Predicting the Future of Zero Trust Security: Innovations & Implications by 2030
Zero Trust is shifting from a network strategy into a business operating system. By 2030, the best programs will not be defined by “never trust, always verify” slogans. They will be defined by continuous authorization, identity context, device health, and policy enforcement that works across cloud, endpoint, SaaS, and third parties. If your Zero Trust plan is still a perimeter refresh with a new VPN, you will carry the same blind spots into a more hostile decade. This guide predicts the biggest innovations coming next and what they mean for real security outcomes.
1) Zero Trust by 2030: what changes, what stays, and what gets exposed
Zero Trust will stay rooted in one idea: access should be earned continuously, not granted permanently. What changes by 2030 is the enforcement surface. Policies will follow identities and workloads across hybrid infrastructure, not stop at the firewall. That evolution tracks with how standards and governance are tightening in The Next Generation of Cybersecurity Standards and how oversight keeps expanding in Cybersecurity Compliance Trends Report 2025. The more regulated your industry becomes, the less tolerance there will be for “informal admin access” and undocumented exceptions.
The biggest misconception is that Zero Trust is primarily a networking project. By 2030, Zero Trust is primarily an identity, endpoint, and data control project. Identity is the new control plane, which is why privacy laws and cybersecurity strategy are converging across regions in Privacy Regulations and Cybersecurity Global Trends and policy expectations will keep rising under GDPR 2.0 Predictions. If your identity layer is weak, your Zero Trust implementation becomes a thin wrapper over broad access.
Zero Trust also becomes more measurable by 2030. Boards will ask for proof, not narratives. They will want to see coverage, enforcement, and time based outcomes. That pressure aligns with the evolution of audits in Future Cybersecurity Audit Practices and the increasing expectation that security controls are testable, repeatable, and logged. This is where many programs break, they implement policy, but cannot prove it is consistently enforced.
Another major shift is that Zero Trust is becoming automation dependent. Manual review cannot keep up with modern access patterns, contractors, SaaS sprawl, and cloud resources. That operational reality is consistent with the direction in Automation and the Future Cybersecurity Workforce and the skill requirements outlined in Future Skills for Cybersecurity Professionals. If your policy enforcement relies on humans approving everything, your program will slow the business and eventually get bypassed.
Finally, Zero Trust will be shaped by threat pressure. Attackers keep pivoting toward identity abuse, endpoint footholds, and cloud control plane exploitation. That pattern is visible in the broader threat landscape framing in State of Ransomware 2025 and what endpoint capabilities need to become in Advances in Endpoint Security Solutions by 2027. A Zero Trust program that ignores endpoint posture and identity telemetry will not withstand modern intrusion paths.
2) Innovations that will define Zero Trust outcomes by 2030
The biggest innovation is continuous authorization. Traditional access checks happen at login, then the session is trusted until logout. By 2030, session risk changes will trigger real time enforcement. If a user’s token is reused from a new device or location, access should downgrade automatically. This is the practical bridge between identity security and threat disruption, which ties directly to the threat pressure described in State of Ransomware 2025 and the detection modernization direction in Next Gen SIEM Technologies to Watch. When attackers rely on “valid logins,” continuous authorization becomes a containment tool.
Passwordless adoption will accelerate because passwords remain a root cause of compromise at scale. By 2030, mature organizations will treat reusable secrets as legacy debt. Passwordless only works if device trust is strong, enrollment is controlled, and recovery processes cannot be socially engineered. That skill and process discipline connects to the workforce readiness themes in Future Skills for Cybersecurity Professionals and the pressure to standardize security practices in The Next Generation of Cybersecurity Standards. Security outcomes will increasingly depend on how well your organization operationalizes identity hygiene.
Policy as code will reshape governance. Instead of manual configuration across dozens of tools, organizations will define policies centrally, version them, test them, and deploy them consistently. This is where Zero Trust becomes auditable and scalable. If you cannot prove which policy existed at which time, you cannot answer auditors confidently during incidents. That reality aligns with the evolution described in Future Cybersecurity Audit Practices and the expectations of compliance frameworks tracked in Cybersecurity Compliance Trends Report 2025. By 2030, policy maturity will become a competitive advantage, not just a defense measure.
