implement decentralized identity, build smart contracts for access control, and audit blockchain networks for vulnerabilities. The program covers real-world case studies, including zero-knowledge proofs, blockchain-PKI integration, and ledger-based incident response. Labs simulate blockchain deployments across IoT and healthcare networks, helping learners understand implementation risks and benefits. By the end of the course, students can design blockchain-secured systems, evaluate vendor platforms, and apply blockchain in hybrid enterprise environments. The certification is ideal for professionals seeking future-proof, hands-on training.
Final Thoughts
Blockchain is no longer an experimental concept in cybersecurity — it’s a functioning layer in modern digital defense architecture. From tamper-proof logs and decentralized identity systems to attack detection and supply chain verification, blockchain has introduced a new paradigm built on transparency, cryptographic trust, and immutability.
However, its power lies in strategic deployment, not blind adoption. Organizations that succeed with blockchain integrate it where it solves real gaps — access control, forensic logging, credential spoofing — while still relying on proven legacy tools for endpoint defense, SIEM analysis, and perimeter control. The result is a hybrid ecosystem with resilience baked in.
Whether you're a security leader planning next-gen infrastructure or a professional building your expertise, understanding blockchain is now a core cybersecurity requirement — not a niche skill. With 2025 data and real-world use cases proving its value, blockchain has shifted from buzzword to business-critical tool.