Botnets: Structure and Disruption Methods
Botnets have transformed from niche cyber tools into dominant forces reshaping the landscape of digital security. Initially simple clusters of infected devices, they now exhibit complex structures capable of overwhelming even robust defense systems. These clandestine networks serve as the backbone for diverse malicious operations, from DDoS attacks to financial theft, and their rapid evolution poses persistent threats to both enterprises and individuals. Unlike traditional malware, botnets are designed for scale and longevity, adapting swiftly to detection methods. Their architectures—ranging from centralized command models to P2P frameworks—demonstrate a relentless capacity for disruption. The global proliferation of IoT devices has further fueled this menace, offering cybercriminals an unprecedented attack surface.
What makes botnets especially insidious is their invisibility. Many infected systems remain unaware of their role in a larger network, while the command and control structures deftly mask the true origin of instructions. This capability to blend into normal traffic flows complicates detection and mitigation efforts. The financial impact on organizations is staggering, and the long-term reputational damage extends far beyond immediate losses. Understanding the structural complexity and evolving tactics of botnets is crucial for cybersecurity professionals aiming to build resilient, proactive defenses.
What Are Botnets and How Do They Operate?
Definition, Origin, and Characteristics
Botnets are decentralized networks of compromised devices, covertly controlled by cybercriminals for malicious purposes. The term derives from "robot" and "network," highlighting their autonomous, distributed nature. Originally, botnets emerged in the early 2000s, targeting home computers to propagate spam and basic DDoS attacks. Over time, their complexity has grown, encompassing advanced tactics such as credential stuffing, click fraud, and ransomware deployment.
Modern botnets exploit a diverse array of devices, from personal computers and smartphones to IoT devices like smart home systems and industrial machinery. Their resilience stems from adaptive coding, with malware that self-updates, ensuring sustained functionality even amid partial takedowns. Central to their operation is the concept of persistence—infected devices, often called "zombies," remain compromised for extended periods, enabling botmasters to orchestrate large-scale attacks with minimal intervention.
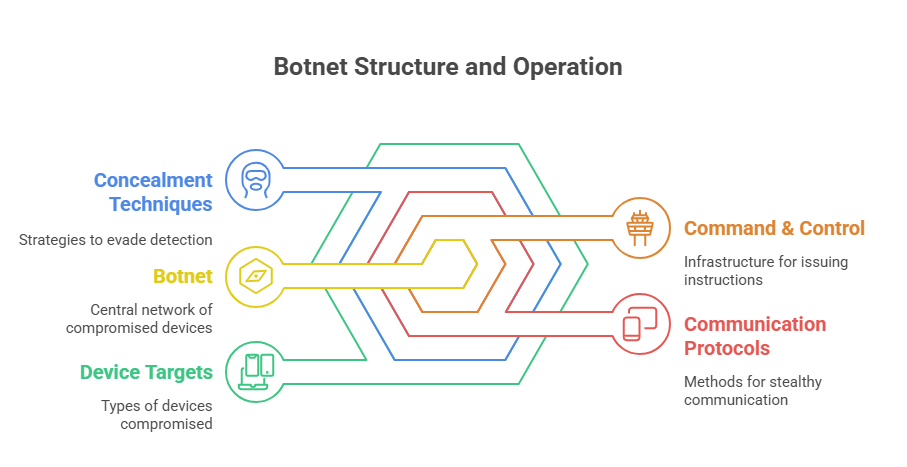
Botnet characteristics include stealthy communication protocols like HTTP/HTTPS, P2P connections for redundancy, and modular architectures that allow rapid expansion. Command-and-control (C2) servers issue encrypted instructions, ensuring botnets adapt to evolving cybersecurity measures. Their dynamic infrastructures leverage fast-flux DNS, rotating IP addresses to obscure detection. In essence, botnets epitomize the intersection of automation and criminal innovation, evolving into persistent, global threats.
Anatomy: Command and Control, Architectures
A botnet’s command and control (C2) structure dictates its efficiency and resilience. Centralized models use singular C2 servers that broadcast commands to infected nodes, offering simplicity but with a critical vulnerability—once identified, authorities can dismantle them. Peer-to-peer (P2P) architectures, however, distribute C2 functionality across the network, eliminating single points of failure. This decentralized approach bolsters botnet durability, complicating takedown efforts.
