State of Ransomware 2025: Original Threat Analysis & Industry Impact
Ransomware in 2025 has evolved into a precision-engineered digital threat, no longer relying solely on brute force or basic phishing. Instead, cybercriminals are leveraging AI-powered payload delivery, real-time reconnaissance, and geopolitical leverage to cripple critical infrastructure and extort multi-million-dollar payments. With ransomware groups operating like organized businesses—complete with customer service and affiliate programs—the global threat surface has expanded beyond enterprise walls into supply chains, small businesses, and remote cyber work ecosystems.
This year's ransomware incidents haven’t just escalated in frequency—they’ve grown in targeting intelligence, payout size, and sector-specific disruption, particularly in healthcare, education, and manufacturing. As governments tighten regulations and insurers shift coverage policies, cybersecurity readiness is no longer optional. The need for advanced ransomware defense training, like that offered in the ACSMI Cybersecurity & Management Certification, has become urgent. In this report, we break down real-time 2025 data, attack models, and prevention strategies—not just to inform, but to equip professionals with the knowledge to respond swiftly and decisively.
Ransomware Trends in 2025
New Tactics and Targets
Ransomware operators in 2025 have abandoned wide-net campaigns in favor of surgical, data-driven targeting. Instead of phishing thousands of employees, attackers now infiltrate supply chain vendors, managed service providers, and cloud platforms that offer access to multiple downstream victims. These attacks are often coordinated after weeks of internal reconnaissance, making detection harder and mitigation costlier.
One major evolution is data exfiltration before encryption, allowing criminals to double-extort victims by threatening public leaks. Many 2025 attackers skip the encryption phase entirely—especially when attacking legal firms, biotech companies, or political groups—choosing instead to auction stolen intellectual property on darknet forums.
New targets also include CI/CD pipelines, DevOps environments, and AI model training clusters, which are vulnerable due to lax IAM practices and interdependent credentials. Critical sectors like utilities and logistics remain high-risk, but attackers are now also exploiting soft underbellies—K–12 school districts, local libraries, and mid-sized manufacturing hubs.
These tactics reflect a maturity in adversary behavior: less brute force, more intelligence-led infiltration. The result is higher dwell time, longer ransom negotiations, and greater long-term impact on brand equity and operational continuity.
Global Volume and Breach Statistics
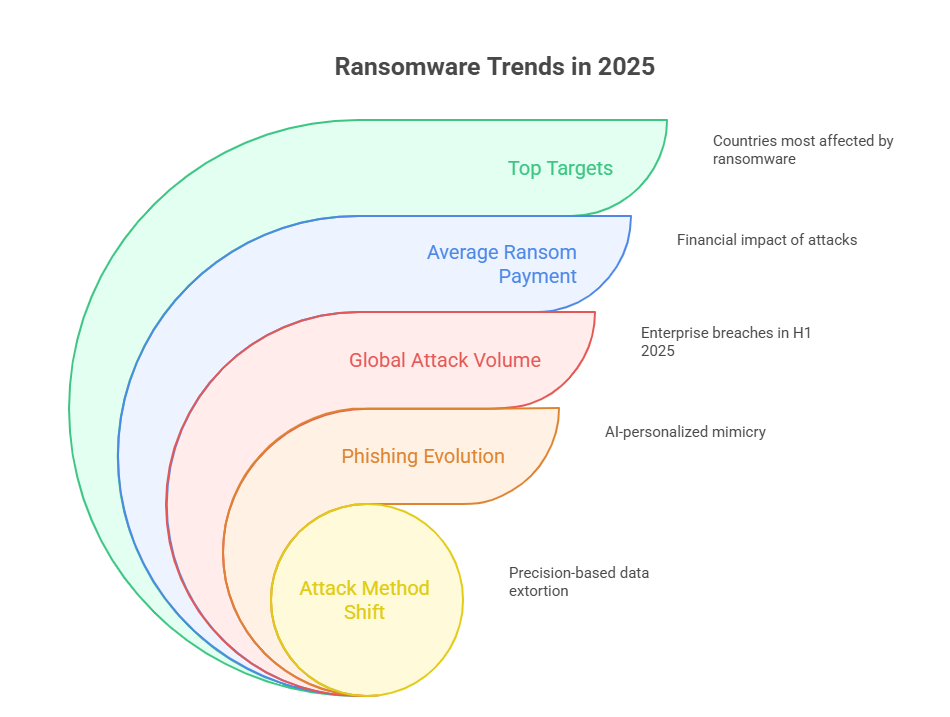
Ransomware volume has risen 67% globally in Q1 and Q2 of 2025, with over 4,200 confirmed enterprise breaches, according to telemetry from cybersecurity firms CrowdStrike and Palo Alto Networks. However, the real count is likely much higher due to non-disclosure clauses and regulatory lag in breach reporting.