Zero Trust will also rely more heavily on automated decisioning. High quality automation is not about replacing analysts, it is about making enforcement reliable. If your environment generates thousands of access events and alerts daily, humans cannot mediate them all. Automation helps you apply consistent containment actions when risk spikes. This is consistent with the operational shift discussed in Automation and the Future Cybersecurity Workforce and the monitoring stack evolution in Next Gen SIEM Technologies to Watch. The organizations that win will be the ones that automate the predictable decisions.
Finally, endpoint trust will remain central. If a compromised endpoint is treated as trusted, Zero Trust collapses. By 2030, device posture and EDR context must be deeply integrated into access decisions. That integration aligns with the direction of capability upgrades outlined in Advances in Endpoint Security Solutions by 2027 and the reality check provided by State of Endpoint Security 2025. Zero Trust cannot be identity only, it must be identity plus device truth.
3) Implications by 2030: what Zero Trust will force businesses to change
Zero Trust will force clarity about “crown jewels.” If you cannot identify the data and systems that define your business value, your policies will be generic. Generic policies waste user patience and still miss the real risk. The most effective programs will classify critical datasets and apply stronger authentication, tighter access scopes, and stricter monitoring around them. This becomes more important as privacy regulation pressure rises through Privacy Regulations and Cybersecurity Global Trends and evolves under GDPR 2.0 Predictions. If a breach happens, your ability to show data control discipline impacts outcomes.
Zero Trust will also expose vendor and contractor risk. By 2030, supply chain access will be a primary intrusion route, especially for organizations that outsource IT, development, or operations. Vendor access must become time bound, scope bound, and continuously monitored. If a third party can access broad internal networks, your perimeter is effectively their security program. That risk grows as legislation tightens, especially for smaller businesses, which is why programs should track direction in Cybersecurity Legislation Impact on SMBs and the control expectation trend in Cybersecurity Compliance Trends Report 2025. You need vendor governance that does not rely on trust.
Another implication is that Zero Trust will become inseparable from detection and response. If you cannot detect identity abuse and endpoint compromise fast, policy enforcement will lag behind attacker actions. Zero Trust should generate containment opportunities, not just prevent access. If identity risk spikes, access should downgrade, endpoints should isolate, and the SOC should receive a high confidence alert. This operational loop depends on the visibility and correlation described in Next Gen SIEM Technologies to Watch and the endpoint capability path in Advances in Endpoint Security Solutions by 2027. Zero Trust without detection maturity becomes a brittle access system.
Zero Trust will also reshape how organizations think about resilience. The goal is not only to prevent compromise, it is to stay operational when compromise happens. That is why Zero Trust must include break glass access design, immutable logging, and tested incident workflows. Those expectations will align with audit innovations in Future Cybersecurity Audit Practices and broader standardization pressure in The Next Generation of Cybersecurity Standards. By 2030, resilience will be a control requirement, not a bonus.
Finally, Zero Trust will pressure teams to upgrade skills. Identity engineering, policy design, cloud governance, and automation will become core competencies. If your team lacks these capabilities, your program will stall. This maps directly to the talent direction in Future Skills for Cybersecurity Professionals and the operational shift described in Automation and the Future Cybersecurity Workforce. Zero Trust is a capability maturity problem, not just a tooling decision.
