Privacy Regulations & Cybersecurity: Emerging Global Trends & Predictions (2026–2030)
Privacy is no longer “a legal checkbox.” From 2026 to 2030, privacy rules will directly shape security architecture, incident response speed, vendor governance, and even how identity systems prove trust. The organizations that win will stop treating privacy, security, and compliance as separate departments. They will build one operating system that can prove data control, reduce breach impact, and respond with defensible evidence fast.
1) The 2026–2030 Shift: Privacy Becomes a Security Control Plane, Not a Policy Document
The most important change is that privacy regulations are moving from “what you should disclose” to “what you must be able to prove.” Proof means immutable logs, demonstrable access control, and evidence that you can detect and contain exposure quickly. This is why modern monitoring maturity described in SIEM fundamentals and roadmap level visibility explained in next gen SIEM evolution becomes privacy critical, not just SOC nice to have.
Between 2026 and 2030, regulators will increasingly evaluate privacy posture through the lens of cybersecurity resilience. If an organization cannot show how it prevents unauthorized access, limits data movement, and detects exfiltration, privacy compliance collapses under scrutiny. That aligns with the direction in future cybersecurity standards because standards are trending toward measurable controls, repeatability, and auditability. In practice, privacy compliance will demand technical capabilities such as encryption governance, data classification, and incident response rigor, not just updated policies.
A second shift is fragmentation. Global privacy rules will push toward different requirements for breach notification windows, cross border transfers, consent models, biometrics, and data localization. Security leaders will be forced to build systems that can enforce “policy by geography” without breaking operations. This is where strong cryptographic posture from encryption standards and identity trust anchored in PKI fundamentals becomes the foundation for compliance at scale, especially when third parties and cloud regions are involved.
The third shift is enforcement pressure extending into vendors and supply chains. Regulators will expect organizations to manage third party access, monitor data processors, and constrain “shadow processing” through marketing tools, analytics, and support platforms. If you cannot identify where data flows and who can touch it, you cannot claim compliance. This is why practical controls like DLP strategy and threat driven detection programs based on CTI collection become the difference between “compliance theater” and defensible compliance.
Finally, privacy incidents will be measured by response speed. If a breach happens, you must show what was accessed, what was exposed, and what containment actions were executed. That is why operational muscle memory from incident response plan execution and resilience thinking from ransomware response and recovery will increasingly function as privacy survival skills.
2) Global Privacy Trends That Will Force Security Architecture Changes
Trend 1: “Proof of control” becomes the default expectation
Regulators will increasingly ask for evidence that you control access, data movement, and exposure response. That means you must be able to produce audit logs, access histories, and containment timelines. This is why strong logging foundations in SIEM monitoring and advanced correlation in next gen SIEM will become compliance enablers. If your logs are incomplete or scattered, you will be forced into guesswork during incidents, and that guesswork becomes legal risk.
Trend 2: Data localization and cross border transfer constraints increase operational friction
From 2026 to 2030, more jurisdictions will demand local processing and stricter cross border transfer controls. Security teams will be pulled into architecture decisions: which data lives where, which processors can access it, and how you enforce geography aware policy. Encryption and key governance from encryption standards becomes critical because it reduces breach impact and strengthens defensibility when data must move. Identity trust mechanisms like PKI help establish strong device and service identity, which supports controlled processing across regions and vendors.
Trend 3: Higher penalties for mishandling sensitive categories
Sensitive data categories will expand beyond classic PII to include biometrics, precise behavioral data, health inferences, and potentially model derived attributes. The security implication is that classification and access boundaries must be real. This is where DLP strategy stops being optional and becomes your safety net against “trusted tool exfiltration.” Threat driven tuning using CTI ensures you focus controls on realistic attacker paths rather than theoretical policy statements.
Trend 4: Vendor accountability becomes enforcement leverage
Privacy regulators will increase pressure on organizations to control processors and vendors. This will force stronger privileged access governance, continuous monitoring, and faster shutdown capabilities when a vendor is compromised. Security teams that already operate with repeatable procedures from incident response execution will handle this shift better because they can execute containment fast and prove it later. Teams that treat vendor access as “IT plumbing” will keep discovering privacy exposure through third party incidents.
Trend 5: Privacy compliance and cybersecurity standards converge
Standards evolution and regulatory trends are converging around measurable outcomes: resilience, auditability, and governance. The direction described in future cybersecurity standards predicts more emphasis on controls you can test, monitor, and continuously validate. That favors organizations that build observable controls using event correlation, strong crypto, and structured incident response.
3) Emerging Threats That Will Trigger Privacy Enforcement (And How They Will Happen)
Silent data theft will replace loud breaches in many sectors
Between 2026 and 2030, many privacy incidents will not look like “a hacked server.” They will look like legitimate logins, slow exports, and repeated access to data lakes and CRMs. Attackers will exploit SaaS admin panels, compromised accounts, and weak access governance, then stage data through approved tooling. Detections must focus on data movement patterns using DLP controls and event correlation through SIEM pipelines. The organizations that cannot detect slow exfiltration will discover exposure when regulators or customers do.