The average ransom payment now exceeds $1.7 million, up from $812,000 in 2023, driven largely by cryptocurrency normalization and AI-driven negotiation bots used by ransomware groups. In sectors like pharma and fintech, payments frequently exceed $10 million—especially where intellectual property is involved.
The top five countries targeted remain the United States, Germany, India, the UK, and Canada, but regional hotspots are emerging in Latin America and Southeast Asia due to weaker data protection laws and increasing cloud adoption without corresponding security measures.
Ransomware-as-a-Service (RaaS) kits are now being used in 73% of attacks, making sophisticated tools accessible to low-skill threat actors. These kits offer everything from zero-day exploits to payment dashboards, and most include multi-lingual support and uptime SLAs for criminal affiliates.
Combined, these trends indicate not only volume but technical acceleration and market-wide democratization of ransomware capabilities.
Industry-Specific Impacts
Healthcare, Education, Government
In 2025, ransomware attacks on healthcare have reached critical severity. Hospitals and diagnostics labs are targeted for their non-disruptable patient services—making them more likely to pay quickly. Electronic health records (EHRs), MRI systems, and even internet-connected pacemakers have been leveraged as pressure points. In Q2 alone, over 130 U.S. medical facilities reported operational shutdowns linked to ransomware, with recovery costs averaging $4.6 million per event.
The education sector, particularly K–12 districts and universities, has also seen an uptick. Attackers exploit outdated systems, poor access controls, and budget constraints. In one major case, over 30,000 student records were auctioned after a state college refused to pay. Ransom demands in education now average $980,000, but the downstream impact—data privacy lawsuits, FERPA violations, and reputational fallout—often far exceeds the initial demand.
Government agencies, especially at the municipal and state level, are now prime targets for politically motivated or financially driven actors. Attackers are exploiting voting systems, licensing portals, and emergency service networks. These systems often run legacy software, lack multi-factor authentication, and require inter-agency coordination for remediation—a delay attackers exploit for higher leverage.
SMEs vs. Large Corporations
Small and medium-sized enterprises (SMEs) were once spared due to limited payout potential. In 2025, that assumption no longer holds. SMEs are being hit through vendor credential theft, weak firewall configurations, and undersecured SaaS platforms. Because most lack a dedicated security team, attackers often gain full domain control within hours. Ransom demands for SMEs typically range from $150,000 to $500,000, yet 40% of affected businesses never recover.
In contrast, large enterprises face sophisticated multi-stage attacks that often involve credential stuffing, lateral movement through hybrid networks, and coordinated extortion of board-level executives. These organizations are not just paying for decryption keys—they’re paying for silence, reputation containment, and in some cases, non-reattack guarantees.
Despite higher IT budgets, many corporations still fail due to poor segmentation, inconsistent backups, and untrained staff. The reality: even companies with mature SOCs are vulnerable if they lack ransomware-specific playbooks and cross-functional crisis drills. Without simulation-based training, even the best defenses can crumble under coordinated pressure.
