Deepfake Cybersecurity Threats: How to Prepare for the Upcoming Wave (2026 Insights)
Deepfakes are not a future problem. In 2026, they are a scaling problem. The tech is cheap, the quality keeps climbing, and the delivery channels are everywhere. The risk is not only fake videos. It is fake voice approvals, fake executives, fake vendors, fake candidates, and fake evidence used to force rushed decisions.
This guide breaks down how the deepfake threat wave will hit real organizations, which attack paths will dominate through 2030, and the practical controls that actually reduce losses.
1. Why Deepfakes Become a Top Tier Cyber Risk in 2026
Deepfakes are dangerous because they exploit the human layer that most security stacks treat as “out of scope.” Your EDR can be perfect and you can still lose six figures if accounting wires money after a convincing voice call. Your IAM can be tight and you can still leak sensitive data if an employee shares screenshots during a fake Zoom “urgent incident review.” That is why deepfakes sit at the intersection of identity abuse, social engineering, and governance. To frame this correctly, connect deepfakes to the shift toward identity and behavior centric defense in AI adoption and security impact, then link the entry methods to modern phishing trend patterns, and the business fallout to the 2025 data breach report.
The next reason deepfakes scale is operational pressure. Teams are remote, decisions are asynchronous, and “quick approvals” happen over chat, voice notes, and short calls. Attackers aim for the moment your process becomes informal. They do not need to fool your best people. They only need to hit the one person who is tired, rushed, and trying to be helpful. That is why deepfake readiness is a workforce readiness problem as much as a tool problem. Build the skills layer using future competencies by 2030 and align the operating expectations to next generation standards, because many organizations will soon be expected to prove controls against impersonation and fraud.
Deepfakes also introduce a new kind of incident: the “credibility incident.” Even if the content is fake, the damage can be real. Reputation loss, customer panic, executive distraction, legal escalation, and internal distrust can hit before you confirm facts. That is why you need an evidence ready response model that can handle manipulation, not only malware. Tie incident response planning to the audit and evidence mindset described in future audit practices, then map policy requirements to the direction in future compliance trends, and keep privacy exposure in focus using privacy regulation forecasting.
Finally, deepfakes link directly to ransomware and extortion. Crews can use synthetic voice or video to increase pressure, fabricate “proof,” or manipulate executives into paying fast. If you want the broader economic context of modern extortion, ground your threat model in the state of ransomware analysis and connect it to the evolving security stack direction in next gen SIEM planning.
| Attack Path | How It Works | Impact | Best Defense | Owner |
|---|---|---|---|---|
| Voice wire fraud | Synthetic executive voice requests urgent payment | Direct financial loss | Out of band approval + verified vendor workflow | Finance + Security |
| Fake vendor onboarding | Deepfake call confirms bank details and legitimacy | Payment diversion | Two person verification + domain and account checks | Procurement |
| CEO emergency Zoom | Synthetic video pressures staff to bypass controls | Policy bypass, data leakage | Code word protocol + meeting verification steps | Exec Ops |
| Helpdesk reset impersonation | Voice clone claims locked out and needs reset | Account takeover | Strong identity proofing + no voice only resets | IT + IAM |
| Recruiting identity spoof | Candidate uses deepfake to pass interviews | Insider access risk | Liveness + verified identity checks | HR + Security |
| Fake employee onboarding | Synthetic identity gets hired to gain access | Persistent internal foothold | Background verification + device enrollment controls | HR + IT |
| Customer support manipulation | Deepfake call to change account details | Fraud, takeover | Step up auth + callback to verified number | Support |
| Fake legal notice | Synthetic video or audio claims urgent legal threat | Panic driven actions | Legal verification workflow + evidence validation | Legal |
| Synthetic extortion proof | Fake recordings used to pressure payment | Rapid payout risk | Crisis protocol + technical verification + comms plan | IR + Comms |
| Fake incident command | Impersonation “runs” response and harvests info | Data leakage, chaos | Verified war room access + identity checks | Security |
| Deepfake CFO invoice approval | Voice note approves invoices quickly | Fraudulent payments | Approval in system only + dual control | Finance |
| Synthetic board member call | Voice clone requests privileged data | Sensitive data exposure | Sensitive data request policy + verification | Exec Ops |
| KYC liveness bypass attempts | Synthetic video tries to pass verification | Fraud and compliance risk | Advanced liveness + device risk scoring | Risk |
| Fake PR crisis video | Synthetic exec statement goes viral | Brand damage | Provenance workflows + rapid comms response | Comms |
| Fake client meeting recording | Synthetic “evidence” changes deal terms | Contract disputes | Signed summaries + verified recording storage | Sales + Legal |
| Deepfake training social engineering | Fake “security training” call gathers credentials | Credential theft | Official training channels only + ITDR | Security |
