Phishing Attacks: Identification and Prevention Techniques
Phishing attacks are a core component of today’s cyber threat landscape, responsible for initiating over 90% of data breaches across industries. These attacks are not just sophisticated—they’re insidious, exploiting human trust and leveraging technological mimicry to deceive even the most vigilant users. Whether it’s a fraudulent email, a fake login page, or a cleverly disguised text message, phishing campaigns adapt rapidly to changing environments. Attackers employ a range of techniques from simple domain spoofing to advanced social engineering, exploiting our natural inclinations to trust familiar brands and authoritative communications. This digital deception extends beyond email to SMS (smishing), phone calls (vishing), and social platforms where personal information is increasingly targeted.
Recognizing and countering phishing attacks is not just about technical tools—it’s about understanding the mechanics of deception. Cybersecurity specialists estimate a single phishing incident costs businesses an average of $4.65 million, highlighting the financial and reputational risks involved. Organizations need to blend awareness training, layered detection systems, and proactive monitoring to build resilience. Meanwhile, individuals must learn to identify subtle red flags and understand how phishing exploits cognitive biases and emotional triggers. This guide provides a comprehensive breakdown of how phishing operates, its many disguises, and the cutting-edge detection and prevention strategies that can safeguard both corporate and personal digital assets.
Understanding Phishing Attacks
Phishing attacks are a persistent and evolving threat, targeting both technical vulnerabilities and human weaknesses. Understanding how phishing works is the first step in defending against it. This section explores the most common phishing techniques, how attackers exploit human psychology, and the typical scenarios that are used to trick victims. Armed with this knowledge, you can begin to recognize phishing red flags and develop proactive strategies for protection.
Types of Phishing Attacks
Phishing techniques evolve constantly, adapting to target vulnerabilities in systems and human behavior. Email phishing remains the most common type, involving deceptive messages that impersonate trusted entities. Spear phishing is a more targeted approach, focusing on specific individuals or organizations using personal data to craft convincing bait. Whaling targets high-level executives, leveraging authority to breach corporate systems. Beyond email, smishing (SMS phishing) and vishing (voice phishing) exploit communication channels to steal sensitive data. Attackers also use clone phishing, where a legitimate message is copied and modified with malicious links. Pharming attacks redirect website visitors to fraudulent sites without their knowledge. Understanding these attack types helps recognize tactics and implement targeted defenses. With every variant, attackers exploit a blend of trust and urgency to trick users into exposing confidential information.
How Phishing Exploits Human Psychology
Phishing attackers skillfully manipulate cognitive biases and emotional triggers. Urgency and fear are classic tools—messages threatening account lockouts or urgent security issues push recipients to act without scrutiny. Authority bias is another exploited factor; emails appearing from company executives or government agencies carry implicit trust. Reciprocity plays a role when users are offered fake incentives or rewards in exchange for personal data. Additionally, attackers exploit our natural tendency to trust familiar brands, often replicating logos, color schemes, and communication styles to enhance credibility. Recognizing these manipulations helps users stay vigilant. Training to spot urgent or authoritative requests, especially those pressuring immediate action or offering too-good-to-be-true deals, is crucial in defending against these psychological tricks.
Common Phishing Scenarios
Attackers exploit a wide range of scenarios to deliver phishing payloads. Fake password reset requests are a classic tactic, preying on users’ concern for account security. Invoice or payment fraud involves sending fraudulent billing notices that mimic legitimate vendors, tricking organizations into wiring funds to criminal accounts. Delivery scams target online shoppers, with messages about failed delivery attempts leading to phishing pages. Social media platforms are also exploited with friend request or message phishing, where compromised accounts send malicious links. Job offer scams lure job seekers with fake recruitment messages that capture sensitive data. Understanding these scenarios, combined with vigilance and verification of messages, is key to reducing phishing risks.