Credential and session compromise becomes a privacy incident generator
If attackers can take over accounts, they can access personal data without breaking systems. This is why identity security trends discussed in endpoint security evolution matter for privacy: the compromise is often not malware, it is stolen trust. Regulators will increasingly treat repeated account takeover patterns as failure to safeguard personal data, especially when MFA is weak or session controls are absent.
Extortion and ransomware increase privacy impact through leak threats
Ransomware is not only about encryption. It is about coercion through data exposure. If you cannot prove what data was accessed and when, your breach notifications become uncertain and your legal exposure increases. This is why containment and recovery guidance in ransomware response must be paired with evidence discipline from incident response plans. Privacy risk is amplified when an organization cannot reconstruct the timeline.
Third party compromise becomes the fastest way to scale privacy harm
Organizations often do not monitor the actions of third parties with enough rigor. Attackers know this and target vendors, scripts, and integrations that sit near personal data. This becomes a privacy enforcement trigger because it shows weak governance. Mature organizations will adopt stronger validation and monitoring by mapping threats using CTI and building centralized visibility through next gen SIEM. If you cannot see third party behavior, you cannot defend or explain it.
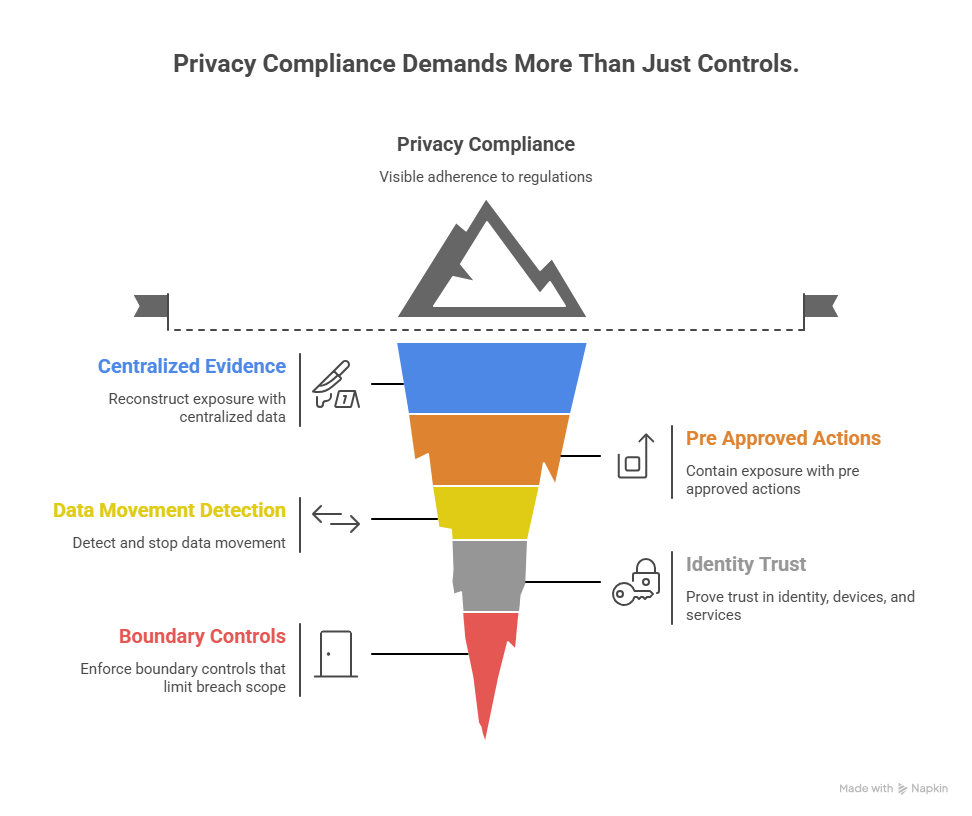
4) The New Compliance Driven Security Stack: What You Must Be Able to Do, Fast
From 2026 to 2030, privacy compliance will demand speed and precision. It will not be enough to say “we have controls.” You must demonstrate that controls work under pressure.
Capability 1: Reconstruct exposure fast with centralized evidence
Your organization must be able to answer: which identities accessed the data, from which devices, through which apps, and where it moved. This requires centralized telemetry based on SIEM fundamentals and enhanced correlation described in next gen SIEM evolution. Without centralized evidence, privacy reporting becomes an estimate, and estimates are dangerous in enforcement contexts.
Capability 2: Contain exposure with pre approved actions
Containment cannot be improvised. Privacy regulations will increasingly punish delayed containment, especially when personal data exposure continues after detection. Mature teams build pre approved containment actions using incident response execution: revoke sessions, suspend risky integrations, lock down exports, rotate keys, and restrict access to sensitive datasets until verification is complete. When extortion or ransomware is involved, recovery posture from ransomware response becomes part of privacy readiness.
Capability 3: Detect and stop data movement, not just malware
Most privacy failures will be data movement failures. You need controls that see exports, uploads, syncing behavior, and unusual access. This is why DLP strategy is increasingly a privacy requirement, and why encryption governance from encryption standards matters because it reduces harm even when attackers touch data. Pair DLP signals with threat driven tuning using CTI so detections are aligned to realistic attacker methods.
