Intrusion Detection Systems (IDS): Functionality and Deployment
Intrusion Detection Systems (IDS) are essential pillars of a modern cybersecurity infrastructure—not optional add-ons. In an era where zero-day threats and lateral movement attacks dominate enterprise breach reports, IDS provides a much-needed layer of proactive threat visibility. Unlike preventive tools like firewalls that block known malicious traffic, IDS monitors live system and network behavior, detecting anomalies and signature-based attacks that slip through perimeter defenses. A well-configured IDS delivers real-time alerts, helping security teams respond to early-stage intrusions, misconfigurations, insider threats, and policy violations.
It forms a critical part of a layered defense strategy, especially when paired with firewalls, endpoint detection, and SIEMs. But IDS isn’t plug-and-play. Its deployment architecture, type (HIDS/NIDS/Hybrid), tuning, and positioning dramatically impact its effectiveness. This guide unpacks how IDS works, its architecture, deployment strategies, use cases, and why mastering IDS is no longer optional for cybersecurity professionals. Whether defending small networks or securing cloud workloads, understanding IDS is foundational to modern threat detection.
What Is an IDS and How Does It Work?
An Intrusion Detection System (IDS) is a cybersecurity tool that monitors traffic or system behavior to detect unauthorized access, policy violations, or malicious activity. It doesn’t block threats—instead, it generates alerts, allowing analysts to investigate and act before an attacker causes damage. IDS works in two primary modes: signature-based detection, which identifies known attack patterns, and anomaly-based detection, which flags deviations from established behavioral baselines.
Signature-Based vs Anomaly-Based Detection
Signature-based IDS relies on predefined rules and known attack patterns. It’s effective for identifying well-documented exploits, malware signatures, and repeatable attack vectors. However, it struggles with zero-day threats or novel intrusion techniques.
Anomaly-based IDS builds statistical models or behavior profiles of normal system/network activity. It flags outliers that deviate from this baseline. This approach detects previously unseen attacks, but also results in higher false positives, requiring tuning and analyst oversight.
Combining both methods creates a hybrid approach that improves accuracy and responsiveness in live environments.
Where IDS Fits in the Security Stack
IDS operates at the monitoring and detection layer, sitting between perimeter security (firewalls, VPNs) and reactive tools like SIEM or SOAR. It passively observes traffic or system logs, without interfering with data flows—unlike an IPS, which actively blocks threats.
For network-based IDS (NIDS), sensors are deployed at choke points—firewall boundaries, router connections, or VLAN hubs—allowing full visibility into ingress and egress traffic.
Host-based IDS (HIDS) resides on individual endpoints or servers, examining logs, file integrity, and system calls in real time.
Both types feed into the analysis engine, where detection algorithms, rule sets, or AI models parse the data. If a threat is detected, the system raises an alert via dashboards, syslogs, or integration with ticketing systems.
The value of IDS lies in its early warning capability. It gives security teams time to respond—whether that means isolating a host, escalating to incident response, or adjusting firewall rules. With proper tuning, IDS can detect lateral movement, brute force attempts, DNS tunneling, and post-exploitation activity that other tools may miss.
IDS Architecture and Key Components
An effective IDS isn’t a single tool—it’s a modular detection framework. Each component plays a distinct role, from data collection to threat alerting. Whether deployed in a corporate data center or a cloud-native architecture, the IDS must align with system topology, threat models, and network visibility goals.
Sensors and Data Collectors
The sensor layer captures traffic or logs depending on the IDS type:
NIDS sensors are deployed inline or in passive mode across strategic points—network edges, DMZs, internal segments, or mirror ports. These sensors collect packet-level data, which is parsed for anomalies or known attack signatures.
HIDS agents sit on endpoints (servers, workstations, IoT devices) and gather system logs, file integrity data, and process activity. These agents must be lightweight, tamper-resistant, and compatible with OS logging systems.