Major Attacks of the Year
Case Study 1: Sector Hit + Ransom Demands
In March 2025, a pharmaceutical manufacturing firm in Switzerland suffered a catastrophic ransomware attack that halted production for over 17 days. The attackers—identified as a splinter group from the Black Basta ransomware gang—used compromised VPN credentials from a third-party logistics provider to access the firm’s internal network. Once inside, they deployed a custom loader that disabled endpoint detection and launched a double-extortion payload, encrypting both on-prem servers and connected Azure backups.
The ransom demand: $15.2 million in Monero, with a 120-hour deadline before intellectual property—including early-stage drug formulations and clinical trial data—would be leaked online. The company refused to pay, citing Swiss regulatory restrictions on terrorist funding. As a result, over 9TB of data were dumped on a darknet portal, leading to lawsuits from research partners and a 30% stock value drop in under two weeks.
This case revealed how supply chain vulnerabilities, when combined with siloed cyber response protocols, allow even advanced companies to fall victim to high-impact breaches.
Case Study 2: Defense Strategy Breakdown
In July 2025, a U.S. electric utility cooperative experienced a ransomware breach that exposed critical SCADA controls and forced power outages across three counties. Despite having cyber insurance, EDR tools, and SOC monitoring, the breach succeeded due to a misconfigured firewall rule and the absence of real-time lateral movement detection.
The attackers, affiliated with the Royal Ransomware syndicate, initially gained access via a phishing email to a facilities contractor, who used a shared corporate credential to log in remotely. Once inside, they launched a living-off-the-land (LOTL) attack using native Windows tools to bypass security alerts and encrypt control system data.
The firm’s disaster recovery strategy failed in execution—backups hadn’t been tested in six months, and the incident response plan required approvals from four departments, causing a 16-hour delay in containment. The ransom was paid—$3.1 million—but forensic reports revealed no DLP rules, no segmented authentication, and incomplete Zero Trust enforcement across the ICS environment.
This breach underscores a harsh truth: having tools is not the same as operational resilience. Without drilled, cross-siloed ransomware simulations, even highly regulated industries remain fragile.
| Case Study | Target Sector | Attack Method | Ransom Demand | Impact |
|---|---|---|---|---|
| Case Study 1 Swiss Pharmaceutical Firm |
Biotech / Pharma | Compromised VPN via third-party vendor; AI-enhanced payload | $15.2 million in Monero |
- 9TB of clinical and R&D data leaked - Legal action from partners - 30% drop in stock value within 2 weeks |
| Case Study 2 U.S. Utility Cooperative |
Critical Infrastructure / Energy | Phishing + misconfigured firewall + lateral movement using LOTL | $3.1 million (paid) |
- Power outage across 3 counties - Backup failure; 16-hour delay in containment - Revealed gaps in Zero Trust enforcement and SOC response |
Evolving Tools Used by Ransomware Actors
AI-Enhanced Phishing and Payload Delivery
In 2025, artificial intelligence is now core to ransomware delivery, both in crafting phishing lures and in executing post-exploit actions. Threat actors are deploying LLM-powered bots to generate hyper-personalized phishing emails, often indistinguishable from internal HR notices, supplier invoices, or executive directives. These emails bypass traditional spam filters by mimicking internal tone, formatting, and metadata—boosting click-through rates by 68% over traditional phishing.
Once the target clicks, payloads are not static executables. Instead, attackers deploy modular malware built using AI-assisted scripts that detect system configuration in real time and download only the most effective ransomware variant. These payloads auto-adjust based on OS, EDR presence, and cloud instance status.
Even the encryption process is optimized—AI is used to prioritize file types, skipping redundant or low-value assets to maximize pressure on the victim. In some attacks, AI-driven payloads detect backup drives or syncing tools like OneDrive and Box, encrypting or disabling them before the user notices.
This automation reduces attack dwell time and increases scale: a single AI-powered campaign can compromise hundreds of endpoints across multiple organizations in under 72 hours. Defense now requires AI vs. AI strategy, where endpoint tools and analysts must match threat intelligence in real time.