Each infected device within a botnet serves dual roles: as a bot receiving commands and as a relay for instructions to other nodes. This self-replicating model accelerates infection rates and distributes network load, ensuring scalability. Architectures often employ layered encryption and steganography to conceal instructions within benign data packets, reducing detection likelihood. Hybrid models combine centralized and P2P elements, optimizing flexibility and persistence.
The backbone of botnet resilience lies in adaptive communication protocols. Attackers leverage domain generation algorithms (DGAs), dynamically creating new domain names for C2 servers, evading blacklists and static defenses. Multi-protocol support enables seamless transitions between communication methods—IRC, HTTP, SSL/TLS—tailored to current detection landscapes. This architectural ingenuity transforms botnets into formidable adversaries, requiring multi-layered countermeasures for effective disruption.
How Botnets Spread and Evade Detection
Infection Vectors (Malware, Phishing)
Botnets leverage multiple infection vectors, ensuring a wide reach and continuous expansion. Malware is their primary tool, often embedded in malicious email attachments, trojanized software, or pirated applications. Cybercriminals craft malware to exploit system vulnerabilities, achieving remote code execution and persistent control over infected devices. Once a system is compromised, the malware silently establishes communication with the botnet’s C2 infrastructure, integrating the device into the network.
Phishing campaigns serve as complementary infection vectors. Through deceptive emails, social media messages, or fraudulent websites, users are lured into revealing credentials or downloading malware-laden files. Phishing not only compromises individuals but also opens pathways into organizational networks, increasing botnet reach. Sophisticated attacks often mimic legitimate communication, using social engineering tactics to bypass user skepticism. This dual-pronged approach—technical exploitation via malware and human manipulation via phishing—maximizes infection rates.
Botnets exploit zero-day vulnerabilities, particularly in outdated software and unpatched devices. IoT ecosystems are particularly vulnerable, with lax security protocols and default credentials enabling effortless infiltration. Once infected, these devices form low-maintenance nodes that silently propagate botnet commands, reinforcing the network’s strength. This multifaceted infection strategy ensures botnets continuously replenish their ranks, maintaining operational capacity.
Evasion Techniques
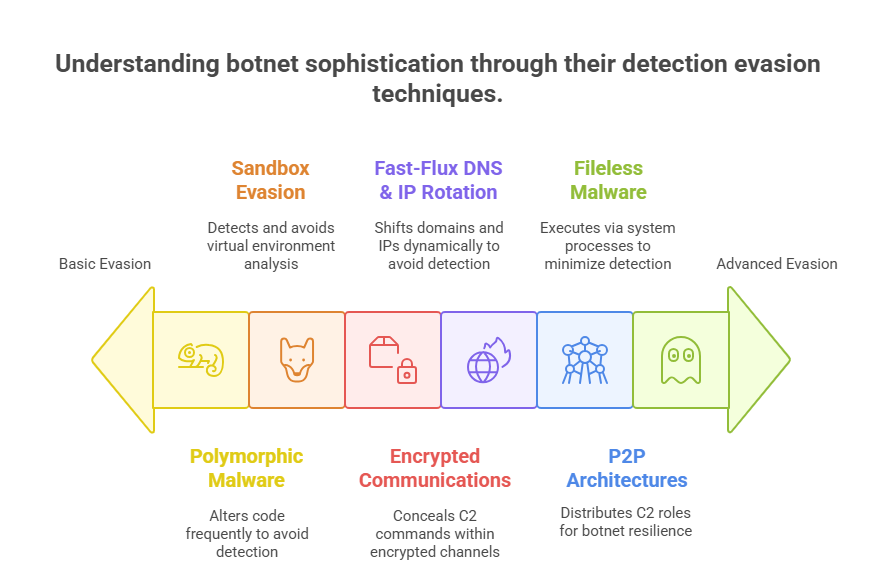
To persist, botnets deploy evasion techniques meticulously designed to bypass detection by security solutions. Polymorphic malware alters its code signature with each infection instance, evading signature-based antivirus tools. Advanced botnets integrate sandbox evasion capabilities, detecting virtualized environments used for malware analysis and altering behavior to appear benign.