Data fidelity is critical—if sensors miss a packet or drop logs due to bandwidth limits or overload, detection gaps emerge.
Analysis Engine, Alert System, and Logging
At the heart of any IDS is the analysis engine, where raw inputs are processed using:
Signature databases (e.g., Snort rules)
Anomaly detection models
Heuristics and behavioral baselines
Upon detecting malicious behavior, the engine triggers the alerting system. This system classifies threats (e.g., high, medium, low severity), timestamps the event, and forwards the data via syslog, JSON, or a SIEM-compatible format.
Robust logging is non-negotiable. Analysts must be able to reconstruct attack timelines using historical data. Therefore, logs are often forwarded to centralized log collectors or SIEM platforms to support correlation, threat hunting, and forensic analysis.
Integration with SIEM and Firewalls
Modern IDS tools must integrate seamlessly with broader security ecosystems, including:
SIEM platforms (e.g., Splunk, IBM QRadar) for aggregation and correlation of alerts
SOAR tools for automated incident response workflows
Firewalls and NACs for reactive measures based on IDS triggers
This integration transforms IDS from a passive observer into a coordinated security control, enabling actions like isolating endpoints, blocking IPs, or launching playbooks when high-confidence threats are flagged.
IDS components should also support encrypted traffic inspection, either via SSL/TLS offloading or integration with decryption tools. With encryption accounting for over 80% of web traffic, visibility into encrypted sessions is critical for full-spectrum threat detection.
| Sensors and Data Collectors | Analysis Engine, Alert System, and Logging | Integration with SIEM and Firewalls |
|---|---|---|
| NIDS sensors monitor perimeter and internal traffic points | Processes data using signatures, anomaly models, heuristics | Connects to SIEMs (e.g., Splunk, QRadar) for alert correlation |
| HIDS agents gather logs from endpoints like servers and IoT devices | Triggers alerts with severity classification | Integrates with SOAR for automated response workflows |
| High data fidelity is essential to prevent blind spots | Forwards alerts/logs via syslog, JSON, etc. | Supports firewall and NAC actions (e.g., block, isolate) |
| Sensors must be tamper-resistant and resource-efficient | Logging enables forensic analysis and attack timeline reconstruction | Enables encrypted traffic inspection via SSL/TLS offloading |
Comparing IDS Types
Selecting the right IDS type depends on network structure, endpoint density, performance requirements, and integration needs. Each type—Host-Based IDS (HIDS), Network-Based IDS (NIDS), and Hybrid IDS—offers specific advantages and trade-offs. Deployment should align with detection goals and operational capacity.
Host-Based IDS (HIDS)
HIDS monitors individual endpoints or servers, offering granular insight into operating system logs, file integrity, process behavior, and user activity. It operates independently of network traffic and is ideal for:
Detecting insider threats
Identifying file tampering or privilege escalation
Monitoring systems in segmented or encrypted environments
HIDS is effective in identifying rootkits, log tampering, unauthorized changes, and malware persistence techniques. However, its visibility is limited to the host it's installed on. For large environments, agent management, resource load, and configuration drift can become challenges.
Network-Based IDS (NIDS)
NIDS monitors network traffic in real time across segments. It’s typically deployed on mirror ports or taps, enabling it to analyze packets without interfering with the actual flow.
Benefits include:
Broad visibility of lateral movement, port scans, reconnaissance activity
Real-time inspection of TCP/UDP payloads for signatures or anomalies
Centralized monitoring across multiple hosts and subnets
However, NIDS struggles with encrypted traffic, has blind spots in east-west traffic (unless sensors are widely distributed), and may require heavy tuning to avoid alert fatigue in high-throughput environments.
Hybrid Systems & Inline vs Passive
Hybrid IDS combines HIDS and NIDS to leverage both host-level insights and network-wide detection. This fusion provides depth—system behavior plus traffic patterns—allowing for stronger correlation and faster threat validation.
