Top Cybersecurity Firms Specializing in Government & Public Sector
Cybersecurity in the government and public sector is not just about data protection—it’s about national security. From military intelligence leaks to critical infrastructure hacks, the consequences of failure are catastrophic. Public agencies face advanced threats from nation-state actors, insider risks, and supply chain vulnerabilities that require far more than commercial-grade solutions.
Unlike the private sector, government entities must meet strict mandates like FISMA, FedRAMP, and CMMC, while balancing transparency and budget constraints. This has led to a demand for specialized cybersecurity vendors who understand clearance requirements, rapid response coordination, and long-term risk mitigation. In this article, we highlight the firms that lead this space, the criteria that matter for government deployments, and why certifications like ACSMI’s Cybersecurity & Management Program are becoming central to meeting these challenges.
Unique Needs of Government Cybersecurity
Government cybersecurity demands go far beyond standard enterprise protection. Agencies must balance national security, regulatory mandates, and public trust while defending against constantly evolving digital threats. Unlike corporate networks, government systems are prime targets for espionage, disruption, and cyber warfare. What makes public-sector protection so complex is the convergence of compliance frameworks, geopolitical threat actors, and budgetary limitations—all of which require tailored solutions rather than off-the-shelf tools.
Data Sovereignty, FedRAMP, FISMA, etc.
Every government system must comply with strict standards for data localization, retention, and auditability. U.S. federal agencies, for example, must use FedRAMP-authorized cloud vendors to ensure continuous monitoring and secure configurations. Compliance with FISMA (Federal Information Security Management Act) ensures that information systems are properly assessed and authorized. At the state level, many governments follow NIST SP 800-53 controls and may implement their own sovereignty rules to prevent foreign data handling. These frameworks aren’t optional—they’re the legal backbone of any IT decision made in the public sector.
In addition, agencies must navigate conflicting mandates across domains. A health department may need to comply with HIPAA, while the same infrastructure must also meet CJIS (Criminal Justice Information Services) security policies. Interoperability between departments only works if the underlying cybersecurity stack meets all overlapping standards. This complexity creates a market for firms that not only know security tools, but can navigate bureaucratic red tape, documentation protocols, and inter-agency handoffs.
Nation-State Threats and Response
Government networks face persistent surveillance, zero-day attacks, and multi-vector campaigns from adversaries such as China, Russia, Iran, and North Korea. These aren’t random attacks—they’re coordinated, well-funded campaigns aimed at stealing sensitive defense data, destabilizing operations, or spreading misinformation.
Vendors working in this space must support classified environments, integrate with defense-grade SIEM systems, and participate in joint task forces for incident analysis. Many contracts now require cyber threat intelligence (CTI) fusion centers, where incoming data is correlated with active threat feeds to produce actionable insights in real time.
Beyond technology, response protocols must include crisis simulation, legal coordination under federal guidelines, and war-gamed incident playbooks. No firm can merely offer detection—they must build hardened, continuously evolving security ecosystems that survive real-world geopolitical pressure.
Evaluation Criteria for Public-Sector Providers
Choosing a cybersecurity provider for government deployment is not about brand recognition—it's about proven resilience under regulatory and operational pressure. Public agencies require partners who bring more than just tools: they must offer deep domain expertise, real-time response infrastructure, and verified compliance across layers of federal and state mandates.
Clearance, Incident Response, Zero Trust Models
The first and most non-negotiable factor is security clearance. Vendors serving federal contracts often need staff with Top Secret or Sensitive Compartmented Information (SCI) clearance, especially when working on defense, intelligence, or law enforcement systems. Without cleared personnel, no contract work is even possible in classified environments. Even state agencies handling critical infrastructure or justice systems may demand background-verified staffing levels and audit logs of internal access.
Incident response capabilities separate surface-level vendors from mission-critical providers. Public-sector systems operate in always-on, high-risk environments. Downtime is unacceptable. The best firms offer 24/7 Security Operations Centers (SOCs) with predefined incident containment and notification protocols, as well as active coordination with federal entities like the Cybersecurity and Infrastructure Security Agency (CISA). This includes tabletop exercises, breach readiness audits, and cyber drills embedded within long-term support contracts.
The third core pillar is the use of Zero Trust Architecture (ZTA). Government environments are too fragmented and too high-value to assume any internal trust. ZTA mandates user verification, device health checks, segmentation, and continuous reauthentication. Leading firms build their stack around NIST’s Zero Trust standards, enabling agencies to isolate breaches, limit lateral movement, and secure legacy systems without complete overhauls.