Encrypted communications form a key defensive layer, obscuring C2 instructions within SSL/TLS tunnels or steganographic channels. This encryption, combined with fast-flux DNS and dynamic IP rotations, conceals the true C2 infrastructure, complicating tracking efforts. Some botnets employ domain generation algorithms (DGAs) to generate fresh, unpredictable domain names, bypassing static blacklists.
Additionally, peer-to-peer architectures decentralize C2 functionality, ensuring that even if certain nodes are isolated or disabled, the network remains operational. Fileless malware execution—leveraging legitimate system processes rather than traditional executable files—further reduces the likelihood of detection. Botmasters constantly refine these tactics, blending technical sophistication with strategic evasion to ensure botnet survival against increasingly advanced cybersecurity countermeasures.
Disruption Methods for Botnets
Takedown Operations and Seizures
Takedown operations target a botnet’s core infrastructure—primarily the C2 servers—disrupting its ability to coordinate infected devices. Law enforcement agencies collaborate with cybersecurity firms and Internet Service Providers (ISPs) to identify, isolate, and neutralize these servers. Joint operations often rely on digital forensics, reverse engineering of malware, and legal channels to secure court orders for infrastructure seizure. Seizing or disabling C2 servers effectively disintegrates centralized botnets, forcing botmasters to rebuild control channels.
High-profile takedowns, such as Operation Tovar, have demonstrated the potential to neutralize widespread threats by dismantling core infrastructure. However, success is often temporary; adaptive botnets employing P2P architectures can reestablish control through remaining nodes. These operations highlight the cat-and-mouse dynamic between security teams and botmasters. Comprehensive disruption efforts necessitate a multi-pronged approach, combining technical acumen, legal leverage, and international cooperation.
Advanced Cybersecurity Countermeasures
Advanced countermeasures focus on preemptive and reactive strategies to disrupt botnet functionality. Intrusion detection systems (IDS) and network anomaly detection tools monitor for unusual traffic patterns indicative of botnet activity. Endpoint detection and response (EDR) solutions analyze behavior at the device level, identifying signs of infection such as unauthorized network communications or persistent processes.
Cybersecurity teams leverage honeypots—decoy systems designed to lure botnets—gathering intelligence on malware behavior, infection vectors, and C2 protocols. This data enables proactive defense development and targeted countermeasures. Threat intelligence sharing platforms facilitate cross-industry collaboration, allowing organizations to adapt to emerging threats rapidly.
Technical measures include sinkholing, redirecting botnet traffic to controlled servers to isolate and neutralize compromised devices. Botnet fingerprinting helps identify distinctive communication patterns or protocol anomalies, streamlining detection and mitigation. Integrating machine learning enhances the capacity to recognize evolving botnet behavior, adapting defenses in real time. User education, emphasizing phishing awareness and secure device configurations, adds a critical human layer to cybersecurity efforts.
Combined, these approaches establish a resilient framework capable of disrupting both centralized and decentralized botnets, reducing the window of vulnerability and minimizing operational impact.
| Aspect | Takedown Operations and Seizures | Advanced Cybersecurity Countermeasures |
|---|---|---|
| Objective | Disrupt the botnet’s core infrastructure (C2 servers). | Detect, prevent, and mitigate botnet activity proactively. |
| Key Players | Law enforcement, cybersecurity firms, ISPs. | Cybersecurity teams, IT staff, global threat intelligence communities. |
| Approach | Reactive, targeting core nodes for takedown through legal and technical means. | Proactive and adaptive, using monitoring tools, deception, and AI-driven detection. |
| Techniques | Digital forensics, malware reverse engineering, legal actions (seizures). | IDS, EDR, sinkholing, honeypots, machine learning, and threat intelligence sharing. |