Hybrid deployments are common in:
SOCs aiming for comprehensive detection coverage
Cloud-native environments where containers and virtual machines coexist
Environments using zero trust architecture, where verification at multiple layers is required
In terms of placement, IDS can be:
Inline (active): Positioned between source and destination. It has packet inspection capability before forwarding data. This allows for real-time action (often part of IPS deployments), but introduces latency and risk if misconfigured.
Passive (monitoring): Connected to mirror ports or span ports. It inspects copy of the traffic and does not interfere with the network. While safer and more scalable, it’s reactive and depends on integration with other tools to initiate remediation.
Ultimately, the best IDS setup is scenario-specific. Enterprises often run NIDS at core switches and HIDS on critical servers, while smaller businesses may opt for hybrid open-source solutions to balance cost and capability.
| Host-Based IDS (HIDS) | Network-Based IDS (NIDS) | Hybrid IDS / Inline vs Passive |
|---|---|---|
| Monitors individual endpoints and servers | Monitors real-time traffic across network segments | Combines HIDS and NIDS for layered detection |
| Detects insider threats, file tampering, and system misuse | Detects port scans, lateral movement, and packet-level anomalies | Used in SOCs, cloud-native, and zero trust environments |
| Independent of network traffic; ideal for encrypted systems | Requires packet visibility; struggles with encrypted traffic | Offers stronger correlation through system + network insights |
| Limited to the host it’s installed on | Broad visibility, but needs tuning and wide sensor distribution | Can be deployed inline (active) or passive (monitoring) |
| Resource-intensive in large-scale environments | Risk of alert fatigue in high-throughput networks | Inline = real-time blocking; Passive = monitoring only |
IDS Deployment Best Practices
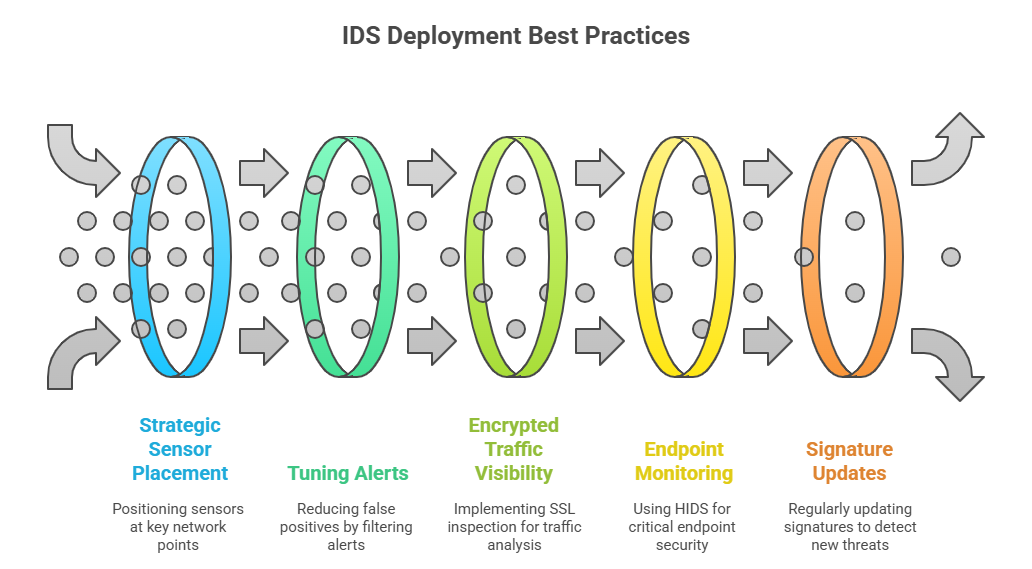
Effective IDS deployment isn’t about coverage alone—it’s about strategic positioning, intelligent tuning, and maximized signal-to-noise ratio. The best systems don’t just detect—they deliver actionable alerts with minimal overhead and false positives. Below are core best practices for successful IDS rollout in modern environments.