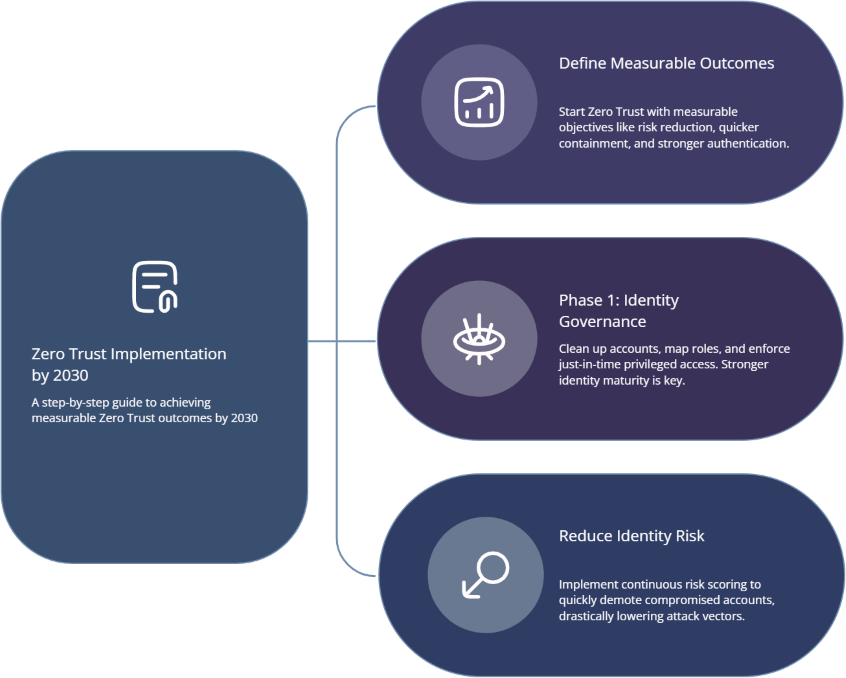
4) How to implement Zero Trust for real outcomes by 2030
A Zero Trust roadmap fails when it starts with tools instead of control intent. Start with outcomes you can measure: reduced standing privileges, shorter access durations, stronger authentication for high risk actions, and faster containment when risk spikes. That outcome focus aligns with compliance pressure in Cybersecurity Compliance Trends Report 2025 and audit scrutiny in Future Cybersecurity Audit Practices. If you cannot measure progress, you cannot defend your program during scrutiny.
Phase one is identity cleanup and governance. Map privileged roles, remove dormant accounts, and implement just in time access for administration. Make high risk access require stronger authentication. Add continuous risk scoring so compromised sessions can be downgraded quickly. This identity maturity approach also reduces ransomware leverage, linking directly to risk trends in State of Ransomware 2025 and the broader standards direction in The Next Generation of Cybersecurity Standards. Identity weakness will remain the fastest route to business compromise.
Phase two is device trust as a gate. Treat device posture as a dynamic signal, not a one time check. Require patched, encrypted, and monitored devices for sensitive access. Build isolation automation for endpoints that show high confidence compromise signals. This aligns with practical capability trajectories in Advances in Endpoint Security Solutions by 2027 and performance realities discussed in State of Endpoint Security 2025. If your posture checks can be bypassed, Zero Trust becomes theater.
Phase three is policy consolidation. Move toward policy as code, where enforcement rules are versioned, tested, and centrally governed. Integrate identity, device posture, and cloud context into unified decisions. This is where tooling matters, but only if you reduce fragmentation. The architecture thinking is reinforced by Next Gen SIEM Technologies to Watch and the operational shift described in Automation and the Future Cybersecurity Workforce. A policy system that cannot move at machine speed will lag behind attackers.
Phase four is resilience validation. Practice incident workflows under realistic conditions. Verify that logs are preserved, access can be downgraded quickly, and business critical functions continue. This is where Zero Trust becomes defensible under audit, aligning with Future Cybersecurity Audit Practices and compliance evolution in Privacy Regulations and Cybersecurity Global Trends. Resilience is the difference between an incident and a shutdown.
5) The Zero Trust mistakes that will hurt the most by 2030
The first mistake is treating Zero Trust like a network refresh. Replacing VPN with ZTNA is useful, but it is not a Zero Trust program by itself. Without identity governance, device trust, and data controls, you still have broad access with different plumbing. This mistake becomes more expensive as privacy regulations tighten under GDPR 2.0 Predictions and global expectations evolve in Privacy Regulations and Cybersecurity Global Trends. Regulators do not care which product you bought, they care whether access was controlled.