| Synthetic voice MFA fatigue | Call pressures target to approve push prompts | Account takeover | Number matching + conditional access | IAM |
| Executive assistant compromise | Deepfake exec requests calendar and access help | Privilege bridging | High risk role protections + training | Exec Ops |
| Fake supplier dispute escalation | Synthetic calls force “quick settlement” payments | Financial loss | Dispute workflow + verified contacts | Procurement |
| Deepfake internal policy update | Fake exec message changes process temporarily | Control bypass | Signed comms + known channels | Security + HR |
| Synthetic voice for bank verification | Attackers pass voice verification with cloned audio | Account fraud | Multi factor verification + fraud monitoring | Finance |
| Fake regulator call | Synthetic authority pressures disclosure or action | Compliance error | Regulator verification + legal escalation path | GRC |
| Impersonated IT admin | Voice clone requests privileged access for “fix” | Privilege escalation | Privileged access controls + ticket verification | IT |
| Deepfake audio in court or HR claims | Fake evidence used for disputes | Legal and HR exposure | Evidence provenance + secure recording chain | Legal + HR |
| Crisis misinformation targeting customers | Fake exec video triggers panic and support overload | Operational disruption | Rapid comms playbook + verified channels | Comms |
| Deepfake “partner” introduction | Synthetic identity opens trust with staff | Long con infiltration | Partner verification + least privilege access | Biz Ops |
| Fake medical or safety emergency call | Authority voice pushes urgent action | Procedural bypass | Emergency verification + escalation rules | Operations |
| Synthetic “confidential” media request | Deepfake journalist pressures for comment or files | Sensitive disclosure | Media request workflow + comms approval | Comms + Legal |
| Deepfake based stock manipulation attempt | Fake exec statement influences market perception | Financial and legal fallout | Provenance + rapid verification and disclosure plan | Legal + Comms |
2. The 2026 Deepfake Kill Chain: Where Attacks Actually Start and How They Scale
Most deepfake attacks start with one of three things. First, leaked audio from podcasts, webinars, investor calls, or internal town halls. Second, social media clips and short videos that provide clean facial angles and voice samples. Third, stolen internal recordings from meetings or support calls. Once an attacker has “training material,” the attack becomes a process, not an art. That is why you need a mindset shift away from “spot the fake” and toward “verify the request.” Build that mindset using the behavior focused thinking in future skills for cybersecurity professionals, then map it to governance expectations in future compliance trends, and anchor the social engineering layer in phishing trends and prevention.
The next phase is channel selection. Deepfakes work best in channels where people assume authenticity. Voice calls, voice notes, video calls, and screen shares have a trust bias. Attackers exploit urgency, authority, and confidentiality. “I cannot talk long.” “This is sensitive.” “Do not escalate.” That language is a control bypass attempt. Your job is to make bypass attempts fail by designing controls that slow down fraud without slowing down the business. This is where standards and evidence matter. If you have a policy that says “two person approval,” but it is optional in practice, you have no control. For a standards lens, use next generation cybersecurity standards, and for evidence expectations, align to future audit practice evolution.
The scaling factor from 2026 to 2030 is personalization. Deepfake attacks become more targeted because attackers combine AI voice with OSINT, breached data, and internal process knowledge. That means the “script” references your real vendors, your real projects, your real meeting cadence, and your real people. This is where breach data creates second order damage. A breach does not just leak passwords. It leaks context. Use the exposure framing in the 2025 data breach report, and connect privacy risk to privacy regulations forecasting and the compliance reality in GDPR and cybersecurity challenges.
Deepfake operations also benefit from tool evolution in security stacks. Attackers increasingly aim for identity and access. They do not need to break in if they can talk their way into a reset, a token, or a credential approval. That is why modern security programs focus on identity behavior and response speed. Use the modernization direction in next gen SIEM and the broader shift in AI in cybersecurity adoption to build a detection approach that surfaces identity anomalies, not just malware.
3. Deepfake Readiness Controls: What Actually Stops Losses
If you want results, focus on controls that interrupt decision making, not controls that hope humans spot pixels. Start with high value workflows: wire transfers, vendor changes, payroll updates, executive approvals, password resets, and customer account changes. Then enforce a simple rule: no high impact change happens based on a single channel. If a voice call requests a wire, approval must happen in the finance system with two people, plus a callback using a known number from a verified directory. If a video call requests sensitive data, the request must be submitted through the ticketing system, then approved by a second owner. This is governance that functions. It also produces evidence, which matters under the trend lines in cybersecurity compliance reporting and the accelerating expectations in future compliance trends.