Strategic Placement of Sensors
Where you place IDS sensors directly impacts detection quality. For NIDS:
Deploy sensors at network ingress and egress points—between firewalls, on perimeter routers, and at data center boundaries.
Monitor internal VLANs or east-west traffic, especially if lateral movement or insider threats are a concern.
In cloud environments, deploy IDS at the virtual switch level or via cloud-native tools like AWS GuardDuty or Azure NSG flow logs.
For HIDS:
Focus on critical assets—database servers, domain controllers, and high-value endpoints.
Ensure agents are installed with minimum user disruption and updated regularly to prevent evasion.
Tuning to Reduce False Positives
An untuned IDS creates alert fatigue, drowning analysts in noise and hiding real threats. Tuning involves:
Suppressing benign signatures that repeatedly fire in safe scenarios
Updating signatures frequently to stay ahead of evolving TTPs
Setting custom thresholds based on baselines of normal behavior
Reviewing alerts regularly to retrain anomaly detection models
Use test environments to validate new rule sets before deploying them in production. Automation tools can help eliminate repetitive tuning work.
Ensuring Visibility into Encrypted Traffic
With over 80% of traffic now encrypted, IDS systems risk losing visibility. Best practices include:
Decryption via SSL inspection at firewalls or load balancers before passing traffic to the IDS
Using endpoint-level HIDS for post-decryption analysis
Logging TLS handshake metadata (e.g., SNI, cert details) even if payload inspection is limited
Avoid violating user privacy or legal frameworks when inspecting encrypted sessions—particularly in industries with compliance mandates like HIPAA or GDPR.
Additional Recommendations
Regularly audit sensor uptime and log forwarding to avoid silent failures
Integrate IDS with threat intelligence feeds to enrich alerts and prioritize remediation
Pair IDS with response frameworks like SOAR to automate investigations where feasible
A well-deployed IDS should feel invisible—but make threats visible. It should fit seamlessly within your security fabric, improving visibility without introducing fragility or noise.
Real-World Use Cases and Limitations
Intrusion Detection Systems (IDS) are deployed across vastly different environments—each with unique visibility demands, bandwidth challenges, and operational risks. While IDS adds critical value in detecting threats missed by perimeter tools, its effectiveness depends on the context in which it's deployed and the resources available to manage its output.
Cloud, SMB, and Enterprise Deployments
In cloud-native environments, IDS is used to monitor east-west traffic between virtual machines, containers, and cloud services. Tools like AWS GuardDuty, Azure Defender, and Suricata in EC2 provide network-level detection within cloud infrastructures. However, encrypted traffic and elastic scaling demand that IDS be cloud-aware, lightweight, and API-integrated.
For small-to-medium businesses (SMBs), open-source IDS (e.g., Snort, Zeek) offers affordable protection. SMBs benefit from:
Monitoring key entry points like VPNs and remote access
Detecting credential theft, brute force attempts, or lateral movement
Integrating with simple dashboards or MSSPs for alert triage
In large enterprises, IDS is typically part of a multi-layered detection framework, feeding into SIEMs and correlating with firewall, endpoint, and behavioral telemetry. Enterprises invest in dedicated SOC teams to manage tuning, triage, and threat hunting.
Encrypted Threat Blindspots and Alert Fatigue
One of the biggest challenges in IDS deployment is its limited visibility into encrypted traffic. Without decryption, IDS cannot inspect payloads—rendering it blind to malware hidden in HTTPS sessions, SSH tunnels, or encrypted C2 communications.
Another limitation is alert fatigue. An untuned IDS can generate thousands of alerts daily—most of which are false positives or low priority. This overwhelms security teams, delays real responses, and reduces trust in the system.