The second mistake is allowing exceptions to become permanent. Every exception becomes a backdoor attackers can exploit. By 2030, program maturity will be judged by how quickly exceptions expire and how tightly they are logged. This is where audit expectations matter, connecting directly to Future Cybersecurity Audit Practices and broader standards direction in The Next Generation of Cybersecurity Standards. If exceptions cannot be defended, they will be flagged.
The third mistake is underestimating third party access. Vendors and contractors often have broad reach because it is convenient. By 2030, that convenience becomes a leading cause of compromise. Build vendor access segmentation, time bound entitlements, and monitoring around third party sessions. This is especially important as policy pressure rises for smaller organizations under Cybersecurity Legislation Impact on SMBs and compliance expectations tighten through Cybersecurity Compliance Trends Report 2025. Supply chain risk is not theoretical anymore.
The fourth mistake is ignoring endpoint truth. If devices are not consistently managed, patched, and monitored, access decisions are based on incomplete trust. This becomes lethal when attackers use compromised endpoints to steal tokens and pivot quietly. That is why endpoint evolution matters, as described in Advances in Endpoint Security Solutions by 2027 and measured reality in State of Endpoint Security 2025. Zero Trust cannot ignore the endpoint.
The fifth mistake is failing to integrate detection and response. If Zero Trust policies do not trigger containment actions when risk changes, you miss the biggest benefit. Mature programs connect identity risk scoring to SOC workflows and automated response playbooks. This integration becomes more necessary as threat pressure continues through ransomware economics in State of Ransomware 2025 and as monitoring stacks evolve in Next Gen SIEM Technologies to Watch. Speed is the new perimeter.
6) FAQs
-
Measure whether access is continuously controlled, not just granted at login. Track reductions in standing privileges, average access duration for admin roles, and how often risky sessions are downgraded automatically. Then measure time to contain identity based anomalies. This measurement approach aligns with the governance expectations in Future Cybersecurity Audit Practices and policy pressure in Cybersecurity Compliance Trends Report 2025.
-
They fail because tools do not replace governance. Without entitlement cleanup, consistent device posture enforcement, and policy consistency, users accumulate broad access over time. Exceptions become permanent and attackers exploit them. Standards and audit pressure described in The Next Generation of Cybersecurity Standards and Future Cybersecurity Audit Practices will make this failure mode more visible by 2030.
-
Ransomware increasingly relies on identity abuse and lateral movement. Zero Trust reduces blast radius by limiting what identities and devices can reach, and by revoking access when risk changes. It also improves detection when identity and endpoint context are correlated. This aligns with threat direction described in State of Ransomware 2025 and the capability curve in Advances in Endpoint Security Solutions by 2027.
-
Start with identity hygiene and vendor access control. Use phishing resistant MFA for admins, remove unused accounts, limit third party access scope and duration, and enforce basic device posture for sensitive access. Small businesses face rising policy expectations, which is why direction in Cybersecurity Legislation Impact on SMBs and control trends in Cybersecurity Compliance Trends Report 2025 matter for planning.
-
Privacy regulations push organizations to prove access control discipline over sensitive data. That means stronger authentication for high risk data, clearer entitlements, better logging integrity, and defensible policy enforcement. These pressures grow through Privacy Regulations and Cybersecurity Global Trends and are reinforced by the direction described in GDPR 2.0 Predictions.
-
Teams will need identity engineering, policy design, cloud governance, automation, and investigation workflows that connect access context to response. These competencies align with the skill direction in Future Skills for Cybersecurity Professionals and the operating model shift in Automation and the Future Cybersecurity Workforce. The gap between tools and outcomes is mostly a skills gap.
-
Use risk based enforcement. Strongly authenticate only when risk is high, and automate decisions for common scenarios. Consolidate policies, reduce fragmentation, and use unified evidence for fast response. This approach depends on monitoring and correlation maturity discussed in Next Gen SIEM Technologies to Watch and on measurable governance expectations in Future Cybersecurity Audit Practices. Speed and consistency are the only way to scale.