| Scope | Disrupts centralized botnets; effectiveness reduced against P2P architectures. | Addresses both centralized and decentralized botnets through layered defenses. |
| Longevity | Often temporary; botnets can adapt and reestablish control. | Continuous monitoring and evolving techniques for long-term resilience. |
| Human Factor | Legal expertise, cross-agency collaboration. | User education and secure practices to prevent infections. |
| Challenges | Adaptive botnets can circumvent takedowns; requires sustained effort. | Sophisticated evasion techniques require constant updates and collaboration. |
The Impact of Botnets on Organizations and Individuals
Data Theft, Financial Losses, and Reputational Damage
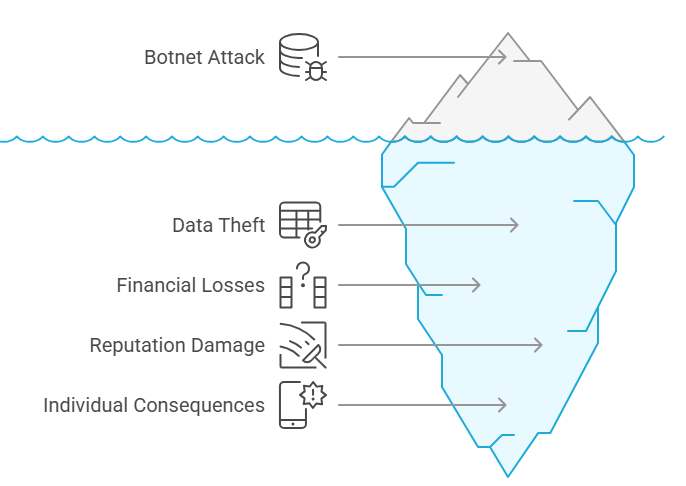
Botnets are potent engines of data theft, extracting sensitive information ranging from customer records to intellectual property. Once compromised, infected devices funnel this data to external servers, enabling identity fraud, corporate espionage, and intellectual property breaches. High-profile incidents involving botnet-enabled data breaches have demonstrated catastrophic outcomes, eroding stakeholder trust and prompting legal ramifications.
The financial impact of botnets is twofold: direct losses and indirect costs. Direct losses stem from fraudulent transactions, ransom payments, and remediation efforts. Indirect costs arise from operational downtime, regulatory fines, and diminished consumer confidence. Botnet-driven DDoS attacks can paralyze ecommerce platforms, resulting in lost sales and service degradation. Recovery costs can run into millions, while enduring reputation damage may depress market valuation and erode long-term customer loyalty.
Reputational harm extends beyond immediate stakeholders. News of a botnet-induced breach spreads rapidly, inviting scrutiny from regulators, partners, and the public. Companies seen as lax in cybersecurity can lose contracts, face boycotts, and suffer brand deterioration. Even individuals affected by botnets—through credential theft or malware infections—may endure financial strain and reputational setbacks, particularly in professional or social contexts.
For organizations, the convergence of data loss, financial depletion, and reputational hits underscores the necessity of comprehensive cybersecurity frameworks. Real-time threat monitoring, proactive patch management, and continuous user education fortify defenses against botnet-induced fallout. Failure to implement robust measures exposes both organizations and individuals to compounding risks that can devastate finances and reputation alike.
Tools and Frameworks for Botnet Disruption
Emerging Technologies and Global Initiatives
Emerging technologies are reshaping botnet disruption strategies, introducing precision and adaptability. AI-powered threat detection tools analyze vast network data streams in real time, identifying botnet patterns based on behavioral anomalies rather than static signatures. These systems adapt to evolving botnet tactics, detecting previously unknown variants and responding dynamically. Machine learning enhances this adaptability, enabling automated containment of botnet activity across diverse network architectures.
Global initiatives play a pivotal role in coordinating botnet countermeasures. Collaborative frameworks like the Cyber Threat Alliance (CTA) and the Global Cyber Alliance (GCA) facilitate real-time intelligence sharing, enhancing collective resilience. These alliances aggregate insights from cybersecurity firms, law enforcement, and governmental bodies, creating a unified front against botnet threats. Information Sharing and Analysis Centers (ISACs) further promote cross-sector collaboration, enabling rapid dissemination of threat indicators.
Technical tools include sinkholing, redirecting botnet traffic to controlled destinations, isolating compromised devices. Deception technologies deploy decoys—honeypots and sandbox environments—that attract botnet activity, providing actionable insights into evolving tactics. Network segmentation confines botnet activity within specific network zones, mitigating lateral movement and reducing risk exposure. The deployment of Zero Trust architectures, emphasizing continuous verification and least privilege access, adds a robust defensive layer against botnet infiltration.