Capability 4: Prove trust in identity, devices, and services
Privacy regulations will pressure organizations to prevent unauthorized access. Strong identity controls and device trust become essential, and that trust is strengthened through concepts in PKI. Remote access is another common failure point, so controls like VPN security posture must be governed, monitored, and aligned with access policies.
Capability 5: Enforce boundary controls that limit breach scope
Even when a compromise happens, regulators will evaluate how much you limited the blast radius. Strong network boundaries and visibility are part of privacy defensibility. Use foundational controls like firewall configuration and detection approaches like IDS deployment to reduce lateral movement and detect suspicious access paths that could expand exposure.
5) A Privacy Ready Roadmap for 2026–2030: What to Build in the Right Order
This roadmap is designed to reduce legal exposure, cut breach impact, and create audit ready evidence.
Phase 1: Make your data map real, not aspirational
The first step is to identify where personal data lives, how it moves, and which systems can export it. Then you define sensitive categories and enforce stricter controls around them. Build monitoring and evidence around those flows using SIEM pipelines and stronger correlation from next gen SIEM. At the same time, implement practical data safeguards using DLP strategy so you can detect exfiltration through legitimate tooling.
Phase 2: Build fast incident proof
Privacy readiness is incident readiness. Define containment actions and practice them so response is consistent. Use playbook discipline from incident response execution and resilience guidance from ransomware response. Your objective is not to create a bigger document. It is to reduce time to contain and produce defensible evidence quickly.
Phase 3: Lock down identity and vendor access as the main control points
Most privacy exposure starts with identity compromise or vendor misuse. Strengthen identity trust with concepts grounded in PKI and ensure remote access is governed using VPN security posture. Then enforce strict vendor access controls and monitor vendor behavior in your central pipeline. Use threat intelligence practices from CTI collection to prioritize vendor risks and emerging attacker behaviors.
Phase 4: Treat encryption and key governance as compliance infrastructure
Encryption is no longer only a security best practice. It becomes compliance infrastructure that reduces harm and strengthens defensibility. Ensure encryption posture aligns with modern guidance from encryption standards, including key rotation, least privilege access to secrets, and protection of key material. Strong crypto posture reduces the severity of incidents and improves your ability to argue reduced risk when regulators ask hard questions.
Phase 5: Limit breach scope through segmentation and network visibility
Privacy regulations will increasingly look at the size of the breach, not just the fact that it happened. You reduce breach size by controlling lateral movement and monitoring access paths. Use practical boundary controls like firewall technologies and early warning visibility like IDS deployment. When paired with centralized logs, you can show regulators that your controls actively limited exposure.
6) FAQs: Privacy Regulations & Cybersecurity (2026–2030)
-
The biggest trend is the shift to “proof of control.” Regulators will expect organizations to demonstrate access governance, data movement protection, and fast incident timelines, not just publish notices. This makes centralized evidence pipelines using SIEM fundamentals and correlation improvements described in next gen SIEM essential. If you cannot reconstruct what happened quickly, your compliance posture becomes fragile during enforcement.
-
Because organizations must prove where data is stored and processed, and they must control how it moves between regions and vendors. That requires geography aware routing, access controls, and strong cryptographic protection. Encryption governance aligned to encryption standards reduces breach impact, while identity trust patterns grounded in PKI help secure services and devices across regions. Without these controls, cross border compliance becomes operationally risky.
-
They raise the bar on speed and evidence. You must contain exposure quickly and document exactly what you did, when, and why. That means standardized playbooks using incident response execution and resilience planning grounded in ransomware response. The organizations that practice containment and keep clean evidence will outperform those that improvise under pressure.
-
Silent exfiltration through trusted tools. Attackers and insiders often move data using legitimate exports, cloud syncing, and admin consoles. This is why DLP strategy is increasingly essential for privacy compliance, and why threat tuning using CTI matters so you detect realistic abuse patterns. If you only hunt malware, you will miss most privacy exposure.
-
Treat vendor access as privileged access. Maintain a processor inventory, enforce least privilege, monitor vendor behavior, and build the ability to shut access down immediately during suspicion. Central correlation via next gen SIEM helps you see vendor actions in context, while response consistency from incident response plans ensures containment is quick and defensible. Vendor incidents become your incident, so governance must be continuous.
-
Because encryption reduces harm when data is accessed, and regulators increasingly treat lack of strong encryption as negligence for sensitive categories. Modern approaches explained in encryption standards focus on strong algorithms plus proper key governance, rotation, and access controls. When you can prove encryption was correctly applied, you can reduce incident severity and strengthen your compliance narrative during investigations.
-
Metrics should prove outcomes: time to contain exposure, time to reconstruct scope, percent of sensitive data flows monitored, and percentage of privileged access governed and logged. These metrics are powered by evidence pipelines from SIEM fundamentals and faster correlation from next gen SIEM. Combine them with practice driven readiness using incident response execution to show regulators and leadership that controls work in reality.