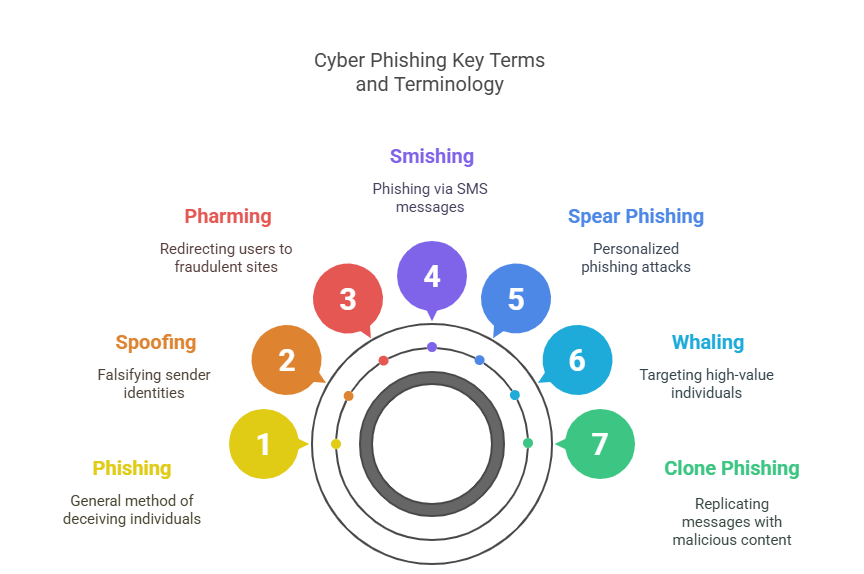
Key Terms and Terminology in Phishing
Understanding phishing requires a firm grasp of key terms that define its diverse techniques and constantly evolving strategies. From basic deception to complex, multi-layered attacks, phishing tactics rely on subtle yet distinct methods that exploit both technical vulnerabilities and human psychology. Recognizing these terms is crucial not only for identification but also for implementing targeted defenses and improving organizational resilience. With cybercriminals continuously refining their approaches, being familiar with essential concepts that provide individuals and organizations with the critical knowledge needed to stay ahead of phishing attempts and effectively protect digital assets.
Spoofing refers to falsifying sender identities, often by mimicking legitimate domains or email addresses to deceive recipients. For example, an email appearing from your bank but actually originating from a malicious domain is a classic spoofing tactic.
Pharming involves redirecting website visitors to fraudulent sites by exploiting vulnerabilities in DNS servers or local network settings. Victims believe they are entering credentials into a trusted site, while attackers harvest sensitive data.
Smishing targets mobile device users through SMS messages. A typical smishing attack might claim a failed delivery attempt, prompting recipients to click a malicious link.
Spear phishing takes a personalized approach, using publicly available information to craft convincing messages aimed at specific individuals or organizations. Unlike generic phishing campaigns, spear phishing exploits knowledge of the target’s role, contacts, or recent activities.
Whaling, specifically targets senior executives or high-value individuals with customized phishing lures, often impersonating legal or financial communications.
Clone phishing replicates a legitimate message previously received by the victim, replacing attachments or links with malicious versions.
These tactics often overlap and evolve, blending technical deception with psychological manipulation. Knowing the distinctions between smishing, spear phishing, and spoofing is crucial for building targeted defenses. Implementing phishing awareness training, multi-factor authentication, and advanced threat protection tools becomes more effective when users understand these terms and their real-world implications. This knowledge empowers individuals and organizations to detect threats early and prevent compromise, elevating overall cybersecurity resilience.
Detection Techniques and Warning Signs
Effective phishing detection relies on a keen eye for subtle cues and proactive security measures. This section dissects the tell-tale warning signs, from email anomalies to suspicious URLs, and reveals advanced email security protocols that significantly lower the risk of falling for phishing attacks.