Cloud-based security solutions offer scalable defense mechanisms, leveraging global threat intelligence feeds to identify and neutralize botnet activity. Integrating blockchain-based identity systems strengthens device authentication, minimizing the risk of unauthorized control. Additionally, endpoint detection and response (EDR) solutions, equipped with automated remediation capabilities, disrupt botnet persistence at the device level. As these technologies converge, they create a proactive, multi-layered defense system capable of countering even the most adaptive botnet threats.
Global cooperation amplifies these efforts, harmonizing policies, legal frameworks, and technical resources. Joint initiatives ensure that botnet disruption strategies transcend borders, addressing the inherently global nature of these threats. The continuous refinement of these tools and frameworks—combined with robust cybersecurity training—fortifies digital ecosystems against evolving botnet architectures.
| Aspect | Details |
|---|---|
| AI-Powered Detection | Analyzes real-time network data, identifies behavioral anomalies, detects new botnet variants. |
| Machine Learning | Enhances adaptability, automates containment across diverse networks. |
| Global Initiatives | CTA, GCA, ISACs enable real-time intelligence sharing and collective resilience. |
| Sinkholing | Redirects botnet traffic to controlled servers, isolating infected devices. |
| Deception Technologies | Honeypots and sandbox environments attract botnet activity for analysis. |
| Network Segmentation | Restricts botnet activity within defined zones, reducing lateral movement risk. |
| Zero Trust Architectures | Continuous verification and least privilege access bolster defenses. |
| Cloud-Based Security | Scalable solutions leveraging global threat intelligence to neutralize botnets. |
| Blockchain Identity Systems | Strengthen authentication, reducing unauthorized control risks. |
| Endpoint Detection and Response (EDR) | Automates remediation, disrupts botnet persistence. |
| Global Cooperation | Harmonizes policies, legal frameworks, and technical resources to address global botnet threats. |
Why Botnet Disruption Skills Are Essential for Advanced Cybersecurity and Management Certification by ACSMI Students
Advanced Cybersecurity and Management Certification by ACSMI as the Essential Training for Cybersecurity Professionals
Mastering botnet disruption is no longer optional—it's a core competency for cybersecurity professionals. Advanced Cybersecurity and Management Certification by ACSMI empowers students with in-depth knowledge of botnet architecture, evasion tactics, and countermeasure design. This certification goes beyond theoretical instruction, offering hands-on simulations that mirror real-world botnet scenarios. By dissecting botnet command structures, infection vectors, and C2 protocols, students gain a tactical understanding of how to dismantle these threats efficiently.
ACSMI’s program emphasizes practical application. Students engage with live botnet environments, developing skills in incident response, network forensics, and automated countermeasures. This approach ensures they can identify and neutralize botnet activity under real-world conditions. The curriculum integrates modules on AI-driven detection, machine learning applications, and advanced evasion techniques, providing a comprehensive skill set tailored to modern botnet challenges.
In addition to technical mastery, ACSMI focuses on strategic leadership. Students learn to design multi-layered defense architectures, incorporating tools like Zero Trust frameworks, EDR solutions, and global threat intelligence into organizational security postures. The program also covers legal and compliance considerations, preparing graduates to navigate the complex regulatory landscape surrounding botnet takedown operations.
Graduates of Advanced Cybersecurity and Management Certification by ACSMI emerge as proactive defenders equipped to anticipate, disrupt, and dismantle botnets at scale. Their expertise positions them as key assets in any cybersecurity team, capable of protecting organizations from both immediate threats and long-term reputational damage. By mastering botnet disruption techniques, these professionals gain a competitive edge in an industry where adaptability and precision are critical for success.
Frequently Asked Questions
-
A botnet is a network of compromised devices, controlled remotely by cybercriminals to launch malicious activities. These devices, often called “zombies,” receive instructions from a command-and-control (C2) server, executing tasks such as DDoS attacks, spam distribution, and data theft. Botnets operate stealthily, blending in with regular network traffic, making them difficult to detect. They can be centrally controlled or use peer-to-peer architectures for resilience. By exploiting software vulnerabilities or phishing tactics, attackers build botnets capable of overwhelming even robust cybersecurity systems. The global distribution of compromised devices allows botnets to sustain operations, adapt to countermeasures, and inflict massive financial and operational damage.