Malware-as-a-Service Growth
The ransomware ecosystem has fully matured into a SaaS-style economy in 2025. Malware-as-a-Service (MaaS) platforms now offer turnkey kits for as low as $500/month, complete with web dashboards, multi-vector payload options, and even 24/7 technical support for affiliates.
These kits are driving the explosion of non-technical attackers, many of whom have zero coding experience. Through affiliate programs, platform developers take a cut—usually 20% to 30%—from each successful extortion, incentivizing continuous updates, exploit integration, and new delivery methods. The most successful MaaS groups even offer “no attack, no pay” guarantees, minimizing entry risk for novice criminals.
Notably, many platforms now integrate one-click payload builders that allow users to select the ransomware variant, delivery method (e.g., phishing, RDP brute-force, webshell injection), and post-encryption instructions. Some even include legal disclaimers or terms of service written to mimic legitimate enterprise software.
This industrialization is why MaaS is now linked to over 70% of ransomware incidents globally. Defending against it requires more than endpoint protection—it demands proactive threat hunting, threat intel feeds, and human-in-the-loop review to detect subtle, obfuscated payloads before activation.
| Tool/Technique | Description | Impact on Defenders |
|---|---|---|
| AI-Powered Phishing | LLM-generated emails mimic internal communications to trick users with near-perfect precision. Messages reflect tone, structure, and metadata of actual corporate correspondence. |
- Bypasses traditional spam filters - Increases click-through rates by up to 68% - Triggers credential theft and initial access |
| Modular Malware | Payloads are broken into dynamic components that adjust based on the target system’s OS, cloud instance, or endpoint protection status. |
- Avoids detection by adapting in real time - Encrypts high-value data first - Targets backup systems before user awareness |
| Malware-as-a-Service (MaaS) | Turnkey ransomware platforms with dashboards, affiliate payouts, payload builders, and tech support. Now accessible to low-skill attackers globally. |
- Drives volume of attacks across all sectors - Allows criminals to scale operations quickly - Includes SLAs and multilingual support |
| Living off the Land (LOTL) | Use of native admin tools like PowerShell, WMI, and PsExec to move laterally and exfiltrate data without deploying obvious malware. |
- Evades traditional antivirus and EDR tools - Leaves minimal signature footprints - Delays detection and containment |
| Zero-Day Exploits in MaaS Kits | Pre-packaged, unpatched vulnerabilities embedded into MaaS payloads, often targeting VPNs, cloud access brokers, or identity federation tools. |
- Allows deep system penetration - Enables ransomware before patch cycles - Often undetectable until after encryption |
Corporate Readiness and Risk Management
Incident Response Timelines
In 2025, incident response speed is no longer a luxury—it's the dividing line between containment and catastrophe. The average ransomware dwell time before detection is now 11.2 days, a drop from 14.7 in 2023, but response timelines remain sluggish. Most companies still take 24–72 hours to initiate coordinated containment, a delay that enables widespread encryption and data exfiltration.
The most resilient organizations initiate containment within 90 minutes, followed by full internal escalation by the 3-hour mark. These timelines are possible only when the organization has:
Pre-approved playbooks, avoiding delays caused by siloed approval chains.
Automated alert correlation that detects behavior anomalies, not just signatures.
Ransomware-specific tabletop exercises that cross legal, IT, PR, and leadership roles.
A key failure point? Many firms still rely on generalist IT teams for incident triage. Without a dedicated threat containment unit, initial alerts are deprioritized as false positives. Worse, password resets and endpoint reboots are mistakenly executed before forensics teams capture volatile memory, corrupting evidence and complicating root-cause analysis.
The hard truth is that containment success in 2025 requires minute-level precision, tiered escalation, and ransomware-first incident drills practiced quarterly.