Firms that win public-sector contracts consistently prove these three layers—personnel clearance, rapid IR protocols, and ZTA implementation—not in marketing decks, but in operational continuity metrics. Agencies don’t just buy technology; they buy predictable survivability under cyber duress.
| Criterion | Requirement | Importance |
|---|---|---|
| Clearance Levels | Secret/Top Secret/SCI staff vetting | Required for classified contracts |
| Incident Response Readiness | 24/7 SOC, playbooks, crisis drills | Enables real-time containment |
| Zero Trust Architecture | Continuous verification, segmentation | Prevents lateral attacks |
| Audit Compliance | Documentation for NIST, HIPAA, CJIS | Required for funding and continuity |
| Tool Interoperability | Integration with SIEM/SOAR, CISA feeds | Improves visibility and response |
Top Cybersecurity Firms Serving Governments
When it comes to cybersecurity for government and public-sector entities, only a handful of firms consistently meet the highest thresholds for compliance, responsiveness, and geopolitical threat awareness. These organizations have demonstrated the ability to secure classified data, deploy at scale, and support long-term incident management contracts across federal, state, and international government bodies.
Booz Allen, Leidos, FireEye, Palo Alto
Booz Allen Hamilton is a longstanding defense and intelligence contractor with cybersecurity capabilities that include threat modeling, cyber warfare simulation, and offensive/defensive security engineering. Their services extend across DoD, DHS, and the intelligence community, making them one of the most trusted partners in defense-grade cybersecurity.
Leidos supports cybersecurity operations for the U.S. Navy, FAA, and several civil agencies. Their work includes SCADA protection, zero trust policy enforcement, and AI-enhanced threat detection. The firm’s background in mission-critical logistics and ISR (intelligence, surveillance, reconnaissance) makes it especially valuable in hybrid cyber-physical threat environments.
FireEye (now under the Trellix brand) remains a staple in public-sector response. Known for its elite Mandiant response teams, FireEye has been involved in uncovering major incidents like the SolarWinds breach, giving them unmatched insight into nation-state attack patterns. Their deployment model fits federal teams requiring fast forensics and APT tracking.
Palo Alto Networks, while often seen as a commercial firewall vendor, has successfully tailored their Cortex XSOAR and Prisma Cloud platforms for FedRAMP compliance and public-sector deployment. Their tools support agency-wide SIEM/SOAR integrations and identity segmentation under zero trust principles.
Each of these vendors is deeply embedded in the national security infrastructure—not as external vendors, but as operational extensions of cyber defense teams. They bring clearance-ready staff, pre-certified architectures, and a long track record of mission-aligned threat containment.
Federal vs State-Level Deployment
At the federal level, cybersecurity providers must meet classified data handling, inter-agency integration, and contract vetting through programs like GSA IT Schedule 70 or Alliant 2. Deployments often involve direct interface with DoD, NSA, or the Joint Cyber Command. The process includes months of due diligence, stakeholder training, and full-scope audits.
State-level governments present a different challenge. Budgets are lower, procurement is decentralized, and legacy systems are common. However, threats—from ransomware to misinformation attacks on voter databases—are no less real. Firms that win here tend to offer flexible SLAs, modular security tools, and hybrid cloud solutions that fit unique compliance overlays such as CJIS, HIPAA, or local IT governance acts.
Vendors that scale both federal and state operations effectively combine top-tier compliance frameworks with practical rollout strategies, proving their adaptability across jurisdictional and budgetary divides.