To combat this:
Organizations must continuously tune rule sets
Prioritize high-fidelity alerts
Use threat intelligence enrichment
Employ automated filtering or tiered alerting mechanisms
When to Upgrade to IPS
IDS is reactive—it alerts but doesn’t block. In high-stakes environments, this may not be enough. That’s where Intrusion Prevention Systems (IPS) come in. IPS not only detects but automatically blocks threats, often using the same underlying engine as IDS (e.g., Snort in inline mode).
Indicators that it's time to upgrade include:
Need for real-time threat suppression
Regulatory requirements demanding automated response
SOC maturity that supports fine-tuned blocklist management
However, IPS introduces latency and operational risk if misconfigured. It’s not a replacement for IDS—it’s an evolution. Many modern deployments use both: IDS for deep monitoring and IPS for perimeter protection.
Why Cybersecurity Certification Is Critical for Understanding IDS
Knowing how to deploy an IDS isn’t enough. Security professionals must understand how to interpret alerts, tune rulesets, identify evasion techniques, and integrate IDS into broader SOC workflows. As cyber threats grow more complex, IDS mastery becomes a non-negotiable skill across blue team roles. This is where formal, advanced cybersecurity training delivers its greatest value—by transforming tools into outcomes.
IDS Proficiency Is Core to SOC Effectiveness
Security Operations Center (SOC) teams rely heavily on IDS for early threat detection. Trained professionals understand how to:
Analyze IDS logs for attack chains and MITRE ATT&CK techniques
Triage false positives versus high-priority signals
Correlate IDS data with SIEM events to construct threat narratives
Without training, even sophisticated IDS deployments become noise generators. A skilled professional knows which traffic patterns are benign anomalies and which signal a real breach in progress.
Tools You’ll Master in IDS-Focused Training
Modern IDS courses cover tools that are industry-standard across enterprise SOCs:
Snort: The most widely deployed IDS/IPS engine. Students learn to write custom rules, build detection pipelines, and deploy Snort in both inline and passive modes.
Suricata: A high-performance, multi-threaded IDS/IPS with advanced protocol parsing. Training includes Suricata’s YAML rule config, EVE JSON logs, and NSM integrations.
Zeek (formerly Bro): A powerful network analysis framework. Unlike Snort or Suricata, Zeek focuses on metadata-level analysis, making it indispensable for threat hunting and anomaly detection.
Training goes beyond tool usage. Learners gain experience in log correlation, alert prioritization, threat hunting, and integrating IDS into automated SOAR workflows.
Enroll in Our Advanced Cybersecurity Certification
Our Advanced Cybersecurity Certification includes dedicated IDS mastery modules, hands-on labs with Snort, Suricata, and Zeek, and real-world threat simulations. Built for professionals preparing for SOC analyst, incident response, or blue team roles, the course offers:
Step-by-step IDS deployment walkthroughs
Live traffic capture analysis
Custom rule creation, anomaly tuning, and log forwarding exercises
Final project with realistic multi-stage attack detection
The curriculum aligns with NIST, MITRE, and CIS standards, ensuring you're not just exam-ready—but field-ready.
Whether you're just starting out or scaling up for advanced roles, IDS fluency is a career accelerant. The security landscape isn’t getting simpler—and those who can detect early, win early.
Frequently Asked Questions
-
An Intrusion Detection System (IDS) monitors traffic and alerts you to suspicious activity, but does not take direct action to stop it. An Intrusion Prevention System (IPS), on the other hand, sits inline and can actively block or drop malicious traffic. IDS is ideal for deep visibility and forensic analysis, while IPS is best for real-time threat mitigation. Many organizations deploy both—IDS for monitoring and IPS for perimeter enforcement. The core distinction is action: IDS detects and alerts, IPS detects and blocks. For environments with regulatory or uptime sensitivity, IDS is preferred to avoid unintended disruptions.