Next, harden identity workflows because deepfakes often target support desks and admin paths. Reduce voice only authentication. Use step up verification for resets. Protect high risk roles such as finance approvers, payroll admins, executive assistants, and IT admins with stronger conditional access. When identity is protected, deepfake attacks become less profitable. This aligns with the direction of modern security stacks discussed in endpoint security advancements and the broader framework adoption perspective in NIST adoption analysis.
Then build detection where it matters. Deepfake detection tools exist, but they are not magic and they can be bypassed. Treat detection as an assist, not a guarantee. The stronger play is correlation. If a request comes from “the CEO,” correlate it with travel location, usual channels, recent behavior, and device posture. If the request is abnormal, force verification steps. This is why SIEM modernization and evidence pipelines matter. Connect your approach to the strategy in next gen SIEM technologies, and measure your readiness through audit minded logging described in future audit practices.
Finally, train for the right behaviors. Generic security awareness does not stop deepfakes. You need micro drills tied to real workflows. Train finance on wire fraud scripts. Train HR on candidate verification and onboarding controls. Train executives on how their public content is used to clone them. This is where security becomes culture. Build your enablement strategy using future skills and competencies and map it to role specialization in specialized cybersecurity roles demand.
Quick Poll: Where Would a Deepfake Hurt Your Organization Most in 2026?
Deepfakes win when urgency beats verification. Pick the scenario that feels most realistic in your environment.
4. Detection, Forensics, and Evidence: How to Respond When You Cannot Trust Media
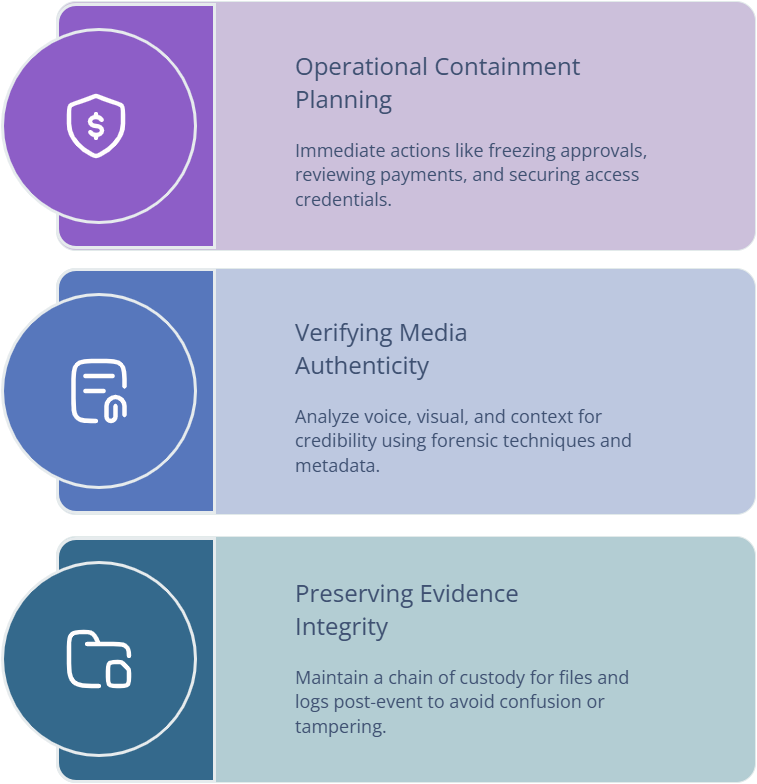
When deepfakes are in play, your incident response must treat media as untrusted input until verified. That does not mean you ignore it. It means you validate it through provenance, context, and supporting system logs. The best response teams separate two tracks. Track one is operational containment, which focuses on access, payments, and data movement. Track two is credibility management, which focuses on communications, legal posture, and customer trust. This split reduces chaos, which matters under the evidence expectations in future audit practices and the regulatory direction in future compliance trends.
Start with containment. If a deepfake was used to request a wire, freeze approvals and verify all pending payments. If it targeted the helpdesk, force credential resets for affected users, review MFA changes, and check token issuance. If it involved screen sharing, assume data exposure and trace access logs. Do not wait for perfect attribution. Deepfake response is about blocking loss quickly. Align this to incident economics covered in ransomware threat analysis and the common credential entry dynamics described in phishing prevention research.
Then move to verification and forensics. You need a way to confirm whether the “voice” was real, whether the “meeting” was legitimate, and whether the “recording” was altered. This is not only a technical task. It is a chain of custody task. Preserve original files, capture metadata, record who received it and when, and store it in a controlled repository. Even if you never go to court, having clean evidence protects your organization from internal confusion. Build your evidence approach around control expectations and documentation discipline using NIST adoption insights and cybersecurity compliance reporting.
