Predicting the Evolution of Cybersecurity Threats in Education (2026–2030)
Education is becoming one of the most strategically exploited sectors in cybersecurity, not because schools are careless, but because they combine open access, sensitive data, legacy systems, and constant operational pressure. From 2026 to 2030, attackers will increasingly view educational institutions as testing grounds, monetization hubs, and supply-chain entry points. Universities, K-12 systems, and research institutions will not just face “more attacks.” They will face more patient, identity-driven, and data-centric campaigns that exploit how education actually works.
This article breaks down how cybersecurity threats in education will evolve, what will materially change between 2026 and 2030, and the exact strategic responses institutions must implement to stay operational, compliant, and trusted.
1: Why education becomes a prime threat surface after 2026
Education environments are structurally different from enterprises, and attackers know it. They are designed for openness, collaboration, and rapid onboarding. That same openness creates chronic identity sprawl, unmanaged endpoints, and inconsistent enforcement. When you layer remote learning platforms, contractor access, and research partnerships on top, you get an ecosystem where credential abuse outperforms malware.
Between 2026 and 2030, attackers will increasingly exploit valid accounts instead of breaching firewalls. Stolen student, faculty, and administrator credentials will be used for persistence, lateral movement, and data harvesting. This mirrors patterns already visible in endpoint compromise trends discussed in the state of endpoint security, but education magnifies the problem due to sheer scale.
Another accelerating factor is data density. Education systems store identity records, health data, financial aid information, research IP, and behavioral data in one place. A single compromise can fuel identity fraud, extortion, or nation-state intelligence collection. Institutions that still treat data protection as a compliance checkbox will struggle, especially when attackers shift from smash-and-grab to long-term surveillance.
Finally, education is becoming an attack training environment. Adversaries test phishing kits, malware loaders, and lateral movement techniques against under-resourced districts before deploying refined versions against enterprises. This pattern closely aligns with findings from broader ecosystem analyses in the cybersecurity workforce shortage study, where staffing gaps directly correlate with longer attacker dwell times.
| Threat Vector | How the Threat Evolves (2026–2030) | Why Education Is Highly Exposed | Strategic Security Response | Primary Metric to Track |
|---|---|---|---|---|
| Credential phishing | Moves from bulk email to targeted role-based attacks | High student and staff turnover weakens awareness | Phishing-resistant MFA for staff and admins | % privileged users with strong MFA |
| Identity token theft | Session hijacking replaces password guessing | Heavy SSO and cloud reliance | Session monitoring and token revocation | Time to revoke compromised sessions |
| Ransomware extortion | Data theft precedes encryption or disruption | Highly sensitive student and research data | Immutable backups and DLP controls | Recovery time objective (RTO) |
| Living-off-the-land attacks | Native admin tools used maliciously | Open admin environments and weak logging | Behavior-based detection and audit logging | High-confidence alerts per month |
| Cloud misconfiguration abuse | SaaS permissions exploited quietly | Rapid cloud adoption without governance | Least-privilege SaaS access reviews | Unauthorized API calls detected |
| Vendor compromise | Third-party tools become entry points | Extensive edtech vendor ecosystem | Vendor access approval and session logging | % vendor sessions audited |
| Student account abuse | Low-privilege accounts used for persistence | Millions of unmanaged student identities | Behavior analytics on student accounts | Anomalous student logins flagged |
| Research data espionage | Long-term stealth intrusions | Valuable intellectual property | Access segmentation and monitoring | Unauthorized research data access |
| Botnet recruitment | Compromised endpoints used as nodes | Large unmanaged device populations | Endpoint isolation and monitoring | Infected endpoints identified |
| DDoS distraction attacks | Used to mask data theft | Public-facing portals and LMS platforms | Rate limiting and upstream protection | Service availability during attacks |
| Privilege escalation | Misused delegated admin rights | Role sprawl across systems | Privileged access management | % admins under PAM |
| Email account takeover | Used for internal phishing and fraud | High trust in internal emails | Email behavior analytics | Internal phishing incidents |
| Data staging | Slow exfiltration over weeks | Weak outbound monitoring | Egress filtering and DLP | Blocked exfiltration attempts |
| Account recovery abuse | Password reset workflows exploited | Self-service recovery at scale | Strong identity verification | Fraudulent reset attempts |
| Shadow IT platforms | Unapproved tools store sensitive data | Faculty autonomy and experimentation | Cloud discovery and policy enforcement | Unknown SaaS apps discovered |
| Insider data misuse | Authorized access used maliciously | Broad access to student data | UEBA and least privilege | Suspicious internal access events |
| API abuse | Automation used for mass data access | Exposed education platforms | API rate limits and monitoring | Abnormal API usage patterns |
| Backup targeting | Attackers disable recovery options | Flat network backup access | Offline and immutable backups | Backup integrity verification |
| Compliance-driven attacks | Threat actors exploit audit gaps | Fragmented regulatory oversight | Continuous control monitoring | Audit findings trend |
| Credential reuse | Passwords reused across platforms | Multiple learning systems per user | Passwordless authentication | Password reuse incidents |
| Log tampering | Attackers erase evidence post-compromise | Inconsistent logging practices | Immutable log storage | Log retention compliance |
| Delayed detection | Intrusions remain unnoticed for months | Alert fatigue and understaffing | Signal-based alert prioritization | Mean time to detect (MTTD) |
| Incident response drift | Inconsistent actions between analysts | No standardized playbooks | Pre-approved response workflows | Containment time variance |
| Regulatory exposure | Fines and sanctions after breaches | Student data protection laws | Evidence-ready incident handling | Regulatory penalties avoided |
2: Threat predictions that will define education cybersecurity by 2030
The most important prediction is that identity becomes the primary attack surface. Attackers will increasingly bypass perimeter defenses and target single sign-on platforms, session tokens, and password recovery workflows. This makes traditional perimeter tools less effective unless identity telemetry is tightly integrated with detection, as outlined in the SIEM overview.