Cyber Insurance Trends
Cyber insurance in 2025 has shifted dramatically—coverage is now conditional, premium costs have spiked by over 35%, and underwriting scrutiny has intensified. Most insurers now require:
Evidence of multi-factor authentication across all endpoints and applications.
Quarterly penetration tests and backup validation reports.
A clearly defined Zero Trust architecture with identity segmentation and microperimeter controls.
Insurers are also capping ransom payouts, especially when payment violates OFAC or anti-terrorism sanctions. In 2025, policies often include co-pay clauses or require insureds to shoulder initial costs for data recovery, PR crisis teams, and notification services.
Organizations without a formal ransomware response plan or training logs may be denied claims altogether. This has led to a surge in insurance readiness audits, which assess an enterprise’s actual recovery maturity—not just the tools they own.
Interestingly, a new trend is emerging: insurance-integrated incident response vendors. These third parties are now embedded in policy terms and are granted automatic breach access rights upon detection. While this ensures swift action, it raises data control and confidentiality risks, particularly in regulated sectors.
In short, cyber insurance is no longer a safety net—it’s a conditional contract tightly aligned to proven readiness metrics.
Why ACSMI Certification Equips You for Ransomware Defense
Real-World Ransomware Simulation Modules
The ACSMI Cybersecurity & Management Certification is purpose-built for modern ransomware defense—not just with theory, but deep practical immersion. One of its core components is a live ransomware simulation lab, designed to train learners in end-to-end breach containment, recovery, and reporting. These are not textbook exercises—they mirror real 2025 attack vectors, including multi-vector entry points, AI-generated phishing, and RaaS payloads.
Trainees are placed into simulated security teams where they must:
Analyze threat telemetry and triage alerts in real time
Navigate containment decisions under strict time pressure
Execute forensics capture, backup restoration, and executive briefings
Coordinate legal, compliance, and external communications post-breach
Each simulation is updated quarterly to reflect the latest ransomware strains, including payloads used by groups like LockBit, Clop, and Royal. Participants gain hands-on experience with endpoint protection tools, SIEMs, and playbook automation systems under active attack conditions.
The emphasis isn’t just on tools—but decision-making. Learners build reflexes for cross-silo collaboration, attack surface reduction, and multi-step recovery. By the end of the course, participants are able to design, test, and lead ransomware incident responses across hybrid infrastructures.
This approach turns passive learners into certified cybersecurity operators—ready to prevent, detect, and outmaneuver evolving threats.
Ready to Elevate Your Cybersecurity Career?
The ACSMI Cybersecurity & Management Certification is engineered for professionals who need proactive ransomware defense skills in the field—not after the fact. Whether you're a security analyst, IT manager, compliance officer, or executive, this program delivers modular, CPD-accredited lessons backed by 379 hands-on labs, 170+ hours of expert instruction, and real-world threat scenarios.
Build live response playbooks
Execute post-breach recovery workflows
Master AI-powered threat detection tools
Pass your certification exam with role-specific prep
This is more than training—it’s a defensive architecture lab that mirrors the exact environments under attack today. Participants walk away with not just a credential, but a ready-to-execute ransomware response system.
Frequently Asked Questions
-
The biggest shift in 2025 is the move from mass encryption to surgical data extortion. Many ransomware actors now skip file encryption entirely and focus on stealing and threatening to leak sensitive data, especially from sectors like healthcare, legal, and finance. Attacks are increasingly powered by AI-driven phishing campaigns, and the use of pre-ransom reconnaissance allows threat actors to tailor demands and pressure points. Also notable is the rise of initial access brokers, who sell verified entry points to specialized ransomware crews. This division of labor has made attacks faster, harder to detect, and more devastating in legal and financial consequences.
-
Both healthcare and education have high-stakes data, minimal downtime tolerance, and historically underfunded cybersecurity infrastructure. In 2025, attackers target Electronic Health Records (EHRs), PACS imaging systems, and student databases not just for ransom but also for identity fraud and black-market resale. These sectors also tend to rely on legacy software, lack real-time detection tools, and often delay patch cycles due to operational needs. With regulatory risks increasing—HIPAA, FERPA, GDPR—organizations in these sectors often pay to avoid public exposure. That makes them prime targets. Attackers know that minimal breach delay leads to maximum payout leverage in these industries.