| Firm | Specialty Area | Public-Sector Examples |
|---|---|---|
| Booz Allen Hamilton | Defense, red teaming, cyber ops | DoD, DISA, IC contracts |
| Leidos | Hybrid threat defense, aviation, OT systems | FAA, Navy, civil agencies |
| FireEye (Trellix) | Nation-state response, incident forensics | SolarWinds, APT groups |
| Palo Alto Networks | FedRAMP-compliant firewalls, cloud security | DHS, federal cloud modernization |
| State Deployments | Budget-limited, hybrid tools | Localized with CJIS/HIPAA overlays |
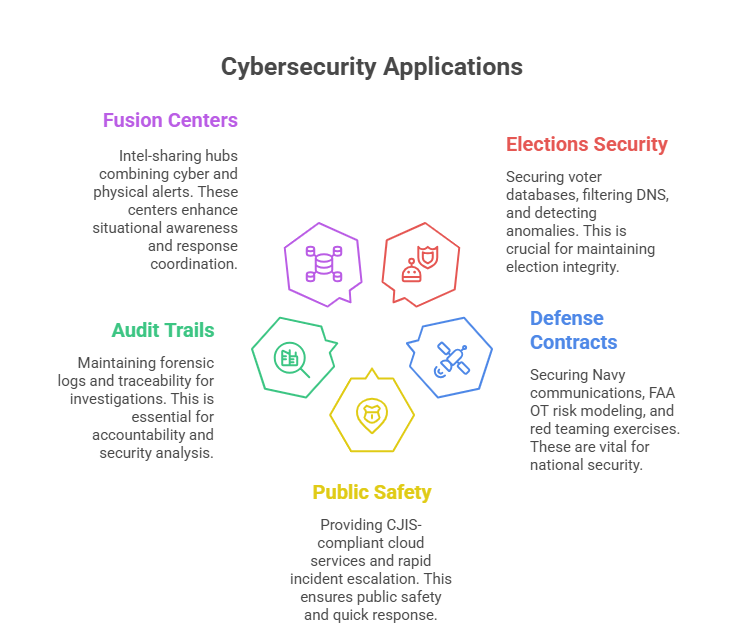
Use Cases: Elections, Defense, and Public Safety
Government cybersecurity isn’t theoretical—it’s tested in the heat of election interference, military operations, and public safety crises. These domains reveal how top firms function under real pressure and highlight the architectures, protocols, and partnerships that separate generic vendors from elite public-sector providers.
Examples of Real Contracts and Solutions
During the 2020 U.S. presidential election, multiple states partnered with DHS and private firms like FireEye and Palo Alto Networks to defend voter databases, detect disinformation campaigns, and secure ballot infrastructure. Their tools enabled real-time anomaly detection, DNS filtering, and forensic audit trails of suspicious login activity. These systems weren’t standalone—they were embedded into Secretary of State networks and monitored through 24/7 threat intelligence channels.
In the defense sector, Leidos plays a major role in securing U.S. Navy communication systems and air traffic control data through advanced encryption and zero-trust segmentation. Their contract with the FAA includes cyber risk modeling for operational technology (OT) layers, which historically had minimal cybersecurity protections. These projects represent mission-critical deployment, not just compliance-driven installs.
Another example is Booz Allen’s work with DISA (Defense Information Systems Agency). Their engineers help harden military-grade cloud services and deploy simulated red team exercises against DoD infrastructure. This ensures that detection, response, and recovery plans aren’t just compliant but battle-tested under active conditions.
Risk Mitigation Frameworks
Public-sector risk management doesn’t stop at software—it integrates legal, operational, and policy safeguards. Most top cybersecurity providers use frameworks like NIST RMF (Risk Management Framework), which mandates continuous monitoring, tailored security controls, and detailed system categorization based on impact level.
High-impact sectors like law enforcement or emergency response demand CJIS compliance, air-gapped incident communication layers, and predefined disaster escalation protocols. In public health agencies, risk management includes encrypting sensitive medical records under HIPAA, while balancing patient service uptime and interdepartmental coordination.
Some firms deploy automated vulnerability scanning tools tied to CMDB (Configuration Management Databases), which track system inventory across fragmented infrastructures. Others integrate with fusion centers that combine cyber threat intelligence with physical security alerts.
This layered approach—contractual clarity, regulatory alignment, and scenario-specific response playbooks—is what transforms generic vendors into long-term public-sector partners.
Global vs Local Cybersecurity Vendors
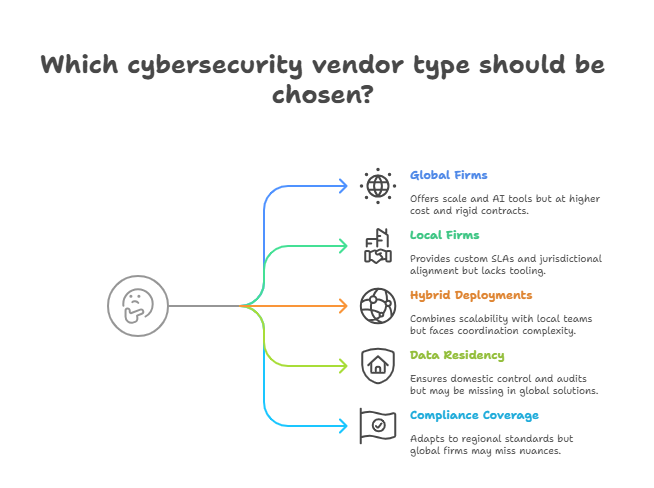
When public-sector agencies choose cybersecurity partners, the decision often boils down to a core tradeoff: global reach vs. local control. International firms bring scale, advanced tooling, and global threat intelligence, while domestic vendors offer jurisdictional compliance, cultural alignment, and on-the-ground agility. Both models have value—but the right fit depends on mission scope, legal boundaries, and resource availability.