The SIEM layer matters here because SIEM is where you prove context. Who logged in. From where. What changed. Which accounts were touched. What files were accessed. If you cannot answer those questions fast, your response becomes debate, not action. That is why the modernization push in next gen SIEM technologies is directly relevant to deepfake response, even though deepfakes are a “human” problem.
Finally, build a credibility response plan. Decide in advance who approves public statements, who contacts affected partners, and how you communicate without amplifying misinformation. This matters in sectors where public trust is fragile, such as healthcare and finance. Use sector context from healthcare cybersecurity predictions and finance cybersecurity trends, and map public sector implications using government cybersecurity analysis.
5. The 2026 to 2030 Roadmap: Deepfake Preparedness That Scales
Deepfake defense fails when it is treated as a single tool purchase. It must be a layered program built into workflows. Start in 2026 with the highest loss pathways. Finance and procurement must have a strict verified vendor and payment change workflow. IT and IAM must harden helpdesk resets. HR must upgrade identity verification for hiring and onboarding. Executives must adopt simple verification habits and reduce avoidable exposure of clean training audio. Build your first year program using the workforce planning direction in future cybersecurity skills and the specialization trend in specialized roles demand.
From 2027 to 2028, formalize evidence and compliance integration. Organizations will be pushed to show how they prevent impersonation fraud, protect customers, and manage misinformation incidents. That pressure is consistent with future compliance trends and the evolving expectations in future audit practices. Put verification protocols into policy. Train teams with scenario drills. Create metrics such as number of attempted impersonations caught, time to verification, and percentage of high impact requests that follow approved channels.
From 2028 to 2030, expect deepfake attacks to merge with broader AI enabled fraud. Synthetic identity, AI generated documents, fake customer calls, and automated social engineering will blend into one continuous fraud machine. Your defense needs to be systematic. Strong identity governance, risk based verification, and consistent telemetry will matter more than any single detector. Use the long term direction from AI adoption and impact, the standards lens in next generation cybersecurity standards, and the control evidence mindset in compliance trend reporting.
Do not ignore the privacy dimension. Deepfake defenses often involve collecting verification data, biometric signals, or behavioral analytics. That creates privacy risk if handled carelessly. Design privacy into your verification flows and retention policies. Use the regulatory direction in privacy regulations forecasting and the compliance realities described in GDPR and cybersecurity best practices, so your defense does not create a new compliance problem.
6. FAQs: Deepfake Cybersecurity Threats (2026 Insights)
-
Traditional phishing asks you to click or type. Deepfakes pressure you to obey. They weaponize authority, urgency, and emotional realism to bypass normal skepticism. The best defense is not “spot the fake,” it is enforcing verification steps for high impact actions, aligned to social engineering patterns in phishing prevention research and the control evidence mindset in future audit practices.
-
A strict out of band approval rule for high impact requests. Payments, vendor changes, password resets, and sensitive data requests must require verification through an approved system and a second person. This is measurable and enforceable, which supports the direction in cybersecurity compliance reporting and the growing pressure described in future compliance trends.
-
Detection tools can help, but they should not be your primary control. Attackers can evolve quickly and false positives can cause distrust. Use detection as a signal, then rely on process controls and telemetry correlation, consistent with the modernization direction in next gen SIEM technologies and the broader view in AI adoption and impact.
-
Synthetic candidates can pass interviews, get hired, and then gain internal access. That can be used for credential harvesting, data theft, or staging future attacks. Strong identity verification and controlled device enrollment are essential. This workforce angle ties directly to future skills and competencies and the specialization trend in specialized roles demand.
-
Preserve the original file, its metadata, the channel it arrived through, the exact timestamps, and any related identity or system logs. Capture who received it and what actions were taken. Store it in a controlled repository to maintain chain of custody. This supports audit and legal defensibility aligned with future audit practices and control frameworks discussed in NIST adoption analysis.
-
Any industry with high value transactions, regulated data, or public trust exposure. Finance faces fraud and market manipulation risk, healthcare faces privacy and trust damage, government faces misinformation and operational disruption. Use sector context from finance cybersecurity trends, healthcare cybersecurity predictions, and public sector threat analysis.
-
Train by workflow, not by fear. Run short scenario drills on wire approvals, helpdesk resets, vendor changes, and sensitive data requests. Teach the verification steps and make them easy. The goal is confident behavior under pressure, consistent with the workforce strategy in future cybersecurity skills and the risk reality described in the data breach report.