Career Roadmap: Becoming a Cybersecurity Curriculum Developer
Becoming a cybersecurity curriculum developer is not about making slides. It is about building job ready skill systems that turn chaos into capability. If your content is generic, learners feel it and hiring managers ignore it. This roadmap shows how to pick a niche, map real workflows, build labs that mirror real attacks, and prove outcomes with measurable assessments. You will leave with a step by step path to become the person organizations trust to train analysts, engineers, and leaders.
1. Choose a curriculum lane that hiring managers actually pay for
“Cybersecurity curriculum developer” is too broad. The fastest path is to specialize in a lane where organizations already spend money and where the job tasks are clear. Start by picking one primary audience and one primary outcome.
A high demand lane is the SOC pipeline because security leaders need analysts who can triage alerts, write clean notes, and escalate with evidence. Anchor your lane around day one readiness for analysts using the workflows from how to become a SOC analyst step-by-step and map progression to team leadership using from SOC analyst to SOC manager. Then align your skill map with what the market keeps demanding in predicting cybersecurity job market trends and the competency clusters in future skills for cybersecurity professionals.
Another strong lane is offense and validation for teams that need pen testing and internal assurance. If you go this route, structure your roadmap around capability milestones from how to become an ethical hacker and advanced consulting pathways like junior penetration tester to senior security consultant. Pair that with real world constraints from the compliance side by linking labs to audit evidence and policy expectations found in future cybersecurity audit practices and the direction of next generation cybersecurity standards.
Here is the reality: learners quit when the content feels like theory, and employers stop trusting training when graduates cannot perform under pressure. Your lane choice must make it easy to answer one question: “What can a learner do on day one that they could not do before?” Use future facing trends to keep your lane modern, like AI powered cyberattacks and the knock on effects of automation and the future cybersecurity workforce.
2. Build your foundation like a security professional, not a content writer
Curriculum developers get rejected because they cannot speak the language of real operations. To fix that, you need a technical spine plus a “how work actually happens” mindset.
Start with a practical security workflow baseline. If your curriculum touches SOC work, your foundation must include triage, investigation, escalation, and documentation. Use the structure from complete guide to becoming a SOC analyst and reinforce career progression signals with SOC analyst to SOC manager salary, skills, and certifications. If your lane is leadership and governance, build credibility by understanding the pressures security leaders face, then connect to management paths like how to become a cybersecurity manager and executive trajectories in chief information security officer roadmap.
Then add “future relevance” so your curriculum does not feel like it belongs in 2019. Employers are optimizing for AI shaped threat models, cloud dominant environments, and identity abuse. That is why you should weave your foundation into macro themes like future of cloud security, predicting the future of zero trust, and the shift in controls and evidence expectations described in future of cybersecurity compliance.
If you skip this foundation, you will keep producing the kind of content learners hate: definitions, lists, and shallow “best practices.” What teams need instead is training that prepares people to make decisions when signals conflict, when logs are incomplete, and when leadership wants answers now. Tie your baseline to real pressure points using sector contexts like healthcare cybersecurity predictions and cybersecurity trends in finance so your curriculum teaches tradeoffs, not fantasies.
3. Design the curriculum the way security teams think: workflows, evidence, and failure modes
A strong cybersecurity curriculum is built from workflows. A weak curriculum is built from topics. Topics make learners feel like they are learning, but workflows make them perform.
Start by mapping the end to end process for your target role. For a SOC track, map “alert intake to closure.” For an offensive track, map “scoping to reporting.” For GRC, map “control intent to audit evidence.” Then build modules that mirror how work moves. This is where your content becomes credible, because it reflects real friction.
Next, bake in failure modes. Security work is full of mistakes that look small but cause big damage: wrong assumptions, missing context, poor documentation, overconfidence in tools, and slow escalation. Use trend pieces like next-gen SIEM innovations to highlight why alert volume and correlation problems are getting worse, not better. Then design labs where learners must reduce noise, validate evidence, and justify decisions.
Now make your assessments performance based. Multiple choice does not prove capability in security. You need rubrics that evaluate artifacts: investigation notes, screenshots, query outputs, remediation steps, and executive summaries. This aligns with the direction employers are moving toward as described in cybersecurity certifications of the future and the broader skills shift highlighted in future skills.
Finally, keep the curriculum alive. Security changes fast. Your content must evolve with emerging threats like deepfake cybersecurity threats and the business impact trends in global cybersecurity market report. The best curriculum developers become trusted because they ship updates like a product team, not a textbook author.