-
Yes—but with limits. Traditional signature-based IDS cannot detect zero-day attacks because they rely on known patterns. However, anomaly-based IDS can identify deviations from normal behavior that may indicate novel threats. These systems use statistical models, baselines, or machine learning to flag unusual patterns—such as a spike in data transfer or an unauthorized process. While this enables zero-day detection, it often comes with higher false positives, requiring trained analysts to verify alerts. To improve detection, IDS should be combined with threat intelligence feeds and behavioral analytics in a broader SOC workflow.
-
Host-Based IDS (HIDS) is best for endpoint-level detection—such as file tampering, log changes, or user privilege escalation. Network-Based IDS (NIDS) monitors traffic across the network, detecting reconnaissance, malware payloads, and lateral movement. If you're monitoring critical servers, go with HIDS. For inter-subnet or external traffic, NIDS is ideal. In most environments, a hybrid approach is optimal: use HIDS for endpoint integrity and NIDS for network-level visibility. The right choice also depends on infrastructure layout, compliance needs, and security staffing.
-
Absolutely. While next-gen firewalls (NGFWs) and Endpoint Detection and Response (EDR) tools provide advanced controls, IDS fills a crucial detection gap. NGFWs filter traffic at the perimeter, and EDR focuses on endpoints—but IDS monitors what's happening in between. It’s especially useful for detecting lateral movement, insider threats, policy violations, and attacks that evade EDR or firewall policies. IDS also logs raw network behavior, supporting forensic investigations and compliance audit trails. In layered defense, IDS acts as the deep observer, catching threats that other tools miss.
-
Popular open-source IDS tools include:
Snort – Signature-based, widely adopted, supports inline blocking when configured as IPS.
Suricata – Multi-threaded, supports IDS/IPS functionality with advanced protocol parsing.
Zeek (formerly Bro) – Focuses on network metadata analysis, ideal for threat hunting.
Security Onion – A full IDS stack that combines tools like Snort, Suricata, Zeek, and ELK.
These tools offer enterprise-grade detection capabilities at zero licensing cost, but they require skilled configuration, tuning, and maintenance. They're especially suitable for SMBs, researchers, and SOC teams with hands-on expertise in packet analysis and SIEM integrations.
-
To reduce false positives in IDS, organizations should:
Regularly tune signature rules and disable irrelevant ones
Implement threshold-based alerting to filter out benign anomalies
Use whitelisting to ignore approved behaviors or sources
Update IDS engines and rule sets with real-time threat intelligence
Run test environments to validate alerts before applying them in production
Correlate IDS alerts with SIEM or log data for greater context
-
Yes. IDS can be deployed in cloud environments, but it requires a different architecture than traditional on-prem setups. Cloud-native IDS tools like AWS GuardDuty, Azure NSG Flow Logs, or GCP Packet Mirroring allow for scalable threat detection. Alternatively, agent-based HIDS (e.g., OSSEC or Wazuh) can be deployed on virtual machines or containers. Cloud IDS must integrate with orchestration tools, encryption layers, and dynamic IP mapping. Challenges include visibility into east-west traffic, encrypted session analysis, and managing sensors in elastic environments. Despite these challenges, IDS remains critical for cloud workload protection and compliance logging.
Conclusion
Intrusion Detection Systems are no longer optional—they’re foundational. Whether monitoring a hybrid cloud environment, securing endpoints, or feeding insights into a SIEM, IDS delivers critical visibility into emerging threats. But value only comes when deployment, tuning, and integration are executed with precision.
Signature and anomaly detection must be balanced. Sensors must be placed intelligently. Analysts must be trained to separate signal from noise. When deployed properly, IDS becomes more than a detection tool—it becomes a strategic asset that reduces response time, strengthens layered defense, and surfaces threats others miss.
If you're serious about cybersecurity, IDS expertise isn’t a nice-to-have—it’s non-negotiable. Train in it. Master it. Deploy it smartly—and your infrastructure won’t just detect intrusions; it will outpace them.