Tradeoffs in Cost, Control, and Customization
Global cybersecurity firms—such as Palo Alto Networks, IBM Security, or Accenture—offer advanced platforms that integrate with multi-cloud environments, leverage AI-enhanced detection, and provide access to threat intelligence across hundreds of active engagements. Their economies of scale allow them to invest in emerging tech like quantum-resilient cryptography or predictive behavioral analytics. However, these benefits come with higher costs and a tendency to follow rigid service models. Customizing protocols for unique state or municipal needs can be slow or deprioritized.
Local and regional vendors, on the other hand, tend to offer more adaptable SLAs, quicker incident response times, and a clearer understanding of local legal frameworks. They’re better suited to implement state-specific compliance regimes, support localized training, and adjust solutions around municipal procurement cycles. These firms also ease concerns around data residency, especially where local sovereignty or anti-surveillance policies restrict cross-border data flow.
Control is another key dimension. With global vendors, agencies may lose visibility into source code audits, backend configurations, or the specific geographic location of cloud resources. Local vendors often offer greater transparency, including in-person audits, co-managed infrastructure models, and flexible policy enforcement that aligns with jurisdictional laws.
For governments operating across diverse regions—urban, rural, and tribal—a hybrid vendor model is becoming increasingly common. Agencies select a global firm for core infrastructure and overlay it with regional support from smaller MSPs (Managed Security Providers) that handle frontline implementation and daily management.
Public-sector cybersecurity is not one-size-fits-all. Understanding the strategic pros and cons of global vs. local providers ensures that agencies don’t overpay for scale or under-deliver on context.
Why ACSMI’s Cybersecurity Certification Fits This Niche
For professionals aiming to secure roles in public-sector cybersecurity—or for agencies seeking to upskill internal teams—the Advanced Cybersecurity & Management Certification offered by ACSMI is uniquely positioned. Unlike generalized programs, this certification directly addresses the compliance-heavy, incident-driven, and threat-intel-intensive nature of government cyber roles.
The course includes dedicated modules on:
Public-sector risk management, including detailed walkthroughs of NIST RMF, FedRAMP, FISMA, and CMMC frameworks.
Government-grade incident response playbooks, simulating election threats, military infrastructure breaches, and public health data leaks.
Audit preparation techniques tailored to agencies that undergo recurring compliance checks across CJIS, HIPAA, and state-mandated IT audits.
Additionally, learners gain exposure to role-based simulations where they must respond to multi-agency breaches, build a Zero Trust architecture blueprint for a government body, or oversee vulnerability scanning across an outdated municipal IT grid.
What makes ACSMI’s certification distinct is its alignment with real-world contracts and expectations. It’s not theoretical—it’s built for clearance-ready professionals, managed service teams, and analysts who want to function effectively inside high-pressure government environments.
Learn more about ACSMI’s Advanced Cybersecurity & Management Certification here and explore how its curriculum bridges the exact skills gap public agencies demand.
Frequently Asked Questions
-
All U.S. federal agencies must comply with FISMA (Federal Information Security Modernization Act), which mandates annual risk assessments, incident reporting protocols, and system categorization based on impact levels. Additionally, any agency using cloud services must utilize FedRAMP-authorized vendors with continuous monitoring in place. NIST frameworks, especially SP 800-53 and SP 800-171, are the core technical controls used to evaluate system readiness. Agencies working in defense must also comply with CMMC (Cybersecurity Maturity Model Certification). These standards are non-negotiable for contracts and audits, and failure to align can result in procurement ineligibility or budgetary penalties. Compliance is tied directly to public trust and national security readiness.
-
To work with classified data or national security assets, vendors must employ staff who possess active federal security clearance, typically at the Secret or Top Secret/SCI level. Clearance eligibility involves U.S. citizenship, a background investigation, and sponsorship from an existing government contract. Vendors also need to comply with facility clearance requirements under the National Industrial Security Program (NISP). For unclassified but sensitive projects, many agencies still demand documented personnel vetting, secure storage of records, and verified training in data handling protocols. Clearance requirements are often embedded directly into RFPs and RFIs for public-sector contracts.