Email Red Flags and Domain Spoofing
Phishing emails are designed to appear legitimate, but subtle red flags reveal their true intent. Look for misspellings, grammar errors, and unusual phrasing, which often signal hastily assembled scams. Be wary of messages that create urgency, such as “Your account will be locked unless you act now,” as these are designed to trigger impulsive responses. Domain spoofing is a common tactic, where attackers replicate a trusted domain with minor variations—such as substituting ‘0’ for ‘O’ or adding extra characters—to trick recipients. Always verify sender addresses, especially when sensitive actions like password resets or financial transactions are requested. Hovering over links to reveal their actual destination is a simple but effective tactic to spot spoofed domains and avoid clicking on malicious content.
URL Analysis and Link Inspection
Attackers embed malicious links in emails, websites, and social media to redirect users to phishing pages. Always check the URL structure for anomalies, such as extra characters, misspelled domain names, or unexpected subdomains. Look for HTTPS and valid security certificates, though even these can be faked. Suspiciously shortened URLs (e.g., bit.ly) should raise alarms, as they can conceal the true destination. Tools like VirusTotal or Google Safe Browsing can analyze links for potential threats before clicking. Inspect email content for mismatched URLs and verify links by typing them manually into your browser rather than clicking directly. By incorporating proactive URL verification, you significantly reduce the risk of falling victim to phishing.
Multi-Layered Email Security
Relying solely on user vigilance is insufficient against today’s sophisticated phishing campaigns. Implementing multi-layered email security—including DMARC, DKIM, and SPF protocols—helps authenticate sender identities and reduce spoofing risks. Advanced email gateways and filtering systems use machine learning and real-time threat intelligence to detect and block suspicious emails before they reach users. Sandboxing attachments and scanning embedded links for malicious payloads further strengthens defenses. Regularly updating spam filters and employing anti-phishing plugins or tools integrated with corporate email systems adds another protective layer. Combining technical safeguards with user training creates a robust defense against phishing attempts.
| Detection Technique | Key Points |
|---|---|
| Email Red Flags & Domain Spoofing | Look for misspellings, poor grammar, and urgent requests. Verify sender emails and hover over links to check URLs. Domain spoofing mimics legitimate domains with small changes. |
| URL Analysis & Link Inspection | Inspect links for odd characters, fake HTTPS, or suspicious short URLs. Use tools like VirusTotal or Safe Browsing. Manually type known URLs for safety. |
| Multi-Layered Email Security | Combine DMARC, DKIM, SPF to authenticate senders. Deploy advanced gateways, sandboxing, and updated spam filters. User training reinforces these defenses. |
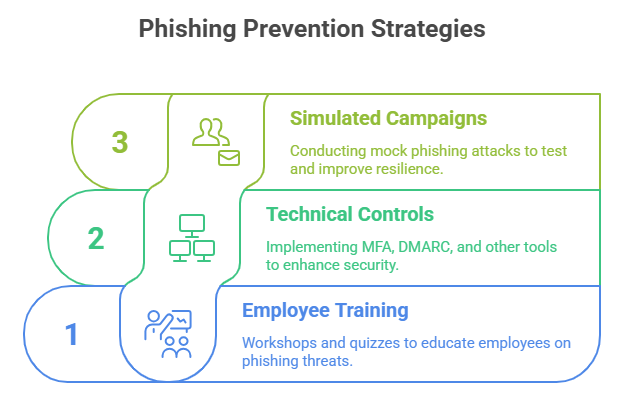
Prevention Strategies
Prevention is the ultimate shield against phishing. This section breaks down proven strategies that combine human vigilance and cutting-edge technology to create a multi-layered defense system. From empowering employees with the knowledge to recognize phishing attempts to deploying automated security tools and running simulated attacks, these methods ensure that phishing is stopped before it causes damage.
Employee Training and Awareness
No technological safeguard is as effective as a well-informed workforce. Employee training remains the frontline defense against phishing. Start with regular, mandatory workshops focusing on real-world phishing examples, emphasizing how attackers exploit human behavior. Interactive simulations and quizzes reinforce learning, highlighting common red flags such as urgent requests, misspellings, or unverified links. Employees should learn to hover over links, verify sender addresses, and avoid sharing sensitive data via email. Building a culture of vigilance—where staff feel empowered to report suspicious activity—reduces human error risks. Moreover, incorporating phishing awareness into onboarding for new hires ensures that all levels of the organization are prepared. Regular refreshers and updates on emerging phishing tactics keep knowledge current. Ultimately, well-trained employees form a human firewall that detects and mitigates phishing threats before they escalate.