-
Botnets spread through multiple vectors. Malware infections via phishing emails, malicious downloads, or compromised websites are common. Once malware executes, it establishes communication with the botnet’s C2 server, integrating the device into the network. IoT devices with default credentials and unpatched vulnerabilities offer easy targets. Additionally, botnets exploit zero-day vulnerabilities, infiltrating systems before security patches are available. Some sophisticated botnets use self-replication, where infected devices scan for other vulnerable systems to propagate the infection. This multifaceted approach ensures rapid expansion, persistence, and resilience against defensive measures, allowing botnets to grow into vast, global networks.
-
Indicators of botnet infection include unexplained slow performance, frequent crashes, and unexpected network activity. Users may notice outgoing traffic spikes, even when the device is idle, or the system may run unfamiliar processes. Antivirus alerts or blocked IP addresses linked to spam or malware distribution are also red flags. Some infections operate silently, but telltale signs like increased data usage or participation in DDoS attacks may surface during forensic analysis. Regular monitoring, intrusion detection systems, and thorough patch management help identify and mitigate botnet activity before significant damage occurs.
-
Organizations combat botnets using a combination of technical defenses, legal actions, and collaboration. Intrusion detection systems (IDS) and endpoint detection and response (EDR) tools help identify infected devices and isolate them from the network. Sinkholing techniques redirect botnet traffic to controlled servers, disrupting communication with the C2 infrastructure. Legal authorities can seize C2 servers through takedown operations. Proactive measures, such as user education, patch management, and network segmentation, minimize infection risks. Collaboration with global cybersecurity alliances enhances resilience, enabling rapid response to evolving botnet threats and reducing operational impacts.
-
Emerging technologies revolutionize botnet detection and prevention. AI and machine learning algorithms analyze traffic patterns to identify anomalies indicative of botnet activity. Behavioral analytics surpass signature-based detection, enabling identification of new, adaptive botnet variants. Blockchain-based identity systems strengthen device authentication, reducing unauthorized access risks. Deception technologies, such as honeypots, lure botnets and gather intelligence on evolving tactics. Cloud-based security solutions integrate threat intelligence feeds, providing real-time updates on botnet behaviors. These advancements create a proactive defense posture, equipping cybersecurity teams to anticipate and counter botnet strategies with precision and adaptability.
-
ACSMI’s Advanced Cybersecurity and Management Certification equips students with hands-on experience in botnet identification, mitigation, and takedown. The program covers real-world botnet scenarios, teaching students to analyze C2 structures, infection methods, and adaptive architectures. Interactive labs simulate botnet infiltration and disruption, providing practical skills in network forensics, AI-driven detection, and incident response. Students learn to deploy multi-layered defense strategies using EDR tools, Zero Trust frameworks, and legal compliance measures. The certification’s emphasis on emerging technologies ensures graduates are equipped to anticipate and neutralize botnet threats, positioning them as leaders in modern cybersecurity operations.
-
P2P botnets distribute command-and-control functions across the network, eliminating single points of failure. Unlike centralized botnets, where taking down a C2 server disrupts operations, P2P botnets remain resilient as nodes communicate directly. Each infected device acts as both client and server, relaying commands to others. This decentralized structure complicates tracking, as no central authority exists. P2P botnets use dynamic IP addresses, encrypted communications, and domain generation algorithms (DGAs) to obscure activity. Their self-healing capability enables rapid adaptation if nodes are disabled. These attributes make P2P botnets formidable adversaries requiring sophisticated, multi-faceted disruption techniques.
Final Thoughts
Botnets represent one of the most sophisticated and persistent threats in modern cybersecurity. Their ability to evolve—leveraging adaptive architectures, sophisticated evasion techniques, and globalized infection vectors—demands an equally dynamic response from defenders. Security teams must adopt a proactive stance, utilizing advanced tools, AI-driven detection systems, and global collaboration frameworks to counteract these digital adversaries.
For cybersecurity professionals, including those pursuing Advanced Cybersecurity and Management Certification by ACSMI, mastering botnet disruption techniques is essential. This expertise ensures readiness to protect both organizations and individuals from the severe financial, operational, and reputational impacts botnets can inflict. As botnet technologies continue to evolve, the defenders’ strategies must remain agile and innovative, safeguarding digital infrastructure from compromise.
| Quick Poll: What's the biggest challenge in combating botnets? | |
|---|---|
|
Evasion Tactics Detection and Monitoring Global Cooperation |
|