-
Public-sector cybersecurity focuses on compliance, resilience, and trust under national scrutiny. Unlike private enterprise, which may prioritize profit protection, government cybersecurity must secure systems tied to public safety, military infrastructure, and democratic processes. Breaches don’t just cost money—they can disrupt services, compromise diplomatic efforts, or endanger lives. Additionally, government systems often rely on legacy platforms, requiring tailored solutions that balance modern zero-trust architecture with outdated infrastructure. Every move is audit-logged, and many decisions require congressional or legislative oversight. Security isn’t just technical—it’s political and procedural.
-
The most dominant firms in this space are Booz Allen Hamilton, Leidos, FireEye (now Trellix), and Palo Alto Networks. Booz Allen provides end-to-end cybersecurity across DoD and intelligence operations. Leidos supports aviation, defense, and civil agencies with hybrid cyber-physical protection. FireEye’s Mandiant division is known for nation-state threat detection and response, particularly in APT (Advanced Persistent Threat) tracking. Palo Alto’s platforms are now fully FedRAMP compliant, with strong deployments across DHS and cloud modernization efforts. These firms are awarded contracts based on clearance-ready staff, regulatory experience, and scalable response infrastructure.
-
Modern election security involves multi-layered defenses, including endpoint hardening, secure cloud storage, MFA authentication, and 24/7 network monitoring. Agencies like the Cybersecurity and Infrastructure Security Agency (CISA) collaborate with state election boards and vendors to deploy real-time monitoring tools. DNS filtering, anomaly detection software, and forensic-ready logging systems are installed on vote tabulation infrastructure. Additionally, cybersecurity tabletop exercises and disinformation simulations are performed months before election days. FedRAMP-certified tools are used for any cloud-based systems, and strict access policies ensure that only verified personnel can view sensitive voter data or analytics dashboards.
-
Zero Trust eliminates implicit trust within networks. Government agencies must now verify user identity, device posture, and access permissions before granting entry to any resource—regardless of whether the request originates inside or outside the firewall. Every user and endpoint is continuously authenticated, segmented, and monitored. Agencies adopt Zero Trust following NIST 800-207, which outlines architectures using microsegmentation, continuous diagnostics, and behavior analytics. Implementation is complex, especially for legacy systems, but crucial for preventing lateral movement during breaches. Many federal Zero Trust roadmaps also mandate integration with AI-based access control and least-privilege frameworks.
-
ACSMI’s Advanced Cybersecurity & Management Certification is tailored for professionals aiming to work in government and high-regulation industries. It includes training on FedRAMP, FISMA, HIPAA, CJIS, and CMMC standards, along with real-world modules simulating election breaches, intelligence system takeovers, and multi-agency crisis response. The program teaches vulnerability scanning, policy writing, risk scoring, and audit prep under frameworks like NIST RMF. Learners walk away with actionable skills for roles in SOC teams, compliance auditing, and cyber incident management. The course also helps professionals understand how to pass clearance-related background checks and prepare for government proposal work.
-
Yes, but it depends on budget, contract scope, and regulatory match. State-level governments often work with smaller, regionally embedded firms or resellers who customize national-grade tools like Palo Alto Cortex or Splunk SOAR for local infrastructure. Some larger states—like California or Texas—sign statewide procurement agreements with top-tier vendors for endpoint protection, cloud security, and identity access management. However, these vendors must align with state-specific compliance laws, such as California Consumer Privacy Act (CCPA) or unique procurement workflows. Vendors serving both levels need agility in SLAs, pricing, and modular toolsets to scale across multiple jurisdictions.
Conclusion
Cybersecurity in the public sector is not just an IT function—it’s a strategic defense priority. The stakes include protecting classified intelligence, public health records, and the very foundation of democratic systems. As cyberattacks become more targeted and state-sponsored, government agencies must partner with firms that bring proven expertise, clearance-ready teams, and frameworks built for accountability and resilience.
Whether it’s defending election infrastructure, securing military communications, or responding to real-time public safety threats, the firms mentioned in this guide consistently deliver at the highest level. And for professionals looking to break into this space, certifications like ACSMI’s Advanced Cybersecurity & Management Program offer the exact tools and frameworks needed to operate in high-stakes, compliance-heavy environments.
Choosing the right cybersecurity partner—or becoming one—starts with understanding what’s truly at risk. In the public sector, that means everything.
| Which cybersecurity provider model do you believe works best for government agencies? | |
|---|---|
| 🔘 | Global vendors with scale and threat intel (e.g., Palo Alto, IBM, Accenture) |
| 🔘 | Local/regional firms offering more customization and speed |
| 🔘 | A hybrid model that combines global tools with local deployment partners |