Technical Controls and Anti-Phishing Tools
Relying solely on user awareness is not enough. Technical controls provide crucial, automated defenses against phishing. Implement multi-factor authentication (MFA) to make unauthorized access significantly harder, even if credentials are compromised. Email servers should enforce DMARC, DKIM, and SPF protocols to validate sender authenticity. Advanced threat protection tools use machine learning to detect and quarantine suspicious emails before delivery. Endpoint protection platforms (EPPs) scan devices for malware payloads embedded in phishing attempts. Secure web gateways filter malicious traffic and block access to known phishing domains. Browser extensions and plugins that inspect links in real time can provide additional protection for users. Finally, integrating these tools into a unified security ecosystem ensures that phishing defense is both proactive and adaptive to evolving threats.
Simulated Phishing Campaigns
Testing your organization’s phishing resilience requires simulated attacks. These controlled campaigns mimic real-world phishing attempts, providing a practical test of both human and technical defenses. By tracking click rates, reporting behaviors, and response times, organizations gain insight into their true preparedness levels. Simulated phishing should mirror current attack trends, including email spoofs, credential harvesting, and fake landing pages. Customized simulations can target specific departments with tailored scenarios, enhancing realism and engagement. After each campaign, conduct thorough debriefs to review performance, identify weaknesses, and deliver targeted retraining where needed. Repetition is key—quarterly or monthly simulations maintain high vigilance and adaptability. Simulations also demonstrate to stakeholders that the organization takes phishing threats seriously, bolstering overall cybersecurity credibility.
How the Advanced Cybersecurity & Management Certification Course by ACSMI Strengthens Your Phishing Defense Skills
The Advanced Cybersecurity & Management Certification Course by ACSMI transforms phishing defense from passive awareness into actionable expertise. This comprehensive program immerses participants in real-world scenarios, replicating the complex tactics used by cybercriminals. By simulating sophisticated phishing campaigns, learners develop the ability to dissect malicious strategies, recognize subtle red flags, and identify deceptive communication cues. The course’s hands-on modules cover critical areas such as email red flags, URL analysis, and domain spoofing detection, sharpening participants’ ability to respond effectively.
Beyond identification, the course equips learners with advanced technical skills, including configuring endpoint protection platforms (EPPs), deploying sandbox environments, and integrating threat intelligence systems for proactive defense. Participants become adept at using these tools to block and neutralize phishing attempts before damage can occur. The program’s focus on multi-layered security strategies ensures that participants don’t just react—they actively prevent phishing attacks through a blend of technical acumen and behavioral awareness.
Graduates of the Advanced Cybersecurity & Management Certification Course by ACSMI are equipped to lead their organizations’ phishing defense efforts. They gain the authority to design simulated phishing campaigns, interpret results, and implement targeted training programs to strengthen the overall security posture. This leadership capacity creates a culture of resilience, ensuring continuous improvement in phishing detection and response. With the Advanced Cybersecurity & Management Certification Course by ACSMI, participants gain not only in-demand cybersecurity skills but also the confidence to safeguard both their organizations and their careers from the evolving landscape of phishing threats.
Conclusion
Phishing attacks continue to be one of the most prevalent and damaging threats in the digital world. However, with the right combination of awareness, technical safeguards, and proactive training, both individuals and organizations can effectively mitigate these risks. This comprehensive guide has outlined the key tactics used by phishers, the red flags to watch for, and the multi-layered defenses needed to protect against them. It has also highlighted how the Advanced Cybersecurity & Management Certification Course by ACSMI equips professionals with actionable skills to strengthen their organization’s cybersecurity posture.