Ransomware will continue, but its role will shift. Encryption becomes optional. The real leverage is data exposure, regulatory pressure, and reputational harm. Institutions that cannot confidently answer “what data left the environment” will lose negotiation leverage immediately. The evolution of ransomware tactics aligns with patterns analyzed in ransomware detection, response, and recovery.
Another major evolution is the blending of cybercrime and espionage. Research universities will see more long-term intrusions aimed at intellectual property, not immediate payout. These intrusions often start with phishing or OAuth abuse, as detailed in broader phishing trend analyses like phishing attack prevention strategies.
Attackers will also increasingly use education environments as botnet infrastructure and testing grounds for denial-of-service campaigns. This mirrors broader botnet economics explored in botnet structure and disruption methods and operational disruption tactics in DoS attack mitigation.
3: Strategic cybersecurity recommendations for schools and universities
The first strategic shift is moving from tool-centric to risk-centric security. Education institutions must define what operational failure actually means: enrollment disruption, grading outages, payroll interruption, or research data exposure. Security investments should map directly to preventing those outcomes, not abstract threat lists. This approach mirrors how mature programs structure priorities in incident response planning.
Second, institutions must aggressively reduce identity risk. That means eliminating shared accounts, enforcing phishing-resistant MFA for staff, and monitoring session behavior, not just login success. Identity governance should be treated as a safety control, not an IT convenience. Encryption and trust foundations described in PKI components and applications play a critical role here.
Third, data protection must become proactive. Sensitive records should be classified, monitored, and protected in motion. Without strong controls, attackers will stage data quietly and exfiltrate over weeks. Practical controls are outlined in data loss prevention strategies, which are increasingly essential in education contexts.
Finally, response must be standardized. Education environments suffer from analyst-dependent containment, where outcomes vary based on who is on call. Playbooks, automation for safe actions, and rehearsals reduce chaos during real incidents. Execution models from IRP development are directly applicable.
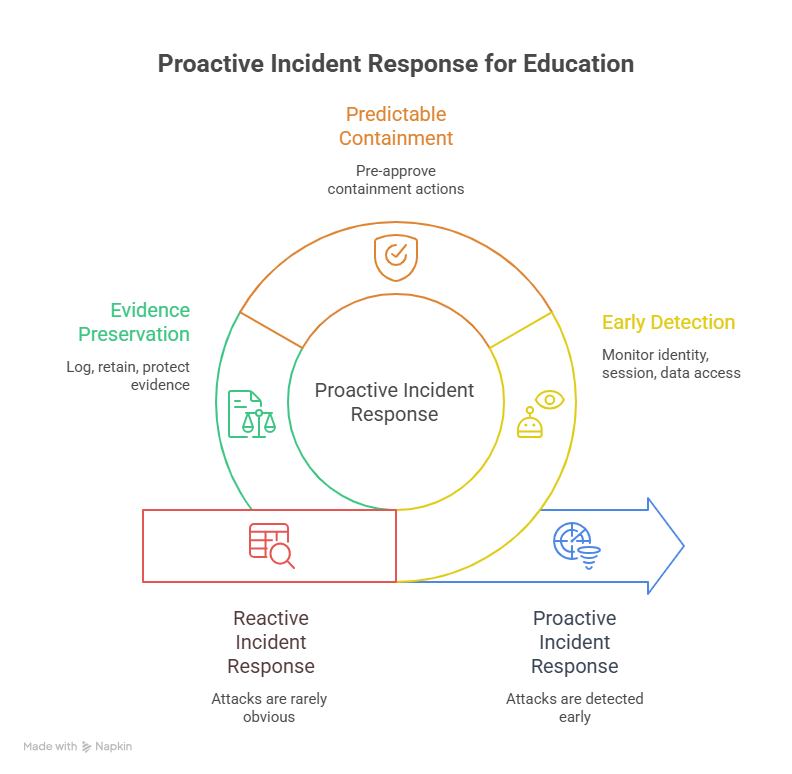
4: Incident response realities in education environments
Incident response in education fails when teams assume attacks will be obvious. They rarely are. Most breaches involve weeks of silent access followed by sudden disruption. Institutions must optimize for early detection of abnormal identity behavior, suspicious session patterns, and unusual data access, not just malware alerts. This is where a properly tuned correlation layer becomes non-negotiable, and the detection architecture outlined in a SIEM overview helps teams connect identity, endpoint, and cloud signals into one timeline. Pair that with proactive hunting around credential theft and login abuse using intelligence workflows from cyber threat intelligence (CTI) collection and analysis, so “quiet” intrusions surface before attackers trigger disruption.