-
The first 90 minutes post-detection are the most critical. After that, the attacker often has full control of the domain or exfiltrated data. While the average dwell time (from initial access to discovery) is about 11 days, containment must occur within hours—not days—to reduce damage. Best-practice organizations trigger their containment playbooks within 3 hours, execute identity lockdowns, and begin forensic triage immediately. However, many still wait 24–48 hours due to internal confusion, missing playbooks, or untrained response teams. In ransomware, delays directly translate to higher ransom demands, operational shutdowns, and increased legal exposure.
-
Ransomware actors in 2025 are using AI-enhanced payloads, modular loaders, and multi-vector initial access techniques. Tools like Cobalt Strike, Brute Ratel, and AI-optimized phishing platforms are standard. They bypass EDR by exploiting legitimate admin tools like PowerShell and WMIC. Many defenders still rely on signature-based detection, which fails against customized, polymorphic code delivered through Malware-as-a-Service kits. Additionally, attackers use dynamic DNS, proxy evasion, and time-triggered payloads to slip through SOC nets. The most dangerous blind spot for defenders remains lack of lateral movement detection and failure to monitor privileged account activity in real time.
-
Yes, but coverage is now conditional and limited. Insurers in 2025 demand proof of proactive controls, such as MFA, Zero Trust architecture, tested backups, and ransomware-specific playbooks. Many carriers have reduced maximum payouts or added co-insurance clauses that require businesses to cover part of the damages. Some policies exclude ransom payments entirely, especially if the attack involves entities sanctioned by OFAC. A growing trend is incident response bundling, where insurers provide their own breach response firms. This speeds up action but may compromise control over evidence, reporting, and post-breach decisions. Companies must be “insurance-ready,” not just insured.
-
The ACSMI Cybersecurity & Management Certification trains professionals in real-world ransomware defense. It includes hands-on breach simulations, live forensics, data recovery, legal response, and leadership coordination. Modules cover AI-driven phishing detection, endpoint lockdown, and Zero Trust design. Unlike generalist cybersecurity programs, this certification is built specifically for today’s ransomware threat landscape. Participants learn to lead cross-departmental containment, manage insurance and compliance workflows, and harden hybrid cloud environments against RaaS tactics. Graduates walk away with a ready-to-deploy incident response strategy, tested under pressure. It’s ideal for SOC analysts, IT leads, and compliance managers seeking immediate, field-ready expertise.
-
In 2025, construction firms, logistics providers, media publishers, and research labs have emerged as high-risk targets. These industries often run complex, interconnected systems, rely on multiple vendors, and handle valuable time-sensitive data—but without dedicated cybersecurity leadership. Attackers exploit weak vendor authentication, shared credentials, and outdated file transfer tools like FTP. For example, research labs are hit for IP theft, construction firms for scheduling disruptions, and logistics companies for route and delivery manipulation. The common denominator is high operational urgency and low security maturity, which makes these organizations low-hanging fruit for attackers seeking fast payouts.
Final Thoughts
Ransomware in 2025 is no longer a chaotic threat—it’s an organized, evolving business model. From AI-driven phishing to industrialized Malware-as-a-Service kits, attackers now operate with speed, precision, and devastating impact across industries and geographies. Defenders can’t rely on outdated playbooks or basic endpoint tools. What’s required is proactive, scenario-based preparation, cross-functional response coordination, and constant upskilling.
The organizations that survive and recover fastest are the ones that invest in their people, not just their software. The ACSMI Cybersecurity & Management Certification offers that investment—training professionals not only to react, but to anticipate, contain, and outmaneuver even the most advanced ransomware threats. The landscape will keep shifting. Your defense strategy must evolve faster.