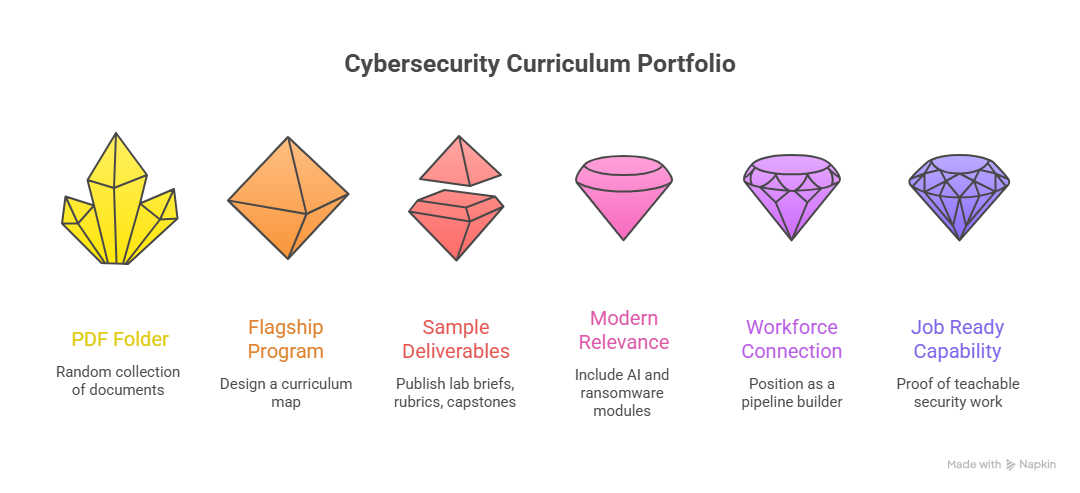
4. Build a portfolio that proves outcomes, not effort
A cybersecurity curriculum portfolio is not a folder of PDFs. It is proof that you can produce job ready capability. Employers and clients want to see two things: your curriculum design thinking and your ability to translate real security work into teachable steps.
Start with one flagship program. Pick a role and publish a “curriculum map” that shows modules, labs, and assessment artifacts. Your map should look like a real operations pathway, similar to how career paths are laid out in career roadmap to CISO or the structured progression in career roadmap how to become a cybersecurity auditor. This signals you understand progression, not random topic coverage.
Then publish sample deliverables. The most convincing samples are:
A lab brief that includes objective, evidence required, and pass criteria
A grading rubric that shows how you judge quality
A capstone brief that ties multiple modules into one incident
A “gold standard” submission that learners can compare themselves against
Your portfolio must also show modern relevance. Include at least one module on AI shaped threats and defenses using the framing from AI-driven cybersecurity tools and one module on ransomware evolution using next big ransomware evolution. This helps buyers trust that your curriculum will not be obsolete the moment it launches.
Finally, connect your curriculum to workforce reality. Security teams are under staffed, drowning in alerts, and judged by response speed. If your training does not reduce time to competence, it will not survive budget reviews. Use the logic from predicting demand for specialized roles to position your curriculum as a pipeline builder, not a nice-to-have learning program.
5. Get hired or win clients: the positioning that separates pros from hobbyists
Most people try to sell “cybersecurity training.” That is a weak offer. A strong offer is a measurable outcome that fixes a painful business problem.
If you want an internal role, position yourself as the person who can build repeatable capability across teams. Organizations want consistent performance, not individual heroics. That aligns with the workforce direction described in automation and the future workforce, because companies are standardizing workflows and expecting training to produce predictable outputs. Your pitch should sound like: “I build job task aligned curriculum with labs and rubrics that reduce ramp time and raise incident handling quality.”
If you want clients, pick an industry problem and build a training package around it. Sector specific framing increases trust instantly. For example:
Healthcare security training grounded in healthcare cybersecurity predictions
Finance security training aligned with cybersecurity trends in finance
Public sector readiness anchored in predictive analysis in government
Also, do not ignore compliance. Even technical teams get evaluated through regulatory pressure. Build modules that teach audit evidence and control mapping, using the future direction outlined in privacy regulations emerging trends and the likely evolution discussed in GDPR 2.0. This makes your curriculum valuable to security leaders, not just learners.
If you want a straight line blueprint, study how the role is framed in the dedicated pathway piece on becoming a cybersecurity curriculum developer and pair it with the broader training career framing in becoming a cybersecurity instructor or trainer. Then build your portfolio around measurable outcomes, not content volume.
6. FAQs
-
No, but you must be able to design around real workflows and evidence. You can start by specializing in one lane, like SOC readiness, and building labs tied to real tasks from SOC analyst roadmaps. The key is not seniority, it is accuracy. If you can map tasks, build assessments, and validate with SMEs, you can be effective while still growing your technical depth through focused tracks like ethical hacker pathways.
-
Build one flagship module with a lab, a rubric, and a capstone style submission. Your proof should include the lab brief, required evidence, and pass criteria. Anchor your module in a modern threat area like ransomware evolution or AI-powered cyberattacks. This instantly signals you can teach what matters now, not what mattered years ago.
-
Treat curriculum like a product with releases. Maintain a quarterly refresh cycle driven by trend monitoring from sources like future of cloud security and next-gen standards. Update labs when workflows shift, update assessments when evidence expectations change, and publish a changelog. Buyers trust creators who show controlled updates more than creators who promise “always current” with no process.
-
Real labs include messy telemetry, imperfect signals, and decision tradeoffs. Build story based incidents where learners must collect artifacts, justify conclusions, and write escalation notes. Use operational pressure themes from next-gen SIEM and workforce reality from job market trend analysis. If learners can produce clean evidence under time pressure, the lab is real enough to matter.
-
Price based on outcomes and scope, not hours. A “module build” is different from a full program with labs, grading automation, and analytics. Package your offer around pipeline impact, like reducing ramp time or standardizing incident handling quality. Tie the value to roles the market keeps demanding, using demand for specialized roles and the employer preference shift described in certifications of the future.
-
Start with how audits and regulations influence technical work. Learn to map controls to evidence, then build training that teaches teams how to produce that evidence during real incidents. Use the direction from future of cybersecurity compliance and the evolution themes in privacy regulations trends. Pair that with leadership pathway context from cybersecurity manager roadmaps so your curriculum matches what leaders actually measure.