To stay ahead of evolving phishing tactics, continuous vigilance and adaptive strategies are essential. Regular training, simulated attacks, and technical controls must become part of your organization’s standard practices. When combined with the expertise gained from structured programs like ACSMI’s certification, these measures empower you to build a resilient and proactive cybersecurity culture. Don’t wait for a phishing attack to strike; take action now to protect your data, finances, and reputation.
Frequently Asked Questions
-
Phishing is a form of cyberattack where malicious actors impersonate legitimate sources to deceive victims into revealing sensitive information such as passwords, credit card numbers, or company data. Phishing emails, text messages, and calls often appear trustworthy, exploiting human psychology to bypass security systems. The danger lies in its subtlety—successful phishing attacks can lead to financial loss, identity theft, data breaches, and reputational damage. Organizations may suffer compliance failures and legal liabilities if customer data is compromised. Recognizing the signs of phishing and implementing proactive defenses, such as anti-phishing tools and user training, is essential to mitigate these risks.
-
Phishing emails often contain tell-tale signs: poor grammar, spelling errors, and urgent requests for personal information. Hover over links without clicking to inspect the actual URL—phishing links often mimic legitimate domains with slight alterations. Unexpected attachments or requests for passwords are red flags. Emails that create urgency, such as “Your account will be deactivated,” are designed to trigger hasty action. Always verify the sender’s email address carefully and, if in doubt, contact the company directly through official channels. Developing the habit of inspecting and questioning suspicious emails is a key defense strategy.
-
Organizations use a variety of anti-phishing technologies, including email filters, multi-factor authentication (MFA), and endpoint protection platforms (EPPs). These tools analyze incoming messages for suspicious content, block known phishing domains, and monitor user behavior for signs of compromise. Additionally, browser extensions and plugins can inspect links in real time. DNS filtering and secure web gateways prevent users from accessing malicious sites. Combining technical defenses with employee awareness creates a robust security framework that detects and neutralizes phishing attempts before damage occurs.
-
Simulated phishing campaigns mimic real-world attacks, providing organizations with insight into user vulnerabilities and response patterns. By analyzing metrics such as click rates and reporting rates, security teams can identify weaknesses and target training accordingly. These exercises keep employees alert, reinforcing lessons on spotting suspicious emails and links. Regular simulations help build a culture of vigilance, ensuring that phishing defenses remain adaptive and effective. They also demonstrate an organization’s commitment to cybersecurity, which can improve compliance and stakeholder confidence.
-
Phishing attackers research their targets using publicly available information from social media, corporate websites, and online directories. This data enables them to craft messages that appear personalized and legitimate. Techniques like domain spoofing, brand impersonation, and email formatting replication enhance credibility. Messages often exploit emotional triggers such as urgency, fear, or curiosity to bypass rational scrutiny. Understanding these techniques helps individuals recognize and resist phishing attempts by carefully verifying unexpected requests and inspecting communication sources.
-
While technical controls like anti-phishing filters, email authentication protocols (DMARC, DKIM, SPF), and threat detection tools are essential, they are not foolproof. Human error remains a significant vulnerability, especially when attackers exploit psychological manipulation. A comprehensive approach combines technical defenses with continuous employee training, awareness programs, and simulated phishing tests. This multi-layered strategy ensures that even if technical barriers are breached, vigilant employees can detect and report suspicious activity before damage occurs.
-
Social engineering is the foundation of phishing. It leverages human emotions—such as fear, greed, urgency, and trust—to trick users into revealing confidential information. Attackers may pose as IT support, financial institutions, or even executives to exploit authority bias. Pretexting, baiting, and tailgating are common social engineering tactics used in phishing campaigns. Recognizing these psychological triggers and questioning suspicious requests are crucial steps in preventing social engineering-based phishing attacks.
-
Begin with mandatory training sessions using real-world examples to highlight common phishing tactics. Incorporate interactive simulations and quizzes to test comprehension. Use simulated phishing campaigns to gauge employee response and provide targeted retraining where needed. Foster an environment where employees feel comfortable reporting suspicious emails without fear of reprimand. Ongoing education ensures that employees remain alert to evolving phishing tactics, creating a human firewall that reinforces technical security measures.