Containment must also be predictable. When response steps vary by analyst, attackers exploit hesitation, internal approvals, and tool handoffs. Education institutions should pre-approve containment actions such as account suspension, session revocation, password reset enforcement for high-risk groups, and scoped network isolation for compromised devices and admin workstations. These steps reduce dwell time without risking operations, and they should be documented and rehearsed using an incident response plan (IRP) that clearly defines who can authorize which action and under what conditions. For extortion-driven events, align isolation and recovery steps with battle-tested practices in ransomware detection, response, and recovery, and reduce attacker leverage by monitoring for staging and exfiltration with data loss prevention (DLP) strategies.
Equally important is evidence preservation. Education breaches often become legal and regulatory matters, especially when student data, financial aid records, or research assets are involved. Logging, retention, and chain-of-custody must be designed in advance so you can prove what happened, when it happened, and what data was touched, even if attackers try to wipe traces. Encrypt sensitive logs and protect integrity where possible using principles from encryption standards, and make sure your team can reliably reconstruct the story during investigations and audits without guessing.
5: Leadership, governance, and budget alignment through 2030
By 2030, education cybersecurity leaders will be judged less on tools and more on outcomes. Boards and governing bodies want to know how likely disruption is, how fast recovery happens, and what data is truly protected. Programs that cannot answer these questions will struggle for funding. To make that conversation real, translate risk into scenarios leadership understands, like ransomware shutting down enrollment systems, a phishing-led takeover of student portals, or data theft that triggers regulatory fallout, then map each scenario to specific controls and response steps from an incident response plan (IRP) and a tested ransomware detection and recovery playbook.
Security leaders should frame investment using scenario-based risk models rather than technical wish lists. Tie funding to reduced outage likelihood, reduced recovery time, and reduced regulatory exposure. This approach mirrors how mature sectors justify spend, as seen in the global cybersecurity market outlook, but education must add a strong identity lens because most real incidents now start with “valid logins” and account compromise. That is why identity hardening and visibility should be positioned as a resilience initiative supported by correlated telemetry through a well-structured SIEM program.
Metrics should focus on identity protection coverage, response speed, data protection effectiveness, and recovery readiness. These are defensible, repeatable indicators that resonate with non-technical leadership. Make them measurable by tracking phishing-driven initial access reduction using the signals in phishing trend prevention strategies, proving data risk reduction with controlled movement and monitoring from DLP strategies and tools, and validating trust foundations where needed with PKI components and applications.
6: FAQs on the future of cybersecurity in education (2026–2030)
-
Education combines open access, valuable data, and limited security staffing. Attackers exploit high user turnover and weak identity controls to gain persistent access. This trend mirrors broader workforce and resource constraints highlighted in the cybersecurity workforce shortage study.
-
Ransomware remains critical, but data theft and extortion will often matter more than encryption. Institutions that cannot verify what data was stolen lose leverage immediately. Preparing for this evolution requires the strategies outlined in ransomware detection and recovery.
-
Focus on phishing-resistant authentication for staff and administrators, combined with behavior-based monitoring. Awareness alone is insufficient. Effective prevention techniques are detailed in phishing prevention strategies.
-
DLP protects student records, financial data, and research assets from silent exfiltration. It reduces extortion leverage and compliance exposure. Practical implementation guidance is available in data loss prevention strategies.
-
Response should be scenario-based, standardized, and rehearsed. Pre-approved containment steps reduce hesitation and attacker dwell time. Use structured approaches from incident response plan development.
-
Leadership should track identity protection coverage, detection-to-containment time, data protection effectiveness, and recovery readiness. These metrics directly correlate with reduced operational disruption and regulatory risk.